Carding 4 Carders
Professional
- Messages
- 2,728
- Reaction score
- 1,574
- Points
- 113
A new cybercrime campaign that uses ads in Google Search attacks users who try to download and install the popular Notepad++text editor.
The Google Ads system was previously used to distribute malware that was linked to legitimate software. Attackers 'calculation of users' inattentiveness and trustfulness.
The new campaign was noticed by researchers from Malwarebytes. According to them, cybercriminals for several months freely used the Notepad++ text editor as bait.
Experts have not yet been able to accurately determine the final payload, but there is an assumption that this is a Cobalt Strike. If you look closely at the search results, it becomes obvious that there is no connection between malicious URLs and legitimate software:
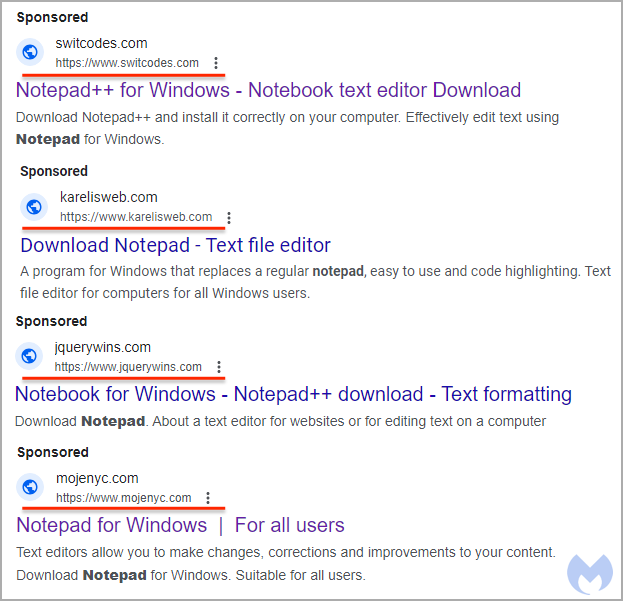
Following this link, the potential victim gets to the notepadxtreme resource[.] com, disguised as the official Notepad++website.
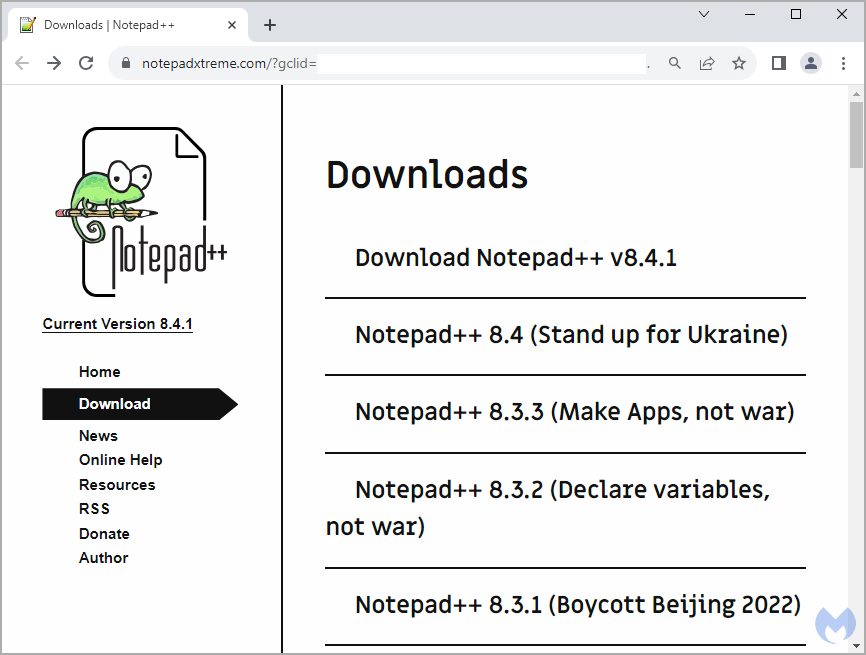
When trying to download the desired software, a special JavaScript snippet checks the digital fingerprint of the device to make sure that there are no anomalies (for example, if the user logged in from the sandbox).
If everything is in order, the victim is given a script in HTA format with a unique identifier. Interestingly, the page load is issued only once, and if you try to load it a second time, the user will get a 404 error.
Malwarebytes studied the mentioned HTA, noting that in July this sample was already uploaded to VirusTotal. At that time, no malicious component was detected in it.
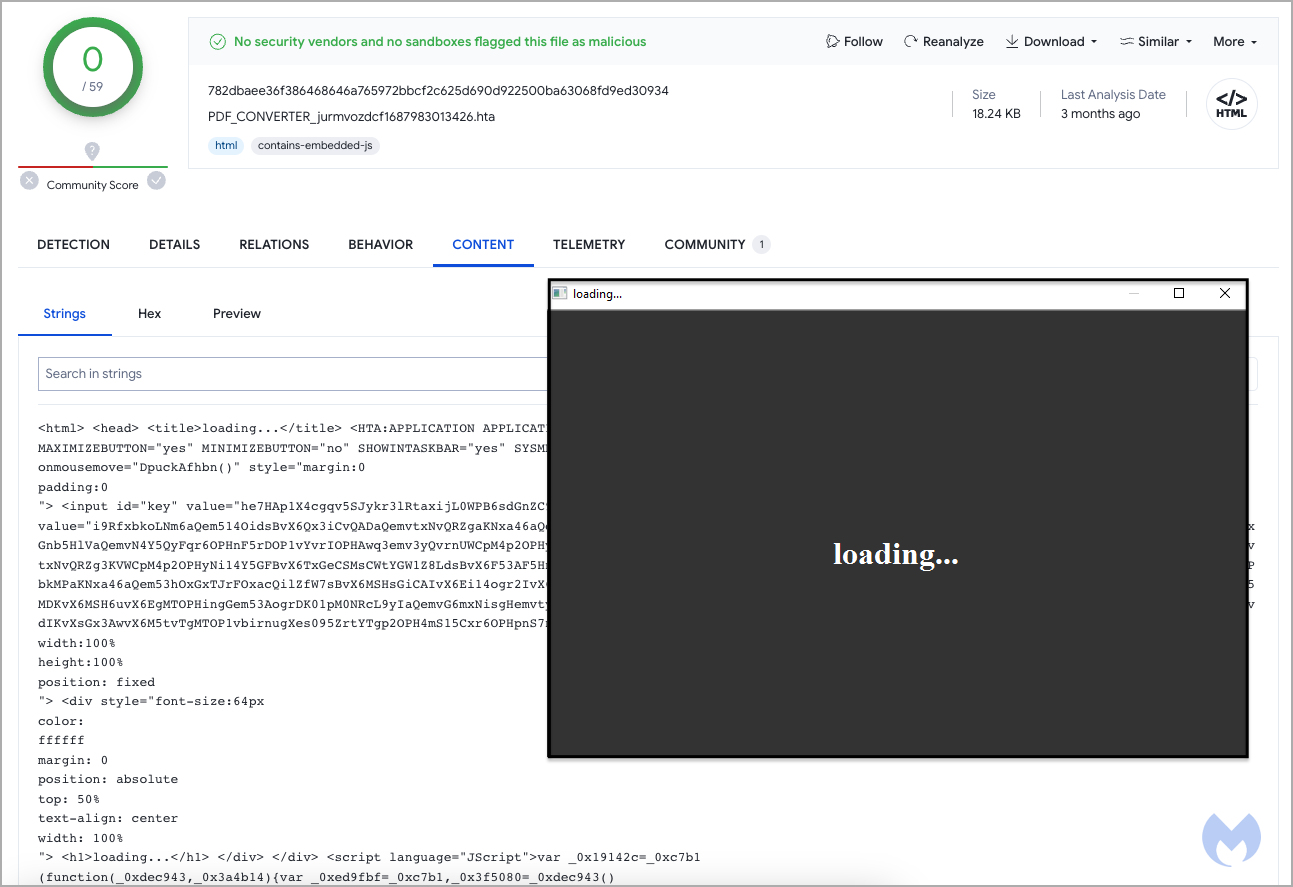
As a reminder, Notepad++ 8.5.7 was released in September with patches for four dangerous vulnerabilities.
The Google Ads system was previously used to distribute malware that was linked to legitimate software. Attackers 'calculation of users' inattentiveness and trustfulness.
The new campaign was noticed by researchers from Malwarebytes. According to them, cybercriminals for several months freely used the Notepad++ text editor as bait.
Experts have not yet been able to accurately determine the final payload, but there is an assumption that this is a Cobalt Strike. If you look closely at the search results, it becomes obvious that there is no connection between malicious URLs and legitimate software:

Following this link, the potential victim gets to the notepadxtreme resource[.] com, disguised as the official Notepad++website.

When trying to download the desired software, a special JavaScript snippet checks the digital fingerprint of the device to make sure that there are no anomalies (for example, if the user logged in from the sandbox).
If everything is in order, the victim is given a script in HTA format with a unique identifier. Interestingly, the page load is issued only once, and if you try to load it a second time, the user will get a 404 error.
Malwarebytes studied the mentioned HTA, noting that in July this sample was already uploaded to VirusTotal. At that time, no malicious component was detected in it.

As a reminder, Notepad++ 8.5.7 was released in September with patches for four dangerous vulnerabilities.
