An excellent article that covers the aspects of physical security and may be useful when conducting penetration testing. The article will describe methods of copying a pass card using a photo using Proxmark3 and how to protect against this ailment.
I'll tell you about the best life hack that I recently learned and tried on myself. But in any case, do not copy other people's cards without the consent of their owners.
Once I urgently needed to get into a business center with a pass system in the form of turnstiles that can be opened with pass cards. The person who had the pass at that moment was far away, he could not give it to me, and due to bureaucratic peculiarities, issuing a new card would take a lot of time.

What are we dealing with
So, the person with the pass is far away, of course he does not have a reader for contactless cards with him, but he has a phone with which you can take a photo of the card.
From the photo, the card was identified as EM-Marin, also known as EM4100. These contactless cards operate at a frequency of 125 KHz and contain a 40-bit or 5 byte number (hereinafter - ID), which is written to the card at the factory and cannot be changed. They do not have any protection against reading or copying.
An appropriate copier is required to record such cards. I use Proxmark3, but you can take any other that can work with the T5577 and allows you to enter the card ID manually. Or even use an emulator, then you can do without discs.
The card does not have its own power source, it comes from the reader "over the air", as in wireless chargers. The reader generates an electromagnetic field, the card catches it through the antenna and turns on. Next, the card modulates the field and begins to cyclically transmit its ID, which is caught by the reader, the communication is one-way.
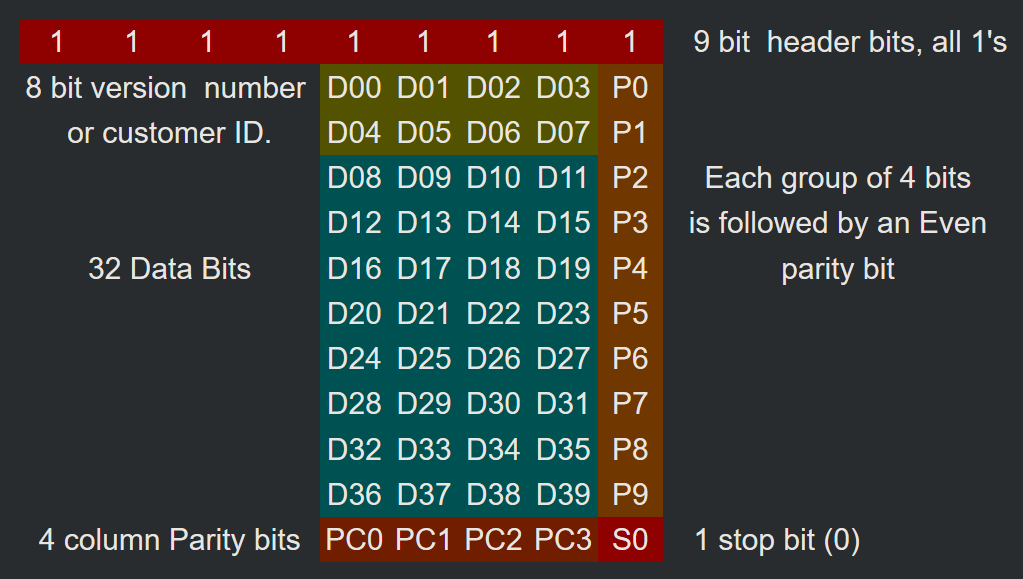
How exactly the data from the card is transmitted: first there is a preamble of 9 bits "1", then 1 byte Version Number, 2 bytes Facility Code and 2 bytes of the unique card number are transmitted, periodically followed by the parity bits. Taken from the link, by the way there is still a good description of the protocol (in English).
In the simplest version of the ACS construction, the reader itself is an access controller - it compares the card ID with the numbers in the memory and decides to open the lock or turnstile. In more complex systems, it sends this information to the controller over some interface.
Experiment
So, there are some numbers on the map. It was logical to assume that this is her ID. In order to find out this, I took the data of a similar card, the following was obtained:
After converting the ID from HEX to DEC, it turned out 317840976040, which does not look like the numbers from the card. Spoiler alert: if I did the opposite, and convert the numbers from the card to hexadecimal format, then I would have achieved success right away, but then this article would not be so meaningful
Reflecting on what else it could mean, I remembered that Proxmark, in addition to the ID card, shows some more data:
Aha, 0013396136 and 204.26792 - this is exactly what is written on the map!
But after all, only 5 bytes are stored on it, which means that these numbers must be calculated from the ID according to some algorithm by the reader or his client. Fortunately, Proxmark is an open-source project, its source code is available on github. I searched the repository for "DEZ 10" and found the cmdlfem4x.c function.
Part of the cmdlfem4x.c code:
From the code above, it becomes clear that these numbers are parts of the card ID:
0013396136 (DEZ 10) - the first 4 bytes, counting from low to high.
204.26792 (DEZ 3.5C) - the third byte separately (aka Facility Code) and directly 2 bytes of the card serial number.
Thus, using the numbers on the card, you can recover part of its ID. But what if 4 bytes are known, but 5 are required? And if the fourth byte had the value 0 on all cards I read, then the fifth byte is always non-zero. To iterate over this byte in a particular case is not an option - I do not want to arouse suspicion among the guards.
Then I remembered that the ACS in this business center had been installed for a long time, so I assumed that the popular but outdated Wiegand-26 could be used there for data transmission. This protocol is designed for communication between the reader and the controller, and allows you to transmit 24 data bits and 2 parity bits per one message, for a total of 3 payload bytes. This means that the card ID is not transmitted completely and the unknown fifth byte does not participate in identification in any way and can be random.
It is worth noting that some modern readers still read and compare the high byte of the card, in which case you will have to go through 255 combinations, but this can be done in a reasonable time, especially if you use an emulator.
Well, now it remains to check in practice all the studies above. To create a copy of the map, I took a blank T5577 and wrote down the received ID on it (the fifth byte is random):
After that, I wrote down the ID of the pass I needed, already converted in the same way.
As expected, the card was counted correctly, the turnstile clicked and the green indicator blinked.
P.S.
If you are responsible for security, then most likely everything described in this article will not be news to you. Otherwise, you shouldn't prematurely pull out your body hair. The problem lies in the fact that this card format does not initially provide a high level of security. These cards do not support any authentication and encryption mechanisms, therefore they can be copied at any time with a suitable reader. At serious facilities, such as banks, data centers and storage of nuclear warheads, more secure map formats are used instead of EM-Marin (at least I want to believe it). For example, this is the MIfare family, where the cards are divided into sectors with individual read and write keys, and some cards of this standard even support the AES encryption algorithm.
Finally, I repeat once again, do not copy other people's cards without the consent of their owners.
I'll tell you about the best life hack that I recently learned and tried on myself. But in any case, do not copy other people's cards without the consent of their owners.
Once I urgently needed to get into a business center with a pass system in the form of turnstiles that can be opened with pass cards. The person who had the pass at that moment was far away, he could not give it to me, and due to bureaucratic peculiarities, issuing a new card would take a lot of time.

What are we dealing with
So, the person with the pass is far away, of course he does not have a reader for contactless cards with him, but he has a phone with which you can take a photo of the card.
From the photo, the card was identified as EM-Marin, also known as EM4100. These contactless cards operate at a frequency of 125 KHz and contain a 40-bit or 5 byte number (hereinafter - ID), which is written to the card at the factory and cannot be changed. They do not have any protection against reading or copying.
Rewritable blank cards look like an ordinary blank plastic card in the form factor of a credit card, and non-rewritable ones (with a serial number stitched at the factory) are slightly thicker and have text on the front side, consisting of several groups of decimal digits. There are also cards in the form of key chains.To create duplicates of these cards, blanks T5577 and EM4305 are used, which are freely available for sale.
An appropriate copier is required to record such cards. I use Proxmark3, but you can take any other that can work with the T5577 and allows you to enter the card ID manually. Or even use an emulator, then you can do without discs.
The card does not have its own power source, it comes from the reader "over the air", as in wireless chargers. The reader generates an electromagnetic field, the card catches it through the antenna and turns on. Next, the card modulates the field and begins to cyclically transmit its ID, which is caught by the reader, the communication is one-way.

How exactly the data from the card is transmitted: first there is a preamble of 9 bits "1", then 1 byte Version Number, 2 bytes Facility Code and 2 bytes of the unique card number are transmitted, periodically followed by the parity bits. Taken from the link, by the way there is still a good description of the protocol (in English).
In the simplest version of the ACS construction, the reader itself is an access controller - it compares the card ID with the numbers in the memory and decides to open the lock or turnstile. In more complex systems, it sends this information to the controller over some interface.
Experiment
So, there are some numbers on the map. It was logical to assume that this is her ID. In order to find out this, I took the data of a similar card, the following was obtained:
Code:
Figures on the card: 0013396136 204.26792After converting the ID from HEX to DEC, it turned out 317840976040, which does not look like the numbers from the card. Spoiler alert: if I did the opposite, and convert the numbers from the card to hexadecimal format, then I would have achieved success right away, but then this article would not be so meaningful
Reflecting on what else it could mean, I remembered that Proxmark, in addition to the ID card, shows some more data:
Code:
lf searchproxmark3> lf searchAha, 0013396136 and 204.26792 - this is exactly what is written on the map!
But after all, only 5 bytes are stored on it, which means that these numbers must be calculated from the ID according to some algorithm by the reader or his client. Fortunately, Proxmark is an open-source project, its source code is available on github. I searched the repository for "DEZ 10" and found the cmdlfem4x.c function.
Part of the cmdlfem4x.c code:
Code:
...From the code above, it becomes clear that these numbers are parts of the card ID:
0013396136 (DEZ 10) - the first 4 bytes, counting from low to high.
204.26792 (DEZ 3.5C) - the third byte separately (aka Facility Code) and directly 2 bytes of the card serial number.
Thus, using the numbers on the card, you can recover part of its ID. But what if 4 bytes are known, but 5 are required? And if the fourth byte had the value 0 on all cards I read, then the fifth byte is always non-zero. To iterate over this byte in a particular case is not an option - I do not want to arouse suspicion among the guards.
Then I remembered that the ACS in this business center had been installed for a long time, so I assumed that the popular but outdated Wiegand-26 could be used there for data transmission. This protocol is designed for communication between the reader and the controller, and allows you to transmit 24 data bits and 2 parity bits per one message, for a total of 3 payload bytes. This means that the card ID is not transmitted completely and the unknown fifth byte does not participate in identification in any way and can be random.
It is worth noting that some modern readers still read and compare the high byte of the card, in which case you will have to go through 255 combinations, but this can be done in a reasonable time, especially if you use an emulator.
Well, now it remains to check in practice all the studies above. To create a copy of the map, I took a blank T5577 and wrote down the received ID on it (the fifth byte is random):
Code:
Write card proxmark3> lf em 410xwrite 0100CC68A8 1The result is an almost complete copy of the card with the photo, only the high byte differs. To be sure, you can enter the lf search command again and check if DEZ 10 and DEZ 3.5C match the numbers on the original card.
After that, I wrote down the ID of the pass I needed, already converted in the same way.
As expected, the card was counted correctly, the turnstile clicked and the green indicator blinked.
P.S.
If you are responsible for security, then most likely everything described in this article will not be news to you. Otherwise, you shouldn't prematurely pull out your body hair. The problem lies in the fact that this card format does not initially provide a high level of security. These cards do not support any authentication and encryption mechanisms, therefore they can be copied at any time with a suitable reader. At serious facilities, such as banks, data centers and storage of nuclear warheads, more secure map formats are used instead of EM-Marin (at least I want to believe it). For example, this is the MIfare family, where the cards are divided into sectors with individual read and write keys, and some cards of this standard even support the AES encryption algorithm.
Finally, I repeat once again, do not copy other people's cards without the consent of their owners.
