The group's strategy from publishing a PoC to installing malware has been identified.
The Magnet Goblin group actively exploits vulnerabilities in public servers to deploy malware on Windows and Linux systems.
The group is targeting 1-day vulnerabilities-publicized security issues that have been patched and require quick action from attackers before updates are installed by the target systems.
Check Point analysts who discovered the activity of Magnet Goblin note the group's desire to exploit vulnerabilities immediately after the publication of a Proof-of-Concept (PoC). Among the targets of the attacks are devices or services such as Ivanti Connect Secure, Apache ActiveMQ, ScreenConnect, Qlik Sense and Magento, the use of which leads to infection of servers with specialized malware, including NerbianRAT and MiniNerbian, as well as a custom version of the JavaScript malware WARPWIRE for stealing credentials.
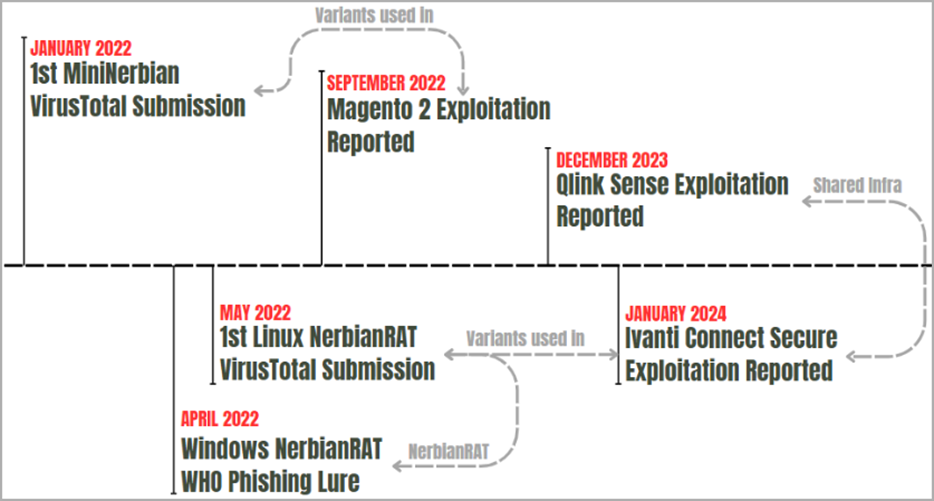
Timeline of Magnet Goblin activities
An analysis of the infrastructure used in the campaigns against Magento and Ivanti showed the use of additional tools for Linux and Windows, including the ScreenConnect program. A possible link to the CACTUS ransomware program, which was used in attacks on the Qlik Sense business intelligence platform, was also noted.
Special attention is paid to the Linux malware NerbianRAT, known since 2022, and its simplified version MiniNerbian. Both versions of the program can collect information about the system, execute commands from the Command and Control server (C2), and provide encrypted communication. Experts note that MiniNerbian uses HTTP for data transmission and is only active during certain hours.
Magnet Goblin uses its own tools to ensure stable control over infected systems, using different communication methods: MiniNerbian communicates via HTTP, and NerbianRAT uses raw TCP sockets.
According to Check Point, identifying specific threats like the Magnet Goblin attacks among all the data on 1-day exploitation is a difficult task. This problem allows hackers to remain undetected amid the chaos that occurs after the vulnerabilities are made public.
Timely application of fixes is critical to counteract 1-day exploitation. Additional measures such as network segmentation, endpoint protection, and multi-factor authentication can help reduce the risk and impact of potential breaches.
The Magnet Goblin group actively exploits vulnerabilities in public servers to deploy malware on Windows and Linux systems.
The group is targeting 1-day vulnerabilities-publicized security issues that have been patched and require quick action from attackers before updates are installed by the target systems.
Check Point analysts who discovered the activity of Magnet Goblin note the group's desire to exploit vulnerabilities immediately after the publication of a Proof-of-Concept (PoC). Among the targets of the attacks are devices or services such as Ivanti Connect Secure, Apache ActiveMQ, ScreenConnect, Qlik Sense and Magento, the use of which leads to infection of servers with specialized malware, including NerbianRAT and MiniNerbian, as well as a custom version of the JavaScript malware WARPWIRE for stealing credentials.

Timeline of Magnet Goblin activities
An analysis of the infrastructure used in the campaigns against Magento and Ivanti showed the use of additional tools for Linux and Windows, including the ScreenConnect program. A possible link to the CACTUS ransomware program, which was used in attacks on the Qlik Sense business intelligence platform, was also noted.
Special attention is paid to the Linux malware NerbianRAT, known since 2022, and its simplified version MiniNerbian. Both versions of the program can collect information about the system, execute commands from the Command and Control server (C2), and provide encrypted communication. Experts note that MiniNerbian uses HTTP for data transmission and is only active during certain hours.
Magnet Goblin uses its own tools to ensure stable control over infected systems, using different communication methods: MiniNerbian communicates via HTTP, and NerbianRAT uses raw TCP sockets.
According to Check Point, identifying specific threats like the Magnet Goblin attacks among all the data on 1-day exploitation is a difficult task. This problem allows hackers to remain undetected amid the chaos that occurs after the vulnerabilities are made public.
Timely application of fixes is critical to counteract 1-day exploitation. Additional measures such as network segmentation, endpoint protection, and multi-factor authentication can help reduce the risk and impact of potential breaches.
