Friend
Professional
- Messages
- 2,671
- Reaction score
- 1,103
- Points
- 113
A random click on an ad risks turning into a HeadLace attack.
The hacker group APT28 recently launched a new campaign to distribute the HeadLace malware through a fake car sale ad. The campaign began in March 2024 and is likely aimed at diplomats.
This tactic is not new to cybercriminals. For several years now, they have been using fake luxury car ads to attract the attention of victims and inject malicious code.
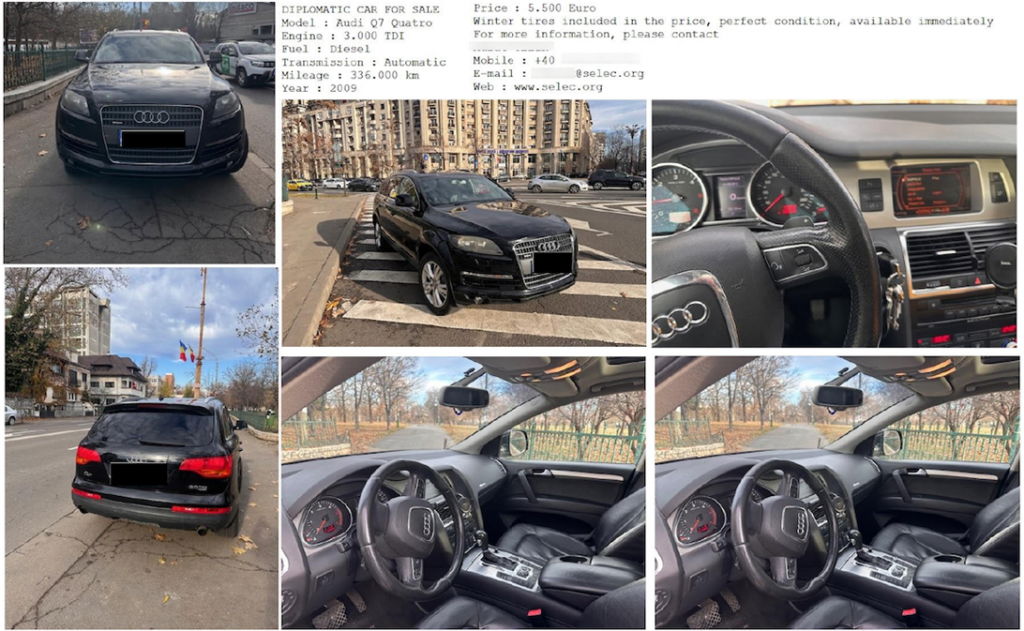
Fake Ad
According to Unit 42 specialists, during the latest campaign related to APT28, public and free services were used to place malicious files and links. For example, a suspicious link was placed on a legal Webhook service[.]site, which allows you to create randomized URLs for various purposes. This functionality was used by hackers to distribute a malicious HTML document.
When you visit this link, the algorithms on the page check whether the computer is using the Windows operating system. If not, the user is redirected to a fake image posted on the free ImgBB service. However, in the case of Windows, the HTML document creates a ZIP archive containing malicious files and offers it for download.
The fake ad for the sale of a car (Audi Q7 Quattro) contains contact details and information about the seller, allegedly located in Romania, which should give the offer credibility. However, all this data is fictitious and serves only to attract the attention of victims.
Downloaded archive " IMG-387470302099.zip " contains three files, one of which is disguised as an image, but is actually an executable file containing a copy of a legitimate calculator from Windows — "calc.exe". This file is used to load a malicious DLL "WindowsCodecs.dll", which, in turn, starts the file "zqtxmo. bat", which ends the infection chain.
APT28 actively uses free legitimate services to host attack elements, which makes them more difficult to detect. The methods used in this campaign correspond to previously documented attacks of this group, and the HeadLace malware is exclusively associated with this group.
To protect yourself from such attacks, it is recommended to restrict access to services that are popular among hackers, or just carefully check their use. Organizations should carefully monitor their free network resources to quickly identify possible attack vectors.
Source
The hacker group APT28 recently launched a new campaign to distribute the HeadLace malware through a fake car sale ad. The campaign began in March 2024 and is likely aimed at diplomats.
This tactic is not new to cybercriminals. For several years now, they have been using fake luxury car ads to attract the attention of victims and inject malicious code.

Fake Ad
According to Unit 42 specialists, during the latest campaign related to APT28, public and free services were used to place malicious files and links. For example, a suspicious link was placed on a legal Webhook service[.]site, which allows you to create randomized URLs for various purposes. This functionality was used by hackers to distribute a malicious HTML document.
When you visit this link, the algorithms on the page check whether the computer is using the Windows operating system. If not, the user is redirected to a fake image posted on the free ImgBB service. However, in the case of Windows, the HTML document creates a ZIP archive containing malicious files and offers it for download.
The fake ad for the sale of a car (Audi Q7 Quattro) contains contact details and information about the seller, allegedly located in Romania, which should give the offer credibility. However, all this data is fictitious and serves only to attract the attention of victims.
Downloaded archive " IMG-387470302099.zip " contains three files, one of which is disguised as an image, but is actually an executable file containing a copy of a legitimate calculator from Windows — "calc.exe". This file is used to load a malicious DLL "WindowsCodecs.dll", which, in turn, starts the file "zqtxmo. bat", which ends the infection chain.
APT28 actively uses free legitimate services to host attack elements, which makes them more difficult to detect. The methods used in this campaign correspond to previously documented attacks of this group, and the HeadLace malware is exclusively associated with this group.
To protect yourself from such attacks, it is recommended to restrict access to services that are popular among hackers, or just carefully check their use. Organizations should carefully monitor their free network resources to quickly identify possible attack vectors.
Source
