CarderPlanet
Professional
- Messages
- 2,549
- Reaction score
- 728
- Points
- 113
The rat chews through the caches of inattentive users.
Specialists of the information security company Proofpoint discovered a new strain of malware called ZenRAT, which is distributed through fake installation packages of the popular Bitwarden password manager.
According to Proofpoint, ZenRAT is aimed at Windows users. When trying to access from other systems, users are redirected to a harmless web page. ZenRAT is a modular Remote Access Trojan (RAT) with information theft capabilities.
The malware is hosted on fake sites that mimic Bitwarden-related pages. However, it is not yet clear exactly how traffic is routed to the fake domains. Note that malware is usually distributed through phishing, fraudulent advertising, or SEO attacks (such as SEO poisoning).
Downloadable file (Bitwarden-Installer-version-2023-7-1.exe) from the crazygameis site[.] com is a Trojan version of the standard Bitwarden installation package that contains malware .NET executable file (ApplicationRuntimeMonitor.exe).
It is noteworthy that users visiting the fraudulent site from "non-Windows" systems are redirected to the cloned article opensource.com published in March 2018, on how to manage passwords using Bitwarden. In addition, Windows users who click on the download links for Linux or macOS versions are redirected to the official Bitwarden website (vault.bitwarden.com).

Cloned opensource article
Analysis of the installer's metadata reveals malicious attempts to disguise the malware as Piriform's Speccy, a free utility for Windows. The digital signature used to sign the executable file is not only invalid, but also allegedly signed by Tim Kosse, a well-known German computer scientist and creator of the free FileZilla software.
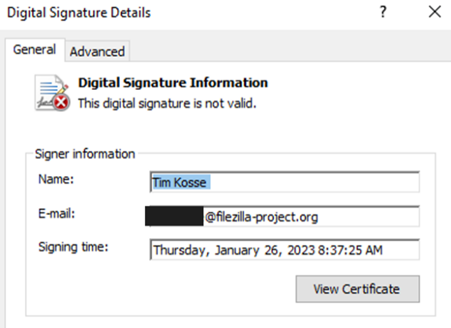
Executable file signature
Once launched, ZenRAT collects information about the host, including the name of the processor, video card, OS version, browser credentials, and installed applications, and sends it to a command and control server (C2 server) managed by attackers. To prevent such threats, it is recommended to download software only from trusted sources and verify the authenticity of the websites.
Specialists of the information security company Proofpoint discovered a new strain of malware called ZenRAT, which is distributed through fake installation packages of the popular Bitwarden password manager.
According to Proofpoint, ZenRAT is aimed at Windows users. When trying to access from other systems, users are redirected to a harmless web page. ZenRAT is a modular Remote Access Trojan (RAT) with information theft capabilities.
The malware is hosted on fake sites that mimic Bitwarden-related pages. However, it is not yet clear exactly how traffic is routed to the fake domains. Note that malware is usually distributed through phishing, fraudulent advertising, or SEO attacks (such as SEO poisoning).
Downloadable file (Bitwarden-Installer-version-2023-7-1.exe) from the crazygameis site[.] com is a Trojan version of the standard Bitwarden installation package that contains malware .NET executable file (ApplicationRuntimeMonitor.exe).
It is noteworthy that users visiting the fraudulent site from "non-Windows" systems are redirected to the cloned article opensource.com published in March 2018, on how to manage passwords using Bitwarden. In addition, Windows users who click on the download links for Linux or macOS versions are redirected to the official Bitwarden website (vault.bitwarden.com).

Cloned opensource article
Analysis of the installer's metadata reveals malicious attempts to disguise the malware as Piriform's Speccy, a free utility for Windows. The digital signature used to sign the executable file is not only invalid, but also allegedly signed by Tim Kosse, a well-known German computer scientist and creator of the free FileZilla software.

Executable file signature
Once launched, ZenRAT collects information about the host, including the name of the processor, video card, OS version, browser credentials, and installed applications, and sends it to a command and control server (C2 server) managed by attackers. To prevent such threats, it is recommended to download software only from trusted sources and verify the authenticity of the websites.

