Brother
Professional
- Messages
- 2,590
- Reaction score
- 537
- Points
- 113
Foreign employees became victims of a campaign with vulnerable versions of WinRAR.
Cybercrime group UAC-0099 continues to attack Ukraine, using a vulnerability in WinRAR to distribute LONEPAGE malware.
According to the information security company Deep Instinct, the main target of the attacks are Ukrainian employees working outside the country. The UAC-0099 group was first detected by the Ukrainian Computer Emergency Response Team (CERT-UA) in June 2023. It was noted that the attacks are aimed at state organizations and the media for the purpose of espionage. The UAC-0099 group also received unauthorized remote access to dozens of computers in Ukraine in 2022-2023.
Attacks are carried out using phishing messages containing HTA, RAR, and LNK attachments, which lead to the deployment of LONEPAGE, a Visual Basic Script (VBS) malware that can communicate with the management server to obtain additional malware, such as keyloggers, infostilers, and screenshot programs.
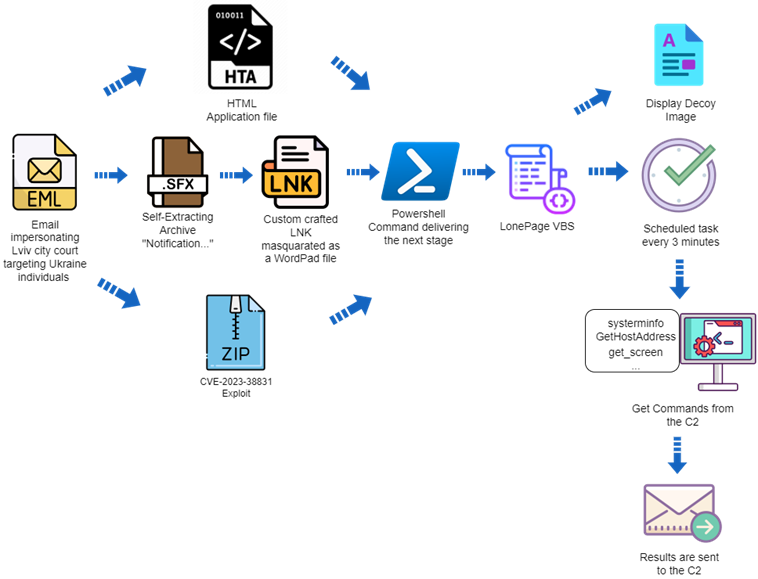
UAC-0099 Attack Chain
Deep Instinct's latest analysis shows that using HTA attachments is just one of three different ways to get infected. The other two include self-extracting archives (SFX) and ZIP archives with decoy documents. ZIP files for distributing LONEPAGE exploit the WinRAR vulnerability (CVE-2023-38831, CVSS score: 7.8), which allows attackers to execute arbitrary code when a user tries to view a secure file in a ZIP archive.
In one case, the SFX file contains an LNK shortcut disguised as a DOCX file with a subpoena, and uses the Microsoft WordPad icon to encourage the victim to open it. The attack leads to execution of malicious PowerShell code and installation of LONEPAGE.
Another attack uses a specially created ZIP archive that is vulnerable to CVE-2023-38831. Deep Instinct discovered two such files created by UAC-0099 on August 5, 2023, three days after WinRAR developers released a patch for the vulnerability.
As stated in Deep Instinct, the tactics used by UAC-0099 are simple, but effective. Despite the different methods of initial infection, the basis of the infection remains the same: it is based on using PowerShell and creating a scheduled task that executes a VBS file.
The use of complex infection methods, including vulnerabilities in the popular WinRAR software, demonstrates the high level of training of the UAC-0099 group. The need for vigilance and increased security measures for both the public and private sectors is becoming clear. This case highlights the importance of constantly updating and strengthening security systems to prevent future cyber attacks and protect the country's digital infrastructure.
Cybercrime group UAC-0099 continues to attack Ukraine, using a vulnerability in WinRAR to distribute LONEPAGE malware.
According to the information security company Deep Instinct, the main target of the attacks are Ukrainian employees working outside the country. The UAC-0099 group was first detected by the Ukrainian Computer Emergency Response Team (CERT-UA) in June 2023. It was noted that the attacks are aimed at state organizations and the media for the purpose of espionage. The UAC-0099 group also received unauthorized remote access to dozens of computers in Ukraine in 2022-2023.
Attacks are carried out using phishing messages containing HTA, RAR, and LNK attachments, which lead to the deployment of LONEPAGE, a Visual Basic Script (VBS) malware that can communicate with the management server to obtain additional malware, such as keyloggers, infostilers, and screenshot programs.

UAC-0099 Attack Chain
Deep Instinct's latest analysis shows that using HTA attachments is just one of three different ways to get infected. The other two include self-extracting archives (SFX) and ZIP archives with decoy documents. ZIP files for distributing LONEPAGE exploit the WinRAR vulnerability (CVE-2023-38831, CVSS score: 7.8), which allows attackers to execute arbitrary code when a user tries to view a secure file in a ZIP archive.
In one case, the SFX file contains an LNK shortcut disguised as a DOCX file with a subpoena, and uses the Microsoft WordPad icon to encourage the victim to open it. The attack leads to execution of malicious PowerShell code and installation of LONEPAGE.
Another attack uses a specially created ZIP archive that is vulnerable to CVE-2023-38831. Deep Instinct discovered two such files created by UAC-0099 on August 5, 2023, three days after WinRAR developers released a patch for the vulnerability.
As stated in Deep Instinct, the tactics used by UAC-0099 are simple, but effective. Despite the different methods of initial infection, the basis of the infection remains the same: it is based on using PowerShell and creating a scheduled task that executes a VBS file.
The use of complex infection methods, including vulnerabilities in the popular WinRAR software, demonstrates the high level of training of the UAC-0099 group. The need for vigilance and increased security measures for both the public and private sectors is becoming clear. This case highlights the importance of constantly updating and strengthening security systems to prevent future cyber attacks and protect the country's digital infrastructure.

