Tomcat
Professional
- Messages
- 2,688
- Reaction score
- 1,015
- Points
- 113
Initially, the mobile malware shifted its focus to desktop platforms.
The malware called LightSpy, previously known only for attacks on Android and iOS, has now been spotted on macOS as well, confirming its extensive data collection capabilities.
LightSpy is a modular spy framework that is used to steal a variety of information, including files, screenshots, location data, WeChat voice call recordings, and data from Telegram and QQ Messenger.
According to a new ThreatFabric report, the LightSpy version for macOS has been actively used since January 2024, although so far it only works in test environments and a few infected devices owned by the researchers themselves.
Experts gained access to the LightSpy control panel by exploiting a configuration vulnerability, which allowed them to understand the functionality, infrastructure, and list of infected devices.
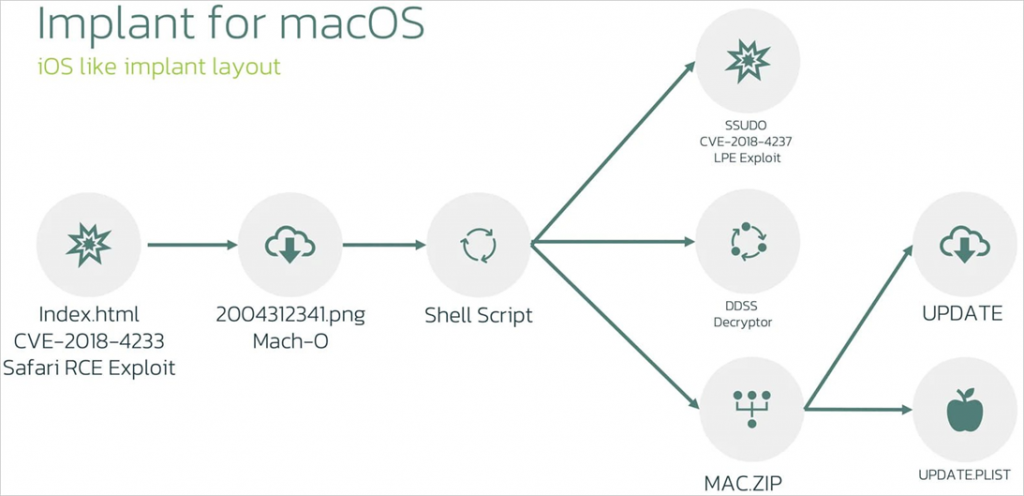
Attackers use WebKit vulnerabilities (CVE-2018-4233 and CVE-2018-4404)to execute code in Safari on macOS 10.13.3 and earlier.
Initially, a 64-bit MachO binary file disguised as a PNG image ("20004312341.png") is delivered to the device. This file then decrypts and executes embedded scripts to load the next step.
The second stage already downloads the privilege escalation exploit ("ssudo"), the encryption/decryption utility ("ddss"), and the ZIP archive ("mac.zip") with two executable files ("update" and "update. plist").
Then the script gets root access on the infected device and installs stability in the system, configuring "update" to run at system startup.
The next step is performed by the "macircloader" component, which downloads, decrypts, and executes LightSpy Core, which manages the spyware plugins and is responsible for communicating with the command server.
LightSpy Core can also execute shell commands on the device, update network configuration, and set activity schedules to bypass detection.
Attack pattern
Although the malware uses 14 Android plugins and 16 iOS plugins, the macOS version uses only the following 10:
These plug-ins allow LightSpy to collect extensive data from infected macOS systems, providing flexibility for the malware.
While investigating the LightSpy web dashboard, ThreatFabric specialists also discovered the potential existence of implants for Windows, Linux, and routers, but so far there is no information about how to deliver them and use them in real attacks.
Thus, despite some limitations of the latest versions of the LightSpy malware, its modular nature and extensive functionality for collecting confidential data pose a serious security threat not only for macOS users, but also, hypothetically, for other desktop platforms.
Users need to be vigilant, update their software in a timely manner, and use robust cybersecurity tools to protect their devices and data.
The malware called LightSpy, previously known only for attacks on Android and iOS, has now been spotted on macOS as well, confirming its extensive data collection capabilities.
LightSpy is a modular spy framework that is used to steal a variety of information, including files, screenshots, location data, WeChat voice call recordings, and data from Telegram and QQ Messenger.
According to a new ThreatFabric report, the LightSpy version for macOS has been actively used since January 2024, although so far it only works in test environments and a few infected devices owned by the researchers themselves.
Experts gained access to the LightSpy control panel by exploiting a configuration vulnerability, which allowed them to understand the functionality, infrastructure, and list of infected devices.
Attackers use WebKit vulnerabilities (CVE-2018-4233 and CVE-2018-4404)to execute code in Safari on macOS 10.13.3 and earlier.
Initially, a 64-bit MachO binary file disguised as a PNG image ("20004312341.png") is delivered to the device. This file then decrypts and executes embedded scripts to load the next step.
The second stage already downloads the privilege escalation exploit ("ssudo"), the encryption/decryption utility ("ddss"), and the ZIP archive ("mac.zip") with two executable files ("update" and "update. plist").
Then the script gets root access on the infected device and installs stability in the system, configuring "update" to run at system startup.
The next step is performed by the "macircloader" component, which downloads, decrypts, and executes LightSpy Core, which manages the spyware plugins and is responsible for communicating with the command server.
LightSpy Core can also execute shell commands on the device, update network configuration, and set activity schedules to bypass detection.

Attack pattern
Although the malware uses 14 Android plugins and 16 iOS plugins, the macOS version uses only the following 10:
- soundrecord: captures audio from the microphone;
- browser: retrieves data from browsers;
- cameramodule: takes photos from the device's camera;
- FileManage: Manages and retrieves files, especially from instant messengers;
- keychain: retrieves data from the Keychain;
- LanDevices: Identifies devices on the local network;
- softlist: shows installed apps and running processes;
- ScreenRecorder: Records the device screen;
- ShellCommand: executes shell commands on the device;
- wifi: Collects data about connected Wi-Fi networks.
These plug-ins allow LightSpy to collect extensive data from infected macOS systems, providing flexibility for the malware.
While investigating the LightSpy web dashboard, ThreatFabric specialists also discovered the potential existence of implants for Windows, Linux, and routers, but so far there is no information about how to deliver them and use them in real attacks.
Thus, despite some limitations of the latest versions of the LightSpy malware, its modular nature and extensive functionality for collecting confidential data pose a serious security threat not only for macOS users, but also, hypothetically, for other desktop platforms.
Users need to be vigilant, update their software in a timely manner, and use robust cybersecurity tools to protect their devices and data.
