Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,095
- Points
- 113
Security experts from ESET reported that North-Korea-linked Lazarus APT (aka HIDDEN COBRA) is behind cyber campaigns targeting South Korean supply chains. According to the experts the nation-state actors leverage stolen security certificates from two separate, legitimate South Korean companies.
The activity of the Lazarus APT group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks. This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems.
The group is considered responsible for the massive WannaCry ransomware attack, a string of SWIFTattacks in 2016, and the Sony Pictures hack.
According to a report published by Kaspersky Lab in January 2020, in the two years the North Korea-linked APT group has continued to target cryptocurrency exchanges evolving its TTPs.
In August, F-Secure Labs experts observed a spear-phishing campaign targeting an organization in the cryptocurrency industry.
In campaigns spotted by ESET, Lazarus attackers attempted to deploy their malware via a supply-chain attack in South Korea.
“In order to deliver its malware, the attackers used an unusual supply-chain mechanism, abusing legitimate South Korean security software and digital certificates stolen from two different companies.” reads the analysis published by ESET.
The attackers are attempting to exploit the need to install additional security software when South Korean users visit government or financial services websites.
The WIZVERA VeraPort integration installation program is used to manage additional security software (e.g., browser plug-ins, security software, identity verification software, etc.) that is requested to visit particular government and banking domains.
WIZVERA VeraPort is used to digitally sign and verify downloads.
Websites that support the WIZVERA VeraPort software contain a server-side component, specifically some JavaScripts and a WIZVERA configuration file. The configuration file is base64-encoded XML containing multiple parameters, including the website address, the list of software to install, and download URLs. Attackers can replace the software to be delivered to users via WIZVERA VeraPort from a legitimate, compromised website
“These configuration files are digitally signed by WIZVERA. Once downloaded, they are verified using a strong cryptographic algorithm (RSA), which is why attackers can’t easily modify the content of these configuration files or set up their own fake website.” continues the report. “However, the attackers can replace the software to be delivered to WIZVERA VeraPort users from a legitimate but compromised website. We believe this is the scenario the Lazarus attackers used.”

Lazarus threat actors were able to obtain code-signing certificates from two South Korean security companies in order to carry out supply chain attacks.
The experts pointed out that WIZVERA VeraPort only verifies the signature for the downloaded binaries, without checking to whom it belongs.
This behavior opens the door to attacks, for this reason, Lazarus APT leverages on valid, but stolen digital certificates to deliver their malware.
Experts detected two malware samples that were delivered with this technique as legitimate, South Korean software. The software appears to be legitimate, it uses similar names, icons, icons, and VERSIONINFO resources as legitimate South Korean software often delivered via WIZVERA VeraPort.
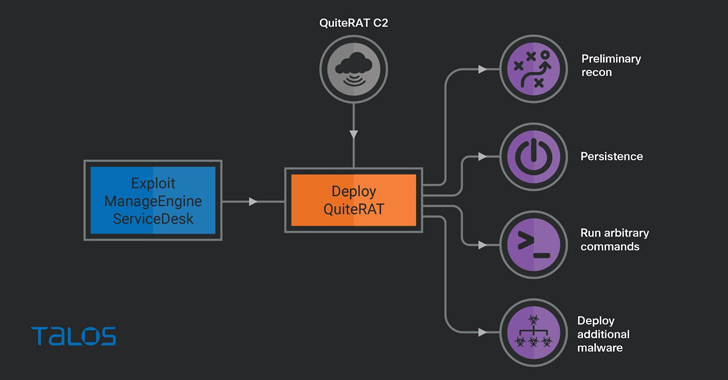
When a victim visits a compromised website, the WIZVERA VeraPort will serve a dropper for the Lazarus malware, which extracts a downloader and configuration files.
Then the malware connects to the attacker’s command-and-control (C2) server and the final payload, which is a Remote Access Trojan (RAT), is deployed on the victim’s machine.
“It’s the combination of compromised websites with WIZVERA VeraPort support and specific VeraPort configuration options that allow attackers to perform this attack,” ESET concludes. “Owners of such websites could decrease the possibility of such attacks, even if their sites are compromised, by enabling specific options (e.g. by specifying hashes of binaries in the VeraPort configuration).”
The activity of the Lazarus APT group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks. This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems.
The group is considered responsible for the massive WannaCry ransomware attack, a string of SWIFTattacks in 2016, and the Sony Pictures hack.
According to a report published by Kaspersky Lab in January 2020, in the two years the North Korea-linked APT group has continued to target cryptocurrency exchanges evolving its TTPs.
In August, F-Secure Labs experts observed a spear-phishing campaign targeting an organization in the cryptocurrency industry.
In campaigns spotted by ESET, Lazarus attackers attempted to deploy their malware via a supply-chain attack in South Korea.
“In order to deliver its malware, the attackers used an unusual supply-chain mechanism, abusing legitimate South Korean security software and digital certificates stolen from two different companies.” reads the analysis published by ESET.
The attackers are attempting to exploit the need to install additional security software when South Korean users visit government or financial services websites.
The WIZVERA VeraPort integration installation program is used to manage additional security software (e.g., browser plug-ins, security software, identity verification software, etc.) that is requested to visit particular government and banking domains.
WIZVERA VeraPort is used to digitally sign and verify downloads.
Websites that support the WIZVERA VeraPort software contain a server-side component, specifically some JavaScripts and a WIZVERA configuration file. The configuration file is base64-encoded XML containing multiple parameters, including the website address, the list of software to install, and download URLs. Attackers can replace the software to be delivered to users via WIZVERA VeraPort from a legitimate, compromised website
“These configuration files are digitally signed by WIZVERA. Once downloaded, they are verified using a strong cryptographic algorithm (RSA), which is why attackers can’t easily modify the content of these configuration files or set up their own fake website.” continues the report. “However, the attackers can replace the software to be delivered to WIZVERA VeraPort users from a legitimate but compromised website. We believe this is the scenario the Lazarus attackers used.”

Lazarus threat actors were able to obtain code-signing certificates from two South Korean security companies in order to carry out supply chain attacks.
The experts pointed out that WIZVERA VeraPort only verifies the signature for the downloaded binaries, without checking to whom it belongs.
This behavior opens the door to attacks, for this reason, Lazarus APT leverages on valid, but stolen digital certificates to deliver their malware.
Experts detected two malware samples that were delivered with this technique as legitimate, South Korean software. The software appears to be legitimate, it uses similar names, icons, icons, and VERSIONINFO resources as legitimate South Korean software often delivered via WIZVERA VeraPort.
When a victim visits a compromised website, the WIZVERA VeraPort will serve a dropper for the Lazarus malware, which extracts a downloader and configuration files.
Then the malware connects to the attacker’s command-and-control (C2) server and the final payload, which is a Remote Access Trojan (RAT), is deployed on the victim’s machine.
“It’s the combination of compromised websites with WIZVERA VeraPort support and specific VeraPort configuration options that allow attackers to perform this attack,” ESET concludes. “Owners of such websites could decrease the possibility of such attacks, even if their sites are compromised, by enabling specific options (e.g. by specifying hashes of binaries in the VeraPort configuration).”