Mutt
Professional
- Messages
- 1,457
- Reaction score
- 1,268
- Points
- 113

The article is presented for informational purposes only and does not call for action!
In this article, we will raise the issue of keyloggers and stealers. This is a fairly simple way to get data if you have access to the device or to the location of the computer. It is also possible to carry out infection through the network.
But first things first.
Keyloggers
A keylogger is a software or hardware device that is designed to record keyboard presses as well as mouse movements and clicks. Additionally, keyloggers can record the date and time of pressing, as well as take screenshots and video recordings of the screen. It is also possible to copy data from the clipboard. It turns out that even password managers are vulnerable to such things.
There are only three types of keyloggers: software, hardware and acoustic. In practice, I've only met the first two. Therefore, in the article we will talk about them in detail.
Software keyloggers exercise full control over the user's activities. Now the software can freely intercept information from windows, read clicks, intercept a buffer, take screenshots and screen recordings, track mail, as well as intercept data from a webcam, printer, etc. A very important point - even if you have anti-virus protection, then there is a possibility of detection only at the time of launch. It is quite difficult to notice the reading afterwards.
Hardware keyloggers are usually placed between the computer and the keyboard. Or they can be built into the keyboard itself to intercept data. Hardware keyloggers do not require registration or additional installation of drivers. Typically, it has enough memory to record about 20 million keystrokes. They are quite difficult to define.
Basically, these click logs are transmitted via E-mail, FTP and HTTP.
Examples of software keyloggers
Windows Spy Keylogger
Free software that allows you to track activity and keep a log of files of keystrokes on the keyboard. You can intercept information such as chat conversations, social networks, as well as logins and passwords. You can hide the keylogger in the operating system. The developers of this program are the SecurityXploded group. Supported versions Windows XP, 2003, Vista, Windows 7, 8, 8.1, 10.
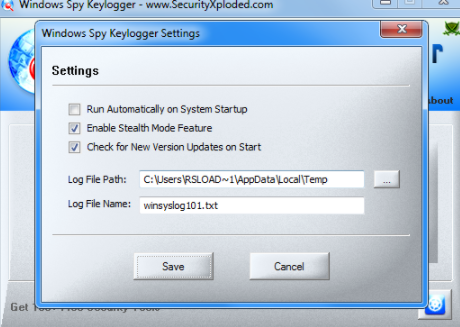
Windows Spy Keylogger
This software does not have much functionality, you can only configure automatic launch, hidden mode, and check for updates.
The data log is stored at this address:
Code:
c: \ temp \ winspykeyloggerThe report file has the name:
Code:
winsyslog101.txtIf you decide to use this program, it is better to change the location and names to others in order to reduce the paleness.
JETLOGGER
Strong enough in functionality, shareware. Allows you to get a general summary: activity time, programs, search queries, take screenshots, and also capture the clipboard. All features are available in the free version, except for the full hidden mode.
This software is really very powerful and can leave dozens of competitors behind. If it is possible to secretly install and run, then you can get all the data and files.
Test results on the machine.
Configuring sending data to mail.
Trial Watching Alert.
Observer
For mobile devices, the best program is Observer. The program is shareware and has good functionality. It can record calls, SMS, eavesdrop on a microphone, answer calls unnoticed by a person, show movement around the world map and satellites, photos and videos, correspondence, voice memos, documents, etc.
Additionally, you can find out if the SIM card will be changed. There is a list of applications, access to the calendar, etc. You can control it via SMS and the Internet.
Stealer consists of two programs: OBServer and Server. The first program is installed on the phone, the second on the second device or computer. The developers are really working on the product.
I think the essence is clear and simple, if you need something more serious, go to private boards and look for paid software.
Its main feature is encryption and the absence of signatures in the database. Thus, the likelihood that he will be burned is almost minimal.
Those that I described above are working, only they are detected by antiviruses.

Stealer
Stealer (from English to steal, to steal) is a certain class of Trojans (malware, viruses - whatever you want), the functionality of which consists entirely of stealing passwords stored in the system and sending them to the "author".
Logs are sent to FTP and mail.
UFR Stealer v4
The program is quite interesting, but it was last updated in 2013. Therefore, there may be problems with newer versions of Google Chrome. Of the useful functions: the ability to paste with other files, sending by mail and FTP. The program is really not bad, but it is fired by antiviruses.
After formation, the executable file can be sent to a USB flash drive or via the Internet. Passwords will be stolen after launch.
XSTEALER
Stiller has a fairly simple functionality. After downloading, a panel opens that allows you to generate an executable file.

XSTEALER interface
When building the stealer itself, you can select a lot of parameters and make a similar shortcut to some program. To do this, you can specify a name, organization, description, and also choose a convenient icon. If you don't have time to mess with it, then you can generate it randomly. We indicate the connection:
127.0.0.1
Port: 8500

XSteal program interface
In the screenshot, all parameters are randomly generated and the connection parameters are indicated. After that, you need to generate an .exe file.
Saving the executable file
Before running the file, you need to configure "Listening". We indicate the data that was when the file was built. After that, you can add notifications about the new log file.

Configuring "Listening ports"

Opening a log file
After the connection is established, the information is displayed in the Logs file. To do this, double-click on the file and open the log file. After that, all passwords from browsers appear in the list. You can look at it in a text file or copy it to a USB flash drive.

Log file of received passwords
Conclusion
In any case, such methods can be used in penetration testing. After all, the reliability of the system is determined by the weakest link. This link can be a user who can merge all passwords and data using keyloggers and stealers. You understand the essence of the work, but good software can be found on private boards. There are quite budget versions with a license for one month at a price of $ 10-35.






