Experts described the process of searching for a virus using the log in iOS.
Kaspersky Lab specialists shared their experience in analyzing iOS devices infected with Pegasus spyware from the Israeli company NSO Group. Malicious programs were found to leave traces in the system Shutdown.log file. The developed method can help detect not only Pegasus, but also other malicious programs, such as QuaDream's Reign and Cytrox's Predator, which use similar paths in the file system.
Shutdown. log is a text log file that is created on iOS devices every time they reboot. It records information about the processes that are running at the time of reboot, their IDs and paths in the file system. If some process interferes with a normal reboot, this is also noted in the log file. Kaspersky Lab experts have noticed that malware is often launched from the "/private/var/db/" or "/private/var/tmp/ " folders, and these paths can be seen in Shutdown. log.
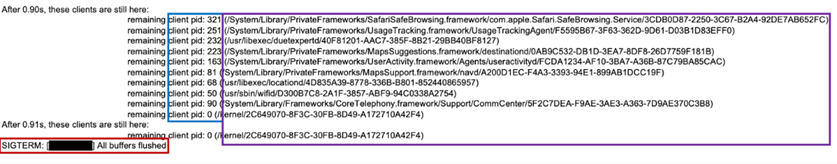
Fragment from the Shutdown.log file
To get a log file, you need to generate a sysdiag archive that contains various system logs and databases. You can do this in the iOS settings, under Settings > Privacy & Security > Analytics & Improvements. The sysdiag archive is about 200-400 MB in size and can be transferred to the analyzing computer. After unpacking the archive, the Shutdown.log file is located in the "\system_logs.logarchive\Extra " folder.
Kaspersky Lab has created several scripts in Python3 that help you extract, analyze, and analyze the Shutdown.log file. Scripts can be used to detect anomalies in the log file – malicious processes running, reboot delays, or unusual paths in the file system. Scripts can also convert a log file to CSV format, decode timestamps, and generate an analysis summary.
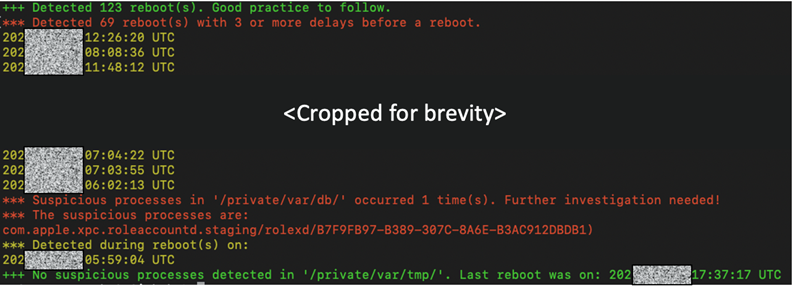
Detecting a Pegasus malware instance
Experts emphasize that analyzing the Shutdown.log file is not a universal way to detect all malware on iOS devices, and that this method depends on how often the user reboots their device. They also continue to study the log file in more detail and across platforms, and hope to create more heuristics from its entries.
Kaspersky Lab encourages users who have interesting samples that can help research, contact the company at [email protected]. The researchers claim that the Shutdown.log file does not contain any personal information, so it can be safely transmitted for analysis.
Note that the fight against malware by rebooting the smartphone was previously mentioned by the GrapheneOS development team, which created the eponymous Android operating system focused on privacy and security. Experts suggested introducing an automatic reboot function in Android, which will complicate the exploitation of firmware vulnerabilities.
Kaspersky Lab specialists shared their experience in analyzing iOS devices infected with Pegasus spyware from the Israeli company NSO Group. Malicious programs were found to leave traces in the system Shutdown.log file. The developed method can help detect not only Pegasus, but also other malicious programs, such as QuaDream's Reign and Cytrox's Predator, which use similar paths in the file system.
Shutdown. log is a text log file that is created on iOS devices every time they reboot. It records information about the processes that are running at the time of reboot, their IDs and paths in the file system. If some process interferes with a normal reboot, this is also noted in the log file. Kaspersky Lab experts have noticed that malware is often launched from the "/private/var/db/" or "/private/var/tmp/ " folders, and these paths can be seen in Shutdown. log.

Fragment from the Shutdown.log file
To get a log file, you need to generate a sysdiag archive that contains various system logs and databases. You can do this in the iOS settings, under Settings > Privacy & Security > Analytics & Improvements. The sysdiag archive is about 200-400 MB in size and can be transferred to the analyzing computer. After unpacking the archive, the Shutdown.log file is located in the "\system_logs.logarchive\Extra " folder.
Kaspersky Lab has created several scripts in Python3 that help you extract, analyze, and analyze the Shutdown.log file. Scripts can be used to detect anomalies in the log file – malicious processes running, reboot delays, or unusual paths in the file system. Scripts can also convert a log file to CSV format, decode timestamps, and generate an analysis summary.

Detecting a Pegasus malware instance
Experts emphasize that analyzing the Shutdown.log file is not a universal way to detect all malware on iOS devices, and that this method depends on how often the user reboots their device. They also continue to study the log file in more detail and across platforms, and hope to create more heuristics from its entries.
Kaspersky Lab encourages users who have interesting samples that can help research, contact the company at [email protected]. The researchers claim that the Shutdown.log file does not contain any personal information, so it can be safely transmitted for analysis.
Note that the fight against malware by rebooting the smartphone was previously mentioned by the GrapheneOS development team, which created the eponymous Android operating system focused on privacy and security. Experts suggested introducing an automatic reboot function in Android, which will complicate the exploitation of firmware vulnerabilities.
