Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
Will the call to ban spyware be implemented?
According to a joint report by human rights organizations Access Now and Citizen Lab , the phones of 35 journalists, activists, human rights defenders and civil society representatives in Jordan were attacked using the Pegasus spyware of the Israeli company NSO Group.
A total of 35 cases of Pegasus infection attempts were confirmed, and 6 devices were successfully infected with spyware. It is estimated that the attacks were carried out starting in 2019 and ending in September 2023.
Pegasus has targeted the following groups of individuals:
Some of the attacks were carried out by disguising themselves as journalists offering interviews or comments, while malicious links to Pegasus were hidden between the lines in the message text itself. In one case, the victim received a WhatsApp message from a man who identified himself as a journalist, who asked for a comment about Jordan's new cybercrime law and its impact on freedoms in the country.
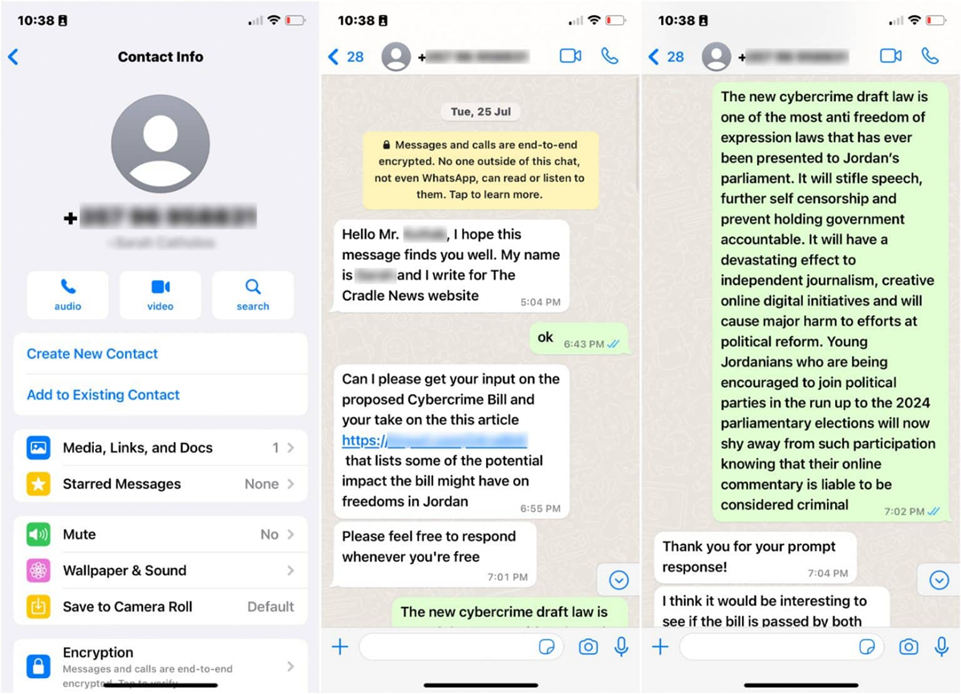
Screenshots of the conversation with the victim
It is noted that some victims were exposed to repeated infections, which underlines the persistent nature of the targeted surveillance campaign.
NSO Group claims that the firm's cyber intelligence technology enables government agencies and law enforcement agencies to fulfill their core responsibilities of preventing violence and ensuring public safety, including by breaking encryption in communication applications without conducting mass surveillance or gaining backdoor access to all users ' devices.
However, the attacks on members of Jordan's civil society demonstrate continued abuse, contrary to the company's claims. In particular, Zero-Click exploits of Apple iOS, such as BLASTPASS , FORCEDENTRY , FINDMYPWN, and PWNYOURHOME were used to bypass security mechanisms and deliver Pegasus using social engineering, including spreading malicious links via WhatsApp and SMS.
Access Now calls on world governments, including the Jordanian one, to stop using such tools and impose a moratorium on their sale until adequate countermeasures are taken. Surveillance technologies and cyberweapons, such as NSO Group's Pegasus, are used to target human rights defenders and journalists, threatening their rights to privacy, freedom of expression, association and peaceful assembly, as well as leading to self-censorship and the cessation of activist or journalistic activities for fear of reprisals.
According to a joint report by human rights organizations Access Now and Citizen Lab , the phones of 35 journalists, activists, human rights defenders and civil society representatives in Jordan were attacked using the Pegasus spyware of the Israeli company NSO Group.
A total of 35 cases of Pegasus infection attempts were confirmed, and 6 devices were successfully infected with spyware. It is estimated that the attacks were carried out starting in 2019 and ending in September 2023.
Pegasus has targeted the following groups of individuals:
- NGO representatives – 4 people.
- Lawyers – 8 people.
- Journalists and media employees – 16 people.
- Activists – 5 people.
- Politicians – 1 person.
- IT technology workers – 1 person.
Some of the attacks were carried out by disguising themselves as journalists offering interviews or comments, while malicious links to Pegasus were hidden between the lines in the message text itself. In one case, the victim received a WhatsApp message from a man who identified himself as a journalist, who asked for a comment about Jordan's new cybercrime law and its impact on freedoms in the country.

Screenshots of the conversation with the victim
It is noted that some victims were exposed to repeated infections, which underlines the persistent nature of the targeted surveillance campaign.
NSO Group claims that the firm's cyber intelligence technology enables government agencies and law enforcement agencies to fulfill their core responsibilities of preventing violence and ensuring public safety, including by breaking encryption in communication applications without conducting mass surveillance or gaining backdoor access to all users ' devices.
However, the attacks on members of Jordan's civil society demonstrate continued abuse, contrary to the company's claims. In particular, Zero-Click exploits of Apple iOS, such as BLASTPASS , FORCEDENTRY , FINDMYPWN, and PWNYOURHOME were used to bypass security mechanisms and deliver Pegasus using social engineering, including spreading malicious links via WhatsApp and SMS.
Access Now calls on world governments, including the Jordanian one, to stop using such tools and impose a moratorium on their sale until adequate countermeasures are taken. Surveillance technologies and cyberweapons, such as NSO Group's Pegasus, are used to target human rights defenders and journalists, threatening their rights to privacy, freedom of expression, association and peaceful assembly, as well as leading to self-censorship and the cessation of activist or journalistic activities for fear of reprisals.

