chushpan
Professional
- Messages
- 1,356
- Reaction score
- 1,632
- Points
- 113
Hello everyone. Perhaps I'll start from the beginning. In order to better understand how any Antifraud works, you need to answer the most important questions first. How does the Internet work? What exactly happens when you request a page in your browser? How exactly does traffic flow through the network? In this article, I want to dispel all the prejudices about how the network works, and explain which part of your system is responsible for which fingerprint (let me remind you that we have three of them: JA3+HTTP2+TCP).
Why exactly three fingerprints? In general, all traffic that goes around the global network is subject to the standard OSI model.
From this picture it is clear that the traffic you send (to get the page) consists of several levels and each level has its own goals and tasks - this is called encapsulation. That is, when you send some request - it can be decomposed from the beginning to the application level - this will be the request itself - then to the presentation level, session level and so on. In the future, we will be interested in the levels: Application, Session and Transport. (We will not be interested in the levels: Channel and physical - since they are needed for internal interaction of the network - the end host will not take them into account).
Many people ask me: Can a host see the MAC address of my router/system, etc.? - I answer: No, it is impossible. Because the MAC is at the channel level and only your router sees the MAC, your MAC address, and the provider's router sees the MAC of your router. Thus, the MAC address is seen ONLY by NEIGHBORING DEVICES. That is, it is impossible according to technology. Well, if it were not so, then this would be a hole in the global Internet from a security point of view.
We'll talk about how exactly different sites can identify your device now.
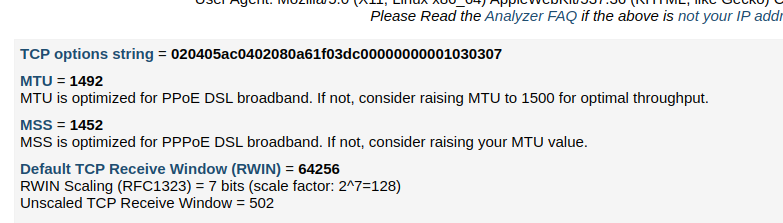
speedguide sample print
What is the fingerprint actually made of? Let's start with what does a TCP packet actually look like?
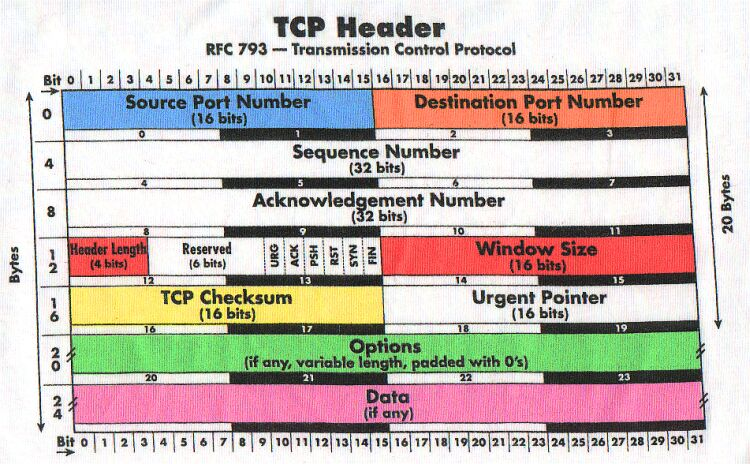
TCP packet headers
The first and most important thing that a TCP fingerprint consists of is, of course, TCP options
Examples of TCP options (fingerprints):
It is clear that they are all different. ( More examples here )
Absolutely all antifraud systems look at your MTU / MSS (MTU = MSS +40) , this is the first signal if a person uses VPN - since when using VPN in some cases MTU becomes smaller (by default it is 1500), for example https ://ip-score.com/ - if you log in with VPN and you have a small MTU, for example 1400, then the system will say that you are using VPN - therefore it is important for us to change this indicator to the maximum (It is important to remember that when using VPN - MTU cannot be more than 1500-40 = 1460 - because these 40 bytes are needed to use the VPN itself) More details about VPN detection through these parameters here. In our proxy, you can replace the MSS value (this is the same indicator only -40 bytes that is prescribed in TCP options) - and MTU will be calculated itself.
WindowSize is how many unacknowledged bytes of data the client can accept.
TTL is a parameter that determines the maximum lifetime of a packet in the network or the number of routers it can pass through. When a packet passes through a router, its TTL is reduced by one. If the TTL reaches zero, the packet is destroyed.
Antifraud can measure the TTL of a packet coming from a client and compare it to the expected value based on the client's geographic location. If the TTL of a packet is significantly lower than the expected value, this may be a sign that the client is using a VPN. When using a VPN, the TTL of a packet is reduced by an amount corresponding to the number of hops between the client's device and the VPN server.
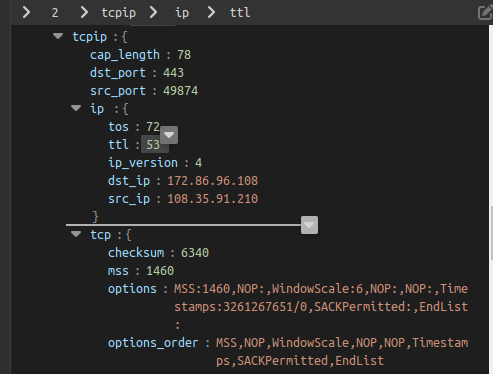
You can read about this in detail here the generally recognized TCP fingerprint: MSS+TCP Options+TTL+TOS+WindowScale. It is issued directly by the OS (Windows\Linux\MacOS\Android\Iphone etc.). But - it happens that they pass through some gateways - for example, a proxy, your fingerprint can change, so it is important to make sure that this fingerprint is exactly the one you want to use.
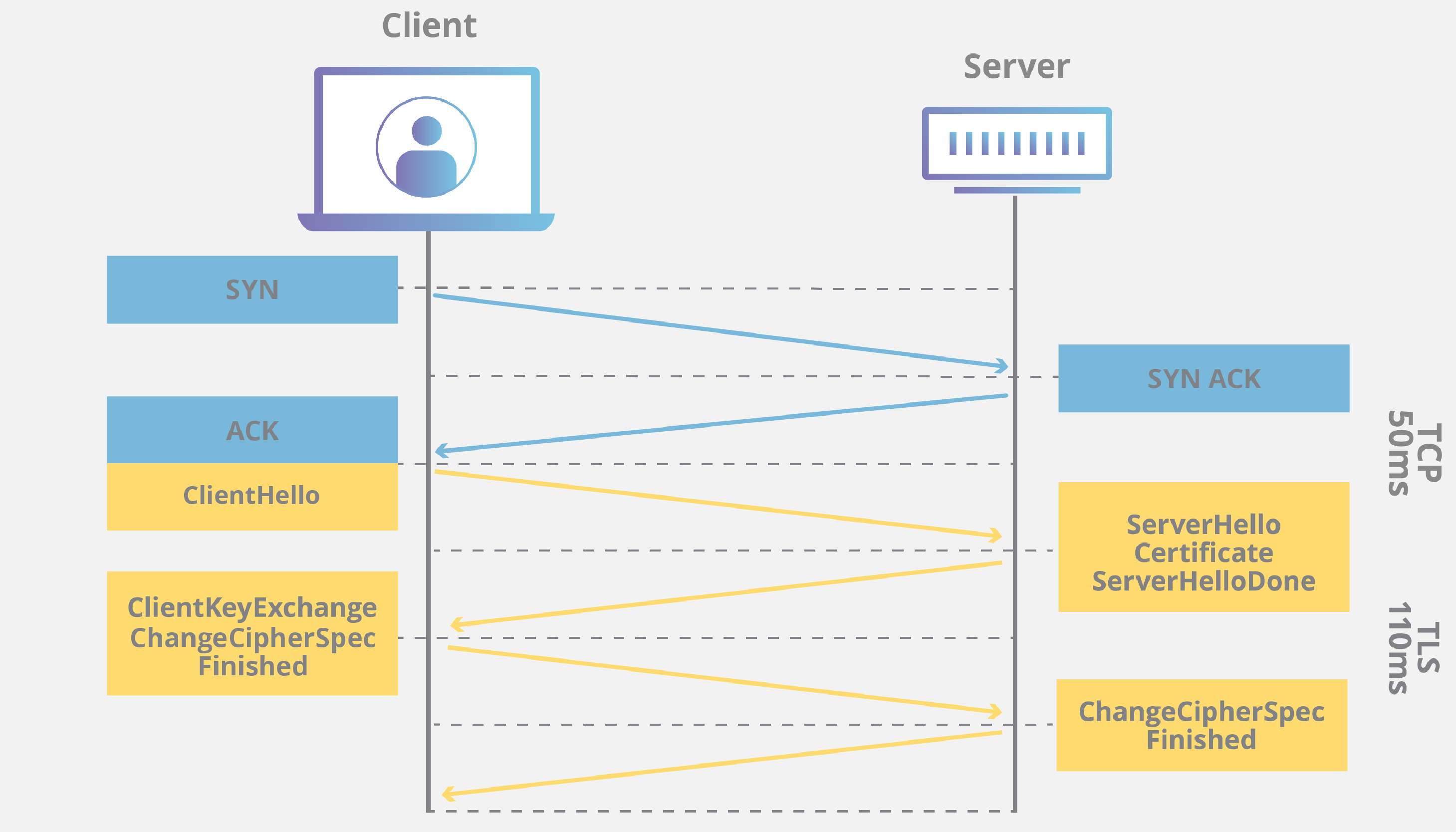
TLS Handshake
That is, in order for an encrypted connection to be established, the server and the client must exchange some packets and agree on what cipher they will use to encrypt messages, what keys to use, etc.
In each TLS connection, the client (that is, us) sends a ClientHello message that looks something like this
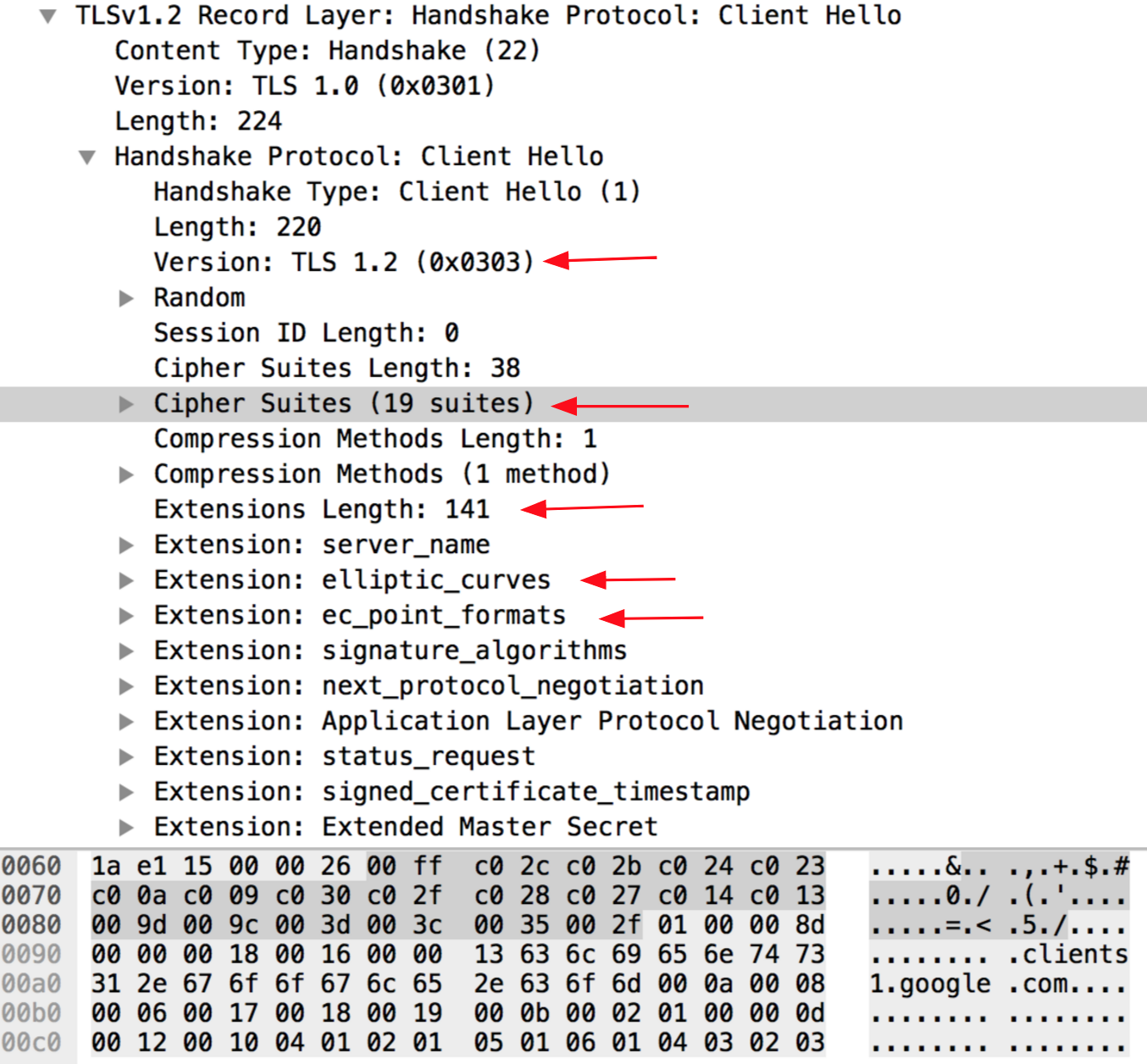
ClearHello
That is, our ClientHello message contains a set of ciphers and other extensions that are in the browser. Each cipher and extension has its own code. Thus, adding these codes together, we get the following print:
Then it turns into MD5 hash and you get something like this 160df3588996dbf66817cc71bba8a903
I have posted examples of fingerprints in a separate table: (See Ja3 Prints). At the end of the table there is a formula - it counts how many unique valuesare in the column (Unique prints) - this way you can understand where which fingerprints are unique. There is also one nuance that only exists in CHROME browsers, this is the GREASE mechanism - it is inside the Extensions field - it mixes up the extensions - thus the fingerprint hash is always different (our proxy can do the same). But the rest of the fingerprint remains unchanged.
You can find out more about these prints here
HTTP2 itself is the next version of the familiar HTTP/1.1 protocol.
Example of http/1.1 request:
Now almost all modern sites support HTTP2. You can verify this in the following way (open the developer console in the browser)
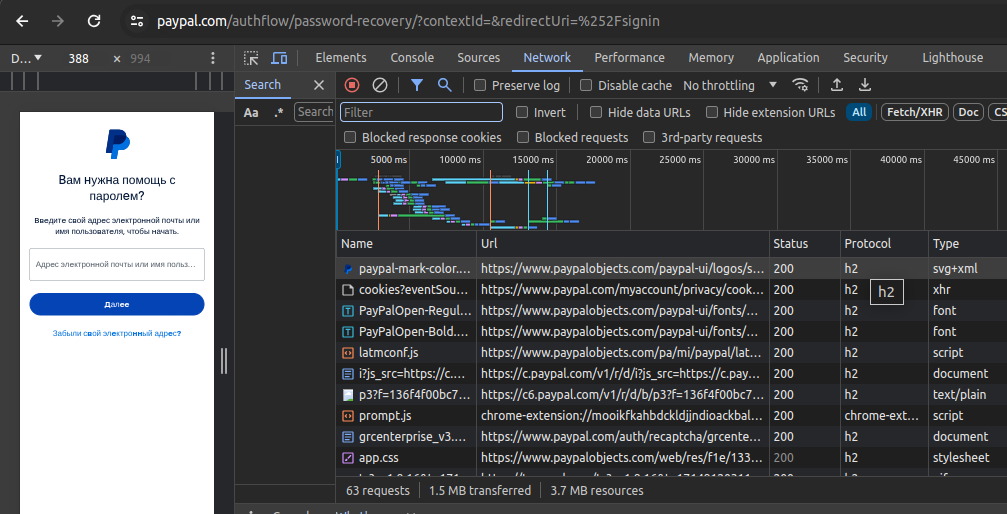
Http2 example
This protocol has several advantages over HTTP1, namely:
We will not go into details. What is more important to us is how this can be used for identification by the antifraud system.
Http2 is a stream. And the stream consists of frames. It is these frames that can be used for identification.
Each of these frames contains information that allows clients to be easily identified. For example, the SETTINGS frame contains parameters that control settings such as the maximum number of simultaneous threads, the maximum number of HTTP headers, the default window size, and server push support. Each HTTP/2 client uses a different set of parameters, and these parameters generally do not change depending on the specific HTTP request being sent.
The WINDOW_UPDATE frame increases the size of the recipient's window. This frame can be used to identify the client, since each client may use a different window size.
The HEADERS frame contains the actual HTTP request from the client to the server. It contains the URI, HTTP method, and client HTTP headers. This frame can also be used to identify the client, since each client can use different sets of headers and different valuesfor these headers.
Examples of prints:
Decoding fingerprints in the table.
You can also read more about these prints here.

Why exactly three fingerprints? In general, all traffic that goes around the global network is subject to the standard OSI model.
From this picture it is clear that the traffic you send (to get the page) consists of several levels and each level has its own goals and tasks - this is called encapsulation. That is, when you send some request - it can be decomposed from the beginning to the application level - this will be the request itself - then to the presentation level, session level and so on. In the future, we will be interested in the levels: Application, Session and Transport. (We will not be interested in the levels: Channel and physical - since they are needed for internal interaction of the network - the end host will not take them into account).
Many people ask me: Can a host see the MAC address of my router/system, etc.? - I answer: No, it is impossible. Because the MAC is at the channel level and only your router sees the MAC, your MAC address, and the provider's router sees the MAC of your router. Thus, the MAC address is seen ONLY by NEIGHBORING DEVICES. That is, it is impossible according to technology. Well, if it were not so, then this would be a hole in the global Internet from a security point of view.
We'll talk about how exactly different sites can identify your device now.
TCP L4 fingerprints
This is the very first fingerprint that can be collected from each user. We have made a special service with which you can view the fingerprint https://fingerprintcheck.work.gd/classify?detail=1 and there is also a third-party service http://www.speedguide.net:8080/
speedguide sample print
What is the fingerprint actually made of? Let's start with what does a TCP packet actually look like?

TCP packet headers
The first and most important thing that a TCP fingerprint consists of is, of course, TCP options
Examples of TCP options (fingerprints):
iPhone OS 17_3_1 MSS:1348,NOP:,WindowScale:12,SACKPermitted:,Timestamps:364032648/0
iPhone OS 17_3_1 MSS:1380,SACKPermitted:,Timestamps:4281595168/0,NOP:,WindowScale:13
iPhone OS 17_4_1 MSS:1388,NOP:,WindowScale:6,NOP:,NOP:,Timestamps:3763022276/0,SACKPermitted:,EndList:
iPhone OS 16_6 MSS:1460,NOP:,WindowScale:8,NOP:,NOP:,SACKPermitted:
Windows MSS:1420,NOP:,WindowScale:8,NOP:,NOP:,SACKPermitted:
It is clear that they are all different. ( More examples here )
Absolutely all antifraud systems look at your MTU / MSS (MTU = MSS +40) , this is the first signal if a person uses VPN - since when using VPN in some cases MTU becomes smaller (by default it is 1500), for example https ://ip-score.com/ - if you log in with VPN and you have a small MTU, for example 1400, then the system will say that you are using VPN - therefore it is important for us to change this indicator to the maximum (It is important to remember that when using VPN - MTU cannot be more than 1500-40 = 1460 - because these 40 bytes are needed to use the VPN itself) More details about VPN detection through these parameters here. In our proxy, you can replace the MSS value (this is the same indicator only -40 bytes that is prescribed in TCP options) - and MTU will be calculated itself.

WindowSize is how many unacknowledged bytes of data the client can accept.
TTL is a parameter that determines the maximum lifetime of a packet in the network or the number of routers it can pass through. When a packet passes through a router, its TTL is reduced by one. If the TTL reaches zero, the packet is destroyed.
Antifraud can measure the TTL of a packet coming from a client and compare it to the expected value based on the client's geographic location. If the TTL of a packet is significantly lower than the expected value, this may be a sign that the client is using a VPN. When using a VPN, the TTL of a packet is reduced by an amount corresponding to the number of hops between the client's device and the VPN server.

You can read about this in detail here the generally recognized TCP fingerprint: MSS+TCP Options+TTL+TOS+WindowScale. It is issued directly by the OS (Windows\Linux\MacOS\Android\Iphone etc.). But - it happens that they pass through some gateways - for example, a proxy, your fingerprint can change, so it is important to make sure that this fingerprint is exactly the one you want to use.
JA3 fingerprints (TLS - L6)
What are these fingerprints anyway and where do they come from? When you go to a http S site, it means that you want to use a secure protocol, ie TLS (Transport Layer Security). According to the protocol rules, the connection should look like this:
TLS Handshake
That is, in order for an encrypted connection to be established, the server and the client must exchange some packets and agree on what cipher they will use to encrypt messages, what keys to use, etc.
In each TLS connection, the client (that is, us) sends a ClientHello message that looks something like this

ClearHello
That is, our ClientHello message contains a set of ciphers and other extensions that are in the browser. Each cipher and extension has its own code. Thus, adding these codes together, we get the following print:
769.47–53–5–10–49161–49162–49171–49172–50–56–19–4.0–10–11.23–24–25.0
Then it turns into MD5 hash and you get something like this 160df3588996dbf66817cc71bba8a903
I have posted examples of fingerprints in a separate table: (See Ja3 Prints). At the end of the table there is a formula - it counts how many unique valuesare in the column (Unique prints) - this way you can understand where which fingerprints are unique. There is also one nuance that only exists in CHROME browsers, this is the GREASE mechanism - it is inside the Extensions field - it mixes up the extensions - thus the fingerprint hash is always different (our proxy can do the same). But the rest of the fingerprint remains unchanged.
You can find out more about these prints here
HTTP2 fingerprints aka Akamai. L7
HTTP2 fingerprint This is another method of user identification that works at the application level - along with User-Agent, JS fingerprint, Canvas, WebGL, etc.HTTP2 itself is the next version of the familiar HTTP/1.1 protocol.
Example of http/1.1 request:
Code:
GET / HTTP/1.1Now almost all modern sites support HTTP2. You can verify this in the following way (open the developer console in the browser)

Http2 example
This protocol has several advantages over HTTP1, namely:
- Multiplexing - multiple requests and responses can simultaneously use one TCP connection, which reduces the time it takes to receive sites with a large number of resources (images, scripts, etc.).
- Prioritization - HTTP/2 supports prioritization of certain requests and responses.
- Server push - in HTTP/2, the server can send resources to the client before the client requests them.
We will not go into details. What is more important to us is how this can be used for identification by the antifraud system.
Http2 is a stream. And the stream consists of frames. It is these frames that can be used for identification.
- SETTINGS: This frame is the first frame sent by the client and contains HTTP/2-specific settings. It is part of stream 0, which is the root stream. No resource is retrieved in stream 0.
- WINDOW_UPDATE: Increases the size of the recipient window.
- HEADERS: Contains the actual request from the client to the server. It contains the URI, HTTP method, and client HTTP headers.
Each of these frames contains information that allows clients to be easily identified. For example, the SETTINGS frame contains parameters that control settings such as the maximum number of simultaneous threads, the maximum number of HTTP headers, the default window size, and server push support. Each HTTP/2 client uses a different set of parameters, and these parameters generally do not change depending on the specific HTTP request being sent.
The WINDOW_UPDATE frame increases the size of the recipient's window. This frame can be used to identify the client, since each client may use a different window size.
The HEADERS frame contains the actual HTTP request from the client to the server. It contains the URI, HTTP method, and client HTTP headers. This frame can also be used to identify the client, since each client can use different sets of headers and different valuesfor these headers.
Examples of prints:
1:65536,2:0,4:6291456,6:262144|15663105|0|m,a,s,p 1:65536,3:1000,4:6291456,6:262144|15663105|0|m,a ,s,p 2:0.4:2097152.3:100|10485760|0|m,s,p,a
4:2097152,3:100|10485760|0|m,s,p,a
Decoding fingerprints in the table.
You can also read more about these prints here.

