Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,095
- Points
- 113
A new scam scheme is targeting Windows and Mac users.
The scammers have once again attracted the attention of security researchers with their brazen use of Google products to spread malware. Recently, they began disguising their intentions as ads related to the company's products, such as Google Authenticator, and even created a fake Google homepage to which they redirected victims. This was reported by Malwarebytes experts.
To implement their scheme, the attackers used Google Looker Studio, with which they blocked the browsers of Windows and Mac users. Particular attention should be paid to the fact that the fraudsters used the technology of dynamic insertion of keywords into ads. This allowed them to effectively target Google's entire product portfolio by creating ads with a URL that looked like an official one, such as "lookerstudio.google.com."

After the first wave of ads was identified and blocked, the attackers quickly registered a new ad account and continued to place malicious ads aimed at Google Maps users.
One of the interesting features of this attack is the use of Looker Studio to create a fake Google homepage, which is just a large image disguised as a regular search page.

When interacting with this page, users were redirected to rogue sites that tried to lock their browsers and showed fake warnings on behalf of Microsoft or Apple.
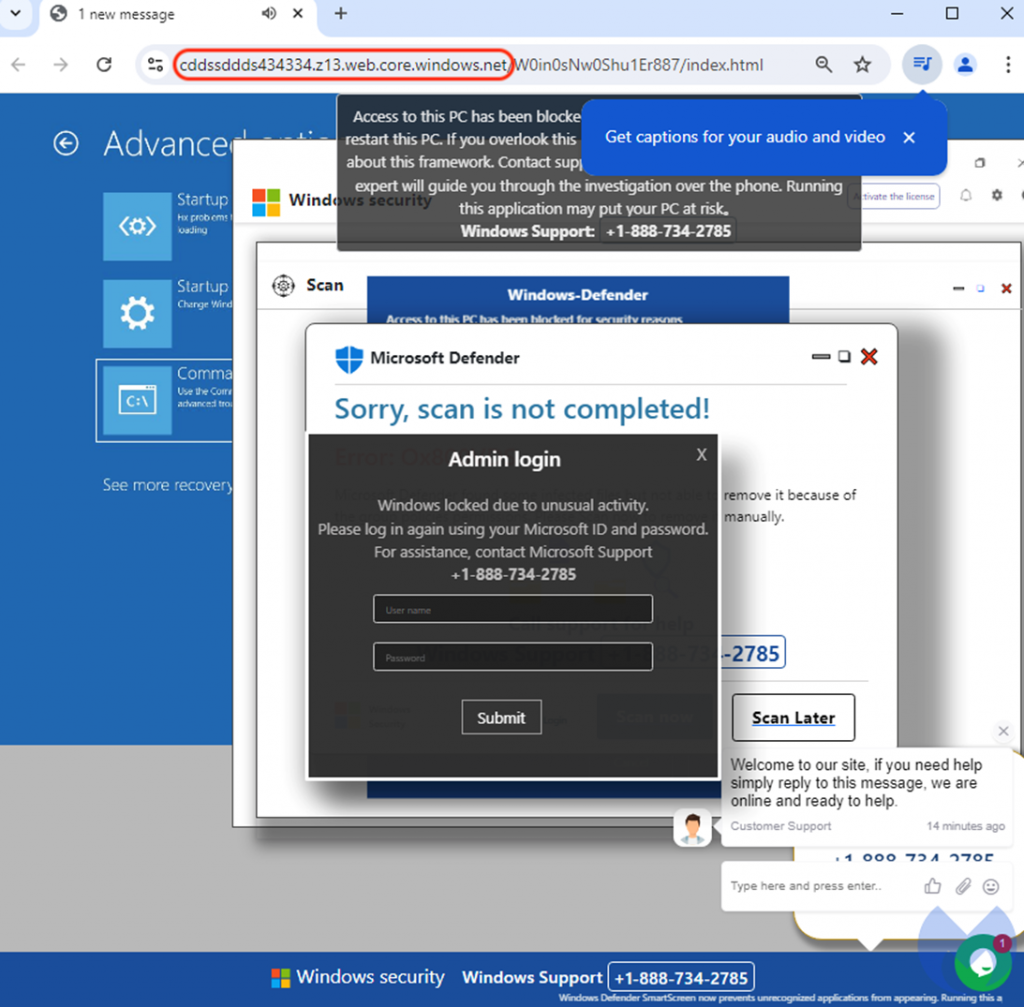
These fake warnings encouraged users to call bogus support services, where, under the guise of technical assistance, the attackers tried to scam victims out of money by offering to pay for "repairs" using gift cards or direct deposits.
The entire mechanism of fraud was built on the use of cloud services such as Microsoft Azure, which made it difficult to identify and block malicious activity. Despite this, Malwarebytes was able to prevent the attack by using state-of-the-art detection methods.
This case once again demonstrates how inventive and dangerous attackers can be, using legitimate platforms and services for their own purposes.
Source
The scammers have once again attracted the attention of security researchers with their brazen use of Google products to spread malware. Recently, they began disguising their intentions as ads related to the company's products, such as Google Authenticator, and even created a fake Google homepage to which they redirected victims. This was reported by Malwarebytes experts.
To implement their scheme, the attackers used Google Looker Studio, with which they blocked the browsers of Windows and Mac users. Particular attention should be paid to the fact that the fraudsters used the technology of dynamic insertion of keywords into ads. This allowed them to effectively target Google's entire product portfolio by creating ads with a URL that looked like an official one, such as "lookerstudio.google.com."

After the first wave of ads was identified and blocked, the attackers quickly registered a new ad account and continued to place malicious ads aimed at Google Maps users.
One of the interesting features of this attack is the use of Looker Studio to create a fake Google homepage, which is just a large image disguised as a regular search page.

When interacting with this page, users were redirected to rogue sites that tried to lock their browsers and showed fake warnings on behalf of Microsoft or Apple.

These fake warnings encouraged users to call bogus support services, where, under the guise of technical assistance, the attackers tried to scam victims out of money by offering to pay for "repairs" using gift cards or direct deposits.
The entire mechanism of fraud was built on the use of cloud services such as Microsoft Azure, which made it difficult to identify and block malicious activity. Despite this, Malwarebytes was able to prevent the attack by using state-of-the-art detection methods.
This case once again demonstrates how inventive and dangerous attackers can be, using legitimate platforms and services for their own purposes.
Source

