Friend
Professional
- Messages
- 2,675
- Reaction score
- 1,059
- Points
- 113
Muddywater uses fear as a hacking tool.
Israeli media reported that on August 4, Israelis received disturbing emails on their e-boxes that allegedly contain "recommendations for the safety of citizens" from the Israel Defense Forces (IDF).
The emails, written in English, contained a link to "important materials", but in fact it was a phishing attack aimed at stealing data. The link is intended for downloading a ZIP archive from cloud storage, which delivers malware for remote capture of the device.
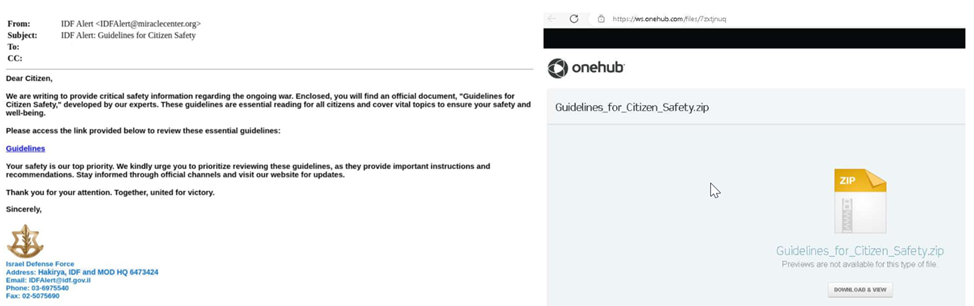
Example of a phishing email (left) and an infected archive (right)
Israel attributed the attack to the Iranian government group MuddyWater, which intensified after the killing of Hamas leader Ismail Haniyeh in Tehran on July 31, which increased tensions in Israel.
After Haniyeh was eliminated, Iranian hackers launched active phishing attacks on Israeli companies. However, the hasty actions of the attackers made the campaign easily recognizable: letters in English, re-used infrastructure and methods that had already been disclosed earlier allowed the Israeli intelligence services to quickly identify the source of the threat.
The main goal of the campaign is to create a sense of fear and uncertainty among Israelis, to force them to click on malicious links. Hackers took advantage of the natural human desire to protect themselves and their loved ones to break into electronic devices and steal confidential data. Thus, in addition to the cyberattack itself, the campaign is aimed at destabilizing the psychological state of Israeli citizens. The Israeli government previously issued a warning about Muddywater phishing attacks in June of this year.
Cybercriminals from MuddyWater often conduct phishing campaigns through compromised corporate email accounts, which leads to the installation of legitimate remote management tools such as Atera Agent and Screen Connect. In addition, hackers have recently started using a new BugSleep backdoor designed to attack Israeli organizations.
Source
Israeli media reported that on August 4, Israelis received disturbing emails on their e-boxes that allegedly contain "recommendations for the safety of citizens" from the Israel Defense Forces (IDF).
The emails, written in English, contained a link to "important materials", but in fact it was a phishing attack aimed at stealing data. The link is intended for downloading a ZIP archive from cloud storage, which delivers malware for remote capture of the device.

Example of a phishing email (left) and an infected archive (right)
Israel attributed the attack to the Iranian government group MuddyWater, which intensified after the killing of Hamas leader Ismail Haniyeh in Tehran on July 31, which increased tensions in Israel.
After Haniyeh was eliminated, Iranian hackers launched active phishing attacks on Israeli companies. However, the hasty actions of the attackers made the campaign easily recognizable: letters in English, re-used infrastructure and methods that had already been disclosed earlier allowed the Israeli intelligence services to quickly identify the source of the threat.
The main goal of the campaign is to create a sense of fear and uncertainty among Israelis, to force them to click on malicious links. Hackers took advantage of the natural human desire to protect themselves and their loved ones to break into electronic devices and steal confidential data. Thus, in addition to the cyberattack itself, the campaign is aimed at destabilizing the psychological state of Israeli citizens. The Israeli government previously issued a warning about Muddywater phishing attacks in June of this year.
Cybercriminals from MuddyWater often conduct phishing campaigns through compromised corporate email accounts, which leads to the installation of legitimate remote management tools such as Atera Agent and Screen Connect. In addition, hackers have recently started using a new BugSleep backdoor designed to attack Israeli organizations.
Source
