CarderPlanet
Professional
- Messages
- 2,549
- Reaction score
- 724
- Points
- 113
Why did Iranian hackers use Exchange servers in attacks?
Security researchers from ESET said that Israeli organizations were targeted in two different campaigns organized by the Iranian OilRig group in 2021 and 2022.
The campaigns, dubbed "Outer Space" and "Juicy Mix", involved the use of two previously documented initial backdoors under the names Solar and Mango. The tools were used to collect sensitive information from major browsers and the Windows Credential Manager. According to ESET researchers, both backdoors were deployed using VBS droppers, presumably distributed through phishing emails.
OilRig (also known as APT34, Cobalt Gypsy, Hazel Sandstorm, and Helix Kitten) is the name given to a group affiliated with the Iranian Ministry of Intelligence and Security (MOIS). Active since 2014, the group has used a wide range of tools to steal information.
Outer Space Campaign
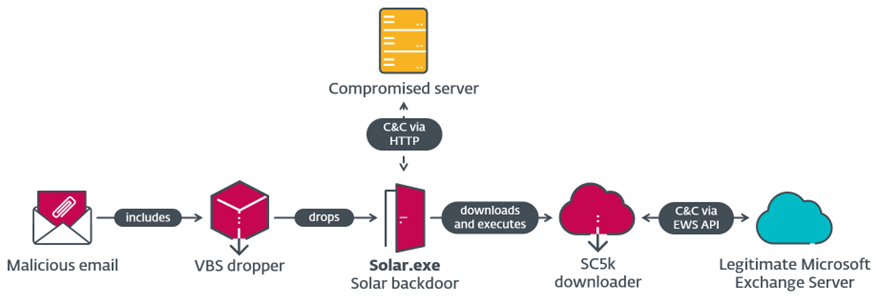
Outer Space Campaign Infection Chain
During the Outer Space 2021 campaign, OilRig hackers compromised an Israeli recruitment site and used it as a Command and Control (C2) server for Solar, a C#/.NET backdoor capable of uploading/executing files and collecting information.
Solar also serves as a means to deploy the SampleCheck5000 loader (or SC5k), which uses the Office Exchange Web Services (EWS) API to download additional execution tools, as well as a utility for exfiltrating data from the Chrome browser called MKG.
Juicy Mix Campaign
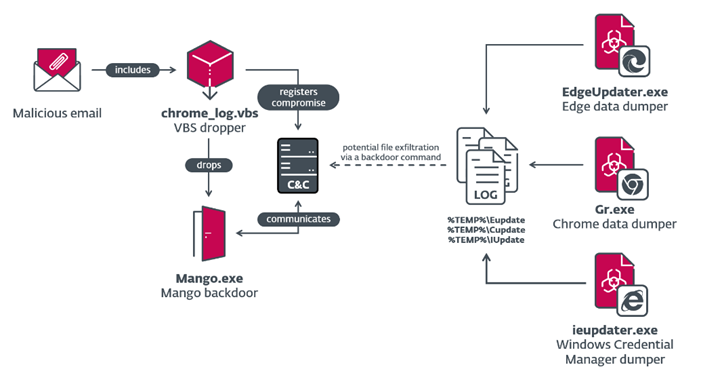
Juicy Mix Campaign Infection Chain
The 2022 campaign included the use of Mango, an improved version of Solar that includes additional features and obfuscation techniques. The tool is able to collect sensitive information from major browsers and the Windows Credential Manager.
The tool is designed for more efficient and stealthy data collection and command execution on infected systems. Mango, like Solar, uses sophisticated communication methods to ensure the secrecy of its activity. Hackers compromised a legitimate Israeli employment portal as a C2 server.
OilRig continues to innovate and create new implants with backdoor-like capabilities, while finding new ways to execute commands on remote systems. The group is deploying a set of custom post-compromise tools that are used to collect credentials, cookies, and browsing history from major browsers, as well as data from the Windows Credential Manager, the ESET researchers concluded.
The observed use of Iran's hacking capabilities indicates pragmatic cyber operations that pursue three strategic goals that coincide with Iran's geopolitical goals.
In addition to the political reasons behind the cyber attacks on Israel, Iran has also recently accused Israel of trying to undermine the country's ballistic missile program through defective foreign parts that can explode, damaging or destroying the weapon before it is used.
Security researchers from ESET said that Israeli organizations were targeted in two different campaigns organized by the Iranian OilRig group in 2021 and 2022.
The campaigns, dubbed "Outer Space" and "Juicy Mix", involved the use of two previously documented initial backdoors under the names Solar and Mango. The tools were used to collect sensitive information from major browsers and the Windows Credential Manager. According to ESET researchers, both backdoors were deployed using VBS droppers, presumably distributed through phishing emails.
OilRig (also known as APT34, Cobalt Gypsy, Hazel Sandstorm, and Helix Kitten) is the name given to a group affiliated with the Iranian Ministry of Intelligence and Security (MOIS). Active since 2014, the group has used a wide range of tools to steal information.
Outer Space Campaign

Outer Space Campaign Infection Chain
During the Outer Space 2021 campaign, OilRig hackers compromised an Israeli recruitment site and used it as a Command and Control (C2) server for Solar, a C#/.NET backdoor capable of uploading/executing files and collecting information.
Solar also serves as a means to deploy the SampleCheck5000 loader (or SC5k), which uses the Office Exchange Web Services (EWS) API to download additional execution tools, as well as a utility for exfiltrating data from the Chrome browser called MKG.
- After getting to the remote Exchange server, SC5k retrieves all emails in the Drafts directory and sorts them by date, saving only drafts with attachments.
- Then SC5k goes through each draft with an attachment and looks for JSON attachments containing data in the email body.
- The loader extracts the value from the data in the JSON file, decodes the value to base64, decrypts the value, and calls cmd.exe to execute the received command line. The results of the command execution are processed and sent back to the operators via a new Exchange message, saving it as a draft.
Juicy Mix Campaign

Juicy Mix Campaign Infection Chain
The 2022 campaign included the use of Mango, an improved version of Solar that includes additional features and obfuscation techniques. The tool is able to collect sensitive information from major browsers and the Windows Credential Manager.
The tool is designed for more efficient and stealthy data collection and command execution on infected systems. Mango, like Solar, uses sophisticated communication methods to ensure the secrecy of its activity. Hackers compromised a legitimate Israeli employment portal as a C2 server.
OilRig continues to innovate and create new implants with backdoor-like capabilities, while finding new ways to execute commands on remote systems. The group is deploying a set of custom post-compromise tools that are used to collect credentials, cookies, and browsing history from major browsers, as well as data from the Windows Credential Manager, the ESET researchers concluded.
The observed use of Iran's hacking capabilities indicates pragmatic cyber operations that pursue three strategic goals that coincide with Iran's geopolitical goals.
In addition to the political reasons behind the cyber attacks on Israel, Iran has also recently accused Israel of trying to undermine the country's ballistic missile program through defective foreign parts that can explode, damaging or destroying the weapon before it is used.

