Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,321
- Points
- 113
How Google Cloud abuse affects your business.
In Latin America, a financially motivated hacker group codenamed FLUXROOT has been identified, which uses serverless Google Cloud projects to organize phishing attacks. The attacks are aimed at stealing credentials, highlighting the misuse of the cloud computing model for malicious purposes.
According to Google, serverless architectures are attractive to developers and businesses because of their flexibility, cost-effectiveness, and ease of use. The same characteristics make them attractive for attackers who use these services to deliver and interact with their malware, place and direct users to phishing pages, and execute malicious scripts specifically adapted for a serverless environment.
The campaign used the URLs of Google Cloud containers to host phishing pages aimed at collecting user credentials of Mercado Pago, a popular online payment platform in Latin America.
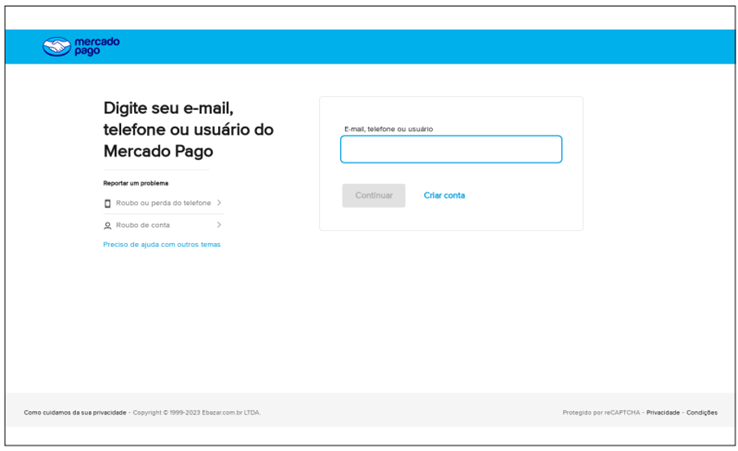
Mercado Pago Phishing Page
FLUXROOT is known for distributing the Grandoreiro banking Trojan, and the group previously used Microsoft Azure and Dropbox cloud services to distribute its malware.
In addition to FLUXROOT, the Google Cloud infrastructure was also used by another PINEAPPLE hacker group to distribute Astaroth malware (Guildma). The attacks target Brazilian users.
PINEAPPLE created container URLs on legitimate Google Cloud domains (cloudfunctions[.]net and run. app) to redirect victims to malicious resources where the Astaroth infection occurred.
Attackers also tried to bypass mail gateway protection by using mail forwarding services that do not discard messages with failed Sender Policy Framework (SPF) entries, or by adding unexpected data to the SMTP Return-Path field to trigger a DNS query timeout and cause email authentication verification to fail.
Google has taken steps to reduce hacker activity by removing malicious Google Cloud projects and updating its safe browsing lists. The abuse of cloud services and infrastructure by hackers is a consequence of the active introduction of cloud technologies in various industries.
Source
In Latin America, a financially motivated hacker group codenamed FLUXROOT has been identified, which uses serverless Google Cloud projects to organize phishing attacks. The attacks are aimed at stealing credentials, highlighting the misuse of the cloud computing model for malicious purposes.
According to Google, serverless architectures are attractive to developers and businesses because of their flexibility, cost-effectiveness, and ease of use. The same characteristics make them attractive for attackers who use these services to deliver and interact with their malware, place and direct users to phishing pages, and execute malicious scripts specifically adapted for a serverless environment.
The campaign used the URLs of Google Cloud containers to host phishing pages aimed at collecting user credentials of Mercado Pago, a popular online payment platform in Latin America.

Mercado Pago Phishing Page
FLUXROOT is known for distributing the Grandoreiro banking Trojan, and the group previously used Microsoft Azure and Dropbox cloud services to distribute its malware.
In addition to FLUXROOT, the Google Cloud infrastructure was also used by another PINEAPPLE hacker group to distribute Astaroth malware (Guildma). The attacks target Brazilian users.
PINEAPPLE created container URLs on legitimate Google Cloud domains (cloudfunctions[.]net and run. app) to redirect victims to malicious resources where the Astaroth infection occurred.
Attackers also tried to bypass mail gateway protection by using mail forwarding services that do not discard messages with failed Sender Policy Framework (SPF) entries, or by adding unexpected data to the SMTP Return-Path field to trigger a DNS query timeout and cause email authentication verification to fail.
Google has taken steps to reduce hacker activity by removing malicious Google Cloud projects and updating its safe browsing lists. The abuse of cloud services and infrastructure by hackers is a consequence of the active introduction of cloud technologies in various industries.
Source

