Carding 4 Carders
Professional
- Messages
- 2,728
- Reaction score
- 1,574
- Points
- 113
The imperfection of Apple processors allows you to imperceptibly siphon off all confidential user data.
Scientists have developed an attack that forces the Safari browser to reveal passwords, the content of Gmail messages and other secrets, exploiting a vulnerability in the A and M series processors used in modern iOS and macOS devices.
A Side-channel attack, called iLeakage, is quite practical and requires minimal resources to perform, but it requires a deep study of Apple hardware and experience in exploiting vulnerabilities in the practical implementation of the cryptosystem. The main vulnerability mechanism is related to speculative execution, a function designed to increase the performance of modern processors.
The iLeakage attack is implemented in the form of a website, which also contains videos demonstrating different attack options. When a user of a vulnerable macOS or iOS device visits a site, iLeakage uses JavaScript to secretly open another site of the attacker's choice and restore the site content displayed in the pop-up window. Researchers have successfully used iLeakage to get their YouTube browsing history, Gmail mailbox content, and auto-populated passwords.
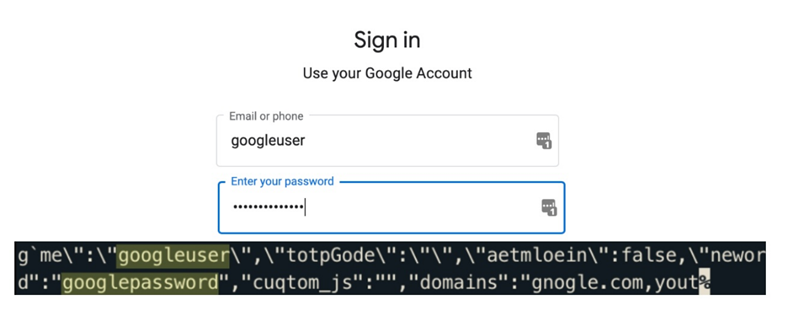
Google Login page-Credentials are automatically filled in by the password manager (top). Credentials are stolen by an attacker (from below).
While iLeakage only works on Macs when using Safari, iPhones and iPads can be attacked when using any browser, as they are all based on Apple's WebKit engine. An Apple spokesperson said the company is aware of the vulnerability and plans to address it in an upcoming software update.
WebKit features and the structure of the A - and M-series processors made it possible to bypass existing security measures designed to protect against speculative execution attacks. Weaknesses in the security implementation allowed iLeakage to overcome it.
iLeakage demonstrates several new features:
In order for the attack to work, the affected computer must first visit the iLeakage website. If you log in to your account on a compromised website and the attacker's site at the same time, it will take about 5 minutes to analyze the visiting device. iLeakage can then force the browser to open any other site and start transmitting certain data at a rate of 24 to 34 bits per second.
Stealing Instagram and LastPass passwords
Despite the technical complexity and the need for deep knowledge to implement an attack, the probability that this vulnerability will be used in real attacks in the near future is extremely low. Apple is expected to release a fix before the iLeakage attack becomes a real threat.
Scientists have developed an attack that forces the Safari browser to reveal passwords, the content of Gmail messages and other secrets, exploiting a vulnerability in the A and M series processors used in modern iOS and macOS devices.
A Side-channel attack, called iLeakage, is quite practical and requires minimal resources to perform, but it requires a deep study of Apple hardware and experience in exploiting vulnerabilities in the practical implementation of the cryptosystem. The main vulnerability mechanism is related to speculative execution, a function designed to increase the performance of modern processors.
The iLeakage attack is implemented in the form of a website, which also contains videos demonstrating different attack options. When a user of a vulnerable macOS or iOS device visits a site, iLeakage uses JavaScript to secretly open another site of the attacker's choice and restore the site content displayed in the pop-up window. Researchers have successfully used iLeakage to get their YouTube browsing history, Gmail mailbox content, and auto-populated passwords.

Google Login page-Credentials are automatically filled in by the password manager (top). Credentials are stolen by an attacker (from below).
While iLeakage only works on Macs when using Safari, iPhones and iPads can be attacked when using any browser, as they are all based on Apple's WebKit engine. An Apple spokesperson said the company is aware of the vulnerability and plans to address it in an upcoming software update.
WebKit features and the structure of the A - and M-series processors made it possible to bypass existing security measures designed to protect against speculative execution attacks. Weaknesses in the security implementation allowed iLeakage to overcome it.
iLeakage demonstrates several new features:
- ability to bypass protection using Safari on A-and M-series chips, exploiting a type confusion vulnerability;
- the second option does not depend on time, but relies on the so-called race condition;
- WebKit's unique ability to combine websites from different domains into the same rendering process using the common JavaScript method "window. open".
In order for the attack to work, the affected computer must first visit the iLeakage website. If you log in to your account on a compromised website and the attacker's site at the same time, it will take about 5 minutes to analyze the visiting device. iLeakage can then force the browser to open any other site and start transmitting certain data at a rate of 24 to 34 bits per second.
Despite the technical complexity and the need for deep knowledge to implement an attack, the probability that this vulnerability will be used in real attacks in the near future is extremely low. Apple is expected to release a fix before the iLeakage attack becomes a real threat.
