Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,025
- Points
- 113
Thunderbird is an open source and free email client from Mozilla. The first release took place in 2003. The application is cross-platform, official assemblies are released for Windows, Linux and MacOS operating systems. The source code is written in C and C ++, the GTK framework is used for the graphical shell. Petrel - this is how the name of the program is translated - has an intuitive interface.
The client supports the protocols SMTP (for sending mail), POP3 (for receiving mail without leaving a copy on the server), IMAP (for receiving letters that remain on the server). In addition, two additional protocols are supported for receiving news and updates from sites - NNTP and RSS, as well as instant messaging protocols IRC and XMPP. Since Thunderbird is primarily an email client and not a chat application, the IRC and XMPP implementations are not very impressive.
The e-mail protocol is very old and does not have any built-in encryption, other than support for a secure connection to the server. On the mail server itself, all letters are in plain text, so they are always available to those who have direct access to the server, including those who are not legitimate.
Next, we will consider an example of using a mail server from the I2P network, which in general does not have any practical differences using the same Gmail and others. The soul only becomes warmer. To provide end-to-end encryption of correspondence from the sender to the recipient, the RNP module will be used - a kind of implementation of the standard OpenPGP asymmetric encryption.
For ease of perception by an inexperienced user, all examples are demonstrated on Windows. On other operating systems, the interfaces and configuration files look similar.
This material is for educational purposes only. The author is not responsible for any errors in the operation of the described software, as well as for those who will use the described technology for illegal purposes.
Now the browser is configured and knows how to open hidden sites! For example, we will use the most popular mail service on the I2P network - hq.postman.i2p, which is most often referred to simply as "mail.i2p". To create a new mailbox, select the "Creating a mailbox" menu item.
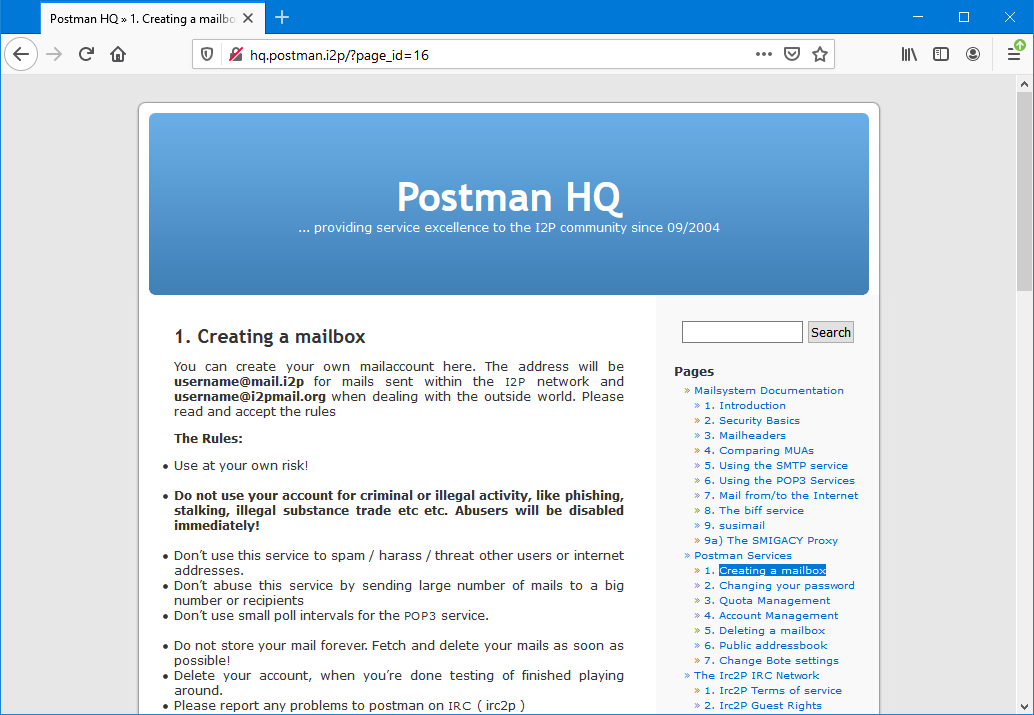
The page with the description of the service informs that when using a mailbox inside the I2P network, an address is possible @mail.i2p, and for calls from outside - @i2pmail.org. It is also highlighted in bold text that it is strictly forbidden to use the service for criminal purposes! We thoroughly agree with these words and move on.
After filling out the registration form and confirming the entered data, we see a summary of the new account. The warning informs us that the registration process can take up to five minutes. The service supports SMTP and POP3 protocols. It is also reported that the account will be deleted if there is no activity on it for more than a hundred days.

You have an account, now you need to connect to it. At this point, you should already have the Thunderbird mail client installed. Download it exclusively from the official site, because it is free and there is no need to pirate it.
Client tunnels must be created to access the server from I2P using SMTP and POP3 protocols. Don't be alarmed, this is an extremely simple operation. To do this, open the text tunnels configuration file tunnels.conf. On Windows the file is usually stored in a directory %APPDATA%\i2pd\, on Debian it is /etc/i2pd/.
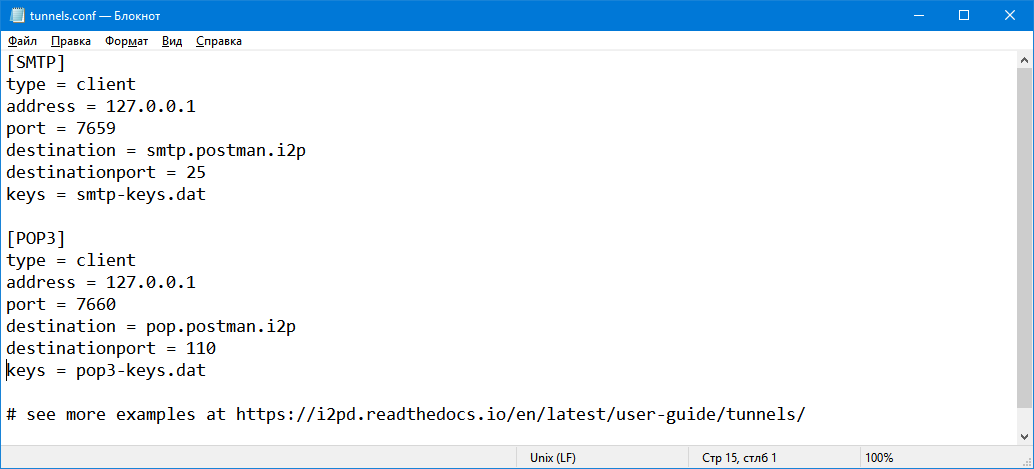
The default file has the necessary tunnels, but they are commented out. Remove the grids at the beginning of the lines from the [SMTP] and sections [POP3]. If for some reason you do not have a template configuration file, create a new file tunnels.conf in the i2pd working directory (you can view it in the web console) and paste the following content into it:
[SMTP]
After that, you need to restart the I2P router. In simple terms: close i2pd and start it again. Then you can verify that the tunnels named SMTP and POP3 have been created. To do this, open "I2P tunnels" in the web console.
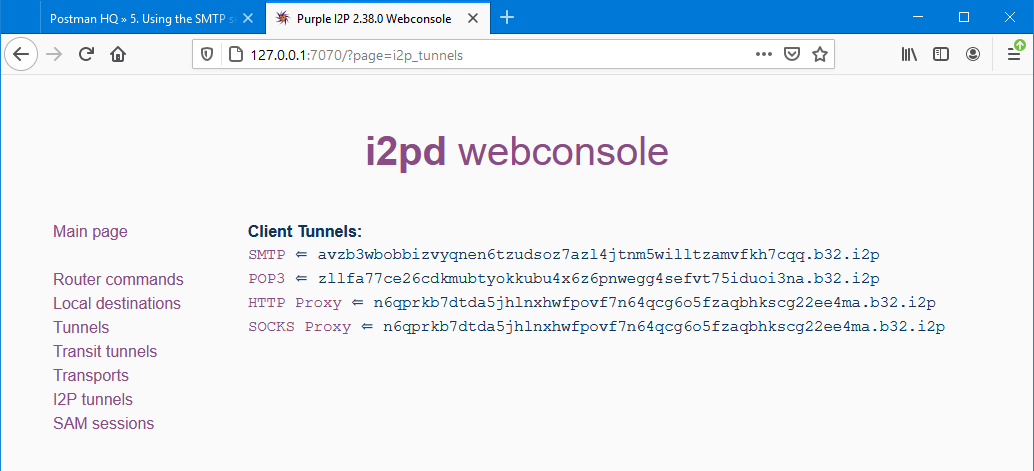
If you have technical skills, you can take your mail server to a hidden network and use it in a similar way.
Registration data is required.
Thunderbird swears at the mail domain @mail.i2p, but allows it to be applied after a warning. To receive incoming mail, the IMAP protocol is installed by default, it must be changed to POP3. Specify the addresses and port numbers that are entered in the tunnel configuration file. Disable SSL encryption, which is responsible for the secure connection to the server, as the I2P network itself provides security. Authentication is a regular password. Username - the name of your e-mail without ending @mail.i2p. When you click on the "Finish" button, the program will probably swear that you are using a connection without encryption. But there is encryption, believe me, and even what! Therefore, ignore the warning and finish adding the account.
If by clicking on the "Receive" button in the upper left corner (meaning "Receive mail") a connection to the server is established, then the setting is correct.
In the case of using mail servers from the regular Internet, you can find the specified connection parameters in the service documentation or on the help page.
Now let's move on to the "End-to-end encryption" item - select the required account and click on the mentioned button on the right side of the screen.
Since August 2020, the email client uses a built-in key store that is not associated with any key managers in the operating system and third-party plugins. It is possible to create new keys (or import existing ones) directly in the Thunderbird client. The built-in key manager supports the creation of keys and the binding of a specific key to the mailbox, which will be used by default to decrypt and sign the sent correspondence. Since this is an instruction for beginners, we will analyze the creation of a new key and further operations with it.
Click the Add Key button, then Generate New OpenPGP Key.
The screenshot shows the option of creating an unlimited key on elliptic curves - more advanced cryptography than the RSA type, which is offered by default. After the key is created, it is automatically bound to the mailbox for which it was created.
The fundamental point in asymmetric encryption is the presence of two keys: private and public. The private key is used for decryption and signature, and is stored in a safe place, while the public key is distributed freely and serves to verify the signature and to encrypt information. In order to be able to use the identity of your key in the future, for example, on another device, you need to make a backup copy of it. To do this, open the spoiler of the dedicated key, click the "More" button and "Create a backup copy of the secret key in a file".
It is important to understand that falling into the wrong hands of the secret key puts an end to your past encrypted correspondence. Also, you will again need to create a new key and share it with the interlocutors, explaining that you are a partridge. In short: you cannot have your secret key with someone other than you, so keep it in a safe place. Preferably in a crypto container and on an isolated device.
Below on the same page are the default encryption and signature settings. It is recommended to activate both options.
Signing is carried out with your key, so you need to sign messages regardless of the presence of the interlocutor's keys, and encryption is possible only if you have the recipient's public key. The integrity of the digital signature is verified by your public key, which is attached to the letter. It allows you to ensure that the content of the message has not been changed during the transfer.
On startup, Thunderbird decrypts its keystore. If your computer falls into the wrong hands, the secret key will be stolen. To be safe, you need to set a master password in the Thunderbird settings, which will be required to decrypt the storage. The password will be requested every time the mail client starts, and if the correct passphrase is not entered, the client will start anyway, but the keys will not be able to be used.
Open the "Settings" email client, then select "Privacy and Security". On this page, check the "Use master password" checkbox, after which you will be prompted to create one. Don't skimp on the complexity! This is the last line of defense for your private keys.
If you forget the master password, all the data that is protected by it will be forever lost for you.
Since there is no recipient's public key in the storage, it is necessary to select the "Do not encrypt" item in the "Protection" tab, because there is nothing to encrypt and the message will not be sent.
After receiving the letter, the addressee imported our public key into his storage and sent the answer already in encrypted form, and also signed it with his key so that we can be sure who the sender is.
The icon with a lock and a checkmark in the message status indicates that the message was encrypted on the sender's side and successfully decrypted on our side. The certificate icon denotes a digital signature. To verify it, you need to import the sender's public key into your local key store. If the public key is attached to the message, a button with an import offer appears automatically.
After importing the key, the signature can be verified. The screenshot shows that the signature is valid, however, Thunderbird is in no hurry with the green full trust icon until we manually confirm the validity of the received key. This is done using the fingerprint of the key, which is usually published in public places: on web pages, in the signature of letters, and the like.
In the example, the sender's key fingerprint is present in the letter, therefore, having verified the fingerprints, we certify the received key. After that, a signature icon will appear on the screen, but not with a yellow icon and an exclamation mark, but with a green checkmark.
No encryption is completely secure, because there are other attack methods to compromise your device and identity. Never open attachments, or click on links from emails, the senders of which you do not fully trust.
The client supports the protocols SMTP (for sending mail), POP3 (for receiving mail without leaving a copy on the server), IMAP (for receiving letters that remain on the server). In addition, two additional protocols are supported for receiving news and updates from sites - NNTP and RSS, as well as instant messaging protocols IRC and XMPP. Since Thunderbird is primarily an email client and not a chat application, the IRC and XMPP implementations are not very impressive.
The e-mail protocol is very old and does not have any built-in encryption, other than support for a secure connection to the server. On the mail server itself, all letters are in plain text, so they are always available to those who have direct access to the server, including those who are not legitimate.
Next, we will consider an example of using a mail server from the I2P network, which in general does not have any practical differences using the same Gmail and others. The soul only becomes warmer. To provide end-to-end encryption of correspondence from the sender to the recipient, the RNP module will be used - a kind of implementation of the standard OpenPGP asymmetric encryption.
For ease of perception by an inexperienced user, all examples are demonstrated on Windows. On other operating systems, the interfaces and configuration files look similar.
This material is for educational purposes only. The author is not responsible for any errors in the operation of the described software, as well as for those who will use the described technology for illegal purposes.
Installing i2pd and registering a mailbox
In order for your computer to have access to the anonymous I2P network, you need to install a special program - an I2P router. I2pd is recommended for good performance. Installation on any operating system is very trivial, so the process from boot to first launch will not be covered. For the web browser to have access to the hidden network, you need to configure a proxy. In Firefox, this is done through Settings -> Network Settings -> Manual Proxy Settings. The default i2pd HTTP proxy address is 127.0.0.1:4444.Now the browser is configured and knows how to open hidden sites! For example, we will use the most popular mail service on the I2P network - hq.postman.i2p, which is most often referred to simply as "mail.i2p". To create a new mailbox, select the "Creating a mailbox" menu item.

The page with the description of the service informs that when using a mailbox inside the I2P network, an address is possible @mail.i2p, and for calls from outside - @i2pmail.org. It is also highlighted in bold text that it is strictly forbidden to use the service for criminal purposes! We thoroughly agree with these words and move on.
After filling out the registration form and confirming the entered data, we see a summary of the new account. The warning informs us that the registration process can take up to five minutes. The service supports SMTP and POP3 protocols. It is also reported that the account will be deleted if there is no activity on it for more than a hundred days.

You have an account, now you need to connect to it. At this point, you should already have the Thunderbird mail client installed. Download it exclusively from the official site, because it is free and there is no need to pirate it.
Client tunnels must be created to access the server from I2P using SMTP and POP3 protocols. Don't be alarmed, this is an extremely simple operation. To do this, open the text tunnels configuration file tunnels.conf. On Windows the file is usually stored in a directory %APPDATA%\i2pd\, on Debian it is /etc/i2pd/.

The default file has the necessary tunnels, but they are commented out. Remove the grids at the beginning of the lines from the [SMTP] and sections [POP3]. If for some reason you do not have a template configuration file, create a new file tunnels.conf in the i2pd working directory (you can view it in the web console) and paste the following content into it:
[SMTP]
After that, you need to restart the I2P router. In simple terms: close i2pd and start it again. Then you can verify that the tunnels named SMTP and POP3 have been created. To do this, open "I2P tunnels" in the web console.

If you have technical skills, you can take your mail server to a hidden network and use it in a similar way.
Configuring Thunderbird
At the top of the interface, find the "Account Settings" button. Then, from the Account Actions menu, select Create Mail Account.Registration data is required.
Thunderbird swears at the mail domain @mail.i2p, but allows it to be applied after a warning. To receive incoming mail, the IMAP protocol is installed by default, it must be changed to POP3. Specify the addresses and port numbers that are entered in the tunnel configuration file. Disable SSL encryption, which is responsible for the secure connection to the server, as the I2P network itself provides security. Authentication is a regular password. Username - the name of your e-mail without ending @mail.i2p. When you click on the "Finish" button, the program will probably swear that you are using a connection without encryption. But there is encryption, believe me, and even what! Therefore, ignore the warning and finish adding the account.
If by clicking on the "Receive" button in the upper left corner (meaning "Receive mail") a connection to the server is established, then the setting is correct.
In the case of using mail servers from the regular Internet, you can find the specified connection parameters in the service documentation or on the help page.
Now let's move on to the "End-to-end encryption" item - select the required account and click on the mentioned button on the right side of the screen.
Since August 2020, the email client uses a built-in key store that is not associated with any key managers in the operating system and third-party plugins. It is possible to create new keys (or import existing ones) directly in the Thunderbird client. The built-in key manager supports the creation of keys and the binding of a specific key to the mailbox, which will be used by default to decrypt and sign the sent correspondence. Since this is an instruction for beginners, we will analyze the creation of a new key and further operations with it.
Click the Add Key button, then Generate New OpenPGP Key.
The screenshot shows the option of creating an unlimited key on elliptic curves - more advanced cryptography than the RSA type, which is offered by default. After the key is created, it is automatically bound to the mailbox for which it was created.
The fundamental point in asymmetric encryption is the presence of two keys: private and public. The private key is used for decryption and signature, and is stored in a safe place, while the public key is distributed freely and serves to verify the signature and to encrypt information. In order to be able to use the identity of your key in the future, for example, on another device, you need to make a backup copy of it. To do this, open the spoiler of the dedicated key, click the "More" button and "Create a backup copy of the secret key in a file".
It is important to understand that falling into the wrong hands of the secret key puts an end to your past encrypted correspondence. Also, you will again need to create a new key and share it with the interlocutors, explaining that you are a partridge. In short: you cannot have your secret key with someone other than you, so keep it in a safe place. Preferably in a crypto container and on an isolated device.
Below on the same page are the default encryption and signature settings. It is recommended to activate both options.
Signing is carried out with your key, so you need to sign messages regardless of the presence of the interlocutor's keys, and encryption is possible only if you have the recipient's public key. The integrity of the digital signature is verified by your public key, which is attached to the letter. It allows you to ensure that the content of the message has not been changed during the transfer.
On startup, Thunderbird decrypts its keystore. If your computer falls into the wrong hands, the secret key will be stolen. To be safe, you need to set a master password in the Thunderbird settings, which will be required to decrypt the storage. The password will be requested every time the mail client starts, and if the correct passphrase is not entered, the client will start anyway, but the keys will not be able to be used.
Open the "Settings" email client, then select "Privacy and Security". On this page, check the "Use master password" checkbox, after which you will be prompted to create one. Don't skimp on the complexity! This is the last line of defense for your private keys.
If you forget the master password, all the data that is protected by it will be forever lost for you.
Sending and receiving encrypted emails
When creating a new message with the above settings, a public key is attached to each message, the message is signed and, if the interlocutor's public key is available, it is encrypted. The interlocutor's key in the key store is determined by the email address.Since there is no recipient's public key in the storage, it is necessary to select the "Do not encrypt" item in the "Protection" tab, because there is nothing to encrypt and the message will not be sent.
After receiving the letter, the addressee imported our public key into his storage and sent the answer already in encrypted form, and also signed it with his key so that we can be sure who the sender is.
The icon with a lock and a checkmark in the message status indicates that the message was encrypted on the sender's side and successfully decrypted on our side. The certificate icon denotes a digital signature. To verify it, you need to import the sender's public key into your local key store. If the public key is attached to the message, a button with an import offer appears automatically.
After importing the key, the signature can be verified. The screenshot shows that the signature is valid, however, Thunderbird is in no hurry with the green full trust icon until we manually confirm the validity of the received key. This is done using the fingerprint of the key, which is usually published in public places: on web pages, in the signature of letters, and the like.
In the example, the sender's key fingerprint is present in the letter, therefore, having verified the fingerprints, we certify the received key. After that, a signature icon will appear on the screen, but not with a yellow icon and an exclamation mark, but with a green checkmark.
Afterword
The key fingerprint with which you sign your messages is your identity. If you have a need to send a message that is not related to your identity, do not use your old digital signature.No encryption is completely secure, because there are other attack methods to compromise your device and identity. Never open attachments, or click on links from emails, the senders of which you do not fully trust.

