Brother
Professional
- Messages
- 2,590
- Reaction score
- 533
- Points
- 113
The audacious approach to compromise opened hackers access to the open source software supply chain.
A malicious package was recently discovered in the npm registry that deploys a sophisticated Remote Access Trojan (RAT) on infected Windows computers. The package called "oscompatible" was published on January 9, 2024 and downloaded 380 times before it was removed.
Phylum, a software supply chain security company, reported that "oscompatible" contained an executable file, a dynamically linked library (DLL), and an encrypted DAT file, along with a JavaScript file.
During the attack, a JavaScript file ("index.js") runs the script " autorun.bat", which first checks compatibility with the Microsoft proprietary operating system and, if the result is positive, checks for administrator rights. If they don't exist, a legitimate component of the Edge browser is used for the attack "cookie_exporter.exe", run via PowerShell.
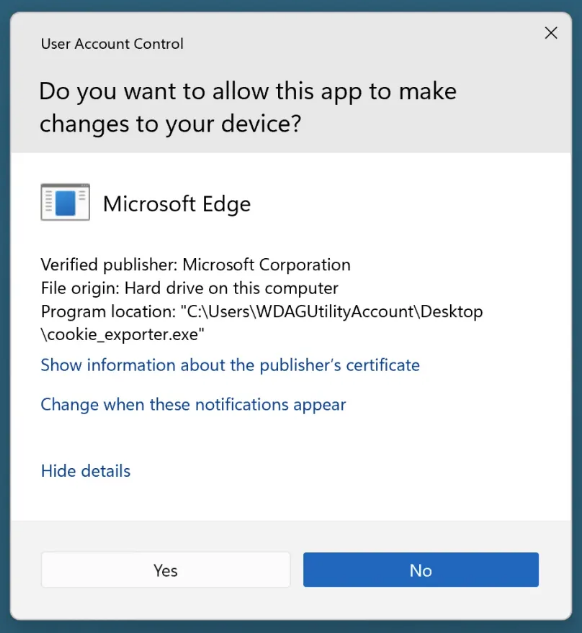
Running an executable file triggers a User Account Control (UAC) request that requires administrative credentials to be executed.
The attacker then runs the aforementioned DLL ("msedge.dll"), using the DLL Search Order Hijacking technique, to perform the next stage of the attack.
The Trojan version of the library is designed to decrypt the DAT file ("msedge.dat") and run another library ("msedge. dat"). msedgedat.dll"), which establishes a connection to the hacker-controlled domain "kdark1 [.] com" to get a ZIP archive.
This archive contains AnyDesk remote access software and the remote access Trojan, also packaged in a DLL ("verify.dll"). The Trojan can receive instructions from the command and control server via WebSockets and collect confidential information from the host.
Phylum reports that the Trojan also installs malicious extensions in the Secure Preferences file, which stores Chrome browser settings, establishes communication with AnyDesk, starts a fake Windows 10 update animation, and blocks Windows from shutting down.
At this point, the attacker can perform any actions with the programs and files of the infected PC, and the user will not be able to find out about it and even turn off the computer in any other way than through the button on the power supply. Usually, no one resorts to such emergency measures, so the hacker will definitely have enough time to implement any malicious plans.
While "oscompatible" appears to be the only npm module used in this campaign, the researchers ' findings again indicate that attackers are increasingly targeting open source software ecosystems to conduct supply chain attacks.
Phylum notes that "the process of decrypting data, using a revoked certificate for signing, downloading additional files from remote sources, and trying to disguise yourself as a standard Windows update process are relatively complex compared to what is usually used for attacks on OpenSource ecosystems."
The Phylum investigation was published amid a report by Aqua Security, according to which about 21% of the 50,000 most downloaded npm packages are outdated and expose users to security risks. This includes both archived and deleted GitHub repositories associated with packages, as well as those packages that are supported without a visible repository, commit history, or issue tracking.
A malicious package was recently discovered in the npm registry that deploys a sophisticated Remote Access Trojan (RAT) on infected Windows computers. The package called "oscompatible" was published on January 9, 2024 and downloaded 380 times before it was removed.
Phylum, a software supply chain security company, reported that "oscompatible" contained an executable file, a dynamically linked library (DLL), and an encrypted DAT file, along with a JavaScript file.
During the attack, a JavaScript file ("index.js") runs the script " autorun.bat", which first checks compatibility with the Microsoft proprietary operating system and, if the result is positive, checks for administrator rights. If they don't exist, a legitimate component of the Edge browser is used for the attack "cookie_exporter.exe", run via PowerShell.

Running an executable file triggers a User Account Control (UAC) request that requires administrative credentials to be executed.
The attacker then runs the aforementioned DLL ("msedge.dll"), using the DLL Search Order Hijacking technique, to perform the next stage of the attack.
The Trojan version of the library is designed to decrypt the DAT file ("msedge.dat") and run another library ("msedge. dat"). msedgedat.dll"), which establishes a connection to the hacker-controlled domain "kdark1 [.] com" to get a ZIP archive.
This archive contains AnyDesk remote access software and the remote access Trojan, also packaged in a DLL ("verify.dll"). The Trojan can receive instructions from the command and control server via WebSockets and collect confidential information from the host.
Phylum reports that the Trojan also installs malicious extensions in the Secure Preferences file, which stores Chrome browser settings, establishes communication with AnyDesk, starts a fake Windows 10 update animation, and blocks Windows from shutting down.
At this point, the attacker can perform any actions with the programs and files of the infected PC, and the user will not be able to find out about it and even turn off the computer in any other way than through the button on the power supply. Usually, no one resorts to such emergency measures, so the hacker will definitely have enough time to implement any malicious plans.
While "oscompatible" appears to be the only npm module used in this campaign, the researchers ' findings again indicate that attackers are increasingly targeting open source software ecosystems to conduct supply chain attacks.
Phylum notes that "the process of decrypting data, using a revoked certificate for signing, downloading additional files from remote sources, and trying to disguise yourself as a standard Windows update process are relatively complex compared to what is usually used for attacks on OpenSource ecosystems."
The Phylum investigation was published amid a report by Aqua Security, according to which about 21% of the 50,000 most downloaded npm packages are outdated and expose users to security risks. This includes both archived and deleted GitHub repositories associated with packages, as well as those packages that are supported without a visible repository, commit history, or issue tracking.

