Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,095
- Points
- 113
Experts reveal a method of stealing the data of online shopping enthusiasts.
During a recent cyberattack on a large number of online stores using the Magento platform, a skimmer was introduced into the sites, which stole customers' payment card data, including the card number, expiration date, and CVV/CVC code. Malwarebytes experts explained in detail how hackers managed to steal information.
Attackers used a vulnerability in the Magento system to inject malicious code into payment pages. The code is a simple line of script that downloads content from a remote site. Hackers created several websites through which the stolen data was collected. The analysis showed that at least several hundred online stores were compromised.
The malware manifested itself when entering card data on the payment page. At the moment when the buyer entered his data, the skimmer intercepted it and sent it to the attackers servers. In one case, the store used a third-party company to process payments, but the skimmer spoofed the process and was the first to intercept the entered data.

Fake (left) and real (right) payment page
Specialists managed to block more than 1,100 attempts to steal data, which became possible thanks to the identification and addition to the list of threats of several dozen malicious domains used by hackers to collect data.
Digital skimmers are hard to notice as they integrate into legitimate payment pages without arousing suspicion among users. To detect such threats, you need to closely monitor network traffic or use developer tools to analyze the page.
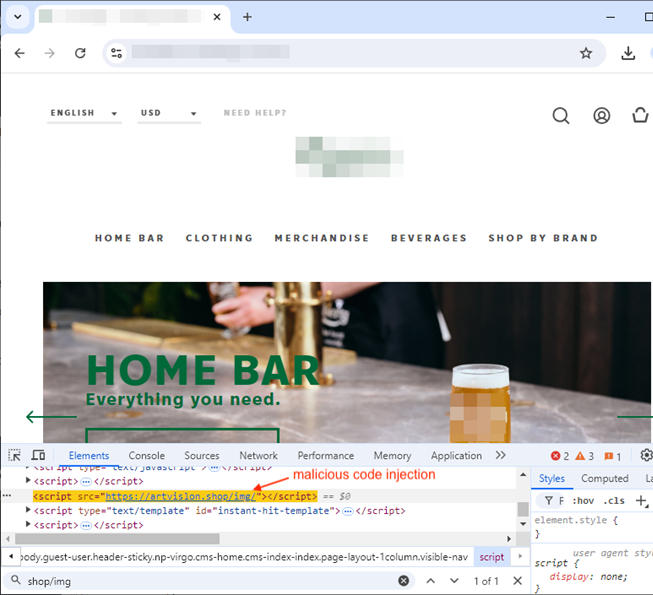
Example of code injection for an online store
Affected stores have already taken measures to eliminate malicious code or temporarily suspended their operations. However, some of the compromised sites remain under attack.
It is important to note that data theft using skimmers can lead to the leakage of not only financial information, but also personal data such as email address, home address, and phone number. In case of suspicion of data leakage, users are advised to contact the bank to reissue the card and consider using programs to protect their identity.
In July, Sucuri specialists discovered a new method of data theft on the Magento e-commerce platform. Attackers use swap files to inject persistent spyware that steals credit card data. The identified injection method dramatically increases the survivability of malicious code in the infected system, allowing it to survive numerous removal attempts without any problems.
Source
During a recent cyberattack on a large number of online stores using the Magento platform, a skimmer was introduced into the sites, which stole customers' payment card data, including the card number, expiration date, and CVV/CVC code. Malwarebytes experts explained in detail how hackers managed to steal information.
Attackers used a vulnerability in the Magento system to inject malicious code into payment pages. The code is a simple line of script that downloads content from a remote site. Hackers created several websites through which the stolen data was collected. The analysis showed that at least several hundred online stores were compromised.
The malware manifested itself when entering card data on the payment page. At the moment when the buyer entered his data, the skimmer intercepted it and sent it to the attackers servers. In one case, the store used a third-party company to process payments, but the skimmer spoofed the process and was the first to intercept the entered data.

Fake (left) and real (right) payment page
Specialists managed to block more than 1,100 attempts to steal data, which became possible thanks to the identification and addition to the list of threats of several dozen malicious domains used by hackers to collect data.
Digital skimmers are hard to notice as they integrate into legitimate payment pages without arousing suspicion among users. To detect such threats, you need to closely monitor network traffic or use developer tools to analyze the page.

Example of code injection for an online store
Affected stores have already taken measures to eliminate malicious code or temporarily suspended their operations. However, some of the compromised sites remain under attack.
It is important to note that data theft using skimmers can lead to the leakage of not only financial information, but also personal data such as email address, home address, and phone number. In case of suspicion of data leakage, users are advised to contact the bank to reissue the card and consider using programs to protect their identity.
In July, Sucuri specialists discovered a new method of data theft on the Magento e-commerce platform. Attackers use swap files to inject persistent spyware that steals credit card data. The identified injection method dramatically increases the survivability of malicious code in the infected system, allowing it to survive numerous removal attempts without any problems.
Source

