You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Bannyblanco
Professional
There are many methods to break a SIM card so we can not say exactly how they broke the SIM card
Sim Swaping, Vishing, Phishing, Trojaning, Keylogging and etc
Sim Swaping, Vishing, Phishing, Trojaning, Keylogging and etc
dunkelh3it
BANNED
Please note, if you want to make a deal with this user, that it is blocked.
Usually, after obtaining the identity information of the person, a fake identity is created, then by contacting the gsm operator, the sim card is declared lost and a new one is purchased.hello brothers, my friend got hacked , they stoped his sim card, and changed all his info including his binance account(10k) they took everything,. How could someone hack a sim card ?
However, as Bannyblanco said, there are many methods.
According to the majority of users of mobile devices, hacking a phone is gaining access to the system data of the device, unauthorized by the owner of the device.
Content
What is phone hacking
At first glance, this action seems illegal. After all, modern mobile devices are used not only as a means of communication with the outside world. At the moment, smartphones are the repositories of a huge amount of user's personal information.
When a telephone is hacked, the “attacker” gains access to all the intimate data of the “victim”. Including: full money from paypment system, bank accaunts, photos, videos, correspondence, notes, application accounts that are installed on the smartphone. For most people, this kind of hacking is equal to infiltrating their privacy.
In addition, some hacking methods provide the ability to control the victim's mobile device. That is, the "attacker" gets access to almost all the functionality of the smartphone: he can make voice calls and send text messages, install or delete messages of interest, change the system settings of equipment.
But, despite such a rich functionality of many "spyware" programs for hacking gadgets, basically, I use access to another user's mobile device solely for the sake of obtaining the subscriber's personal information necessary for the cracker.
Why do you need to hack someone else's phone
It is worth understanding that hacking someone else's phone is an invasion of a person's personal life, since at present mobile devices are not only means of communication, but also stores of the user's personal information: photos, videos, and correspondence.
Therefore, victims of a hacked smartphone can file a complaint with law enforcement agencies. In this case, an investigation will begin in the case of the introduction into a person's personal life.
However, despite the enormous risks and even the threatening criminal liability on the vastness of the World Wide Web, you can find many ways to hack someone else's mobile device. After all, demand creates supply.
Basically, people close to each other try to get access to the smartphone. For example, parents who start to worry about the behavior of their teenage child. Remote monitoring of the smartphone allows them to know about all the secrets of their child.
Also, hacking the phone is in demand among married couples, in which one of the spouses begins to doubt the loyalty of the other, and reading personal correspondence is the best way to catch cheating.
In addition, distrustful employers often resort to remote access of a mobile device to check how their subordinate uses the office phone provided to him.
Naturally, the user may have their own reasons for hacking someone else's smartphone, but this does not make this process any less illegal.
What are the ways you can hack phone
There are two main ways you can hack someone else's phone:
The offices that promise to hack someone else's smartphone will be discussed further, so first we will analyze the first method.
Getting data through a specialized spyware is without a doubt the easiest method to hack someone else's smartphone. After all, this does not require any specialized programming skills from the cracker. However, the main advantage of this kind of application is that it is almost impossible to detect them by the "hacked victim".
Spy programs, in turn, are divided into two main types:
That is, the attacker must have physical access to the device of interest. After installation, the application will start uploading information from the smartphone of interest to the special online server of the program. The cracker, in turn, will have access to this storage.
Physical access to the victim's mobile device is required only once. In the future, the data will be automatically uploaded to the online server.
The second type of spy apps works exclusively with Apple iPhone smartphones. These programs work by monitoring specialized cloud storage, in the case of Apple products, this is iCloud. Accordingly, to hack a smartphone, physical access to the gadget is not required.
However, this type of program has a significant drawback - updated "victim" data. The fact is that cloud storages update information at certain time intervals set by the user. Therefore, it will not be possible to view the data online.
Applications for remote access to someone else's phone
On the mobile application market, there are many programs that provide their users with remote access to other people's mobile devices. However, it should be borne in mind that the desire of users to hack another subscriber's smartphone is taken into account by cybercriminals who spread viruses and other malicious software under the guise of spyware, or seize money by deception.
In this article, we will analyze the following applications for hacking someone else's phone:
This software has been tested by many users, so there is no need to fear for the compliance of the services provided.
Each of the programs provided in the list has its own functionality, so it would be wiser to consider the presented spy applications in more detail.
iKeymonitor
iKeymonitor is a popular application for remote access to someone else's electronic device.
The main feature of this spy program is the "keylogger". This is a specialized feature that allows an attacker to enter everything that has ever been typed on the keyboard: messages, phone numbers, usernames and passwords.
Another plus of this software is cross-platform. That is, the iKeymonitor application can be used to hack devices both on devices running on the Android operating system and on iPhones with their iOS.
To jailbreak a device using the iKeymonitor program, the user needs to:
1. Create an iKeymonitor account.
2. On a mobile device that needs to be hacked, you need to go to the site and enter your user data.
3. Go to downloads and select the desired file corresponding to the parameters of the device - the operating system, the presence or absence of rooting / jailbreak.
4. Install the selected file on your smartphone.
5. Wait an hour for the program to collect all system information.
6. Go to the iKeymonitor website to get remote access to the device.
It's best to download a spy app from the developer's official website to avoid malware or viruses.
IP Webcam
This application specializes more in espionage than providing access to the device of interest to the intruder.
The fact is that this software only allows you to track the "victim" directly through the front or main camera of the telephone, but does not give the cracker the right to view personal information stored on the smartphone.
IP Webcam works exclusively on smartphones that are equipped with the Android operating system.
To hack a mobile device camera using the IP Webcam application, you need to follow the following step-by-step instructions:
1. First of all, you need to install the IP Webcam application. This must be done both on the mobile device that needs to be hacked and on the equipment from which the monitoring will be carried out. It can be either a smartphone on the Android operating system or a personal computer.
2. Then the application should be launched. In the "Server control" menu, click the "Start server" tab.
3. The broadcast from the device's camera will start. At the bottom of the screen there will be an address bar, which must be copied to the browser of the device from which the user will "spy".
4. The final action is to hide the application so that the user does not suspect that his phone is being viewed. To do this, in the program settings, click on the "Run in background" tab.
Applications of this type use a huge amount of smartphone energy, because in fact a mobile device will almost always broadcast live video to the network.

MSPY
mSPY is one of the most popular programs for hacking someone else's mobile device.
This application has the following functionality:
To hack someone else's smartphone using the mSPY spy app, follow these instructions step by step:
1. Purchase the software on the developer's official website. mSPY works on the basis of a subscription fee, that is, for the services provided, the user must pay a certain amount every month. In addition, the price of the offer will depend on the package of services provided.
2. Check the specified email. In the sent letter, choose the hacking path "with jailbreak" or "without jailbreak".
3. For hacking without JailBreak. Enter the Apple ID password and password of the user whose phone you want to hack.
4. To get access with JailBreak. Install the application on the victim's smartphone.
5. After completing all the steps, go to the mSPY control panel and start monitoring the selected device.
It is necessary to purchase software from mSPY exclusively on the official website of the developer in order to avoid fraud.
Spyzie
Spyzie is a jailbreak app that can be easily bypassed without giving the cracker root privileges. That is, confirmation from the owner of the phone about the ability to edit and change the system files of the equipment.
Another useful feature of Spyzie spyware is the ability to remove it remotely. An extremely handy feature if the attacker forgot to hide the application icon or access to the victim's personal data is no longer needed.
In order to get remote access to the device using the Spyzie utility, you need to:
1. Register on the official website of the developer.
2. Enter the basic data of the smartphone of interest.
3. Download the application to the victim's phone or enter the Apple ID information, in case of remote access.
4. Go to the program website and start monitoring.
Spyzie software can be downloaded from the developer's official website, both for smartphones running on Android OS and for iPhone owners .
Is it worth using the services of dubious companies
In addition to specialized spyware on the World Wide Web, you can find many firms that provide services for hacking gadgets. Consider all the pros of this type of company. Benefits - the ability to hack a mobile device without physical access to it.
As can be seen from the comparison, this method of gaining access to someone else's phone has more negative sides, so you should contact the company only if absolutely necessary.
Multi-SIM
There is such a device called Multi-SIM.
Outwardly it looks like a regular SIM card, but in terms of functionality it is like ten (although it depends on its type), and not necessarily from one operator! From a technical point of view, a Multi-SIM card (aka Clone Card) is a contact chip card (aka smart card) with a PIC microprocessor and EEPROM memory. To work as SIM-cards (or rather emulate them), it is specially stitched with the appropriate programmer.
Now in more detail about the possibilities that this stuff opens up before you. For each number, you can independently specify the SMS center number and
GPRS settings . You choose which SIM to load when you turn on the phone by entering the corresponding PIN code for each SIM card. Or, if you don't want to dial it every morning (for those who turn off the phone at night) set which SIM card to download by default.
Also, a new item appears in the phone menu, from which you can quickly switch to another SIM card. You do not need to turn off the phone for this . The switchover (together with network registration) takes less than 20 seconds.
How it works
To emulate a SIM card, you first need to get the registration data from it - this is the so -called international subscriber identifier - IMSI (International Mobile Subscriber Identity) and an individual subscriber authentication key KI (Key Individual). If these same KI and IMSI are known and you have a Multi-SIM card flashed with SIM-EMU version 6 or 5 (I recommend buying an already flashed and cut card - save on the programmer and nerve cells that are not restored), then insert Multi- SIM card to your cell phone and, following the SIM card menu items, enter KI, IMSI for each SIM card that you want to emulate and what PIN, PUK codes you want, as well as SMS center numbers.
That's it, the card is ready. The main difficulty is finding these same KI & IMSI.
A bit of theory
The KI key is stored on the SIM card in a closed memory area, i.e. there is no external access to it. The rest of the data, such as the phone book, sms and others, is stored in a protected area of memory, which can only be protected by a PIN code.
The encryption is handled by the A3-A8 algorithm, which is implemented at the hardware level in the SIM card. This is how everything happens: the base station (BS) sends a random number (possibly 32-bit), respectively, the phone receives it, transmits it to the SIM, it encrypts it using the A3-A8 algorithm using KI, and then the
result is sent back to the BS , thus KI is never broad cast in cleartext (from this, in theory, it follows that it cannot be calculated over the air), then the base station does the same, and at the end of this event it compares its result with the one sent, and if it converges, then you can call - access to the switch is allowed.
We extract KI & IMSI
However, the developers of this algorithm (the COMP128-1 encryption algorithm) made a serious mistake, due to which it is possible to calculate the KI and IMSI. In order to read this data, you need a special device called a GSM SIM Card Reader (reader, programmer), which you either need to assemble or buy.
In addition, as you might guess, you need special software to work with this case.
I am using SimScan version 2.01. It works for me on Windows without problems.
Dealing with it will not be difficult for you, the only thing I would advise is to leave all the default settings. On the third stump with 256 MB of RAM, the scan took me 40 minutes, but it should be noted that the limiting factor here is the speed of access to the SIM card, and not the speed of the computer. If the scan was successful and you got the KI and IMSI, then it's in the bag. And if not then two options are possible: either the SIM card has screwed up (most likely) and you have to change it, or it hasn't screwed up. The fact is that bad operators have come up with a new "protection" - they put a limit on the number of calls to a SIM card, but I have not met with such and I have not had a single lethal outcome. I heard about the real protection COMP128-2, which SimScan cannot cope with. But I think that our people will deal with it too.
So go for it!
What if use the copy and the original sim on the network at the same time?
Hackers who have dealt with this in detail say:
It works fine, the conversation is dropped only if both cards are in the range of one base station. If in different cities or in roaming - no problem at all. An incoming call comes to the one that last communicated with the base station. But in each case there are nuances that depend on the operator's equipment settings.
Types of cards
Here is a table showing what types of cards there are and their parameters:
The Numbers and SMS columns show the number of numbers and SMS that can be stored on the card. Which one to use is up to you, but in terms of price / usability, in my opinion, Silver wins. Virgin Silver Card can be bought on the radio market, which sells goods for satellite television. In the same place, by the way, you can still read about this case and even buy a programmer.
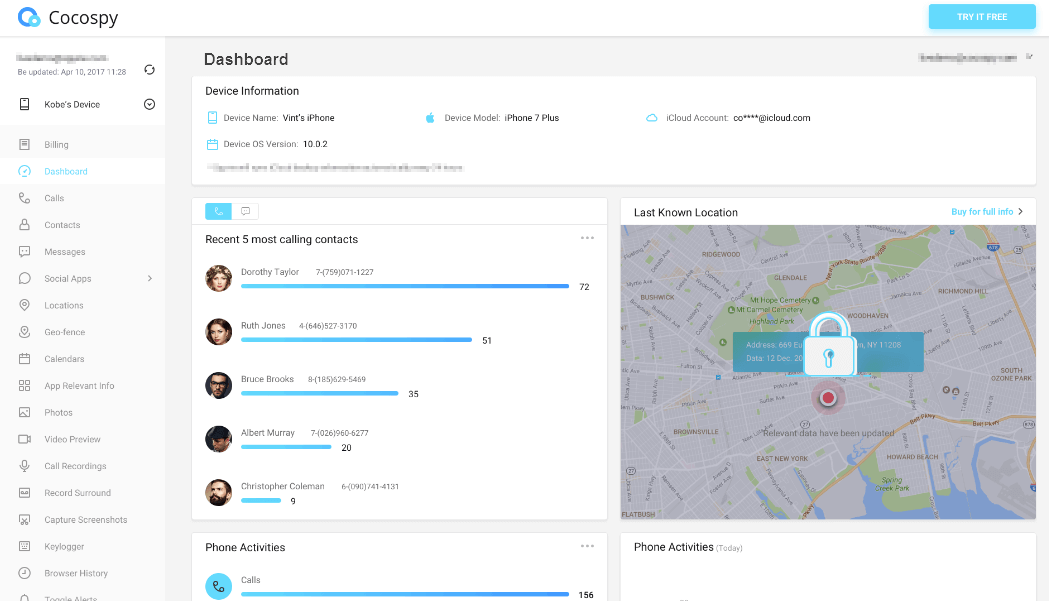
Part 1. How to clone data from a phone remotely using Cocospy?
Cocospy is the best phone cloning app on the market. It is extremely reliable and is used by over 190 million users worldwide, so you know you can trust it.
Moreover, it is also quite reasonable, since so many people cannot be wrong.
When it comes to copying from iPhone, you can do it remotely by entering the iCloud account details of the desired iPhone.
However, if you want to clone your Android phone data, you NEED physical access to your phone.
First, you need to get physical access to the phone, and then install the Cocospy app on it.
You may come across services promising to clone an Android phone without physically touching it. But they are crooks. It is impossible to jailbreak an Android smartphone without access to it.
Features of copying data
Below are some important data that you can clone using Cocospy.
How to copy data from Cocospy?
Step 1: Create a Cocospy account.
Step 2: for Android - Get physical access to your phone, and then, install the Cocospy app on it. Don't worry, you don't need to root your smartphone.
Step 3: for iPhone - During app installation, enter your iCloud account details and start cloning data from your phone. Yes, you don't need to install anything else or jailbreak the phone you are interested in.
Step 4: Go to your Cocospy dashboard and copy the data from your phone.
Part 2: How to copy data from phone using Spyzie
Spyzie is the safest and perhaps the most inexpensive phone cloning app. It has the same powerful feature set as Cocospy, but more reliable, perhaps due to its lower reputation and brand name.
Like Cocospy, for example, this app can also copy from iPhone, without physical access via iCloud data. However, for Android, you need physical access.
The good news is that Spyzie automatically removes the app icon after installing it. Therefore, you do not have to delete the icon manually, which means that there is no chance of making a mistake.
These features make the app the safest phone cloning app on the market.
In terms of phone copy capabilities, it has the same feature set as Cocospy.
With Spyzie, you can check text messages, call logs, browser history, social media apps, access calendars, notes, and more.
You can effectively clone an entire phone to your dashboard and then upload them to another phone if needed.
Part 3: How to clone a phone via mSpy without touching it.
mSpy is another option when it comes to cloning data from your phone without touching it.
It is one of the most powerful copy phone apps on the market and has a number of features such as call logging, text message recording, keyboard, social media tracking, browser history, and more.
Which will help you upload all the information about the required phone to your own control panel.
The app is trustworthy and reliable. However, it is listed below as it is quite expensive compared to Cocospy. If you choose one of these, I would recommend Cocospy.
It is worth noting that access to copy from the phone, if you do not have physical control over it, is only available for the iPhone.
You can enter your iCloud account information and access the information directly. For an Android phone, be sure to pick it up and install the application yourself.
How do I clone a phone using mSpy?
Part 4: How to Copy a Phone Number Easily
In this part of the article, we will show you how to copy a phone number. Now for those wondering what this means. Phone number cloning gives you the ability to use the same number on multiple devices at the same time.
Hackers can also use this technology to make calls from someone else's number without even having a phone OR their SIM card.
There are two effective ways to easily clone a phone number. We'll cover both of them below.
Clone phone number using SIM Copy Tool
You can also clone a phone number using the SIM cloning tool. However, you will also need a SIM card reader to do this.
You can easily find a device in the market. The reader basically copies the target phone's mobile ID to itself so that it becomes a duplicate of the original SIM. Just follow these steps:
Part 5: How to clone a SIM card in 2 minutes
In this part of the article, we will show you how to clone a SIM card. But first, we need to answer a few questions you may have regarding this process.
Is it possible to clone a SIM card
It is completely possible to clone a SIM card by extracting the secret codes from the card and copying them to a blank SIM card. Operator authentication on a SIM card is based on these codes, so transferring them to another blank card can help trick operators. This method mainly exploits a small glitch in GSM technology.
However, not all SIM cards can be cloned.
Only some. There are three main types of SIM card algorithms: COMP128v1, COMP128v2, and COMP128v3. COMP128v1 is currently the most popular SIM algorithm and luckily for us, it is the only one that can be cloned.
Now read on to find out how easy it is to clone a SIM card!
How to copy a SIM card in 2 minutes?
Part 6: How to copy text messages from Mobile Phone
Clone cell phone text messages is easy. You can do this with the apps we mentioned in parts 1-3.
Cocospy, mSpy, and Spyzie have a copy text message feature in their toolbars.
So when you choose this, you will get a complete log of all the target phone's text messages (sent, received and deleted), which can then be downloaded to another phone.
Part 7: How to know if my phone is cloned
Since cloning a phone is very easy, you may be concerned that someone else might have done it with your phone.
If so, you can check if your phone is cloned using the following methods:
As soon as you find that your number has been hacked, do the following:
Conclusion
So now you know all about the best ways to clone phone number, SIM card and text messages.
When it comes to copying data from your phone without touching it, my personal recommendation is to use Cocospy as it is reliable, user-friendly and has a wide range of features.
mSpy is too expensive by comparison. And Spyzie isn't all that reliable or has such a good reputation. As we mentioned earlier, you can only clone iPhones over the air.
If you want to copy data from your phone to Android, physical access to it is absolutely essential.
Spyzie, Cocospy, and mSpy can help you clone phone content, including text messages. However, these apps cannot be used to clone a SIM card phone number.
To do this, you will either have to use the secret menu method, or you will have to clone the SIM card into a dummy, as shown in parts 4 and 5.
Finally, if you suspect that your phone has been cloned or jailbroken by someone, follow the instructions and precautions listed at the end of this article.
If you have any other questions about how to clone a phone without touching it, feel free to ask them in the comments section.
Content
- What is phone hacking
- Why do you need to hack someone else's phone
- What are the ways you can hack your phone
- Applications for remote access to someone else's phone
- Is it worth using the services of dubious companies
- ]Part 1. How to clone data from a phone remotely using Cocospy?
- [Part 2: How to copy data from phone using Spyzie
- Part 3: How to clone a phone via mSpy without touching it
- Part 4: How to copy a phone number easily
- Part 5: How to clone a SIM card in 2 minutes
- Part 6: How to copy text messages from Mobile Phone
- Part 7: How to know if my phone is cloned
- Conclusion
What is phone hacking
At first glance, this action seems illegal. After all, modern mobile devices are used not only as a means of communication with the outside world. At the moment, smartphones are the repositories of a huge amount of user's personal information.
When a telephone is hacked, the “attacker” gains access to all the intimate data of the “victim”. Including: full money from paypment system, bank accaunts, photos, videos, correspondence, notes, application accounts that are installed on the smartphone. For most people, this kind of hacking is equal to infiltrating their privacy.
In addition, some hacking methods provide the ability to control the victim's mobile device. That is, the "attacker" gets access to almost all the functionality of the smartphone: he can make voice calls and send text messages, install or delete messages of interest, change the system settings of equipment.
But, despite such a rich functionality of many "spyware" programs for hacking gadgets, basically, I use access to another user's mobile device solely for the sake of obtaining the subscriber's personal information necessary for the cracker.
Why do you need to hack someone else's phone
It is worth understanding that hacking someone else's phone is an invasion of a person's personal life, since at present mobile devices are not only means of communication, but also stores of the user's personal information: photos, videos, and correspondence.
Therefore, victims of a hacked smartphone can file a complaint with law enforcement agencies. In this case, an investigation will begin in the case of the introduction into a person's personal life.
However, despite the enormous risks and even the threatening criminal liability on the vastness of the World Wide Web, you can find many ways to hack someone else's mobile device. After all, demand creates supply.
Basically, people close to each other try to get access to the smartphone. For example, parents who start to worry about the behavior of their teenage child. Remote monitoring of the smartphone allows them to know about all the secrets of their child.
Also, hacking the phone is in demand among married couples, in which one of the spouses begins to doubt the loyalty of the other, and reading personal correspondence is the best way to catch cheating.
In addition, distrustful employers often resort to remote access of a mobile device to check how their subordinate uses the office phone provided to him.
Naturally, the user may have their own reasons for hacking someone else's smartphone, but this does not make this process any less illegal.
What are the ways you can hack phone
There are two main ways you can hack someone else's phone:
- use of specialized programs for remote access to a mobile device;
- contact the services of companies that provide phone hacking services.
The offices that promise to hack someone else's smartphone will be discussed further, so first we will analyze the first method.
Getting data through a specialized spyware is without a doubt the easiest method to hack someone else's smartphone. After all, this does not require any specialized programming skills from the cracker. However, the main advantage of this kind of application is that it is almost impossible to detect them by the "hacked victim".
Spy programs, in turn, are divided into two main types:
- with access to a hacking mobile device;
- without access to the victim's smartphone.
That is, the attacker must have physical access to the device of interest. After installation, the application will start uploading information from the smartphone of interest to the special online server of the program. The cracker, in turn, will have access to this storage.
Physical access to the victim's mobile device is required only once. In the future, the data will be automatically uploaded to the online server.
The second type of spy apps works exclusively with Apple iPhone smartphones. These programs work by monitoring specialized cloud storage, in the case of Apple products, this is iCloud. Accordingly, to hack a smartphone, physical access to the gadget is not required.
However, this type of program has a significant drawback - updated "victim" data. The fact is that cloud storages update information at certain time intervals set by the user. Therefore, it will not be possible to view the data online.
Applications for remote access to someone else's phone
On the mobile application market, there are many programs that provide their users with remote access to other people's mobile devices. However, it should be borne in mind that the desire of users to hack another subscriber's smartphone is taken into account by cybercriminals who spread viruses and other malicious software under the guise of spyware, or seize money by deception.
In this article, we will analyze the following applications for hacking someone else's phone:
- iKeymonitor;
- IP Webcam;
- mSPY;
- Spyzie.
This software has been tested by many users, so there is no need to fear for the compliance of the services provided.
Each of the programs provided in the list has its own functionality, so it would be wiser to consider the presented spy applications in more detail.
iKeymonitor
iKeymonitor is a popular application for remote access to someone else's electronic device.
The main feature of this spy program is the "keylogger". This is a specialized feature that allows an attacker to enter everything that has ever been typed on the keyboard: messages, phone numbers, usernames and passwords.
Another plus of this software is cross-platform. That is, the iKeymonitor application can be used to hack devices both on devices running on the Android operating system and on iPhones with their iOS.

To jailbreak a device using the iKeymonitor program, the user needs to:
1. Create an iKeymonitor account.
2. On a mobile device that needs to be hacked, you need to go to the site and enter your user data.
3. Go to downloads and select the desired file corresponding to the parameters of the device - the operating system, the presence or absence of rooting / jailbreak.
4. Install the selected file on your smartphone.
5. Wait an hour for the program to collect all system information.
6. Go to the iKeymonitor website to get remote access to the device.
It's best to download a spy app from the developer's official website to avoid malware or viruses.
IP Webcam
This application specializes more in espionage than providing access to the device of interest to the intruder.
The fact is that this software only allows you to track the "victim" directly through the front or main camera of the telephone, but does not give the cracker the right to view personal information stored on the smartphone.
IP Webcam works exclusively on smartphones that are equipped with the Android operating system.
To hack a mobile device camera using the IP Webcam application, you need to follow the following step-by-step instructions:
1. First of all, you need to install the IP Webcam application. This must be done both on the mobile device that needs to be hacked and on the equipment from which the monitoring will be carried out. It can be either a smartphone on the Android operating system or a personal computer.
2. Then the application should be launched. In the "Server control" menu, click the "Start server" tab.
3. The broadcast from the device's camera will start. At the bottom of the screen there will be an address bar, which must be copied to the browser of the device from which the user will "spy".
4. The final action is to hide the application so that the user does not suspect that his phone is being viewed. To do this, in the program settings, click on the "Run in background" tab.
Applications of this type use a huge amount of smartphone energy, because in fact a mobile device will almost always broadcast live video to the network.

MSPY
mSPY is one of the most popular programs for hacking someone else's mobile device.
This application has the following functionality:
- Keylogger - the ability to restore information previously typed by the user;
- Geo-Fencing is a function that demonstrates the actual location of the device;
- Monitoring social networks - the ability to access the accounts of the "victim" in popular social networks.
To hack someone else's smartphone using the mSPY spy app, follow these instructions step by step:
1. Purchase the software on the developer's official website. mSPY works on the basis of a subscription fee, that is, for the services provided, the user must pay a certain amount every month. In addition, the price of the offer will depend on the package of services provided.
2. Check the specified email. In the sent letter, choose the hacking path "with jailbreak" or "without jailbreak".
3. For hacking without JailBreak. Enter the Apple ID password and password of the user whose phone you want to hack.
4. To get access with JailBreak. Install the application on the victim's smartphone.
5. After completing all the steps, go to the mSPY control panel and start monitoring the selected device.
It is necessary to purchase software from mSPY exclusively on the official website of the developer in order to avoid fraud.
Spyzie
Spyzie is a jailbreak app that can be easily bypassed without giving the cracker root privileges. That is, confirmation from the owner of the phone about the ability to edit and change the system files of the equipment.
Another useful feature of Spyzie spyware is the ability to remove it remotely. An extremely handy feature if the attacker forgot to hide the application icon or access to the victim's personal data is no longer needed.
In order to get remote access to the device using the Spyzie utility, you need to:
1. Register on the official website of the developer.
2. Enter the basic data of the smartphone of interest.
3. Download the application to the victim's phone or enter the Apple ID information, in case of remote access.
4. Go to the program website and start monitoring.
Spyzie software can be downloaded from the developer's official website, both for smartphones running on Android OS and for iPhone owners .
Is it worth using the services of dubious companies
In addition to specialized spyware on the World Wide Web, you can find many firms that provide services for hacking gadgets. Consider all the pros of this type of company. Benefits - the ability to hack a mobile device without physical access to it.
As can be seen from the comparison, this method of gaining access to someone else's phone has more negative sides, so you should contact the company only if absolutely necessary.
Multi-SIM
There is such a device called Multi-SIM.
Outwardly it looks like a regular SIM card, but in terms of functionality it is like ten (although it depends on its type), and not necessarily from one operator! From a technical point of view, a Multi-SIM card (aka Clone Card) is a contact chip card (aka smart card) with a PIC microprocessor and EEPROM memory. To work as SIM-cards (or rather emulate them), it is specially stitched with the appropriate programmer.
Now in more detail about the possibilities that this stuff opens up before you. For each number, you can independently specify the SMS center number and
GPRS settings . You choose which SIM to load when you turn on the phone by entering the corresponding PIN code for each SIM card. Or, if you don't want to dial it every morning (for those who turn off the phone at night) set which SIM card to download by default.
Also, a new item appears in the phone menu, from which you can quickly switch to another SIM card. You do not need to turn off the phone for this . The switchover (together with network registration) takes less than 20 seconds.
How it works
To emulate a SIM card, you first need to get the registration data from it - this is the so -called international subscriber identifier - IMSI (International Mobile Subscriber Identity) and an individual subscriber authentication key KI (Key Individual). If these same KI and IMSI are known and you have a Multi-SIM card flashed with SIM-EMU version 6 or 5 (I recommend buying an already flashed and cut card - save on the programmer and nerve cells that are not restored), then insert Multi- SIM card to your cell phone and, following the SIM card menu items, enter KI, IMSI for each SIM card that you want to emulate and what PIN, PUK codes you want, as well as SMS center numbers.
That's it, the card is ready. The main difficulty is finding these same KI & IMSI.
A bit of theory
The KI key is stored on the SIM card in a closed memory area, i.e. there is no external access to it. The rest of the data, such as the phone book, sms and others, is stored in a protected area of memory, which can only be protected by a PIN code.
The encryption is handled by the A3-A8 algorithm, which is implemented at the hardware level in the SIM card. This is how everything happens: the base station (BS) sends a random number (possibly 32-bit), respectively, the phone receives it, transmits it to the SIM, it encrypts it using the A3-A8 algorithm using KI, and then the
result is sent back to the BS , thus KI is never broad cast in cleartext (from this, in theory, it follows that it cannot be calculated over the air), then the base station does the same, and at the end of this event it compares its result with the one sent, and if it converges, then you can call - access to the switch is allowed.
We extract KI & IMSI
However, the developers of this algorithm (the COMP128-1 encryption algorithm) made a serious mistake, due to which it is possible to calculate the KI and IMSI. In order to read this data, you need a special device called a GSM SIM Card Reader (reader, programmer), which you either need to assemble or buy.
In addition, as you might guess, you need special software to work with this case.
I am using SimScan version 2.01. It works for me on Windows without problems.
Dealing with it will not be difficult for you, the only thing I would advise is to leave all the default settings. On the third stump with 256 MB of RAM, the scan took me 40 minutes, but it should be noted that the limiting factor here is the speed of access to the SIM card, and not the speed of the computer. If the scan was successful and you got the KI and IMSI, then it's in the bag. And if not then two options are possible: either the SIM card has screwed up (most likely) and you have to change it, or it hasn't screwed up. The fact is that bad operators have come up with a new "protection" - they put a limit on the number of calls to a SIM card, but I have not met with such and I have not had a single lethal outcome. I heard about the real protection COMP128-2, which SimScan cannot cope with. But I think that our people will deal with it too.
So go for it!
What if use the copy and the original sim on the network at the same time?
Hackers who have dealt with this in detail say:
It works fine, the conversation is dropped only if both cards are in the range of one base station. If in different cities or in roaming - no problem at all. An incoming call comes to the one that last communicated with the base station. But in each case there are nuances that depend on the operator's equipment settings.
Types of cards
Here is a table showing what types of cards there are and their parameters:
| Card | CPU | EEPROMT | Number of SIM | Numbers | SMS |
| GoldWafer | PIC16F84 | 24C16 | 4 | 31 | 1 |
| Silver | PIC16F876 | 24C64 | 8 | 208 | 10 |
| Green | PIC16F876 | 24C128 | 10 | 250 | 40 |
| Black | PIC16F876 | 24C256 | 10 | 250 | 40 |
Part 1. How to clone data from a phone remotely using Cocospy?
Cocospy is the best phone cloning app on the market. It is extremely reliable and is used by over 190 million users worldwide, so you know you can trust it.
Moreover, it is also quite reasonable, since so many people cannot be wrong.
When it comes to copying from iPhone, you can do it remotely by entering the iCloud account details of the desired iPhone.
However, if you want to clone your Android phone data, you NEED physical access to your phone.
First, you need to get physical access to the phone, and then install the Cocospy app on it.
You may come across services promising to clone an Android phone without physically touching it. But they are crooks. It is impossible to jailbreak an Android smartphone without access to it.
Features of copying data
Below are some important data that you can clone using Cocospy.
- Text messages. You can check all text messages sent or received by your phone. Cocospy also supports data backups, so you can access your text messages even if the person you're interested in deletes them. You can check text messages with date and time stamps, and even get contact information.
- Call log. You can download a complete log of all incoming and outgoing calls, contacts, as well as date and time stamps.
- View contacts. You can upload all contacts of the phone you are interested in to the Cocospy dashboard.
- Social media posts. Cocospy gives you access to all social media profiles on your phone like Facebook, Telegram, WhatsApp, etc. Also, you can even download all of his profiles, posts, etc. Unlike other apps, you don't need to root your Android smartphone to spy on it.
- Browser history. Load your entire browser history into your control panel so you know which sites were visited and when.
- Calendars and Notes. Access the user's calendar and notes.
How to copy data from Cocospy?
Step 1: Create a Cocospy account.
Step 2: for Android - Get physical access to your phone, and then, install the Cocospy app on it. Don't worry, you don't need to root your smartphone.
Step 3: for iPhone - During app installation, enter your iCloud account details and start cloning data from your phone. Yes, you don't need to install anything else or jailbreak the phone you are interested in.
Step 4: Go to your Cocospy dashboard and copy the data from your phone.

Part 2: How to copy data from phone using Spyzie
Spyzie is the safest and perhaps the most inexpensive phone cloning app. It has the same powerful feature set as Cocospy, but more reliable, perhaps due to its lower reputation and brand name.
Like Cocospy, for example, this app can also copy from iPhone, without physical access via iCloud data. However, for Android, you need physical access.
The good news is that Spyzie automatically removes the app icon after installing it. Therefore, you do not have to delete the icon manually, which means that there is no chance of making a mistake.
These features make the app the safest phone cloning app on the market.
In terms of phone copy capabilities, it has the same feature set as Cocospy.
With Spyzie, you can check text messages, call logs, browser history, social media apps, access calendars, notes, and more.
You can effectively clone an entire phone to your dashboard and then upload them to another phone if needed.
Part 3: How to clone a phone via mSpy without touching it.
mSpy is another option when it comes to cloning data from your phone without touching it.
It is one of the most powerful copy phone apps on the market and has a number of features such as call logging, text message recording, keyboard, social media tracking, browser history, and more.
Which will help you upload all the information about the required phone to your own control panel.
The app is trustworthy and reliable. However, it is listed below as it is quite expensive compared to Cocospy. If you choose one of these, I would recommend Cocospy.
It is worth noting that access to copy from the phone, if you do not have physical control over it, is only available for the iPhone.
You can enter your iCloud account information and access the information directly. For an Android phone, be sure to pick it up and install the application yourself.
How do I clone a phone using mSpy?
- Get mSpy for your phone. There are three subscription models available - Basic, Premium and Family Kit. The Premium package has advanced features that you can access by rooting the target Android phone by physically accessing it. So you should stick to the basic package. Or, if you want to clone up to 3 phones at the same time, you can also purchase the Family Kit.
- You will receive a link to the control panel from which you will need to set up an account. You will need to choose whether you want to clone an iPhone or an Android phone, and whether you want to select the rooted option or not. Without touching the device, i.e. ... remotely, you can only clone an iPhone. You need to select this particular option.
- Enter the iCloud account details of the desired user
- If you are cloning an Android phone, then you need to physically access it. Next, you need to go to "Settings"> "Security". Then unlock "Unknown Sources" before installing the mSpy app.
- Log in to your personal control panel with your account details.
Part 4: How to Copy a Phone Number Easily
In this part of the article, we will show you how to copy a phone number. Now for those wondering what this means. Phone number cloning gives you the ability to use the same number on multiple devices at the same time.
Hackers can also use this technology to make calls from someone else's number without even having a phone OR their SIM card.
There are two effective ways to easily clone a phone number. We'll cover both of them below.
Clone phone number using SIM Copy Tool
You can also clone a phone number using the SIM cloning tool. However, you will also need a SIM card reader to do this.
You can easily find a device in the market. The reader basically copies the target phone's mobile ID to itself so that it becomes a duplicate of the original SIM. Just follow these steps:
- Remove the target phone's SIM card and write down its IMSI code.
- Insert the SM card reader into the SIM card slot to obtain a unique authentication code
- Connect the original SIM card to the SIM card reader and connect it to the PC. She will automatically receive an authentication code. The duplication process will be completed after a while. Once this happens, you will have a copied clone number.
Part 5: How to clone a SIM card in 2 minutes
In this part of the article, we will show you how to clone a SIM card. But first, we need to answer a few questions you may have regarding this process.
Is it possible to clone a SIM card
It is completely possible to clone a SIM card by extracting the secret codes from the card and copying them to a blank SIM card. Operator authentication on a SIM card is based on these codes, so transferring them to another blank card can help trick operators. This method mainly exploits a small glitch in GSM technology.
However, not all SIM cards can be cloned.
Only some. There are three main types of SIM card algorithms: COMP128v1, COMP128v2, and COMP128v3. COMP128v1 is currently the most popular SIM algorithm and luckily for us, it is the only one that can be cloned.
Now read on to find out how easy it is to clone a SIM card!
How to copy a SIM card in 2 minutes?
- Download and install two programs called MagicSIM and USB SIM Card Reader.
- Buy a blank programmable SIM card and a SIM card firmware reader and writer.
- Remove the target SIM card from your phone and place it in the SIM card reader / writer.
- In "MagicSIM" click "Read"
- When it's connected, select "Crack SIM" from the toolbar.
- Select the "Strong KI" parameter and select all other final parameters before clicking "Start".
- After the KI is detected and the jailbreak is complete, save your jailbroken SIM information to a new file.
- Click 'Disconnect' from the menu, otherwise the SIM card will be damaged.
- After successfully disconnecting, take out the SIM card and insert it into your phone.
- Now go to Phone Tools and select the "Unlock SIM" option. To unlock your SIM, you need to call your network provider to get the unlock code. They will ask you for basic information and then ask the reason why you want to unlock the SIM. You just need to tell them that you need to unlock it for international use.
- Once they give you the unlock code, enter it and unlock the SIM card. Insert a blank SIM card and access the "USB SIM Card Reader" software.
- When you select "Connect" you will receive a "Information not found" message. Select the "Write to SIM" option and select the ".dat" file you saved earlier.
- Click "Start" and wait for the process to complete. This will take approximately 10 minutes. If asked for a security code, enter the code provided by your network provider.
- With these steps, you will be able to successfully clone your SIM card until no one finds out! The writing process may seem quite complicated, but it is actually quite simple.
Part 6: How to copy text messages from Mobile Phone
Clone cell phone text messages is easy. You can do this with the apps we mentioned in parts 1-3.
Cocospy, mSpy, and Spyzie have a copy text message feature in their toolbars.
So when you choose this, you will get a complete log of all the target phone's text messages (sent, received and deleted), which can then be downloaded to another phone.
Part 7: How to know if my phone is cloned
Since cloning a phone is very easy, you may be concerned that someone else might have done it with your phone.
If so, you can check if your phone is cloned using the following methods:
- Ask your carrier for your mobile phone records. Check all outgoing calls and internet data usage to make sure you did it. If you are making calls to strange numbers, it is likely that someone has cloned your phone number.
- If you find anything unusual in the call recording, you can contact your operator and ask for a diagnostic test. If there are bugs or the phone is jailbroken, you will find it.
- Enter your number in a search service and see if it is present on unwanted sites that you do not use.
- Dial your own mobile number. If someone answered the call, it means that your SIM card has been cloned.
As soon as you find that your number has been hacked, do the following:
- Check all credit and debit cards to be sure no one has used them.
- Change PIN codes and passwords for all your accounts.
- Report the problem to your operator.
Conclusion
So now you know all about the best ways to clone phone number, SIM card and text messages.
When it comes to copying data from your phone without touching it, my personal recommendation is to use Cocospy as it is reliable, user-friendly and has a wide range of features.
mSpy is too expensive by comparison. And Spyzie isn't all that reliable or has such a good reputation. As we mentioned earlier, you can only clone iPhones over the air.
If you want to copy data from your phone to Android, physical access to it is absolutely essential.
Spyzie, Cocospy, and mSpy can help you clone phone content, including text messages. However, these apps cannot be used to clone a SIM card phone number.
To do this, you will either have to use the secret menu method, or you will have to clone the SIM card into a dummy, as shown in parts 4 and 5.
Finally, if you suspect that your phone has been cloned or jailbroken by someone, follow the instructions and precautions listed at the end of this article.
If you have any other questions about how to clone a phone without touching it, feel free to ask them in the comments section.
Hackers can redirect victims' SMS messages to their number for as little as $ 16
Some companies allow SMS messages to be redirected to another number without asking for permission for this operation and without even notifying the user.
A Motherboard specialist discovered a dangerous problem, the exploitation of which allows attackers to secretly redirect victims' SMS messages to their number by purchasing appropriate services from telecommunications companies.
As part of the attack, criminals use the services of companies that help businesses conduct SMS marketing and bulk messaging to discreetly redirect text messages and gain access to any two-factor authentication codes or links in text messages.
Some companies allow SMS messages to be redirected to another number without asking for permission for the operation or even notifying the user that their text messages are now being sent to someone else.
Researcher Joseph Cox asked his friend an information security expert to attack his number and redirect SMS messages to another number. The specialist used Sakari's service, and the attack cost him only $ 16.
“I used a prepaid card to purchase a monthly subscription for $ 16, and then I was able to steal a number by simply filling out a LOA (Letter of Authorization) form with fake information,” the expert explained.
The Letter of Authorization is a document that states that the signatory has the right to change phone numbers.
Hackers have found many ways to use SMS and cellular systems to access other people's messages - SIM swapping and attacks on SS7 networks have been widely used for several years, and sometimes even used against high-ranking targets. SIM swapping is fairly easy to detect as the phone is disconnected from the cellular network, but with SMS redirection it can take quite a while before the user notices the attack, giving attackers the opportunity to compromise their accounts.
Just a contribution to what is listed above.
Some companies allow SMS messages to be redirected to another number without asking for permission for this operation and without even notifying the user.
A Motherboard specialist discovered a dangerous problem, the exploitation of which allows attackers to secretly redirect victims' SMS messages to their number by purchasing appropriate services from telecommunications companies.
As part of the attack, criminals use the services of companies that help businesses conduct SMS marketing and bulk messaging to discreetly redirect text messages and gain access to any two-factor authentication codes or links in text messages.
Some companies allow SMS messages to be redirected to another number without asking for permission for the operation or even notifying the user that their text messages are now being sent to someone else.
Researcher Joseph Cox asked his friend an information security expert to attack his number and redirect SMS messages to another number. The specialist used Sakari's service, and the attack cost him only $ 16.
“I used a prepaid card to purchase a monthly subscription for $ 16, and then I was able to steal a number by simply filling out a LOA (Letter of Authorization) form with fake information,” the expert explained.
The Letter of Authorization is a document that states that the signatory has the right to change phone numbers.
Hackers have found many ways to use SMS and cellular systems to access other people's messages - SIM swapping and attacks on SS7 networks have been widely used for several years, and sometimes even used against high-ranking targets. SIM swapping is fairly easy to detect as the phone is disconnected from the cellular network, but with SMS redirection it can take quite a while before the user notices the attack, giving attackers the opportunity to compromise their accounts.
Just a contribution to what is listed above.
Similar threads
- Replies
- 0
- Views
- 24
- Replies
- 0
- Views
- 43
- Replies
- 0
- Views
- 79
- Replies
- 0
- Views
- 222
