Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,027
- Points
- 113

If you have enough knowledge to copy a file from folder to folder, then today you will learn how to securely encrypt your data.
Introduction
Almost everyone uses cloud storage, it's really convenient. I hope you understand that Google / Dropbox / Microsoft / Yandex regularly review what you store with them. By the way, in case of a request from law enforcement agencies, your data will be immediately issued.It is clear that the best option would be to store data on your own server using NextCloud (or other open source alternatives), but the goal of this article is to teach you how to securely encrypt data so that no one except you has access to it, be it Google, Dropbox, Yandex. or Comrade Major.
Installing Cryptomator
Installation of the program is as simple as possible, as they say "one-button". So you won't have any problems. Download Cryptomator for your system and install it.Website:

Cryptomator - Free Cloud Encryption for Dropbox & Co
Encrypt Dropbox, Google Drive, and any other cloud. Cryptomator is free and open source.
cryptomator.org
About the program
Cryptmator is completely free and open source software for encrypting data on the client side. In 2017, Cure53 conducted a penetration test, the report can be found here. All bugs found in the process have been fixed in version 1.1.0.The advantages of Cryptomator include:
- Using AES with 256 bit key;
- The vault password is protected from brute force attacks using scrypt;
- Creation and management of multiple storages at the same time;
- Can work with cloud storage (provided that the cloud storage folder is already mounted on your computer);
- Uses WebDAV or FUSE (macOS and Linux only) and Dokany (Windows);
- Easy to install, easy to use;
When you open the vault with Cryptomator, it will appear as a virtual drive. You can work with it like a regular USB stick.
The encrypted data is stored in a regular folder. If you open the repository without Cryptomator, you will see only a set of directories and files with incomprehensible names. You can recognize that this Cryptomator repository is based on the masterkey.cryptomator file located inside the folder.
The program is really very easy to use. After the first launch, you will see an empty list, and a hint that you can create new repositories:
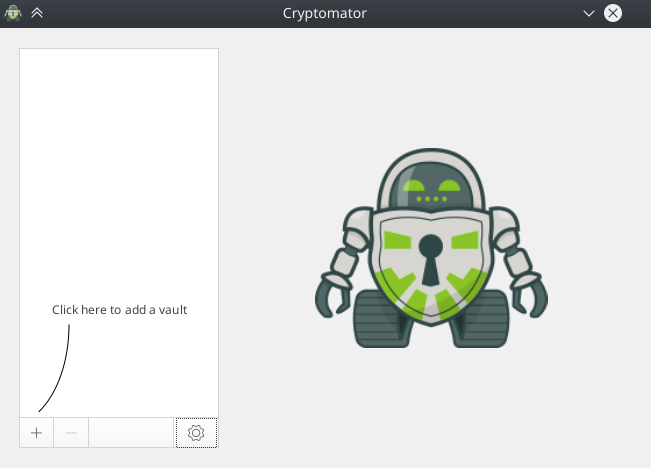
Create a repository
Just four steps:- Click on the "+" button;
- Select "Create new storage"; (Create New Vault)

As you can see, there is a second option "Open an existing repository" (Open Existing Vault), yet you have no storage, so you first create it.
3. Specify a location for the repository, give it a name and click "Save" (Save):
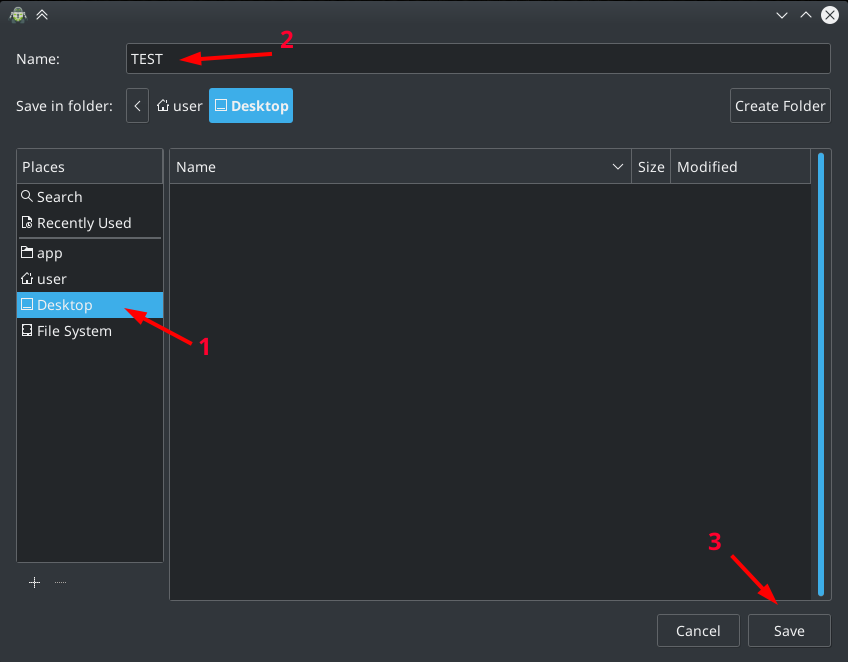
I specified " Desktop " (Desktop), gave the name "TEST".
After that Cryptomator will offer to set a password for this repository.
First, you must set a good password to securely protect your vault.
Secondly, if you forget / lose this password, then you will permanently lose access to your data! This password cannot be reset or recovered:
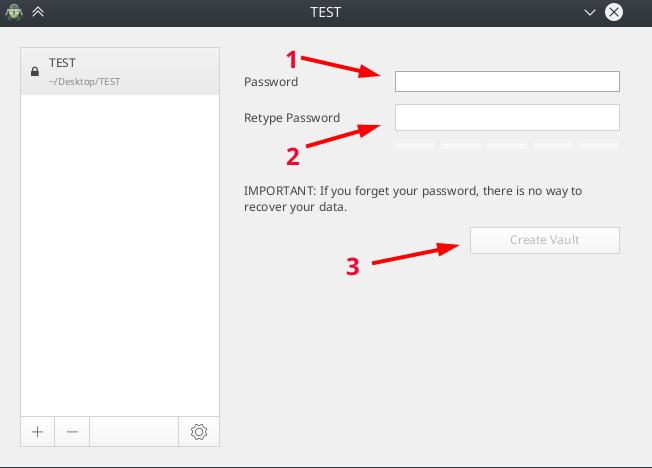
4) Set a password and click "Create Repository" (Create Vault)
Congratulations, you've created your first repository.
Inside the vault
If you just open the storage folder you will see:
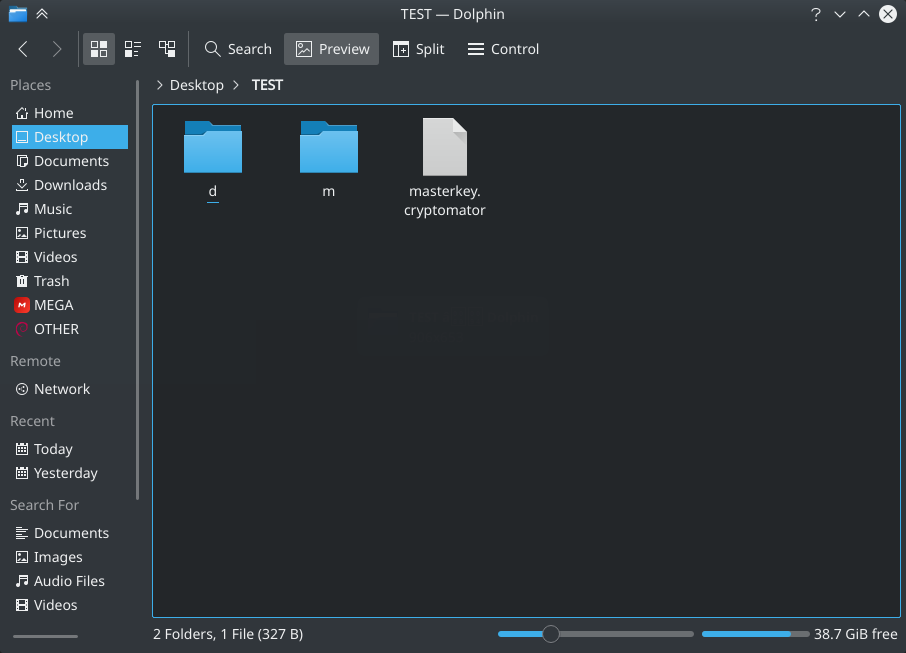
You do not need to memorize the following information, I just want you to better understand the "internals" of the storage.
Folder d - encrypted data will be stored here.
Folder m - metadata (currently only used for name abbreviations).
The masterkey.cryptomator file contains encrypted data that is required to obtain a password-based master key. The file itself does not contain the decrypted master key, so it is insensitive and must be stored along with the storage in the cloud. In addition, this file also stores some metadata about the vault (for example, the version of Cryptomator used to create it). Also, it provides convenient access to storage on various devices.
After you start using the repository, a .bkup file appears , which is a backup copy of your master key file. It is created after each successful vault unlocking.
All of the above is part of the repository and you should not rename / move / delete anything in this folder. If in the future you need to delete any data from the storage, you must open the storage through Cryptomator, and then delete the data.
For the sake of testing, I will upload an mp3 file to the repository and show how it will look to an outside observer.
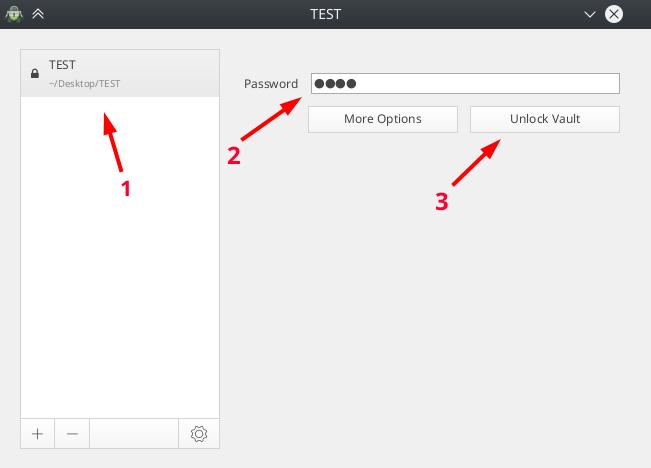
To open a repository, select it from the list, enter a password and click on " Unlock repository » (Unlock Vault).
Yes, my password is 1234, because this is a test store. But, you must set a good password to reliably protect your data:
After you unlock the vault, the file manager will automatically open and your vault will be mounted:
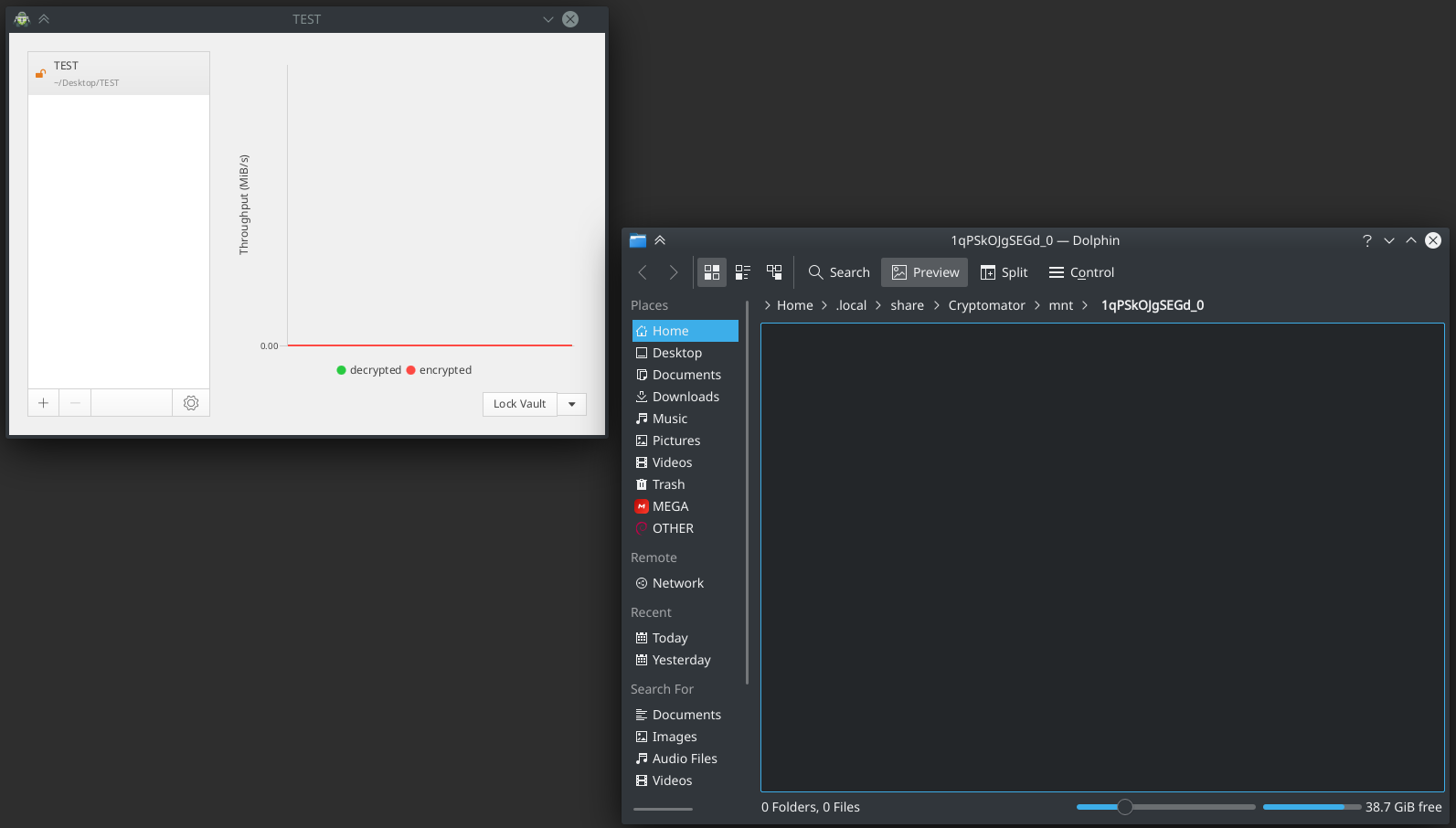
Everything, the storage is mounted and ready to go. Now you can upload an mp3 file there:
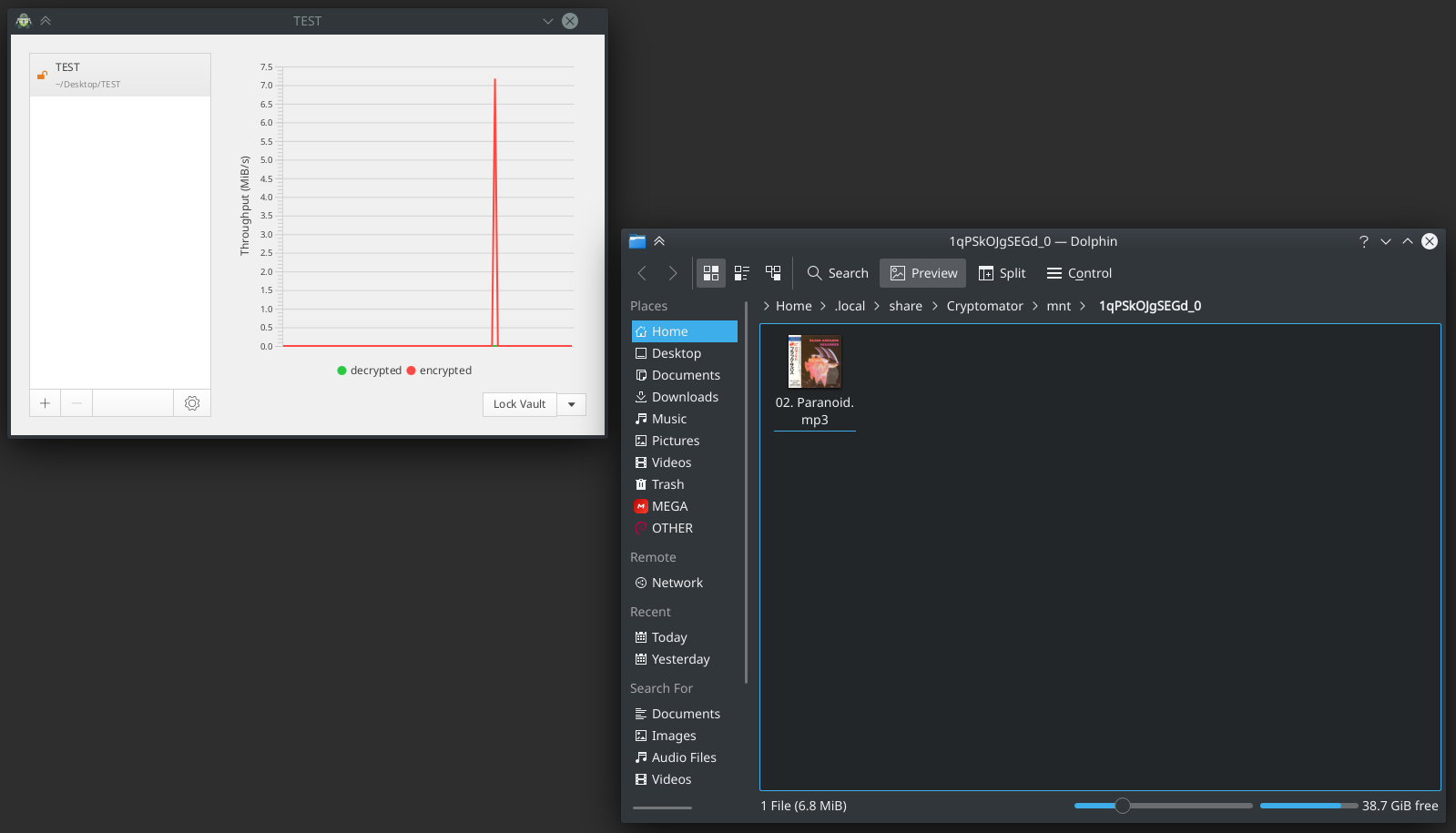
As you can see, Cryptomator processed and encrypted the test mp3 file in less than one second. That's it, I finished working with this storage, and now it needs to be locked. To do this, click on " Lock Vault " (Lock Vault).
*** Note. After you finish working with a particular vault, be sure to lock it.
That's it, the test storage is ready to be sent to the cloud. This is how the cloud provider will see this test storage with an mp3 file inside (it is not even clear that it is an mp3 file):
At the end of this article, I will give my opinion about services such as Google / Dropbox / Microsoft / Yandex, and what theoretical danger your data will face (no, this is not a cipher breaking).
What is the difference between Cryptomator storage and VeraCrypt container?
When using VeraCrypt or other container-based encryption software, all files stored in the container are combined into one large container file, and this creates certain inconveniences. It is inconvenient to work with such container files in the cloud, because in order to change any file in the container, you will have to download the entire container, make changes and upload the container to the cloud again.*** NOTE. Dear reader, if you have been using VeraCrypt to encrypt your data for many years, this is a great choice! I have also been using VeraCrypt for years. The purpose of this article is not to say that VeraCrypt is worse / better than Cryptomator, but that these are quite different tools.
Also, when using VeraCrypt, you may encounter the following situation. For example, you have a VeraCrypt container in the cloud (or offline), the size of which is 1GB. You spent some time creating it, set a good password, etc. Let's say you have additional data in the amount of 500 MB that you want to add to this container. You will not be able to expand an existing container, and you will have to create a new container to put the data from the first container (1 GB) + add new data (500 MB) there.
Also note that if more than one computer must have access to the encrypted container at the same time, this is not possible with VeraCrypt containers.
Cryptomator is optimized for use with cloud storage, which can also be used locally (offline).
When using Cryptomator, each file is encrypted separately. And changing any file leads to reloading only this file to the cloud, and not the entire storage. In addition, Cryptomator has integrated change detection and conflict resolution, allowing you to conveniently and securely use cloud storage even from mobile devices. The Cryptomator storage changes dynamically, that is, if you take the example above (you have a storage for 1 GB of data and you need to add another 500 MB of data), then you simply add the required amount of data to the storage, Cryptomator will encrypt them and the total volume of your storage will increase to ~ 1.5 GB. Of course, the individual encryption of each file also means that Cryptomator cannot hide the modification date and file size information.
What's cooler? Cryptomator vs VeraCrypt
Oddly enough, there are quite a few questions on this topic on the net. Personally, I am of the opinion that it all depends on your tasks, since these are quite different tools.Some "dry" information
Veracrypt allows the user to customize ciphers and their key lengths. This is useful for users who know exactly what they are doing.
The philosophy in Cryptomator is different. It uses ciphers and configurations that are known to work well with each other. The prefabricated cipher suite in Cryptomator means less complexity for the end user, as well as less room for attack. On the other hand, if AES is hacked, Cryptomator users will not be able to simply switch to a new algorithm from the drop-down list (like in VeraCrypt), they will have to wait until a new Cryptomator release is released.
Cryptomator developers do not want to provide the user with all the possibilities in choosing ciphers and their configurations, not because they have evil intentions, but because they want to offer the most simple and secure application, and I want to note that they are very good at it.
Veracrypt only creates one container, so an outside observer won't even know how many files are in the container. Also, the VeraCrypt container can be disguised as mp3 / mp4 / dat / dll (or other file types), then an outside observer will not understand at all that you have a container. For example, you disguised your container as a Black Sabbath file - Paranoid.mp3 , for your operating system it will look like an mp3 file, it will even automatically open with a music player, but there will be no playback, you will see an error. Also, if someone on your device finds a 10 GB mp3 file that cannot be opened through the music player, agree that such a file may raise suspicion.
Outwardly, the VeraCrypt crypto-container does not differ from the file under which it is masked (mp3 / mp4 / avi or others), but there are internal differences - many file types have a characteristic binary header, which can be used to determine, for example, that mp3 the file is not actually an mp3 file. There are also untyped binaries, among which there is often a file with the * .dat extension , by the contents of which it is impossible to understand what is inside, so you can consider disguising the VeraCrypt container as a * .dat file.
Cryptomator encrypts each file separately. This allows you to conveniently synchronize data in the cloud that has really changed, but at the same time an outside observer sees the total amount of information in the storage.
It is convenient to encrypt your entire USB drive with Veracrypt. You can also encrypt the system drive in Windows (for example, Cryptomator cannot do this). In addition, VeraCrypt has the ability to create a double bottom container. The scheme of working with such containers is simple: when you enter one password, one container opens, when you enter the second, another. This can be useful in the case when you are forced to enter the password for the container, then you can open the container and show that there is nothing there, or that there are a couple of personal photos stored there.
It is more convenient to use Cryptomator to synchronize encrypted files on any server / cloud, or use it offline.
Dangers in conjunction with Google Drive / Microsoft OneDrive / Dropbox / Yandex Disk, etc.
Do you think I'll say that something is wrong with Cryptomator, that it has some kind of backdoor tab for special services? No, everything is much simpler. When using Google Disk / Microsoft OneDrive / Yandex Disk or others, there is always a chance that they will simply block your account. They may not like the fact that they cannot see your data.Thank you for the attention.

