Lord777
Professional
- Messages
- 2,576
- Reaction score
- 1,552
- Points
- 113
Content
1. Brief information
2. Why is it not safe?
3. How to check
4. How to disable it
4.1 Firefox
4.2 Usage statistics.
4.3 Chrome/Chromium
WebRTC (Web Real-Time Communication) is an open source technology that allows streaming data between browsers using point — to-point (p2p) technology.
WebRTC is built in by default in the latest versions of Firefox, Chrome/Chromium, and Opera, and allows you to connect between two or more browsers for video / audio calls and more.
The fact is that for a p2p connection, you need to know the real IP address and WebRTC shamelessly merges this information. Even if you are sitting under TOR / VPN, it will not be difficult to find out your local IP address on the network and on the side of, for example, a VPN server. And with the use of vulnerabilities, you can determine your real IP address, behind which you are hiding.
The JavaScript code and description are available on the following page: https://github.com/diafygi/webrtc-ips
To check whether the camera, audio, screen capture, etc. are enabled in the browser, follow the link: https://www.browserleaks.com/webrtc
In addition, you need to disable the following services::
Chromium and Firefox-based browsers support WebRTC technology for audio and video chats directly from the browser window. In addition to convenience, this feature has an unpleasant side effect.
In particular, WebRTC allows sending requests to STUN servers that return the user's local and public IP addresses. Such requests can be made using a script, so IP addresses are displayed using JavaScript.
Requests are sent bypassing the standard XMLHttpRequest procedure and are not visible from the developer console. You can't block them with plugins like AdBlockPlus or Ghostery. Thus, these queries can be used, for example, by advertisers to secretly track users.
On this demo page, you will see your own local and external IP address.
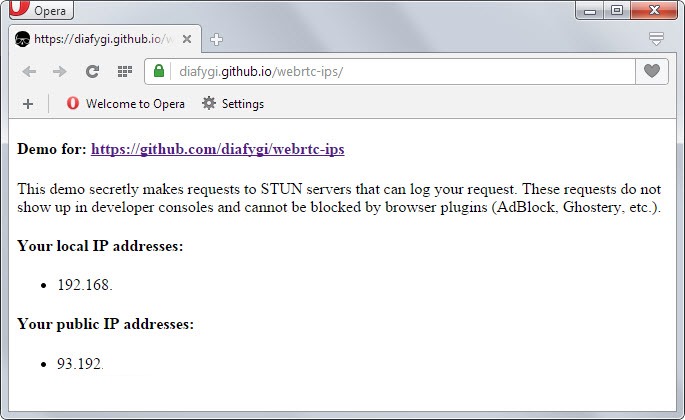
This code works in Firefox and Chrome. You can copy it to the developer console for testing.
The only extensions that block such requests are extensions that completely prohibit script execution, like NoScript for Firefox. Of course, there is also an option in the browser settings to disable scripts.
Click to rate this post!
(c) https://cryptoworld.su/как-отключить-webrtc-в-браузере-firefox-и-chrome/
1. Brief information
2. Why is it not safe?
3. How to check
4. How to disable it
4.1 Firefox
4.2 Usage statistics.
4.3 Chrome/Chromium
WebRTC (Web Real-Time Communication) is an open source technology that allows streaming data between browsers using point — to-point (p2p) technology.
WebRTC is built in by default in the latest versions of Firefox, Chrome/Chromium, and Opera, and allows you to connect between two or more browsers for video / audio calls and more.
Why isn't it safe?
The fact is that for a p2p connection, you need to know the real IP address and WebRTC shamelessly merges this information. Even if you are sitting under TOR / VPN, it will not be difficult to find out your local IP address on the network and on the side of, for example, a VPN server. And with the use of vulnerabilities, you can determine your real IP address, behind which you are hiding.
How to check it
To check the local IP address, use the page: https://diafygi.github.io/webrtc-ips/The JavaScript code and description are available on the following page: https://github.com/diafygi/webrtc-ips
To check whether the camera, audio, screen capture, etc. are enabled in the browser, follow the link: https://www.browserleaks.com/webrtc
How to disable it
Firefox
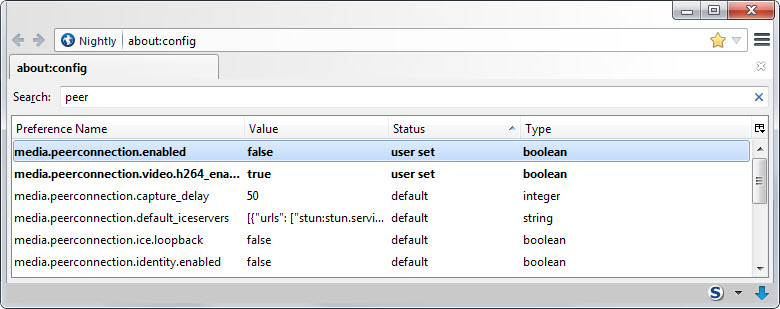
We call the hidden software settings about:configin the address bar, search for the parameter media.peerconnection.enabled, and set it to false.
Code:
[ad name=»Responbl»]In addition, you need to disable the following services::
Google Safe Browsing
Which merges your browsing history to Google. You need a warning that disabling Safe Browsing increases the risk of getting infected as a result of visiting a malicious site.
Code:
browser.safebrowsing.enabled
browser.safebrowsing.downloads.enabled
browser.safebrowsing.malware.enabledFirefox Statistics
Sends stability and performance reports to Mozilla.
Code:
datareporting.healthreport.service.enabled
datareporting.healthreport.uploadEnabledUsage statistics.
Code:
toolkit.telemetry.enabledEncrypted Media Extensions (DRM)
A binary plugin with unknown source code that comes with Firefox starting with version V. 38. Allows you to play encrypted media content and use Netflix, etc. without Microsoft Silverlight. To completely remove the plugin, you need to install the EME-free version of the Firefox browser.
Code:
media.eme.enabled
media.gmp-eme-adobe.enabledFirefox Hello
Firefox connects to third-party servers (Telefonica) without permission.
Code:
loop.enabledIntegration with Pocket
A third-party service for managing the list of articles that you have set aside for reading.
Code:
browser.pocket.enabledGeolocation
Code:
geo.enabledSearch suggestions
Everything typed in the search bar is sent to the search engine. If you disable this option, suggestions will continue to work, but only based on the local search history.
Code:
browser.search.suggest.enabledProtection from site surveillance
Unlike all the options listed above, you should enable this option instead. This is necessary to actively block sites that are known for their incorrect behavior in relation to tracking users. Not to be confused with DNT, which only "asks" sites not to track you. Here you can also apply a forced lock.
Code:
privacy.trackingprotection.enabledChrome/Chromium
It is disabled only by installing a small extension (~10 kb): WebRTC Block, although the local IP address of the browser does not stop shining.Chromium and Firefox-based browsers support WebRTC technology for audio and video chats directly from the browser window. In addition to convenience, this feature has an unpleasant side effect.
In particular, WebRTC allows sending requests to STUN servers that return the user's local and public IP addresses. Such requests can be made using a script, so IP addresses are displayed using JavaScript.
Requests are sent bypassing the standard XMLHttpRequest procedure and are not visible from the developer console. You can't block them with plugins like AdBlockPlus or Ghostery. Thus, these queries can be used, for example, by advertisers to secretly track users.
On this demo page, you will see your own local and external IP address.

This code works in Firefox and Chrome. You can copy it to the developer console for testing.
Code:
//get the IP addresses associated with an account
function getIPs(callback){
var ip_dups = {};
//compatibility for firefox and chrome
var RTCPeerConnection = window.RTCPeerConnection
|| window.mozRTCPeerConnection
|| window.webkitRTCPeerConnection;
var mediaConstraints = {
optional: [{RtpDataChannels: true}]
};
//firefox already has a default stun server in about:config
// media.peerconnection.default_iceservers =
// [{"url": "stun:stun.services.mozilla.com"}]
var servers = undefined;
//add same stun server for chrome
if(window.webkitRTCPeerConnection)
servers = {iceServers: [{urls: "stun:stun.services.mozilla.com"}]};
//construct a new RTCPeerConnection
var pc = new RTCPeerConnection(servers, mediaConstraints);
//listen for candidate events
pc.onicecandidate = function(ice){
//skip non-candidate events
if(ice.candidate){
//match just the IP address
var ip_regex = /([0-9]{1,3}(.[0-9]{1,3}){3})/
var ip_addr = ip_regex.exec(ice.candidate.candidate)[1];
//remove duplicates
if(ip_dups[ip_addr] === undefined)
callback(ip_addr);
ip_dups[ip_addr] = true;
}
};
//create a bogus data channel
pc.createDataChannel("");
//create an offer sdp
pc.createOffer(function(result){
//trigger the stun server request
pc.setLocalDescription(result, function(){}, function(){});
}, function(){});
}
//Test: Print the IP addresses into the console
getIPs(function(ip){console.log(ip);});The only extensions that block such requests are extensions that completely prohibit script execution, like NoScript for Firefox. Of course, there is also an option in the browser settings to disable scripts.

Click to rate this post!
(c) https://cryptoworld.su/как-отключить-webrtc-в-браузере-firefox-и-chrome/

