Man
Professional
- Messages
- 3,223
- Reaction score
- 1,151
- Points
- 113
Contents of the article:
Imagine this situation: an anonymous person calls from a disposable phone and blackmails or demands ransom for a person he has kidnapped. A few days later, the criminal calls again. The victim calls the police, and within an hour, the officers determine not only the real number of the attacker, but also the entire history of his movements and incoming and outgoing calls. And all this without complex equipment and technology, fake base stations and signal interception.
According to Australian law, mobile operators must store certain information about network users, the Call detail record database, for two years. This includes data on the location of the phone at any given time (by the way, recently in Sweden, which never ceases to amaze, there was a case where this information was not enough to pass a sentence), a call log, including information about the other subscriber, and data on Internet sessions. As for SMS, according to the Australian Privacy Act, without prior authorization for wiretapping, the operator has the right (and is obliged) to save only metadata: the time of sending, the size of the message and the addressee. The content of the SMS messages themselves (and especially voice calls) is not saved.
This is what the information collected about a journalist by a cameraman looks like.

Places visited by the journalist on April 1, 2015.
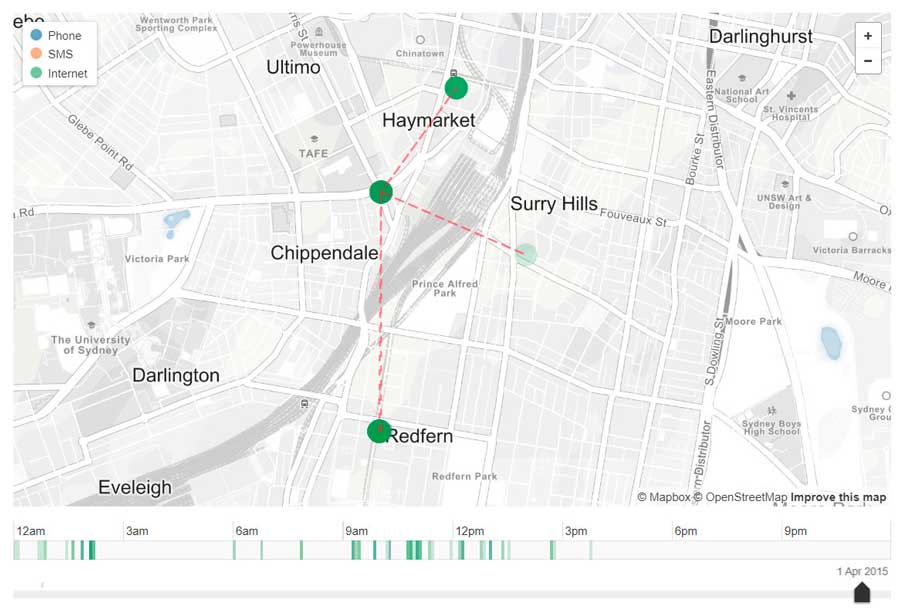
The places he visited most often during a given time period.

Interactive versions of this data are available at the link.
Metadata includes information about who the user called and texted, the duration of calls, and what base stations the phone connected to at what point in time (this information allows the location of the device to be determined quite accurately). In some countries, operators not only provide user location information to the police, but are also happy to sell such data.
The most interesting thing is that mobile operators have access to (and give it to the police, and also sell it to anyone who wants it) details about internet usage, including website addresses and the amount of data transferred. This is a completely separate topic for discussion; the data is collected by tracking requests to the provider's DNS servers. The operators are also happy to trade this data; the bait is so attractive that the operators have even tried to block clients from using third-party DNS servers.
Mobile operators in the United States are required to store CDR records. In addition, the United States maintains a single database, MAINWAY, in which records can be stored much longer than the mobile operators themselves are legally allowed to do.
In Russia, the so-called Yarovaya Law has been adopted, which obliges mobile operators to store metadata for three years (their list almost completely coincides with the Australian version of the law). In addition, since October of last year, operators are required to store text, voice, video and other messages of users for at least 30 days (but not more than six months). Accordingly, in Russia, any call must be recorded by the operator and provided to the police upon legal request.

By comparison, in the US, police requested information on 19,318 devices in the same year (81% of the requests were successful). Google offers an interactive chart, which you can view here.
And if Apple doesn't give the police data like user passwords, device usage statistics, SMS/iMessage messages, and Health data (the user's physical activity history, including the number of steps and heart rate over a given time period - a very useful thing for catching both criminals and unfaithful spouses), then Google will give up everything, including passwords (to be completely technically correct, I will add that Android 9 introduced encryption of backups; accordingly, the police will not receive either the backups themselves, or the SMS and call logs stored in them).
In order to get at least some information about a suspect, the police need at least one clue - IMEI is quite enough. But what can be determined from the identifier of a device that was turned on for only a few minutes? Having read a lot of conspiracy theories (a great example), novice criminals reverently remove the battery from the phone, turning on the device, only to make a call.
Of course, none of them even think about what happens when the device is turned on and off (both normally and in an emergency, with the battery removed). Moreover, few people think about whether the police operatives know about such a pattern.
Confident in his safety, the criminal leaves home (if he doesn't leave, his location will most likely be determined immediately or after the fact, by analyzing the logs) and calls from a disposable phone. Where is his main phone? Let's consider the options.
The police request the mobile operator to provide CDR records for the specified period. Depending on the country and its laws, the operator returns either raw data or an anonymized list of devices (each hardware identifier is replaced with a hash function). In fact, the police receive a ready-made list of devices connected to the cell where the device from which the call was made was registered. It is assumed that the offender's own phone will be among these devices.
Several thousand subscribers can be connected to the same cell at the same time, so a single request will give the police little information. However, if the criminal calls the victim again - no matter from the same cell or from another (from another is even better) - the police will receive additional samples. Then the sets of devices that were registered in the same cell at the time of the call from the "anonymous" device intersect; as a rule, only a few dozen, or even single identifiers remain in the second or third sample.
Of course, in practice, everything is somewhat more complicated. For example, not only the connection to the specific tower from which the call was made is taken into account, but also data from neighboring towers. Using this data allows (and allowed, by the way, even fifteen years ago) to perform triangulation, determining the location of the device with an accuracy of several dozen to several hundred meters. Agree, it is much more pleasant to work with such a sample.
However, in large cities with a high population density (anonymous calls are often made in crowded places), the circle of suspects even as a result of the third sample may be too large. In such cases (not always, but in particularly important cases), the analysis of "big data" comes into play. The analyst examines the behavior patterns of devices designated by conditional identifiers. Telephone conversations, active traffic consumption, movements in space, time of registration in the cell and a number of additional parameters allow you to exclude a significant number of devices, thereby significantly reducing the circle of suspects.
Conclusion: it is easiest to detect a criminal who has a personal device (personal smartphone) and who is moving. Make an anonymous call from one cell - many devices are outlined. Make a second call from another cell - and the list of devices following the same route is reduced by an order of magnitude.
By the way, I will debunk a popular movie template. For the exact determination of the phone's location, the time it was online does not play the slightest role: the location is determined instantly when the phone is registered on the network and is saved in the logs, from where it can be easily retrieved. If the device moves, the location can be determined even more accurately. At the same time, let's go over the conspiracy theorists: a switched off phone does not report its location, even if you do not remove the battery from it (well, the iPhone 11 can report thanks to the U1 chip , and even then not now, but sometime in the future, when Apple includes this feature in the firmware).
To summarize: the criminal turned on the device, made an anonymous call or sent an SMS, turned off the device or removed the battery. The next day, he turned it on again, called from another part of the city, turned it off. The list of devices that could belong to the criminal was reduced to several. The third call allowed us to finally identify the criminal, we can leave. All this without using any special equipment, a simple analysis of the logs for three activations.
Why is that? The thing is that when the phone is turned off, it sends a signal to the cell, and this allows us to distinguish between devices that were turned off and those that left the cell. When turned on, a new record is created accordingly. Tracking such activities is not difficult.
If the criminal really never takes a phone with him (practice shows that usually everyone makes a mistake at least once), then big data analysis can help to identify him. Much here will depend on how much time and how much effort the attacker is ready to put into making an anonymous call, as well as on how many such calls there will be.
Surprisingly, such criminals are often caught using operational and investigative measures that were developed back in the days of calls from street payphones. If the criminal has a permanent smartphone, then the circle of suspects can be sharply limited by conducting an analysis using the first of the methods described in the article. Thus, even in a city with a population of over a million, the circle of suspects is narrowed to several hundred (rarely - thousands) subscribers. If we are talking about "mining" a school, then many "suspicious" subscribers intersect with many students of the school. It will be enough for the operative to simply talk to those who remain.
Another factor that helps in uncovering telephone terrorism is that such criminals, as a rule, have a poor understanding of the capabilities and features of the work of operatives and try to protect themselves from invented, non-existent dangers, completely ignoring the obvious. Two years ago, employees of one of the neighboring offices (developers of programs for the police) were evacuated by a call from an unknown person who reported an explosive device in the building. Less than a few hours later, the police detained the criminal. The criminal turned out to be a crazy granny who wanted to annoy her neighbors, but mixed up the address. Neither a specially purchased push-button phone by the vengeful old lady, nor an “anonymous” (or rather, registered to a non-existent full name) SIM card helped.
Of course, there is always the possibility of “getting screwed up” by forgetting to control the connection to the VPN server or accidentally logging in with your own, not “anonymous” data for calls. To prevent this from happening, criminal groups go to great lengths to order the production of modified (at the software level) phones. The case of the arrest of the CEO of a company producing such devices based on old BlackBerry phones showed the scale of the operations. Although the police managed to shut down this criminal network (and gain control over the encrypted communications infrastructure used by the criminals), the police understand that this is only the first step. “Criminals inevitably migrate to other services, and we know which ones.

And a little more detail.

All the police need is the raw CDR data itself and software that can download and analyze it (raw data is of little use for manual analysis, but filtered data can be easily displayed on the screen in text form or printed).
The popularity of this method of investigation is evidenced by the fact that CDR records are supported by almost every serious forensic package. Examples: Penlink, HAWK Analytics, GeoTime, CSAS, the Russian "Mobile Forensic" from Oxygen Software, Advanced Cell Tracking and many others. However, police officers successfully use a combination of Google Maps and Microsoft Excel in their work.
Of course, the special services have special equipment that allows them to jam cellular communications, replace the base station, or fake GPS coordinates. But the police do not use most of this equipment - at least not in investigating routine crimes of telephone terrorists and extortionists. It is expensive, fussy, time-consuming, and by and large unnecessary, and sometimes ineffective. Analysis of CDR (Call Detail Record) logs is a much more effective investment of time and effort.
A case that happened a few years ago in the UK is illustrative. The police were monitoring a drug cartel boss. It would not be a problem to arrest him, but there was no evidence, and the case would have fallen apart in court. According to the police, the criminal’s phone (he used an iPhone) could contain vital evidence, but it was impossible to crack the lock code of a fairly new model at that time. As a result, an operation was developed; the criminal was monitored. As soon as he took the phone, unlocked it and started typing, the drug lord was detained, and the phone was literally snatched from his hands.
What's interesting here is not the background, but this minor detail: in order to deliver the criminal's iPhone to the lab in an unlocked state, a special police officer was assigned, whose entire job was to periodically swipe the screen, preventing the device from falling asleep. (There's no need to think of the police as simpletons: everyone knows that there is a setting that controls the time after which the phone's screen turns off and the phone itself is locked. But not everyone knows that you can easily, in a couple of clicks, install a configuration profile on your phone that prohibits disabling the automatic lock.) The phone was successfully delivered to the lab, the data was extracted, and the necessary evidence was obtained.
Most police training courses teach that digital evidence cannot be trusted completely, no matter how it was obtained. Cases are told where a suspect’s location was determined based on metadata from photographs that were synced via the cloud, rather than taken by the device itself.
An illustrative case is when answering an incoming call was interpreted as "distraction while driving", which led to an emergency situation. In fact, the push-button phone, which was still a push-button phone at the time, was peacefully lying in the driver's pocket, but due to an accidentally pressed button, the phone "answered" the call, which was recorded by the operator. The defense was able to acquit the driver by interrogating the second subscriber, who testified that the conversation did not take place (by the way, what "really" happened there is unknown, but the court sided with the accused).
I am sure that such a case is far from unique. CDR data is a great tool in the hands of an operative, but unreliable as an evidence base.
Getting such a lead is the result of a regular, routine analysis of mobile operators' logs. No special equipment is needed, no conspiracy theories are needed, everything happens much more simply and interestingly. Instead of chases and shooting, there is desk work with an analytical program, a simple database, or even printouts.
Source
- How to Catch Criminals Using Phones
- Not just CDR
- Disposable phones
- Calculate by phone. Case 1
- Calculate by phone. Case 2
- Calculate by phone. Case 3
- What if there are many anonymous devices?
- But what if there really was just one call?
- What if you make calls via VoIP using VPN?
- How does the analysis take place?
- Somehow this is all… unreliable!
- Total
Imagine this situation: an anonymous person calls from a disposable phone and blackmails or demands ransom for a person he has kidnapped. A few days later, the criminal calls again. The victim calls the police, and within an hour, the officers determine not only the real number of the attacker, but also the entire history of his movements and incoming and outgoing calls. And all this without complex equipment and technology, fake base stations and signal interception.
How to Catch Criminals Using Phones
The first thing the police do is not try to hack or intercept anything, but simply make a request to the mobile operator, and the latter will send them not only the call history, but also a lot of other confidential information. As an example: an article about an Australian journalist, which analyzed the information collected about the journalist himself by his mobile operator over the past two years (and only that).According to Australian law, mobile operators must store certain information about network users, the Call detail record database, for two years. This includes data on the location of the phone at any given time (by the way, recently in Sweden, which never ceases to amaze, there was a case where this information was not enough to pass a sentence), a call log, including information about the other subscriber, and data on Internet sessions. As for SMS, according to the Australian Privacy Act, without prior authorization for wiretapping, the operator has the right (and is obliged) to save only metadata: the time of sending, the size of the message and the addressee. The content of the SMS messages themselves (and especially voice calls) is not saved.
This is what the information collected about a journalist by a cameraman looks like.
Places visited by the journalist on April 1, 2015.
The places he visited most often during a given time period.
Interactive versions of this data are available at the link.
Metadata includes information about who the user called and texted, the duration of calls, and what base stations the phone connected to at what point in time (this information allows the location of the device to be determined quite accurately). In some countries, operators not only provide user location information to the police, but are also happy to sell such data.
The most interesting thing is that mobile operators have access to (and give it to the police, and also sell it to anyone who wants it) details about internet usage, including website addresses and the amount of data transferred. This is a completely separate topic for discussion; the data is collected by tracking requests to the provider's DNS servers. The operators are also happy to trade this data; the bait is so attractive that the operators have even tried to block clients from using third-party DNS servers.
By the way, devices issued (imposed) by stationary Internet providers (usually a combined cable or ADSL modem + router) often do not allow changing the DNS server on the router. If you want, change it on your computer, on each individual phone, smart TV and speaker, but the user will not be able to fully protect his privacy by simply setting the router settings.
Mobile operators in the United States are required to store CDR records. In addition, the United States maintains a single database, MAINWAY, in which records can be stored much longer than the mobile operators themselves are legally allowed to do.
In Russia, the so-called Yarovaya Law has been adopted, which obliges mobile operators to store metadata for three years (their list almost completely coincides with the Australian version of the law). In addition, since October of last year, operators are required to store text, voice, video and other messages of users for at least 30 days (but not more than six months). Accordingly, in Russia, any call must be recorded by the operator and provided to the police upon legal request.
Not just CDR
In the above study, journalist Will Ockenden used an iPhone. A properly completed request to Apple (in the company's terminology, a Device Request, i.e. a request in which the police have nothing but the hardware identifier of the device - IMEI) will allow the police to obtain the data that Apple collects about the user, and this includes almost everything with rare exceptions. For example, this is what the statistics of requests to Apple in Russia look like.By comparison, in the US, police requested information on 19,318 devices in the same year (81% of the requests were successful). Google offers an interactive chart, which you can view here.
And if Apple doesn't give the police data like user passwords, device usage statistics, SMS/iMessage messages, and Health data (the user's physical activity history, including the number of steps and heart rate over a given time period - a very useful thing for catching both criminals and unfaithful spouses), then Google will give up everything, including passwords (to be completely technically correct, I will add that Android 9 introduced encryption of backups; accordingly, the police will not receive either the backups themselves, or the SMS and call logs stored in them).
Disposable phones
Criminals who use their main phone to make threatening calls, extort money, and commit other criminal offenses are now almost non-existent; we have discussed why in detail above. What is left for the criminal? Disposable SIM cards (we will probably not discuss the methods by which criminals acquire such cards) and disposable (usually cheap push-button) devices, preferably without any Internet access at all.In order to get at least some information about a suspect, the police need at least one clue - IMEI is quite enough. But what can be determined from the identifier of a device that was turned on for only a few minutes? Having read a lot of conspiracy theories (a great example), novice criminals reverently remove the battery from the phone, turning on the device, only to make a call.
Of course, none of them even think about what happens when the device is turned on and off (both normally and in an emergency, with the battery removed). Moreover, few people think about whether the police operatives know about such a pattern.
Confident in his safety, the criminal leaves home (if he doesn't leave, his location will most likely be determined immediately or after the fact, by analyzing the logs) and calls from a disposable phone. Where is his main phone? Let's consider the options.
Calculate by phone. Case 1
Let's start by looking at the most typical situation: a "suspicious" call is made from a disposable, "anonymous" phone, and the criminal has taken his own phone with him. There is nothing incredible about this; it is enough to read the police reports to understand that this is how most people act.The police request the mobile operator to provide CDR records for the specified period. Depending on the country and its laws, the operator returns either raw data or an anonymized list of devices (each hardware identifier is replaced with a hash function). In fact, the police receive a ready-made list of devices connected to the cell where the device from which the call was made was registered. It is assumed that the offender's own phone will be among these devices.
Several thousand subscribers can be connected to the same cell at the same time, so a single request will give the police little information. However, if the criminal calls the victim again - no matter from the same cell or from another (from another is even better) - the police will receive additional samples. Then the sets of devices that were registered in the same cell at the time of the call from the "anonymous" device intersect; as a rule, only a few dozen, or even single identifiers remain in the second or third sample.
Of course, in practice, everything is somewhat more complicated. For example, not only the connection to the specific tower from which the call was made is taken into account, but also data from neighboring towers. Using this data allows (and allowed, by the way, even fifteen years ago) to perform triangulation, determining the location of the device with an accuracy of several dozen to several hundred meters. Agree, it is much more pleasant to work with such a sample.
However, in large cities with a high population density (anonymous calls are often made in crowded places), the circle of suspects even as a result of the third sample may be too large. In such cases (not always, but in particularly important cases), the analysis of "big data" comes into play. The analyst examines the behavior patterns of devices designated by conditional identifiers. Telephone conversations, active traffic consumption, movements in space, time of registration in the cell and a number of additional parameters allow you to exclude a significant number of devices, thereby significantly reducing the circle of suspects.
Conclusion: it is easiest to detect a criminal who has a personal device (personal smartphone) and who is moving. Make an anonymous call from one cell - many devices are outlined. Make a second call from another cell - and the list of devices following the same route is reduced by an order of magnitude.
By the way, I will debunk a popular movie template. For the exact determination of the phone's location, the time it was online does not play the slightest role: the location is determined instantly when the phone is registered on the network and is saved in the logs, from where it can be easily retrieved. If the device moves, the location can be determined even more accurately. At the same time, let's go over the conspiracy theorists: a switched off phone does not report its location, even if you do not remove the battery from it (well, the iPhone 11 can report thanks to the U1 chip , and even then not now, but sometime in the future, when Apple includes this feature in the firmware).
To summarize: the criminal turned on the device, made an anonymous call or sent an SMS, turned off the device or removed the battery. The next day, he turned it on again, called from another part of the city, turned it off. The list of devices that could belong to the criminal was reduced to several. The third call allowed us to finally identify the criminal, we can leave. All this without using any special equipment, a simple analysis of the logs for three activations.
Calculate by phone. Case 2
"Who goes to work with their phone on?" you might logically ask. Indeed, a prudent criminal can turn off their main phone before making a call from an anonymous device. Very good: now the police only need to look at the list of devices that were turned off at the time of the anonymous call. In this case, one iteration will be enough. If the criminal also turns on his main phone after the anonymous call, then you can safely send an operational team after him.Why is that? The thing is that when the phone is turned off, it sends a signal to the cell, and this allows us to distinguish between devices that were turned off and those that left the cell. When turned on, a new record is created accordingly. Tracking such activities is not difficult.
Calculate by phone. Case 3
"Who even takes their own phone with them to work?" Oddly enough, they do and carry them, and not just phones. They take phones or leave their phones at home, but they take smart watches; by the way, this has allowed the police to solve a lot of crimes. Most "phone" criminals are far from professionals, and their knowledge of how cellular communications function, what data is collected and how it is analyzed is in its infancy. The human factor allows the police to solve many crimes by simply comparing facts.If the criminal really never takes a phone with him (practice shows that usually everyone makes a mistake at least once), then big data analysis can help to identify him. Much here will depend on how much time and how much effort the attacker is ready to put into making an anonymous call, as well as on how many such calls there will be.
What if there are many anonymous devices?
But what if the criminal is cunning and uses not one, but several anonymous phones, getting rid of the evidence after each call? This is the practice often shown in movies. After reading the previous sections, you probably already figured out that all that the criminal gains by using several different devices is a few extra seconds of anonymity, those that precede the actual call. Since calls from all anonymous devices will be included in the case, the police have additional leads: the source of the "anonymous" SIM cards and, possibly, the place where the disposable phones were purchased. Whether the call was made from the same device or several different ones will not affect the course of the investigation.But what if there really was just one call?
But what if there really was only one call? A second call is not needed to report a bomb threat at a school or airport: a telephone terrorist only needs to make one call, after which the “exposed” device can be thrown away or destroyed along with the SIM card.Surprisingly, such criminals are often caught using operational and investigative measures that were developed back in the days of calls from street payphones. If the criminal has a permanent smartphone, then the circle of suspects can be sharply limited by conducting an analysis using the first of the methods described in the article. Thus, even in a city with a population of over a million, the circle of suspects is narrowed to several hundred (rarely - thousands) subscribers. If we are talking about "mining" a school, then many "suspicious" subscribers intersect with many students of the school. It will be enough for the operative to simply talk to those who remain.
Another factor that helps in uncovering telephone terrorism is that such criminals, as a rule, have a poor understanding of the capabilities and features of the work of operatives and try to protect themselves from invented, non-existent dangers, completely ignoring the obvious. Two years ago, employees of one of the neighboring offices (developers of programs for the police) were evacuated by a call from an unknown person who reported an explosive device in the building. Less than a few hours later, the police detained the criminal. The criminal turned out to be a crazy granny who wanted to annoy her neighbors, but mixed up the address. Neither a specially purchased push-button phone by the vengeful old lady, nor an “anonymous” (or rather, registered to a non-existent full name) SIM card helped.
What if you make calls via VoIP using VPN?
If you have the idea that a truly anonymous call can be made via a VoIP service (preferably a free one, so as not to reveal your payment methods), and even via a VPN service that does not store logs, congratulations, you think like a real bandit.Of course, there is always the possibility of “getting screwed up” by forgetting to control the connection to the VPN server or accidentally logging in with your own, not “anonymous” data for calls. To prevent this from happening, criminal groups go to great lengths to order the production of modified (at the software level) phones. The case of the arrest of the CEO of a company producing such devices based on old BlackBerry phones showed the scale of the operations. Although the police managed to shut down this criminal network (and gain control over the encrypted communications infrastructure used by the criminals), the police understand that this is only the first step. “Criminals inevitably migrate to other services, and we know which ones.
How does the analysis take place?
The report published by ITU (Republic of Guinea) describes in some detail both the methods and the tools used by analysts. In general, the process can be depicted as follows.And a little more detail.
All the police need is the raw CDR data itself and software that can download and analyze it (raw data is of little use for manual analysis, but filtered data can be easily displayed on the screen in text form or printed).
The popularity of this method of investigation is evidenced by the fact that CDR records are supported by almost every serious forensic package. Examples: Penlink, HAWK Analytics, GeoTime, CSAS, the Russian "Mobile Forensic" from Oxygen Software, Advanced Cell Tracking and many others. However, police officers successfully use a combination of Google Maps and Microsoft Excel in their work.
Of course, the special services have special equipment that allows them to jam cellular communications, replace the base station, or fake GPS coordinates. But the police do not use most of this equipment - at least not in investigating routine crimes of telephone terrorists and extortionists. It is expensive, fussy, time-consuming, and by and large unnecessary, and sometimes ineffective. Analysis of CDR (Call Detail Record) logs is a much more effective investment of time and effort.
A case that happened a few years ago in the UK is illustrative. The police were monitoring a drug cartel boss. It would not be a problem to arrest him, but there was no evidence, and the case would have fallen apart in court. According to the police, the criminal’s phone (he used an iPhone) could contain vital evidence, but it was impossible to crack the lock code of a fairly new model at that time. As a result, an operation was developed; the criminal was monitored. As soon as he took the phone, unlocked it and started typing, the drug lord was detained, and the phone was literally snatched from his hands.
What's interesting here is not the background, but this minor detail: in order to deliver the criminal's iPhone to the lab in an unlocked state, a special police officer was assigned, whose entire job was to periodically swipe the screen, preventing the device from falling asleep. (There's no need to think of the police as simpletons: everyone knows that there is a setting that controls the time after which the phone's screen turns off and the phone itself is locked. But not everyone knows that you can easily, in a couple of clicks, install a configuration profile on your phone that prohibits disabling the automatic lock.) The phone was successfully delivered to the lab, the data was extracted, and the necessary evidence was obtained.
Somehow this is all… unreliable!
If after reading this article you have the impression that basing a conviction on data obtained from mobile operators is somehow not quite right, I hasten to agree. Moreover, the Supreme Court of Denmark agrees with you, having restricted the use of location data from CDR records by the prosecution. The ban did not come out of nowhere: out of 10,700 convictions based on this data (which is not a small amount for a quiet country), 32 people have already been found not guilty as a result of additional checks. According to the director of the Telecommunications Industry Association, “this infrastructure was created to provide communications services, not to spy on citizens.” “Attempts to interpret this data lead to errors,” and “evidence that appears to be based on precise technical measurements does not necessarily have high value in court.”Most police training courses teach that digital evidence cannot be trusted completely, no matter how it was obtained. Cases are told where a suspect’s location was determined based on metadata from photographs that were synced via the cloud, rather than taken by the device itself.
An illustrative case is when answering an incoming call was interpreted as "distraction while driving", which led to an emergency situation. In fact, the push-button phone, which was still a push-button phone at the time, was peacefully lying in the driver's pocket, but due to an accidentally pressed button, the phone "answered" the call, which was recorded by the operator. The defense was able to acquit the driver by interrogating the second subscriber, who testified that the conversation did not take place (by the way, what "really" happened there is unknown, but the court sided with the accused).
I am sure that such a case is far from unique. CDR data is a great tool in the hands of an operative, but unreliable as an evidence base.
Total
What conclusions can be drawn from this article? Now that almost everyone has a personal smartphone or at least a push-button telephone, any person leaves a "digital trace". This trace contains significantly more information, and it is much easier to get to it than many people realize. To obtain all the information of interest, the police need only one clue, which can be the hardware identifier of the criminal's personal smartphone, even if he has never used his personal device for criminal purposes.Getting such a lead is the result of a regular, routine analysis of mobile operators' logs. No special equipment is needed, no conspiracy theories are needed, everything happens much more simply and interestingly. Instead of chases and shooting, there is desk work with an analytical program, a simple database, or even printouts.
Source