Tomcat
Professional
- Messages
- 2,689
- Reaction score
- 978
- Points
- 113
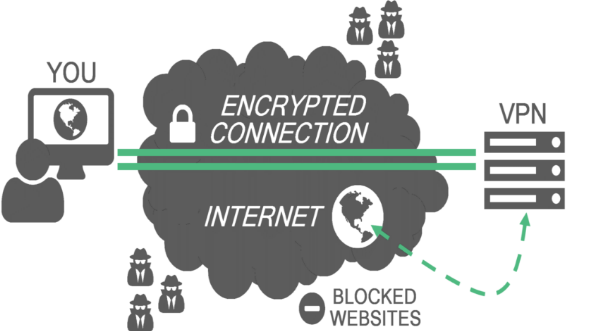
I think they already almost know that for free access to any sites and maintaining your privacy, you need to use a VPN connection through a server that is located where there is no censorship. But this is not always the case.
Over time, not only users have figured it out, but the sites themselves have developed ways to block access through VPN. In other words, even a VPN can be useless in accessing a particular site. Therefore, we have prepared for you this simple but detailed report on how to bypass VPN blocking and work without restrictions on the network.
Internet censorship can become a kind of continuation of the state policy of restricting access to inappropriate content (in fact, this is censorship). It can be based on political, social or legal reasons.
First of all, I would like to emphasize that using VPN services is quite rarely illegal, but the content that you try to access using a VPN may be illegal. However, all this does not prevent some sites from blocking VPN services.
IP blocking is the most common way to block VPN access and is as follows: it compiles a list of all IP addresses that belong to the VPN service and adds them entirely to the blacklist. Currently, there are a large number of VPN services and therefore many sites only block access through the most popular VPN services. Lesser known VPN services remain in the shadows and allow their users to access blocked content.
On whoer.net you can find out if your IP or proxy is blacklisted or not.
Port blocking is another effective way to block, and it consists in configuring the firewall in a special way and blocking the ability to connect to certain ports that are most often used by VPN services, for example: ports 1194 (UDP), 1723 (TCP), 500 (UDP), 4500 (UDP), 1701 (UDP), and so on.
The sites that most often block VPN services:
1) Streaming services - more and more services that provide access to streaming content block access to users using VPN services to bypass geographic restrictions to viewers. This greatly increases the flow of money to copyright holders by dividing the global market into segments. In such cases, the user sees something like:
2) Services that provide content for rent - VPN services are often blocked on airplanes and hotels, such as GoGo does. This is logical, since the service is profitable for the user to rent content from them, and not receive it for free.
Here are the ways to solve this problem. For convenience, I have divided this size into two parts - for the experienced user and for the "noob".
Simple way:
1) Access to the network through a mobile operator. This method is the easiest one to bypass VPN blocking. To do this, you just need to turn on the mobile Internet on your phone or use the device as an access point, and you get access to content that is blocked at a hotel, school or at work.
2) Server variety - instead of one single VPN service, which is "locked" everywhere, you can use lesser known ones. Or, you can change the server and get a different IP address without changing your VPN provider. Check with your VPN service if it changes IP addresses frequently
3) Do it yourself - instead of relying on VPN services with their servers, you can always create your own VPN server and connect to it from anywhere in the world. Your VPN server is your unique IP address, which is 100% not yet blacklisted.
Step 1: open the start menu. Enter VPN in the search bar and select 'Create a new secure (VPN) connection'.
Step 2: enter the IP address or domain name of the server you are going to connect to.
Step 3: If you just want to create a connection, but not connect, select 'Do not connect now'. Otherwise, just click on 'Next'.
Step 4: In the window that appears next, enter your username and password or leave the corresponding forms blank. When establishing a connection, you will have to enter these details again. Then click on 'Connect'.
Step 5: to connect, click on the Windows network icon located in the lower right corner of the screen and select 'Connect' under the line 'VPN connection'.
Step 6: In the 'Establish VPN Connection' field, enter the required domain and credentials, then click 'Connect'.
4) Tor is a system that is built on the principle of "onion routing". The connection is first encrypted and then established through randomly selected network nodes, which are supported by volunteers from all over the world. Tor hides the identity and actions of the user from monitoring and analyzing traffic by separating identification and routing. Bridge connections to Tor can be used to bypass IP blocking of Tor nodes, and obfsproxy can be used to hide Tor traffic from DPI.
5) Lahana is a script that builds automatically and creates a simple VPN connection like OpenSwan using PSK and redirects all outgoing traffic like TCP and DNS through Tor. Lahana does not attempt to protect user privacy more securely than a PSK IPSEC / L2TP VPN connection can do. You can spend no more than $ 20 per month to support the Lahana node.
6) Shadowsocks is an open source proxy application. It is popular in mainland China, where it is used to bypass Internet censorship. It is essentially a SOCKS5 proxy server that is available for most major modern platforms.
7) Psiphon is an open source internet censorship bypass tool. It uses a combination of secure connection and obfuscation (hiding) technologies - VPN, SSH and HTTP Proxy. When using a VPN service, if you are faced with blocking access to a resource, you can reconnect via SSH or obfuscated SSH (SSH +). When logging into the network from a region where access to the Psiphon site is blocked, you can ask to send you all the necessary files by sending an email to info@psiphon.ca.
Ways for an advanced user:
1) TCP port 443 is a standard Internet encryption protocol that you use every time you enter a website with your sensitive personal information, for example, your bank website. Since most reliable and paid VPN services already use the SSL encryption library, reconnecting on port 443 will allow you to avoid almost all (well, perhaps the most picky ones) DPI firewalls. You can configure this by contacting the technical support of your provider.
Port number changes:
* Find the desired settings file. It is a .ovpn file
he is located:
- Windows XP / Vista: C: \ Programs \ OpenVPN \ config
- Windows XP / Vista 64-Bit: C: \ Program Files (x86) \ OpenVPN \ config
- Macintosh OS X: Library / openvpn (in the corresponding user's Home folder)
* Open the settings file in WordPad or TextEdit. On computers running Windows Vista, you will need to run the text editor as administrator.
- Delete all lines with the text "proto udp"
- Insert the "#" sign at the beginning of the line "remote vpn1.hideway.eu"
- Add a line or remove the "#" sign: "remote vpn2.hideway.eu 443 tcp"
- Save the file
2) Stealth VPN / Obfuscation - when exiting through port 443, many VPN protocols use a special data packet header that can be decrypted by the firewall and recognized as VPN traffic. Of course VPN services know that some networks block VPN traffic. Therefore, stealth VPN technology was invented, which masks VPN traffic, making it completely different from regular VPN traffic or representing it as regular web traffic encrypted using the TLS protocol. VPNs that provide this service include IPVanish, Proxy.sh, Torguard, VyprVPN, APN.ac and a few others. Using a VPN service that supports traffic obfuscation makes it possible to rewrite or hide the headers of VPN traffic packets, thereby hiding it from filewalls.
3) SSL tunnels - we are talking about cases when a client application requests a web object through the HTTPS protocol on port 8080 through a proxy server. For example, when making a purchase in online stores.
The Internet connection to the respective online store is established via a tunnel through a proxy server. The user sends and receives data immediately from the desired web server after the proxy server establishes a primary connection using an SSL tunnel, which was created following certain procedures. SSL tunnels are created using the Stunnel program, which must be configured on both the VPN server and the user's computer. If you want to use SSL tunnels, you will need to discuss this fact with the staff of your VPN service. OpenVPN data is wrapped in an additional layer of TLS / SSL encryption. The DPI firewall is unable to break through this encryption layer. It turns out that he will not notice the encryption of OpenVPN, which is under it either.
4) SSH tunnels. An SSH tunnel consists of an encrypted tunnel that is created using the SSH (Secure Shell) protocol. This method is similar to SSL tunnels, the difference is that VPN traffic is wrapped in SSH encryption. The protocol is used in serious corporate systems to provide access to accounts through a special shell on UNIX systems. Most likely because of this, the protocol is not even close to being popular with SSL. To activate this option, you will have to contact your VPN service technical support, just like with SSL tunnels.
SSL tunnels and SSH tunnels are much more reliable than simple obfuscation, as they wrap the traffic in an additional layer of encryption. On the other hand, obfsproxy is much easier to install and configure, and this method does not clog the channel much - after all, there is no additional encryption layer there.
