Carder
Professional
- Messages
- 2,620
- Reaction score
- 2,043
- Points
- 113
Credits to pentester
BYPASSING OTP?
OTP IS MOSTLY A 4/6 DIGIT NUMERICAL/ALPHANUMERIC CODE USED AS ANOTHER WAY OF AUTHENTICATING A USER ALONG WITH THE CREDENTIALS.
STONE AGE
People used to just enter their email and pass to login.
It still is there for majority of sites but some have 2FA[OTP] as optional and some have it mandatory.
WHY OTP?
BECAUSE PEOPLE CAN HACK/CRACK YOUR EMAIL/PASS EASY
WITH OTP EVEN IF THEY CAN, THEY WONT BE ABLE TO LOGIN
WHATS THE OTHER WAY ROUND THIS?
There are tons of other ways to bypass OTP but the most popular and bit of HQ is SS7 Attack.
Comment down below the thread if you want me to write those up too.
So Where were we:
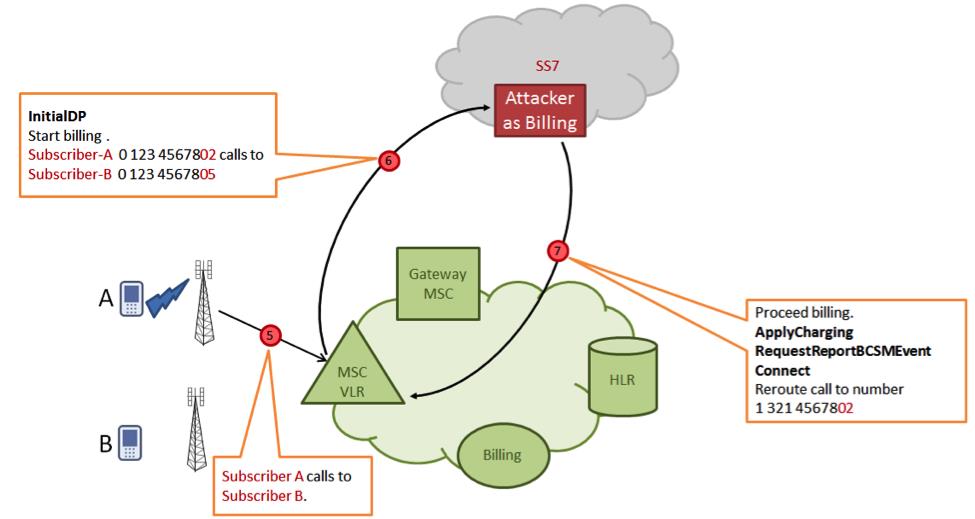
SS7 Tunneling/Attack = Same as MITM but operates on telephonic communication rather than data/wifi communication.Those who got no idea what MITM is can go through my previous thread about it.
Now Why is SS7 HQ
Because the global telephonic communication runs on it.
Old Protocal but hasnt been changed much.
What Tools needed for this Attack?
A Linux OS and SS7 SDK [They re on the Internet]
The Inside Workaround?
Take an Example: Our Freind Roobbin is having some cash piled up in his bank account. Forget it. FBI gonna bust my ass for this example.
Our freind roobbin got an app in his phone which lets him login to his account after entering the credentials and an OTP generated on Real-Time.
We as usual gets the credentials by hacking/cracking
But when we treid to log-in to the app using just the email/pass it generated the OTP [Take an example of Hotstar or BLockChain or anything that requires OTP].
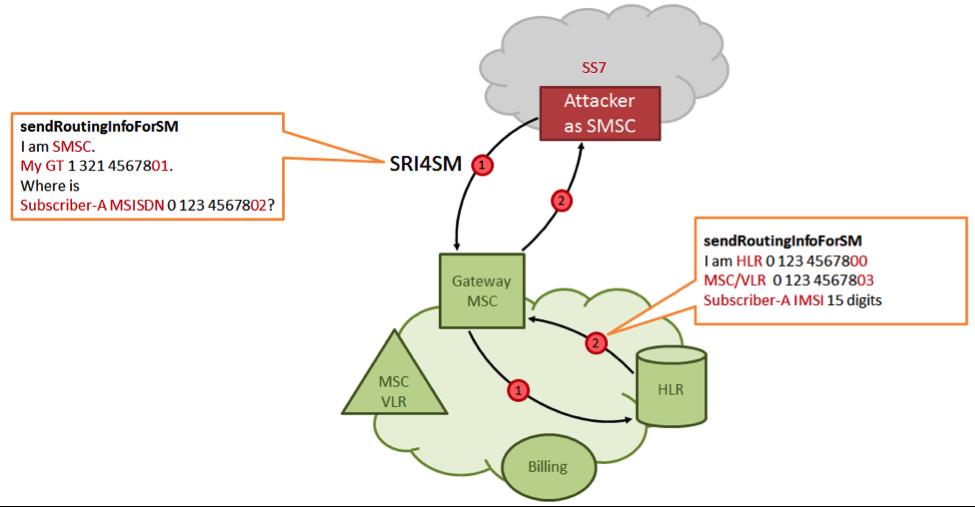
When there is some kinda communication via our phone to any other service over the Network, Our Unique Phone address is stored in HLR [Home Location Register] and it acts as a medium to transmit data. See what i learned in "Wireless Communication" is coming in handy right now. The Enggineering guys would know if they had the subject taken.
Ok to be straight. Phone sends data to HLR and checks the unique address of our mobile device,
Then from there the HLR sends the request to VLR[Virtual Location Register - It temporarilhy stores our mobile info till connection time out.
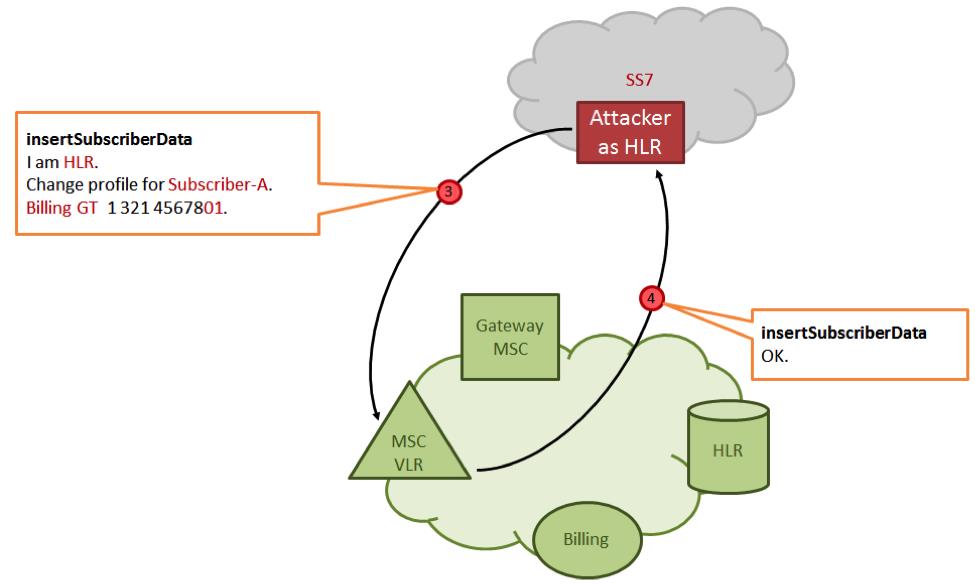
SS7 Fakes VLR Address and put the hackers machine address in it. So, basically we are tricking the system into beleiving our address to be the users address we need to get the OTP from.
Now you know what. HLR will transmit the details to the fake VLR and hackers gonna get all the details flowing in and out the the victims mobile phone.
Enjoy!
BYPASSING OTP?
OTP IS MOSTLY A 4/6 DIGIT NUMERICAL/ALPHANUMERIC CODE USED AS ANOTHER WAY OF AUTHENTICATING A USER ALONG WITH THE CREDENTIALS.
STONE AGE
People used to just enter their email and pass to login.
It still is there for majority of sites but some have 2FA[OTP] as optional and some have it mandatory.
WHY OTP?
BECAUSE PEOPLE CAN HACK/CRACK YOUR EMAIL/PASS EASY
WITH OTP EVEN IF THEY CAN, THEY WONT BE ABLE TO LOGIN
WHATS THE OTHER WAY ROUND THIS?
There are tons of other ways to bypass OTP but the most popular and bit of HQ is SS7 Attack.
Comment down below the thread if you want me to write those up too.
So Where were we:
SS7 Tunneling/Attack = Same as MITM but operates on telephonic communication rather than data/wifi communication.Those who got no idea what MITM is can go through my previous thread about it.
Now Why is SS7 HQ
Because the global telephonic communication runs on it.
Old Protocal but hasnt been changed much.
What Tools needed for this Attack?
A Linux OS and SS7 SDK [They re on the Internet]
The Inside Workaround?
Take an Example: Our Freind Roobbin is having some cash piled up in his bank account. Forget it. FBI gonna bust my ass for this example.
Our freind roobbin got an app in his phone which lets him login to his account after entering the credentials and an OTP generated on Real-Time.
We as usual gets the credentials by hacking/cracking
But when we treid to log-in to the app using just the email/pass it generated the OTP [Take an example of Hotstar or BLockChain or anything that requires OTP].
When there is some kinda communication via our phone to any other service over the Network, Our Unique Phone address is stored in HLR [Home Location Register] and it acts as a medium to transmit data. See what i learned in "Wireless Communication" is coming in handy right now. The Enggineering guys would know if they had the subject taken.
Ok to be straight. Phone sends data to HLR and checks the unique address of our mobile device,
Then from there the HLR sends the request to VLR[Virtual Location Register - It temporarilhy stores our mobile info till connection time out.
SS7 Fakes VLR Address and put the hackers machine address in it. So, basically we are tricking the system into beleiving our address to be the users address we need to get the OTP from.
Now you know what. HLR will transmit the details to the fake VLR and hackers gonna get all the details flowing in and out the the victims mobile phone.
Enjoy!