Carding 4 Carders
Professional
- Messages
- 2,724
- Reaction score
- 1,579
- Points
- 113
How can I scan the data center using Nmap?
Consider today a well-known and world-old tool for network research.
For a test scan, consider the Metasploitable tool. An image with already prepared vulnerabilities.
Download the image from the link https://sourceforge.net/projects/metasploitable/ in zip format and extracted from the archive.
Open VMware Workstation Pro – > Open a Virtual Mashine > and select the VM configuration file Metasploitable.vmdk then start the VM.
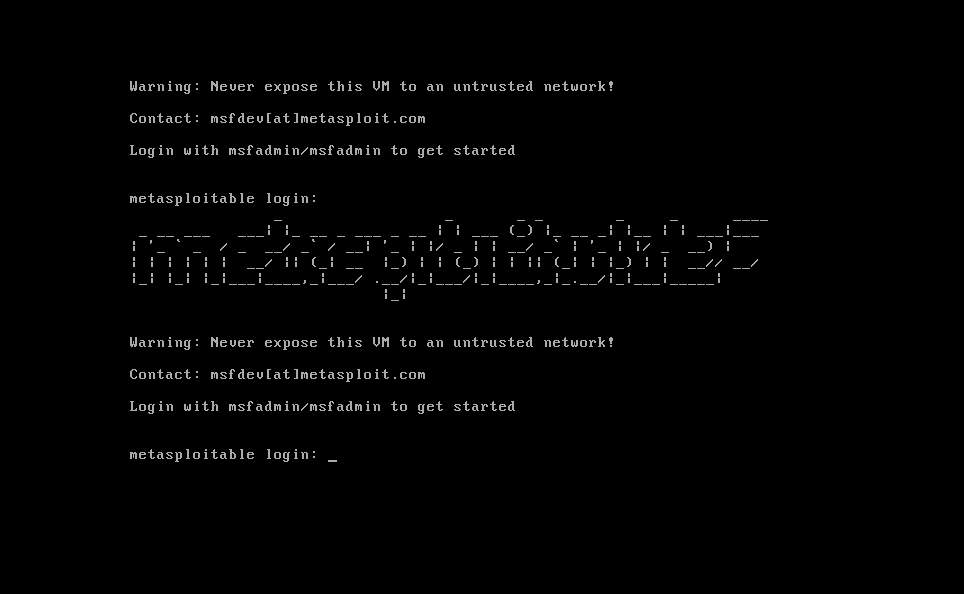
After downloading the components and greeting, enter login: msfadmin, password: msfadmin.
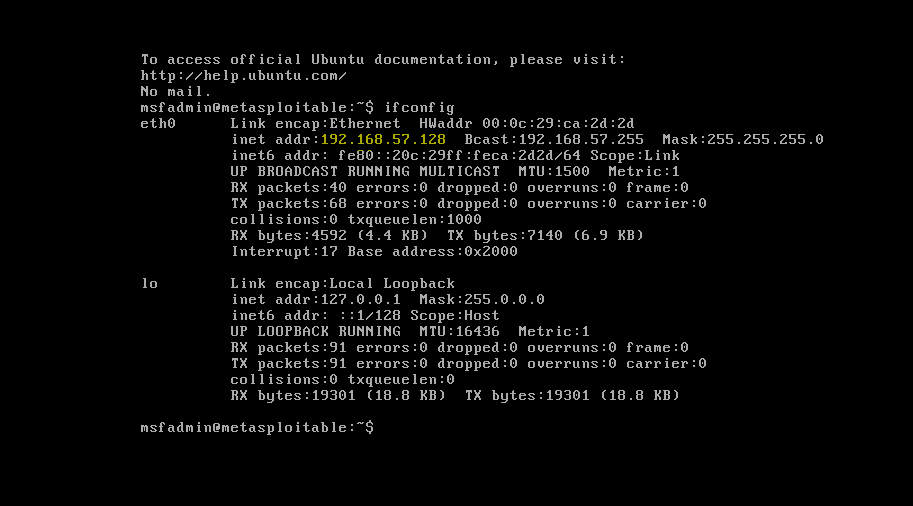
Then you need to make sure that the ipaddress was obtained with the ifconfig command. The resulting ip in this case is 192.168.57.128. If the ip was not received, you can register a static ip in etc/network/interfaces
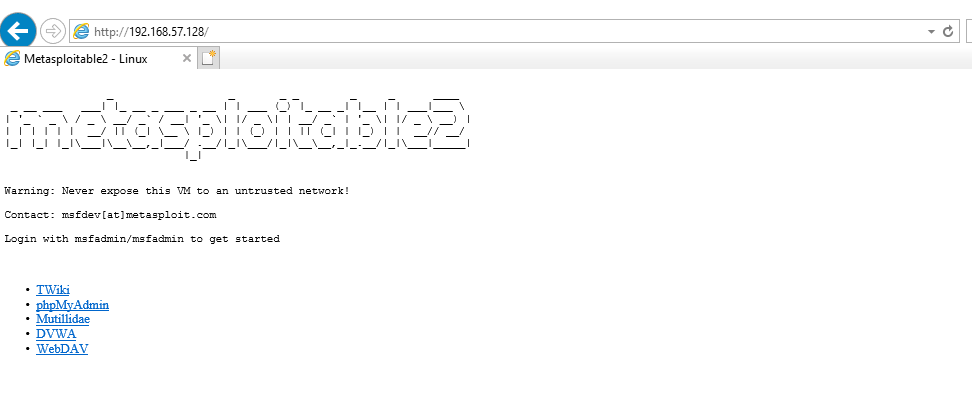
Let's open a web form by the received ip via IE
После необходимо скачать клиент Nmap and put it on the host (other virtual) machine. In our case, we put on Windows 10. https://nmap.org/download.html. During installation, select the necessary components and install. It is more convenient of course to use the distribution kit Kali Linux, where many of the necessary tools for scanning purposes are already included.
First, we will perform a scan to detect the target by sending an echo request and receiving an echo response using the ping utility. Let's scan the entire subnet with a 24 mask using the command:
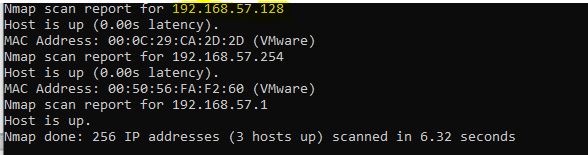
As a result, as we can see, our host is pinged, the other 2 values with the ipaddress are a virtual switch of Vmware. There are situations when the firewall blocks icmp, the windows firewall does this by default, so we will consider scanning with sending TCP packets to a specific host to do this, enter the command:
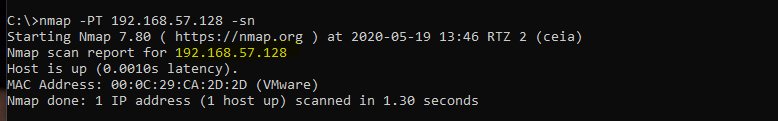
–sn-flag indicating that you don't need to scan the ports of the target under investigation
Next, we'll look at port scanning using TCP. It is worth noting that ports come in 3 States: open, closed, and filtered. The result about the status of ports is achieved by sending a packet with the SYN flag specified in the header. if the port is open, then in response from the target, in accordance with the 3-step construction of a TCP connection, a packet is returned in the header with the SYN and ACK flags set. If the port is closed a TCP packet with the RST flag set is sent in response, this flag indicates that the connection attempt was rejected by the target. If the port is filtered, we don't get a response. TCP scanning can be hidden (when only 2 of the 3 stages of a TCP connection are implemented, and it is not logged) and a full TCP connection.
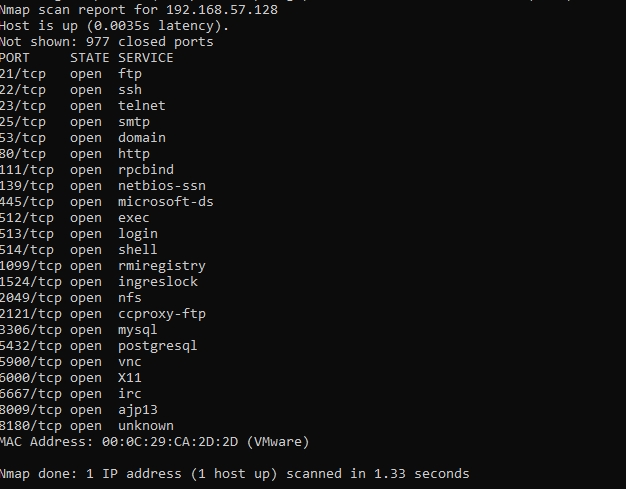
First, let's run a hidden TCP scan using the command:
Based on the results, we will see open TCP ports
Now we will perform a TCP scan with a complete connection by entering the command
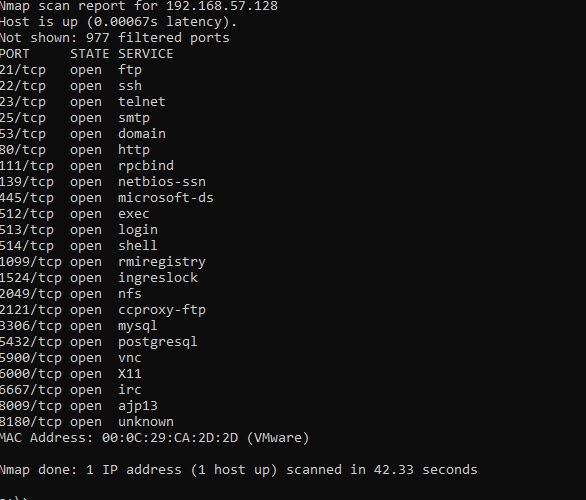
The results for open ports and their services are similar. We see a lot of interesting open protocols and services running on them
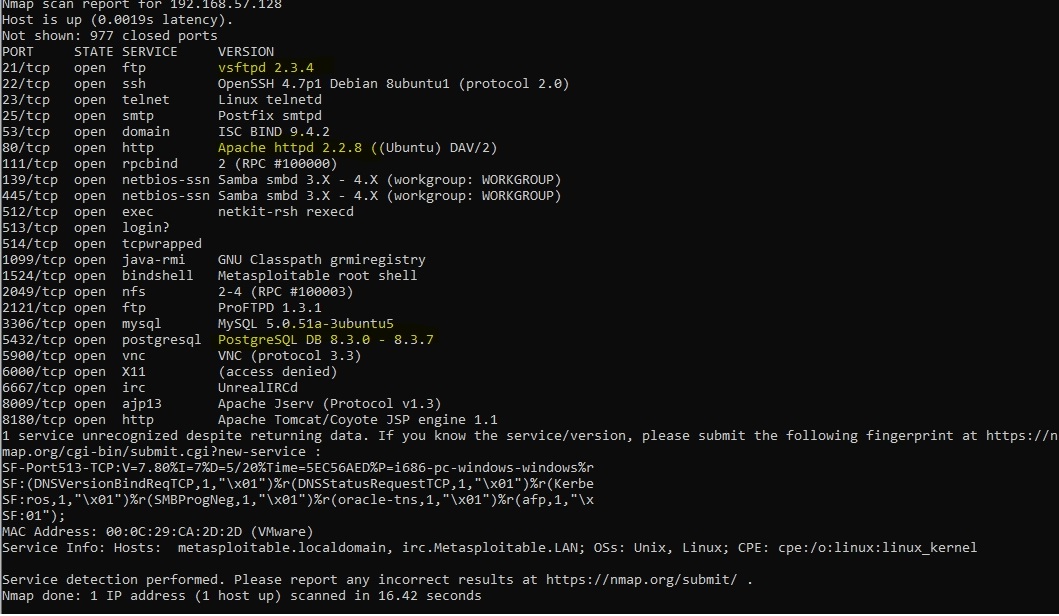
To view the version of the software running on various services, enter
UDP scanning is achieved by sending a request (response) to ports, if a response is received in response, then this means that the port is open. If an ICMP response type 3 code 3 is received in response to the request (there are no flags in udp), then the port is closed. If no response is received, the port is filtered.
Another interesting type of scanning is using a script engine. Although nmap is classified as a network scanner, it has in its Arsenal functionality for finding vulnerabilities. To use it, enter the command:

Based on the results, we can see, for example, anonymous login via FTP is allowed, ssh keys, smtp commands available on the machine under study, etc.
To scan “for all”, enter the command:
Executing the command will take a significant amount of time and put a significant burden on the target under study.
After collecting information about the system, it is analyzed and evaluated.
Consider today a well-known and world-old tool for network research.
For a test scan, consider the Metasploitable tool. An image with already prepared vulnerabilities.
Download the image from the link https://sourceforge.net/projects/metasploitable/ in zip format and extracted from the archive.
Open VMware Workstation Pro – > Open a Virtual Mashine > and select the VM configuration file Metasploitable.vmdk then start the VM.

After downloading the components and greeting, enter login: msfadmin, password: msfadmin.
Then you need to make sure that the ipaddress was obtained with the ifconfig command. The resulting ip in this case is 192.168.57.128. If the ip was not received, you can register a static ip in etc/network/interfaces

Let's open a web form by the received ip via IE

После необходимо скачать клиент Nmap and put it on the host (other virtual) machine. In our case, we put on Windows 10. https://nmap.org/download.html. During installation, select the necessary components and install. It is more convenient of course to use the distribution kit Kali Linux, where many of the necessary tools for scanning purposes are already included.
First, we will perform a scan to detect the target by sending an echo request and receiving an echo response using the ping utility. Let's scan the entire subnet with a 24 mask using the command:
Code:
nmap -sP 192.168.57.0/24
As a result, as we can see, our host is pinged, the other 2 values with the ipaddress are a virtual switch of Vmware. There are situations when the firewall blocks icmp, the windows firewall does this by default, so we will consider scanning with sending TCP packets to a specific host to do this, enter the command:
Code:
nmap -PT 192.168.57.128 -sn–sn-flag indicating that you don't need to scan the ports of the target under investigation

Next, we'll look at port scanning using TCP. It is worth noting that ports come in 3 States: open, closed, and filtered. The result about the status of ports is achieved by sending a packet with the SYN flag specified in the header. if the port is open, then in response from the target, in accordance with the 3-step construction of a TCP connection, a packet is returned in the header with the SYN and ACK flags set. If the port is closed a TCP packet with the RST flag set is sent in response, this flag indicates that the connection attempt was rejected by the target. If the port is filtered, we don't get a response. TCP scanning can be hidden (when only 2 of the 3 stages of a TCP connection are implemented, and it is not logged) and a full TCP connection.
First, let's run a hidden TCP scan using the command:
Code:
nmap -sS 192.168.57.128Based on the results, we will see open TCP ports

Now we will perform a TCP scan with a complete connection by entering the command
Code:
nmap -sT 192.168.57.128
The results for open ports and their services are similar. We see a lot of interesting open protocols and services running on them
To view the version of the software running on various services, enter
Code:
nmap 192.168.57.128 -sV
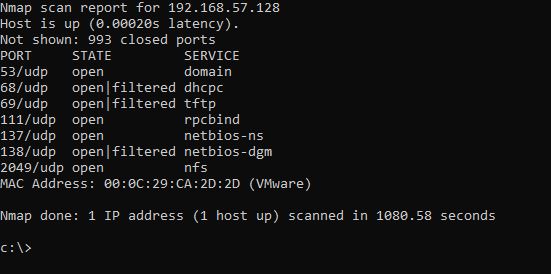
UDP scanning is achieved by sending a request (response) to ports, if a response is received in response, then this means that the port is open. If an ICMP response type 3 code 3 is received in response to the request (there are no flags in udp), then the port is closed. If no response is received, the port is filtered.
Code:
nmap -sU 192.168.57.128
Another interesting type of scanning is using a script engine. Although nmap is classified as a network scanner, it has in its Arsenal functionality for finding vulnerabilities. To use it, enter the command:
Code:
nmap -sC 192.168.57.128
Based on the results, we can see, for example, anonymous login via FTP is allowed, ssh keys, smtp commands available on the machine under study, etc.
To scan “for all”, enter the command:
Code:
nmap -A 192.168.57.128Executing the command will take a significant amount of time and put a significant burden on the target under study.
After collecting information about the system, it is analyzed and evaluated.

