Brother
Professional
- Messages
- 2,590
- Reaction score
- 528
- Points
- 113

In 2021, cybercriminals managed to steal 10% of all funds invested in ICOs through Ethereum. The total damage to almost $ 225 million, 30 thousand investors lost an average of $ 7,500. Let's figure out exactly how money is stolen during the ICO. The entire hacker arsenal can be involved here, or the most primitive methods can be used.
“Even before the start of the ICO, we faced a dozen phishing sites, DDoS attacks and threats from ISIS and the Italian mafia:“ Transfer 10 bitcoins to this wallet, otherwise we will destroy you! ”, Recalls preparations for September ICO Ilya Remizov, Chief Technology Officer, Blackmoon. His team turned to Group-IB for protection, and they cleaned phishing sites, neutralized these ransomware blackmailers.
In less than twenty hours, Blackmoon has raised over $ 30 million. But such a perfect ICO doesn't always happen. Not only speculators and crypto enthusiasts have been trying to make money on cryptocurrencies for a long time, but also hackers who use their skills for theft and cyberattacks.
Cryptocurrency has attracted cybercriminals since 2011: it was then that hackers began to actively hack online wallets, cryptocurrency exchanges and exchangers, and steal private keys from individuals' wallets. Some banking Trojans - TrickBot, Vawtrak, Qadars, Triba, Marcher - have been targeted at cryptocurrency wallet users.
Having felt the smell of money, not only traditional cybercriminals, but also pro-government hackers began to attack cryptocurrency exchanges. For example, hackers from the North Korean group Lazarus are suspected of recent attacks on South Korean crypto services.
In the early days of Bitcoin, hackers required quality training and an extensive repertoire of techniques. The widespread use of ICOs has significantly changed the situation. Often, even an attacker who does not understand anything about blockchain and information security has the ability to hit the jackpot.
The path to ICO
When a team decides to conduct an ICO, they first of all develop a White Paper (WP) - a document that describes the technology and business model of the project. Based on the developed WP, a landing page is created, and the organizers attract the community, whose interest in the project is constantly fueled by news and the opportunity to communicate with the team. At some point, the ICO date is announced, followed by a series of activities until the "X" hour: advertising campaigns in search engines and on other resources, mailing lists, and so on. At the appointed time, the ICO opens, investors get the opportunity to purchase project tokens, and the project accepts cryptocurrency to their wallets.At what step in the ICO path do hackers appear? For everyone! Hackers, like all other investors, also want to make money on ICOs. As soon as the first version of the White Paper is published, the attackers have a starting point to start the operation.
Stealing white paper
One of the features of blockchain industry projects is complete openness and transparency. Most of the developments and source codes are published in the public domain. Obviously, the team publishes WP first.Quite recently, an interesting case was registered when attackers were able to make money by copying someone else's project. The scheme looks very simple: a legitimate, well-developed White Paper in Russian is taken, a full copy of it is made via Google Translate, a landing page is created with a description of the project, a new team (fake, of course ) and a new brand. The project is well promoted on the Web: contextual advertising appears, huge threads on Bitcointalk.org, and so on.
For example, our colleagues at Crypto Detectives discovered that the owners of the Wi-Fi Global project had copied and translated the WPs of the worldwifi.io team. If you look closely, Wi-Fi Global is just a slightly reworked version of World Wi-Fi. At the same time, the Wi-Fi Global Telegram community numbers more than two thousand people and, according to the project participants, they managed to raise 500 thousand dollars for pre-ICO.


Account compromise
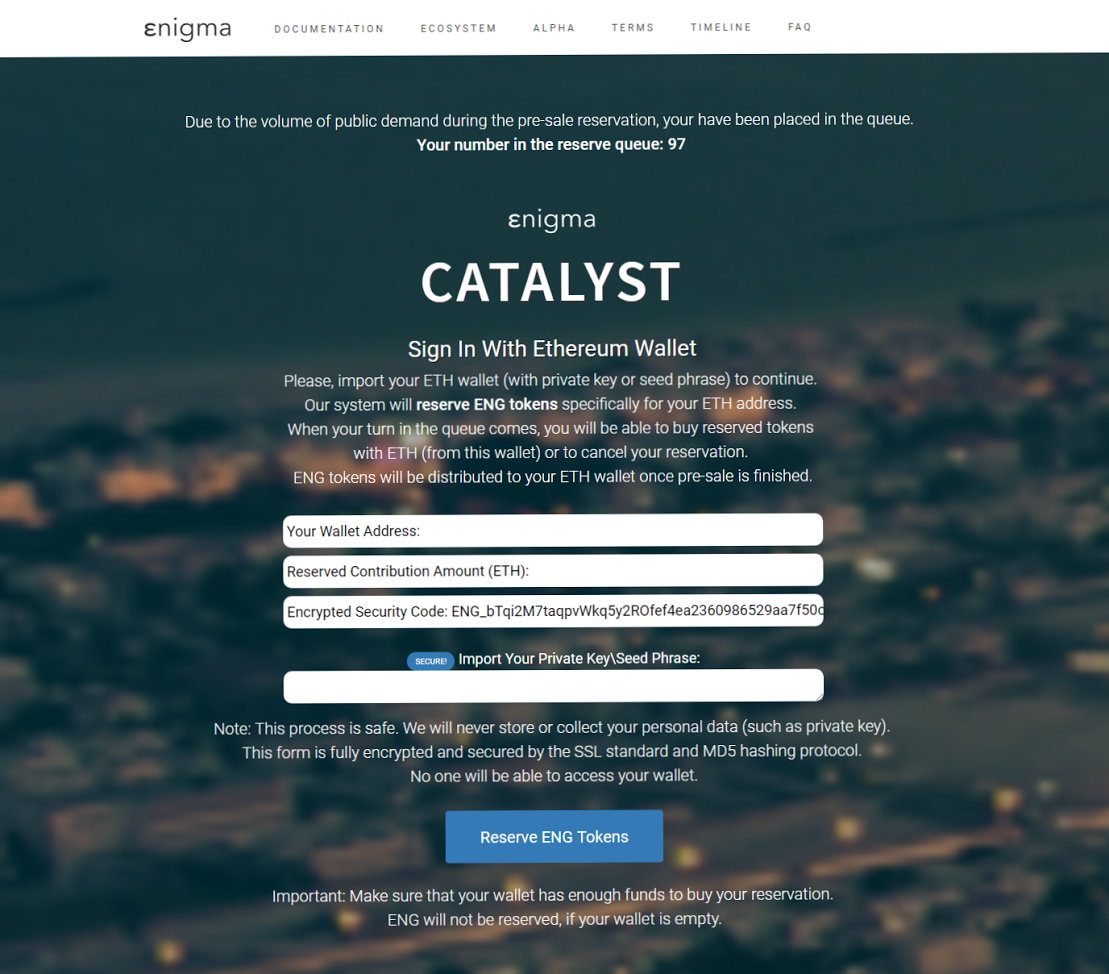
Since the project website usually has detailed information about all team members, intelligence for attackers is greatly simplified. It's no secret that a huge number of dumps of leaked passwords are circulating on the Internet. If a compromised password is used somewhere else, then this can lead to extremely undesirable consequences - not only for the account owner, but also for the project and investors.It is such an unpleasant story that happened to the authors of the Enigma project. The hackers managed to earn half a million dollars even before the ICO date was announced. The attackers were able to compromise the Enigma website and several social media accounts.
The founders of the project are from the Massachusetts Institute of Technology. The CEO, apparently, was not very fond of using different and complex passwords for his accounts. Thanks to this, hackers gained access to his email address (which did not have two-factor authentication). Naturally, it was not difficult to gain access to other services and accounts tied to the address. Next, the credentials of other team members were compromised. The attackers gained access to the enigma.co page (the site on which the token sale was made was not compromised) and the Slack messenger.
After gaining access to enigma.co, the hackers posted an announcement of the token sale there, wrote about it in Slack in a chat for the community, and made a mailing list on the stolen list. All this is to distribute your address to which it was proposed to transfer tokens. In total, they managed to collect 1492 ETH - about one and a half million dollars.
Defaces
All the worst, as a rule, happens on the day of the ICO. A flurry of DDoS attacks simultaneously with an influx of users, an avalanche of messages to the project's channel in Telegram and Slack, spam on the mailing list.The most offensive thing that can happen is the site defacement during the ICO. The goal of the hackers is very simple: to put your wallet on the official portal of the project and collect funds for it.
The victim of such an attack was the CoinDash project. During the ICO, the CoinDash website was hacked, hackers put an illegitimate wallet on the main page of the project. It is clear that all investors rushed to throw cryptocurrency not on CoinDash wallets, but on hacker ones. More than two thousand investors became victims of the attack, having lost about 37,000 ETH in total.
The project team turned out to be decent and compensated for the damage to investors who fell into the hands of hackers.
Phishing
Phishing almost always occurs when a more or less well-known project enters the ICO. Sending fraudulent emails is usually accompanied by a powerful DDoS attack on the project's website. The meaning of all this is very simple: hackers copy the content of the site, create a similar domain and post it on the Internet. There is nothing unusual here, everything is as usual. In the case of ICO, two types of fish are created: the first type is designed to steal the user's private key, the second simply asks to transfer the cryptocurrency to the address of the wallet or smart contract.How can someone leave a private key on a fraudulent site? Doesn't that sound suspicious? Alas, when the desire to get rich quickly is involved, something else also happens. According to Etherscan, people sometimes make repeated transfers without getting anything in return.
According to statistics from the Chainalysis company, about 56% of all funds stolen from ICOs were stolen using phishing attacks. The estimated damage from phishing is $ 115 million. According to Group-IB, a large phishing group makes between $ 3,000 and $ 1 million a month. Phishing is now the most popular way to steal funds from investors. In the midst of the "cryptocurrency rush", everyone strives to buy tokens as soon as possible (they are often sold at a large discount) and do not pay attention to such trifles as crooked domains.
A typical scheme is that cybercriminals buy contextual advertising in search engines, organize an avalanche of messages in instant messengers, and by any means try to drive traffic to a phishing site. In general, if you wish, you can even enter an indicator of the investment attractiveness of a project by counting the number of phishing sites based on it.
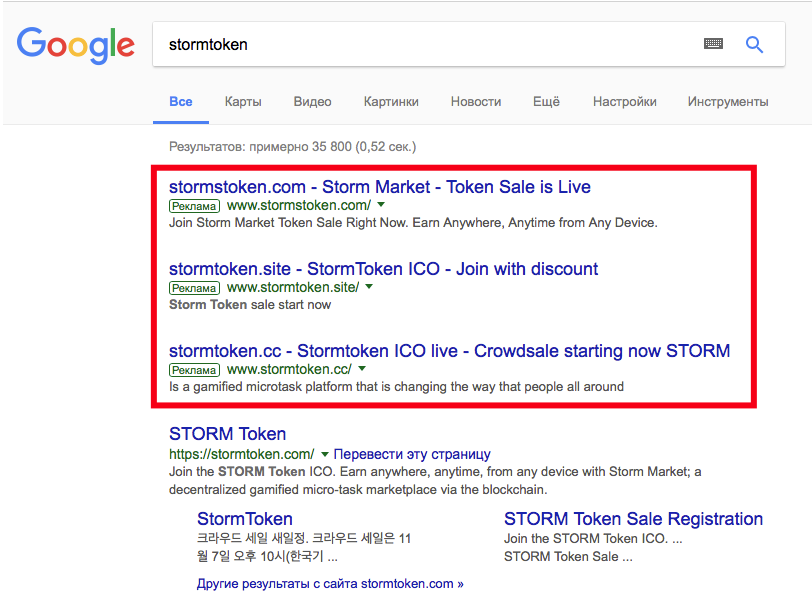
In preparation for one presentation, I took a screenshot of the ICO STORM Token search on Google. It is notable for the fact that the first three links are phishing, placed through contextual advertising. In addition, phishing MyEtherWallet is common. Be carefull!
There is a very good project etherscamdb.info, where phishing is aggregated by ICO. There are 2533 entries in its database. Essential for such a young industry. For MyEtherWallet alone, 2,206 phishing domains have been registered.
When you lose after collecting
The worst option for any ICO team is to lose funds after a successful fundraising. This happens due to inaccurate handling of cryptocurrency, vulnerabilities in smart contracts, and zyrodey in popular wallets. And even if we discard the vulnerabilities in our own software, the risk of losing funds in other cases is quite difficult to neutralize.A good example is the DAO project, from which the attackers were able to steal at least $ 53 million. Another example is the aeternity project, from which $ 30 million was stolen through a zirodei vulnerability in the Parity wallet.
Vulnerabilities in smart contracts are being actively explored by the community. For example, scientists from the University of Cagliari ( PDF ) describe different operating techniques. There are also attempts to improve security - for example, the Oyente utility automatically checks smart contracts for vulnerabilities.
Most likely, “criminal” smart contracts will still find their application in the high-tech world. For example, in the research paper Giga Ring: Exploring the Future of Criminal Smart Contracts (PDF), researcher Ari Ewels and his colleagues look at options for harming smart contracts.
How to protect your team: a typical scenario
The most vulnerable part of any project is its team. Poor protection of personal accounts, the lack of an elementary culture of computer hygiene often leads to the fact that the accounts of messengers and social networks are compromised and attackers are able to send links to phishing sites left and right, discredit the team, change data on sites, and so on. The only thing worse than that is the compromise of private keys from cryptocurrency wallets.So, here's what you need to do so that the ICO is not overshadowed by criminals.
- DDoS protection. Almost every promoted project is faced with this type of attack. It is better to take care of high-quality DDoS protection in advance. The inaccessibility of the site often discourages potential investors from investing.
- Protection of the project team. All team members must protect their personal social media accounts, provide two-factor authentication, and implement password policies.
- Information security of applications. Naturally, you need to check everything for vulnerabilities and make high-quality access settings to critical services on the servers.
- Checking smart contracts for known vulnerabilities. At the very least, you need to scan them with automatic means.
- Train your community to recognize phishing. This is a relatively simple and cheap measure that will significantly protect potential investors from losing funds.
