Lord777
Professional
- Messages
- 2,576
- Reaction score
- 1,550
- Points
- 113
Hello, today we continue the topic of cryptography and in this post I will tell you about the main principle by which all information on the Internet is encrypted.
Anyone who read the previous post already knows that there are two main encryption methods. Symmetrical and asymmetrical. With symmetrical, everything is simple.
Both the sender and the recipient of the message have one encryption key. This is his main vulnerability, because if someone from the outside finds out the key, then it will not be difficult for him to decipher the intercepted message. So people went further and came up with asymmetric encryption. What is its essence?
I will use the most popular example with chests example. Let's remember symmetric encryption. There is one chest which contains messages. Both participants of the exchange have the same key. In asymmetric, everything is much more cunning. The recipient sends an open chest to the sender. The sender puts his message in it, closes it and sends it back. At the same time, only the recipient has the key itself, which means that this method of exchanging information is an order of magnitude more reliable.
RSA
And now, how it all works in practice. In the 1970s, three American scientists Ron Rivest, Adi Shamir and Leonard Adleman made a real breakthrough in the field of cryptography and created the first asymmetric encryption algorithm, which was named after the first letters of their names. It was based on a combination of several simple mathematical theories such as Fermat's theorem and Euler's function. And now, in a simple way. Suppose we have two numbers 17 and 19. They can be easily multiplied on a calculator and we get 323. But how to do the opposite operation - factor 323 into factors. It's already an order of magnitude more difficult, isn't it? Now imagine that this number is not 323, but for example 872847573857382943849229. A human is definitely not able to do this, and even a computer will take some time to find the factors. All asymmetric encryption is based on this simple principle. The multipliers are a private key that only the recipient has. But this large number is the public key that is sent from the recipient to the sender and back.
Application?
RSA-based encryption is used almost everywhere. This includes encryption of sites, messages in instant messengers, and much more. The trick is that modern services use a public key, which is a number of thousands of characters. Even a couple of supercomputers can't handle that. Also, these numbers are constantly changing. For example, why even the creators of Telegram do not know their own encryption keys. But because they are automatically updated on an ongoing basis. That's the whole point.
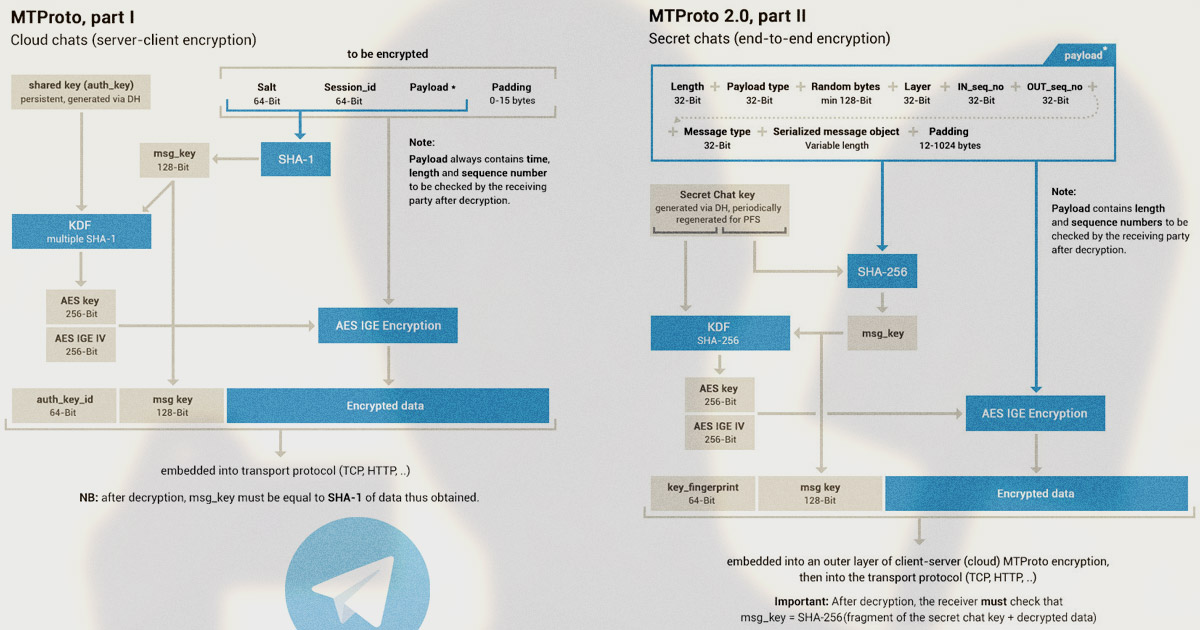
Durov explained why Telegram suddenly changed the cryptographic primitive → Roem.ru
Telegram encryption scheme
PS If you liked this post, let me know in the comments and we will continue to delve deeper into the topic of cryptography.
Anyone who read the previous post already knows that there are two main encryption methods. Symmetrical and asymmetrical. With symmetrical, everything is simple.
Both the sender and the recipient of the message have one encryption key. This is his main vulnerability, because if someone from the outside finds out the key, then it will not be difficult for him to decipher the intercepted message. So people went further and came up with asymmetric encryption. What is its essence?
I will use the most popular example with chests example. Let's remember symmetric encryption. There is one chest which contains messages. Both participants of the exchange have the same key. In asymmetric, everything is much more cunning. The recipient sends an open chest to the sender. The sender puts his message in it, closes it and sends it back. At the same time, only the recipient has the key itself, which means that this method of exchanging information is an order of magnitude more reliable.
RSA
And now, how it all works in practice. In the 1970s, three American scientists Ron Rivest, Adi Shamir and Leonard Adleman made a real breakthrough in the field of cryptography and created the first asymmetric encryption algorithm, which was named after the first letters of their names. It was based on a combination of several simple mathematical theories such as Fermat's theorem and Euler's function. And now, in a simple way. Suppose we have two numbers 17 and 19. They can be easily multiplied on a calculator and we get 323. But how to do the opposite operation - factor 323 into factors. It's already an order of magnitude more difficult, isn't it? Now imagine that this number is not 323, but for example 872847573857382943849229. A human is definitely not able to do this, and even a computer will take some time to find the factors. All asymmetric encryption is based on this simple principle. The multipliers are a private key that only the recipient has. But this large number is the public key that is sent from the recipient to the sender and back.
Application?
RSA-based encryption is used almost everywhere. This includes encryption of sites, messages in instant messengers, and much more. The trick is that modern services use a public key, which is a number of thousands of characters. Even a couple of supercomputers can't handle that. Also, these numbers are constantly changing. For example, why even the creators of Telegram do not know their own encryption keys. But because they are automatically updated on an ongoing basis. That's the whole point.

Durov explained why Telegram suddenly changed the cryptographic primitive → Roem.ru
Telegram encryption scheme
PS If you liked this post, let me know in the comments and we will continue to delve deeper into the topic of cryptography.

