Carding
Professional
- Messages
- 2,870
- Reaction score
- 2,493
- Points
- 113
We are all surrounded by passwords, one-time codes, keys, and tokens, but we don't always know they exist. They ensure the security of our accounts and data every minute. However, it is important for us to know exactly how the most basic information protection mechanisms work. One of them is authentication tokens, which increase the reliability of data protection and at the same time do not interfere with the comfortable use of services.
Subscribe to the data
Both people and programs need to know that the data was created by a trusted source and remained unchanged. For this purpose, the technology of generating a special hash (signature) was invented, which confirms the integrity of information and the authenticity of its sender/the Creator. To create this signature itself, a scheme of several steps is used, the purpose of which is to protect data from forgery.
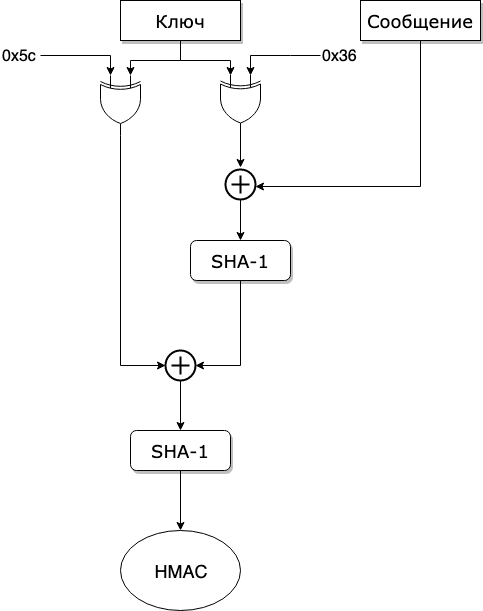
Scheme for generating HMAC (hash-based message authentication code), a message authentication code using a hash function
The hash algorithm may change, but the essence of this approach is simple and unchangeable: to confirm the integrity of the message, you need to find the signature of the protected data again and compare it with the existing signature.
Creating access codes
The people who came up with two-factor authentication, apparently, were guided by the principle "one head is good, and two are better". And indeed, two passwords are definitely safer than one. However, the passwords that the site sends via SMS are not completely secure: the message can most often be intercepted. Another thing is special authentication applications. they are aimed at fully protecting the entire user login process. It is these that we will now analyze with you.
Creating secure one-time passwords consists of two steps:
The initial configuration of the application is to exchange a secret key between the server and the application for authentication. This secret key is then used on the client's device to sign data that is known to both the server and the client. This key serves as the main confirmation of the user's identity when entering the password on the server.
In fact, the entire secret is a sequence of random characters that are encoded in Base32 format. In total, they occupy at least 128 bits, and more often all 190 bits. This sequence is what the user sees as text or a QR code.

This is what the QR code for exchanging a secret looks like
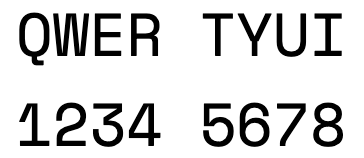
The same secret, only in text
How does the app create one-time codes? It's simple: the application uses the key to hash a certain value, most often a number, takes a certain part of the resulting hash and shows it to the user as a number of six or eight digits.
From the very beginning, the developers used a simple input counter for this number. The server counted the number of times you visited a website, for example, and the app knew how many times you requested a one-time password. This value was used to create each subsequent one-time code. In modern applications, the current time is taken instead of the counter and this is much more convenient for the user: input counters often got lost, and they had to be configured again.
Now let's try to calculate the authorization code yourself. For example, let's imagine that we decided to post a photo of a beautiful fireworks display right on New year's eve, and to do this, you need to log in to your account, which means that we can't do without a one-time password.
Let's take the time of the New year's celebration in UNIX format (1577811600000) and calculate the sequence number of our password: divide by 30 seconds - 52593720. Let's use our secret and calculate the hash - according to the RFC 6238 standard, this is a SHA-1 function:
Don't forget the argument -nfor the command echoso that there is no unnecessary line feed in its output, otherwise the hash will be different.
Now it's a small matter: you need to get six digits, which we will send to the server during authorization. Let's take the last four bits of the hash-the shift - it will be a number, or 10. It is on this shift that our code is located, which is still in the form of bytes,—03b08b12= 61901586. Discard all digits of this number, except for the last six, and get our brand-new, ready to-use one-time code -901586.
Logging in to the app
No modern application asks the user for a password all the time, because it annoys users. That is why developers and cryptographic scientists have come up with tokens that can replace a login — password pair. Scientists were faced with the task not so much to hide some information, but to create a common standard for its storage and confirmation of its reliability. For all this, the JSON Web Token (JWT) technology was invented.
How does JWT work?
If there is data that needs to be verified, we need to sign it with a secret key using HMAC. For this purpose, the same hashing method is used as for one-time passwords, only instead of six digits, the entire hash is taken. The only difference is the hash algorithm itself: in such tokens, SHA-1 is considered too short and insecure, so SHA-256 is usually used.
The main task of JWT is to confirm the identity of the token Creator and related data. Usually, the content of the token is a username or other user ID.
Let's try to create your own token. Let's continue our little story with the publication of a photo of fireworks on the social network: we entered a one-time password, the server confirmed our identity and wants to issue a token so that we can use it to open our application.
Any token consists of three parts: a header with service information, data, and a signature. Since the security standard is considered to be SHA-256, we will write it in our header.
Inside the token itself, information about the ID of the account we just signed in to will be stored.
We encode our data and header in Base64 and connect them via a dot. This is done to send data safely over HTTP: eyJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjogMTIzNDU2fQ. Now, knowing both the data and the header, we can calculate its hash, which contains our password string QWERTYUI12345678.
We also need to convert this hash to Base64 encoding and then attach it to the existing string from the header and data: eyJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjogMTIzNDU2fQ.4Ka0ipYe4/x-s4r82xqO8i77BXLh1TM7hdsqpmkZ6Y4- this is our token. You can use it!
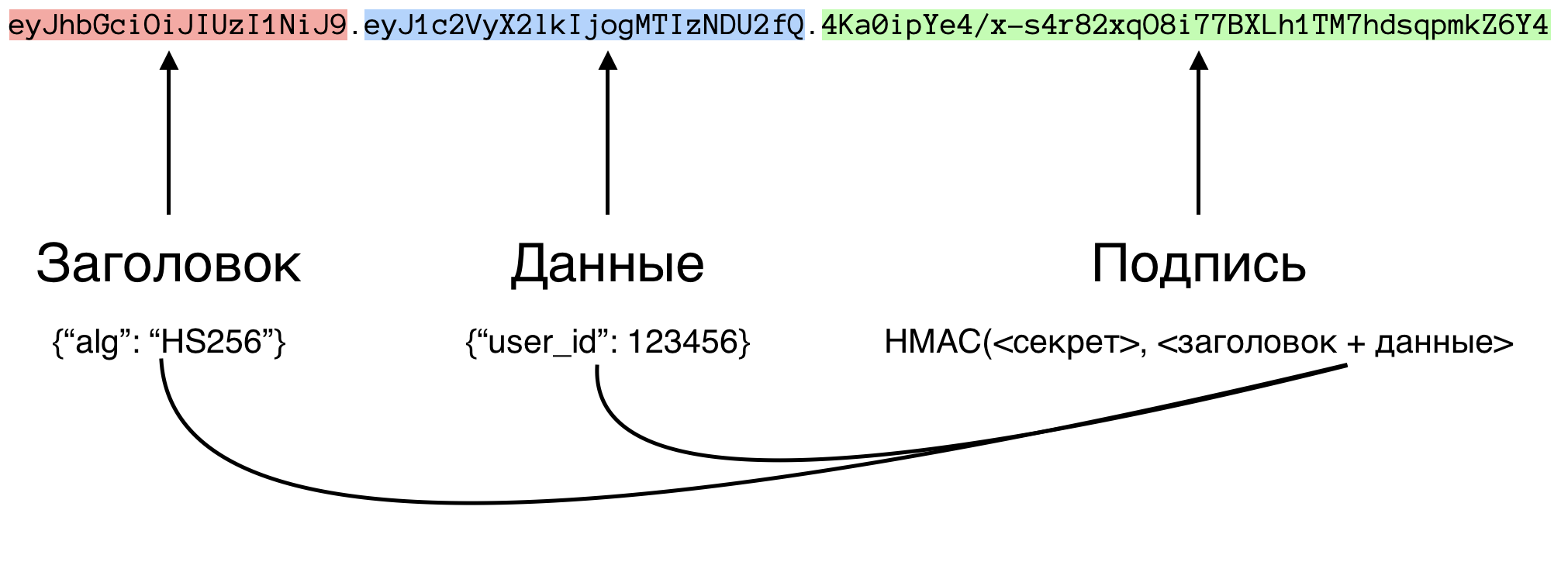
This is what our token looks like
WWW
You can read more about the JWT standard on the organization's RFC website and about the implementation for your favorite language on the site jwt.io.
Conclusion
Now you know what happens every day when you open your browser and log in to a web service. By understanding how this works, you can better protect your data, and perhaps even decide to apply some of these methods in your development.
xakep.ru
Subscribe to the data
Both people and programs need to know that the data was created by a trusted source and remained unchanged. For this purpose, the technology of generating a special hash (signature) was invented, which confirms the integrity of information and the authenticity of its sender/the Creator. To create this signature itself, a scheme of several steps is used, the purpose of which is to protect data from forgery.

Scheme for generating HMAC (hash-based message authentication code), a message authentication code using a hash function
The hash algorithm may change, but the essence of this approach is simple and unchangeable: to confirm the integrity of the message, you need to find the signature of the protected data again and compare it with the existing signature.
Creating access codes
The people who came up with two-factor authentication, apparently, were guided by the principle "one head is good, and two are better". And indeed, two passwords are definitely safer than one. However, the passwords that the site sends via SMS are not completely secure: the message can most often be intercepted. Another thing is special authentication applications. they are aimed at fully protecting the entire user login process. It is these that we will now analyze with you.
Creating secure one-time passwords consists of two steps:
- The primary setting is to enable two-factor authentication.
- Using a password means entering the code directly and sending it for verification.
The initial configuration of the application is to exchange a secret key between the server and the application for authentication. This secret key is then used on the client's device to sign data that is known to both the server and the client. This key serves as the main confirmation of the user's identity when entering the password on the server.
In fact, the entire secret is a sequence of random characters that are encoded in Base32 format. In total, they occupy at least 128 bits, and more often all 190 bits. This sequence is what the user sees as text or a QR code.

This is what the QR code for exchanging a secret looks like

The same secret, only in text
How does the app create one-time codes? It's simple: the application uses the key to hash a certain value, most often a number, takes a certain part of the resulting hash and shows it to the user as a number of six or eight digits.
From the very beginning, the developers used a simple input counter for this number. The server counted the number of times you visited a website, for example, and the app knew how many times you requested a one-time password. This value was used to create each subsequent one-time code. In modern applications, the current time is taken instead of the counter and this is much more convenient for the user: input counters often got lost, and they had to be configured again.
Now let's try to calculate the authorization code yourself. For example, let's imagine that we decided to post a photo of a beautiful fireworks display right on New year's eve, and to do this, you need to log in to your account, which means that we can't do without a one-time password.
Let's take the time of the New year's celebration in UNIX format (1577811600000) and calculate the sequence number of our password: divide by 30 seconds - 52593720. Let's use our secret and calculate the hash - according to the RFC 6238 standard, this is a SHA-1 function:
Code:
$ echo -n '52593720' | openssl sha1 -hmac 'QWERTYUI12345678'
e818e7f3efcb625658c603b08b12522f1e4d160aDon't forget the argument -nfor the command echoso that there is no unnecessary line feed in its output, otherwise the hash will be different.
Now it's a small matter: you need to get six digits, which we will send to the server during authorization. Let's take the last four bits of the hash-the shift - it will be a number, or 10. It is on this shift that our code is located, which is still in the form of bytes,—03b08b12= 61901586. Discard all digits of this number, except for the last six, and get our brand-new, ready to-use one-time code -901586.
Logging in to the app
No modern application asks the user for a password all the time, because it annoys users. That is why developers and cryptographic scientists have come up with tokens that can replace a login — password pair. Scientists were faced with the task not so much to hide some information, but to create a common standard for its storage and confirmation of its reliability. For all this, the JSON Web Token (JWT) technology was invented.
How does JWT work?
If there is data that needs to be verified, we need to sign it with a secret key using HMAC. For this purpose, the same hashing method is used as for one-time passwords, only instead of six digits, the entire hash is taken. The only difference is the hash algorithm itself: in such tokens, SHA-1 is considered too short and insecure, so SHA-256 is usually used.
The main task of JWT is to confirm the identity of the token Creator and related data. Usually, the content of the token is a username or other user ID.
Let's try to create your own token. Let's continue our little story with the publication of a photo of fireworks on the social network: we entered a one-time password, the server confirmed our identity and wants to issue a token so that we can use it to open our application.
Any token consists of three parts: a header with service information, data, and a signature. Since the security standard is considered to be SHA-256, we will write it in our header.
Code:
{
"alg": "HS256"
}Inside the token itself, information about the ID of the account we just signed in to will be stored.
Code:
{
"user_id": 123456
}We encode our data and header in Base64 and connect them via a dot. This is done to send data safely over HTTP: eyJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjogMTIzNDU2fQ. Now, knowing both the data and the header, we can calculate its hash, which contains our password string QWERTYUI12345678.
Code:
$ echo -n 'eyJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjogMTIzNDU2fQ' | openssl sha256 -hmac 'QWERTYUI12345678'
e0a6b48a961ee3fc7eb38afcdb1a8ef22efb0572e1d5333b85db2aa66919e98eWe also need to convert this hash to Base64 encoding and then attach it to the existing string from the header and data: eyJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjogMTIzNDU2fQ.4Ka0ipYe4/x-s4r82xqO8i77BXLh1TM7hdsqpmkZ6Y4- this is our token. You can use it!

This is what our token looks like
WWW
You can read more about the JWT standard on the organization's RFC website and about the implementation for your favorite language on the site jwt.io.
Conclusion
Now you know what happens every day when you open your browser and log in to a web service. By understanding how this works, you can better protect your data, and perhaps even decide to apply some of these methods in your development.
xakep.ru

