Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,036
- Points
- 113
Everything you need to know about a destructive attack using DNS queries.
Scientists have revealed details of a new powerful and effective pulsing denial-of-service (PDOs) attack technique that uses DNS queries and responses to achieve a 20,000-fold attack gain.
At its core, an attack called DNSBomb (CVE-2024-33655), exploits legitimate DNS features such as query frequency limits, query response timeouts, query aggregation, and maximum response size settings. These mechanisms allow you to create synchronized response streams using a specially designed authoritative server and a vulnerable recursive DNS resolver.
DNSBomb attack mechanism
Experts explain that DNSBomb uses many widely implemented DNS mechanisms to accumulate requests sent at a low speed, increase their size in responses, and concentrate all responses in short, high-volume periods in order to simultaneously overload the target systems.
Attack strategy
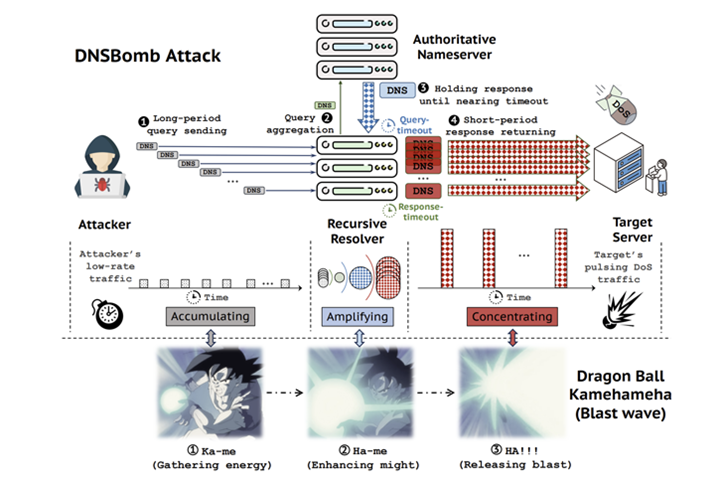
DNSBomb Attack Model
The attack model involves IP spoofing multiple DNS requests to a domain controlled by the attacker, and delaying responses to aggregate multiple responses. The goal of DNSBomb is to overload the victim with periodic bursts of heavy traffic that is difficult to detect.
Presentation of results and protection measures
The results of the study were presented at the 45th IEEE Symposium on Security and Privacy, held last week in San Francisco, and earlier at the GEEKCON 2023 event, held in Shanghai in October 2023.
The Internet Systems Consortium (ISC), which develops and maintains the BIND software package, said that the company's software is not vulnerable to DNSBomb. In addition, existing mitigation measures are sufficiently effective to minimize risks.
Scientists have revealed details of a new powerful and effective pulsing denial-of-service (PDOs) attack technique that uses DNS queries and responses to achieve a 20,000-fold attack gain.
At its core, an attack called DNSBomb (CVE-2024-33655), exploits legitimate DNS features such as query frequency limits, query response timeouts, query aggregation, and maximum response size settings. These mechanisms allow you to create synchronized response streams using a specially designed authoritative server and a vulnerable recursive DNS resolver.
DNSBomb attack mechanism
Experts explain that DNSBomb uses many widely implemented DNS mechanisms to accumulate requests sent at a low speed, increase their size in responses, and concentrate all responses in short, high-volume periods in order to simultaneously overload the target systems.
Attack strategy

DNSBomb Attack Model
The attack model involves IP spoofing multiple DNS requests to a domain controlled by the attacker, and delaying responses to aggregate multiple responses. The goal of DNSBomb is to overload the victim with periodic bursts of heavy traffic that is difficult to detect.
Presentation of results and protection measures
The results of the study were presented at the 45th IEEE Symposium on Security and Privacy, held last week in San Francisco, and earlier at the GEEKCON 2023 event, held in Shanghai in October 2023.
The Internet Systems Consortium (ISC), which develops and maintains the BIND software package, said that the company's software is not vulnerable to DNSBomb. In addition, existing mitigation measures are sufficiently effective to minimize risks.

