Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,038
- Points
- 113

Almost from the very beginning of the pandemic of the new coronavirus infection COVID-19, cybercriminals have been trying to cash in on this topic. We have already covered some of these malicious campaigns, but here we want to collect and consider all the ways to exploit the topic of coronavirus that can be found on the Web today.
Introduction
Most often, using the panic associated with COVID-19, attackers try to infect computers and mobile devices of citizens with malware. Also, various fraudulent schemes are often used, the main task of which is to force the victim to give his money.Unfortunately, with rare exceptions, such methods work because the attack surface is changing and expanding rather quickly - organizations are forced to move to the digital space as quickly as possible, exposing their systems to cyber threats.
Most modern attacks exploit the fear that accompanies the spread of the new COVID-19 infection. By reinforcing their campaigns with disinformation and fake posts, attackers are quite successful in slipping malware and mobile apps into inattentive users.
Criminals are primarily interested in money, but some COVID-19-related operations are setting the stage for cyber espionage.
Coronavirus-related cyber threats
As Rob Lefferts, VP of Microsoft 365 Security recently stated:However, of the total number of attacks analyzed by Microsoft on a daily basis, “coronavirus attacks” account for less than 2%. These statistics were presented by the employees of the corporation from Redmond."Every country in this world has faced at least one cyberattack exploiting the COVID-19 theme."
It should also be borne in mind that, as such, new and original attacks on the landscape did not arise. It's just that the criminals adapted their old proven schemes to the theme of a pandemic of a new infection. However, let's take a look at the most popular ways to exploit COVID-19 for cybercrime.
Mobile malware applications
Of course, attackers take into account our obsession with mobile devices, so they try to attack them. Such operations are especially successful under the cover of COVID-19.For example, researchers from Check Point have identified at least 16 different mobile applications, the authors of which promised up-to-date information about the spread of the new virus. Instead, users received malware on their devices.
Among such malicious software are Adware Hiddad and the Cerberus banking Trojan, which steals personal data and money. Also, experts met a malicious “dialer” (dialer), distributed under the guise of up-to-date information on COVID-19.
All 16 discovered apps were hosted on newly created domains that also featured coronavirus. By the way, the number of such resources has skyrocketed over the past few weeks.
Phishing emails
In the case of email phishing, delivering misinformation that plays on people's fear is even easier. It is enough to use a bright title and promise to familiarize the user with extremely important information.In such mailing lists, cybercriminals tend to disguise malware as attachments. For example, experts from Group-IB calculated that most phishing emails with the subject COVID-19 contain AgentTesla spyware (45%). It is followed by NetWire (30%) and LokiBot (8%).
Thus, attackers could collect personal data and payment information from unsuspecting victims almost without hindrance.
Malicious emails sent between February 13 and April 1, 2020 were most often disguised as notifications from the World Health Organization (WHO). Google analysts have just pointed to an increased number of such letters.
Discounts for malware posted on hacker forums
Not only the developers of information security products have thought out anti-crisis proposals to protect the remote access of employees (you can read the proposals in our article "Free protection of remote access for employees during the coronavirus pandemic"), but also cybercriminals are ready to drop the prices of their products.Cybersecurity researchers found over 500 posts on hacker forums in which attackers offered discounts and promo codes for DDoS, spam campaigns, and other similar services.
In particular, the authors of tools for creating exploits were noted, which offered their developments with the promo codes "COVID19" or "coronavirus".
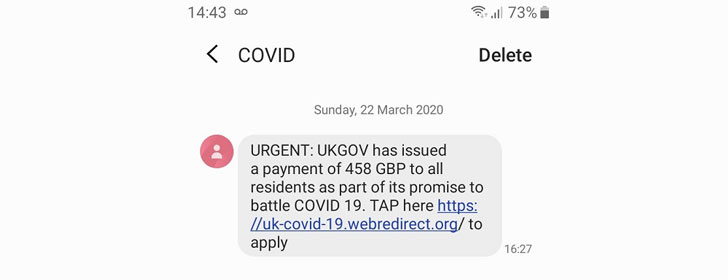
SMS phishing
The US Cybersecurity and Infrastructure Protection Agency and the UK National Cybersecurity Center recently warned citizens about the wave of SMS messages sent by "COVID" or "UKGOV". These notifications contained a link to a phishing site.Note that in this case, the criminals were not limited to only SMS messages, mailings were also carried out through popular instant messengers: WhatsApp, Telegram, Skype.
Figure 1. An example of a phishing SMS message
Medical mask and antiseptic scam
Europol recently arrested a 39-year-old Singaporean who was sending offers on behalf of a legitimate company. The fraudster promised to arrange for a fast delivery of medical masks and hand sanitizers.
As a result, a pharmaceutical company based in Europe suffered losses of € 6.64 million. Naturally, neither masks nor antiseptics were delivered, and the supplier himself simply disappeared.
Malicious programs
It's trite, but cybercriminals are using the skyrocketing popularity of video calling services to spread malware. For example, attackers have grown fond of Zoom and Microsoft Teams.In such campaigns, as a rule, the user receives a phishing email containing files with names like "zoom-us-zoom _ ##########. Exe" and "microsoft-teams_V # mu # D _ # #### #####. exe ".
Inattentive users can download and run these files on their computers, which will infect the device with malware.
Ransomware attacks
Interpol warned about operations in which cybercriminals use ransomware. Worst of all, criminals are attacking medical institutions that are currently in a very difficult situation - they are forced to fight the COVID-19 pandemic.Thus, ransomware operators are taking medical facilities as digital hostages, blocking critical files until management pays the ransom.
Conclusions
First of all, in order to protect yourself from such speculations on the pandemic, it is worth paying special attention to each link that comes by email and in instant messengers.Also, be sure to password protect your video conferencing so strangers can't get in your way.
We also recommend that you review the list of currently known malicious websites and email addresses.

