CarderPlanet
Professional
- Messages
- 2,552
- Reaction score
- 726
- Points
- 113
The Angara SOC team of cybercriminalists prepared a material with a reconstruction of the hacker attack, which lasted several days and seriously threatened the customer's business.
Let's note right away that the entry point was the account of an employee who had nothing to do with the IT and information security infrastructure, so this case once again confirms how important cyber literacy is not only for company employees, but also for contractors and even subcontractors.
Attack. First clues
Initially and further, criminals connected directly through Citrix ADC / NetScaler under the domain account of a sales department employee. Citrix is often used to provide remote access to the corporate network, including web-based access to the network. Below are the detected VPN sessions of the initially compromised user.

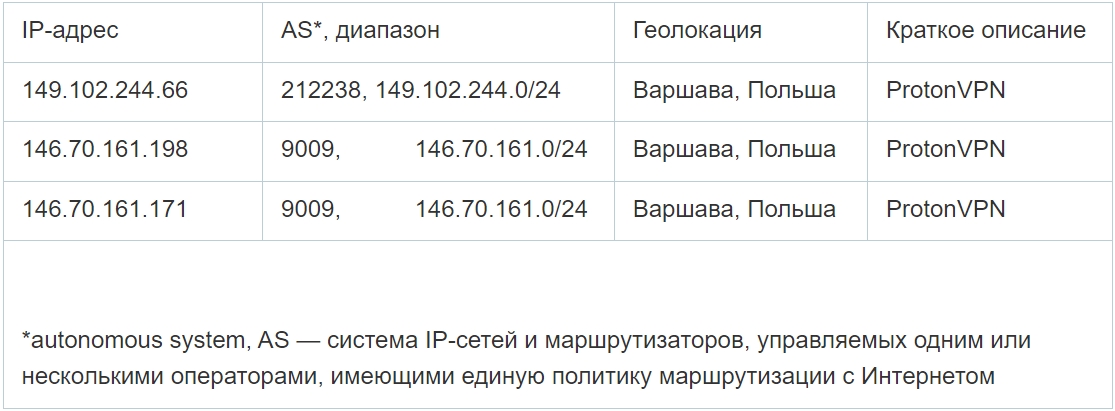
During the entire attack period, by correlating established sessions and connection events of Palo Alto network equipment, it was established that the connection source was IP addresses belonging to the same VPN provider-ProtonVPN:
149.102.244.66,
146.70.161.198,
146.70.161.171
Attack. Day one
On the first day of the investigation, we got access to the intermediate server and started studying the available local and remote files within the established session. To do this, we used a graphical interface and web resources that were marked in the browser bookmarks of the compromised user.
Below is a part of the history of web page visits in Internet Explorer. As you can see from these screenshots, the attackers were primarily interested in the organization's internal resources, such as Confluence, Jira, and other available applications.


Moreover, based on the Confluence access logs, it can be concluded that when accessing from a compromised server, criminals also tried to gain access from other accounts, but without subsequent clicks to any pages as part of the information search.

Attack. Second day
After connecting using a VPN the next day at 07: 10, the hackers continued exploring the host to find sensitive information. This is evidenced by the large number of available LNK files that are automatically created by the operating system when opening local or remote files, as well as the history of Internet Explorer, which contains information about access to both web and local resources.
During the entire attack period, the attackers gained access to a variety of files, source codes of individual applications, private keys, configuration files, and files .bash_history containing sensitive information.
After a short time after connecting and viewing individual files, we uploaded one of the first tools – EmEditor-as an archive(emed64_22.3.0_portable.zip). This is a flexible text editor with a wide range of features, including the ability to view very large files and manipulate them through a graphical interface. The archive was unpacked to the directory C:/Users/ < victim>/Downloads, which is actively used by attackers in the future.
As a continuation of our research of network directories, we downloaded three more tools in the same way on the same day:
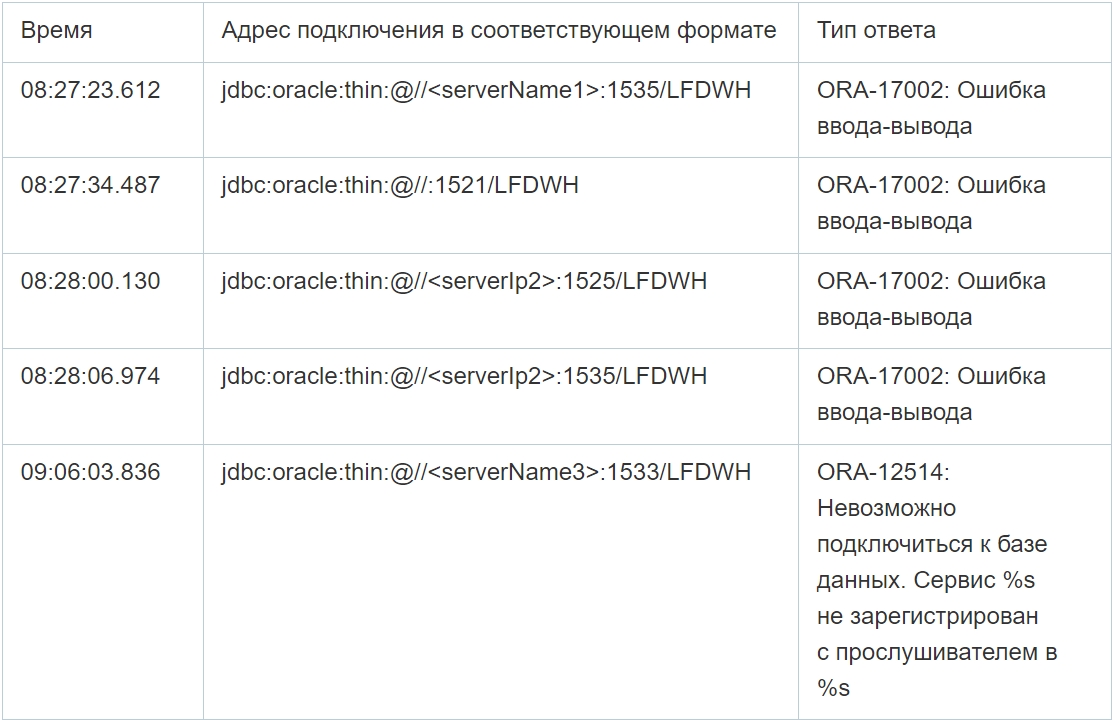
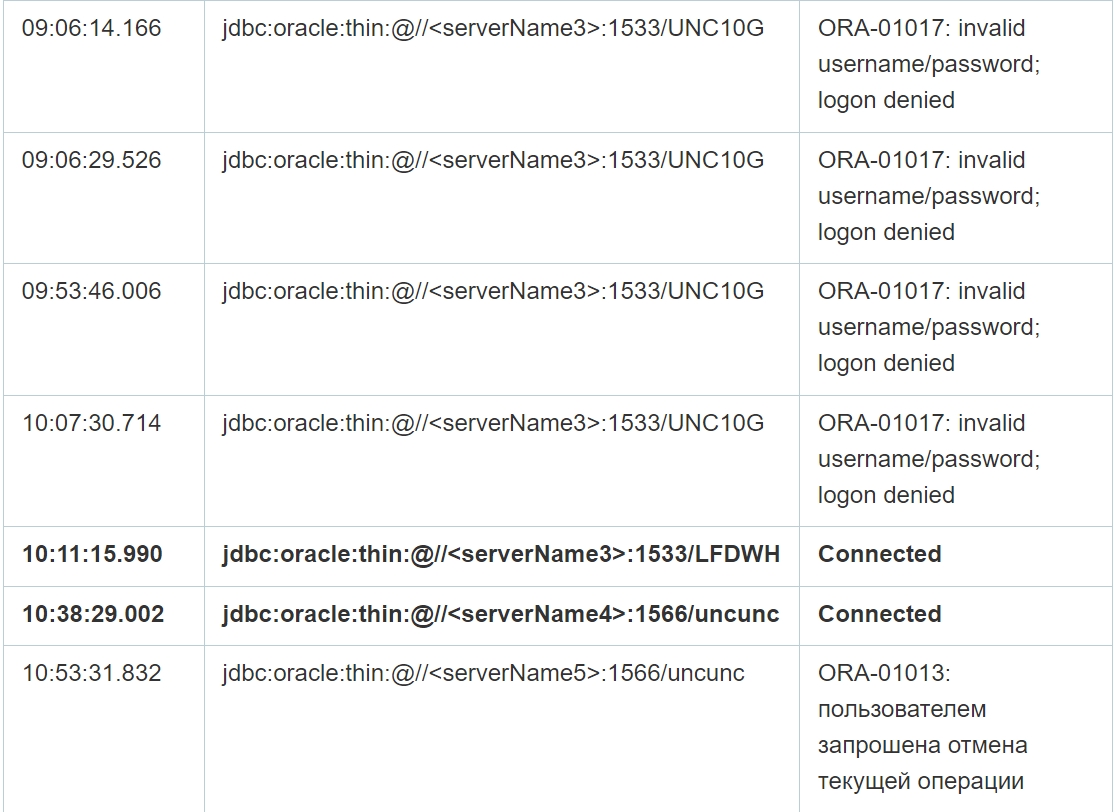
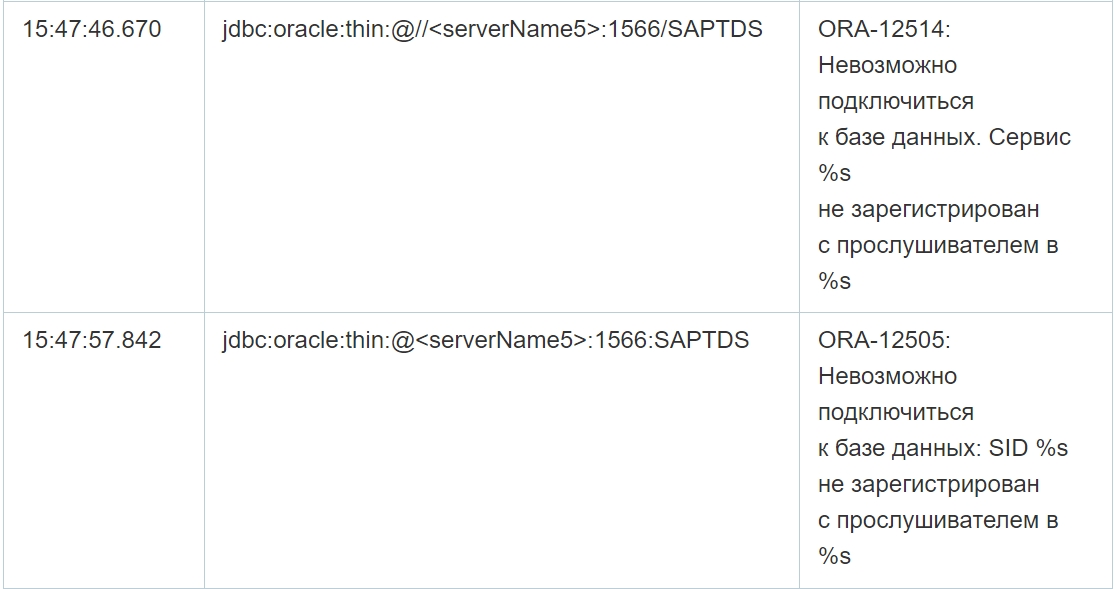
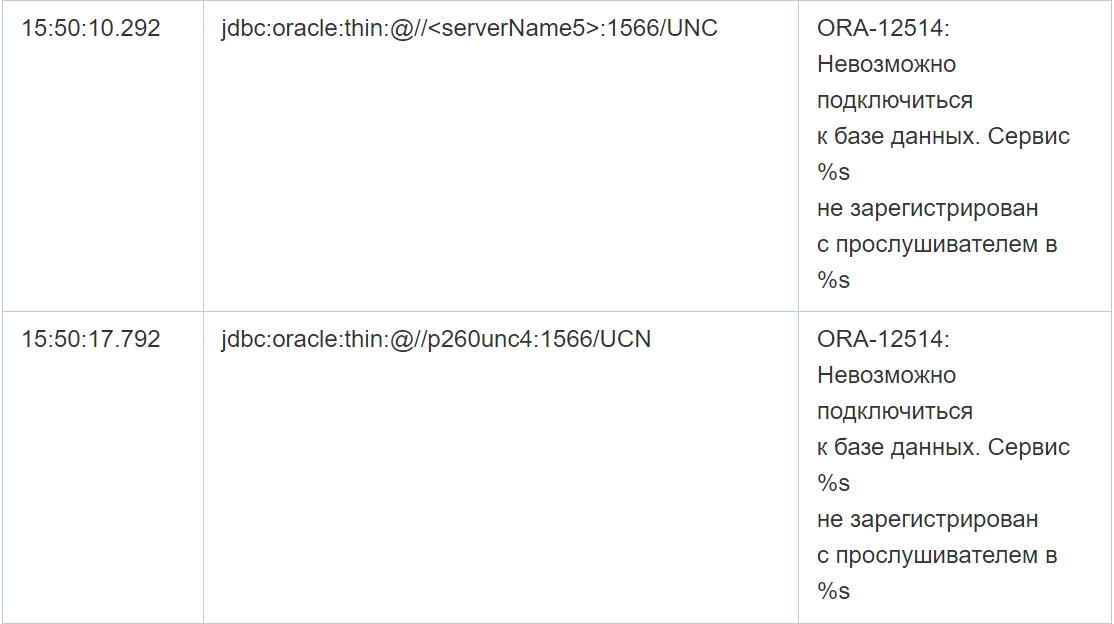
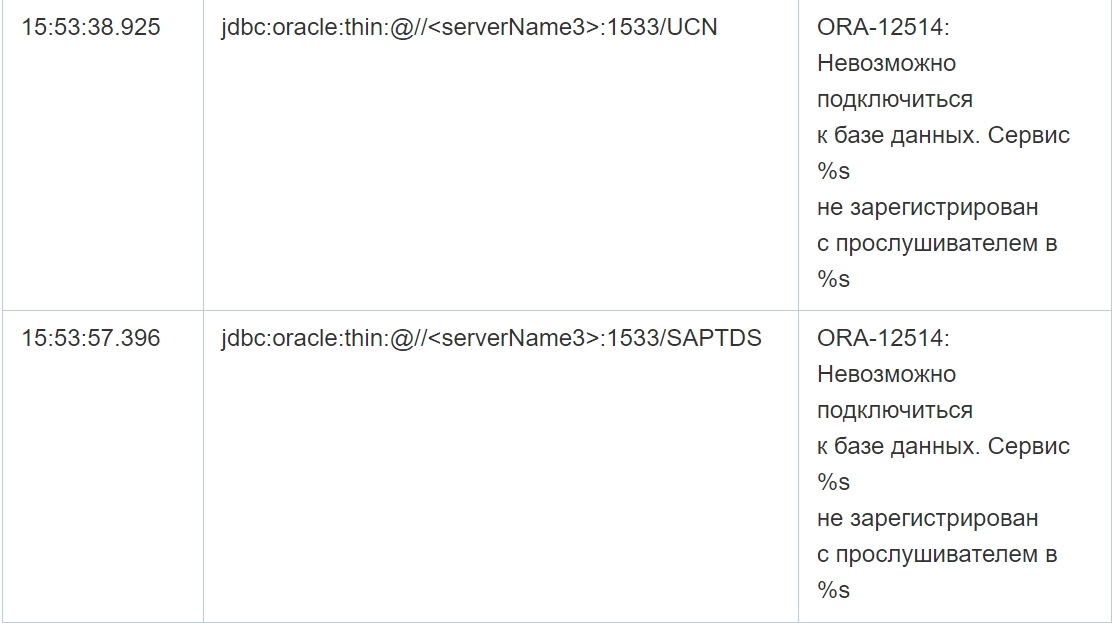
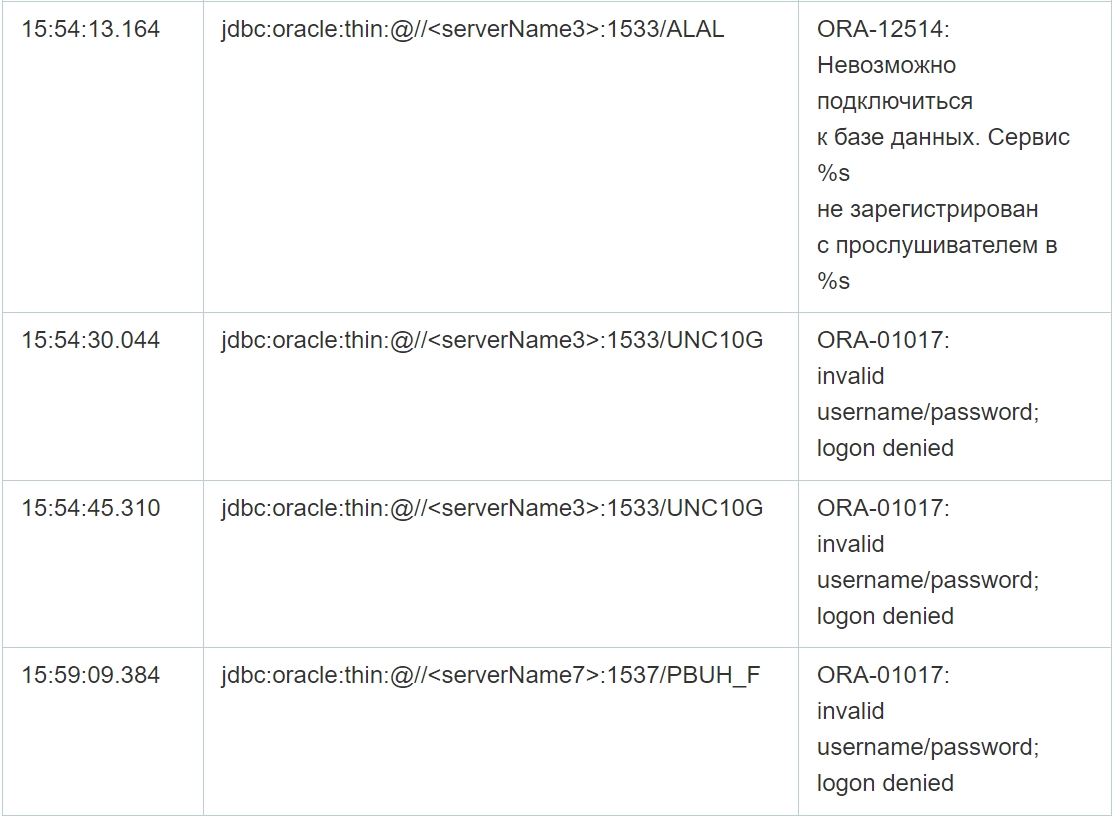
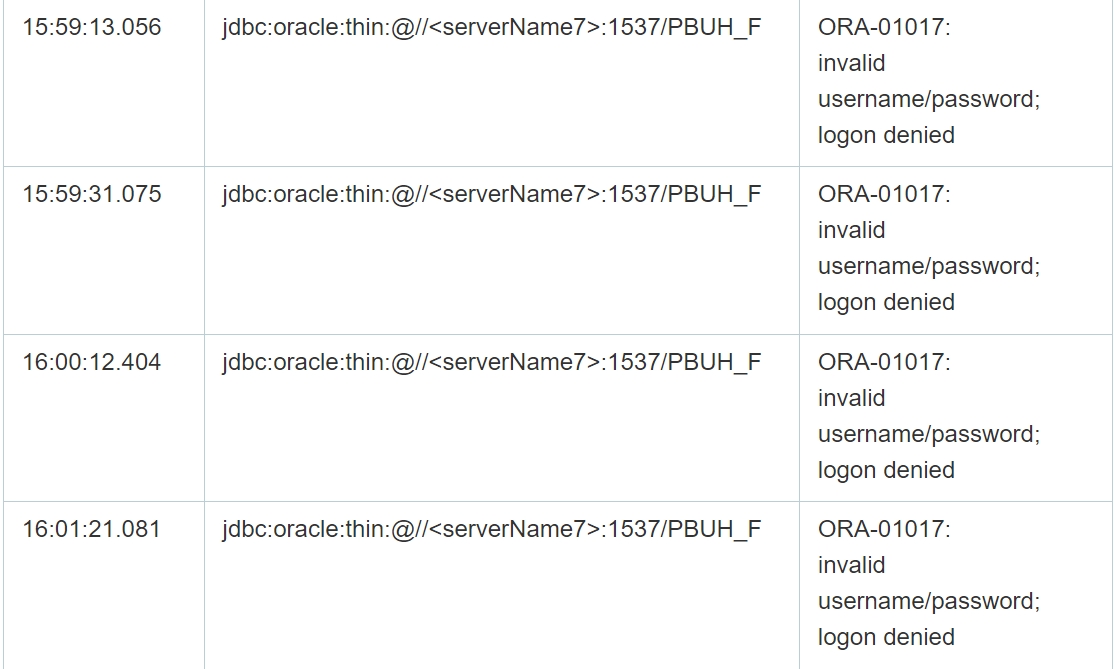
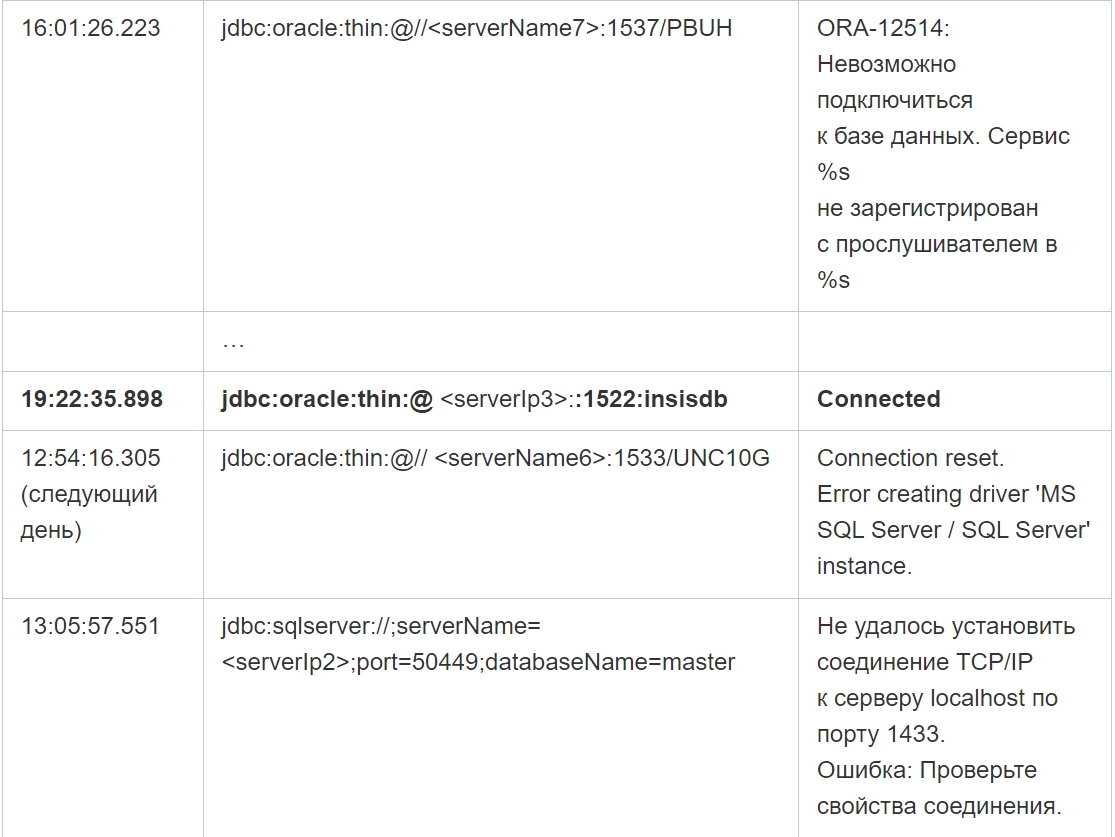
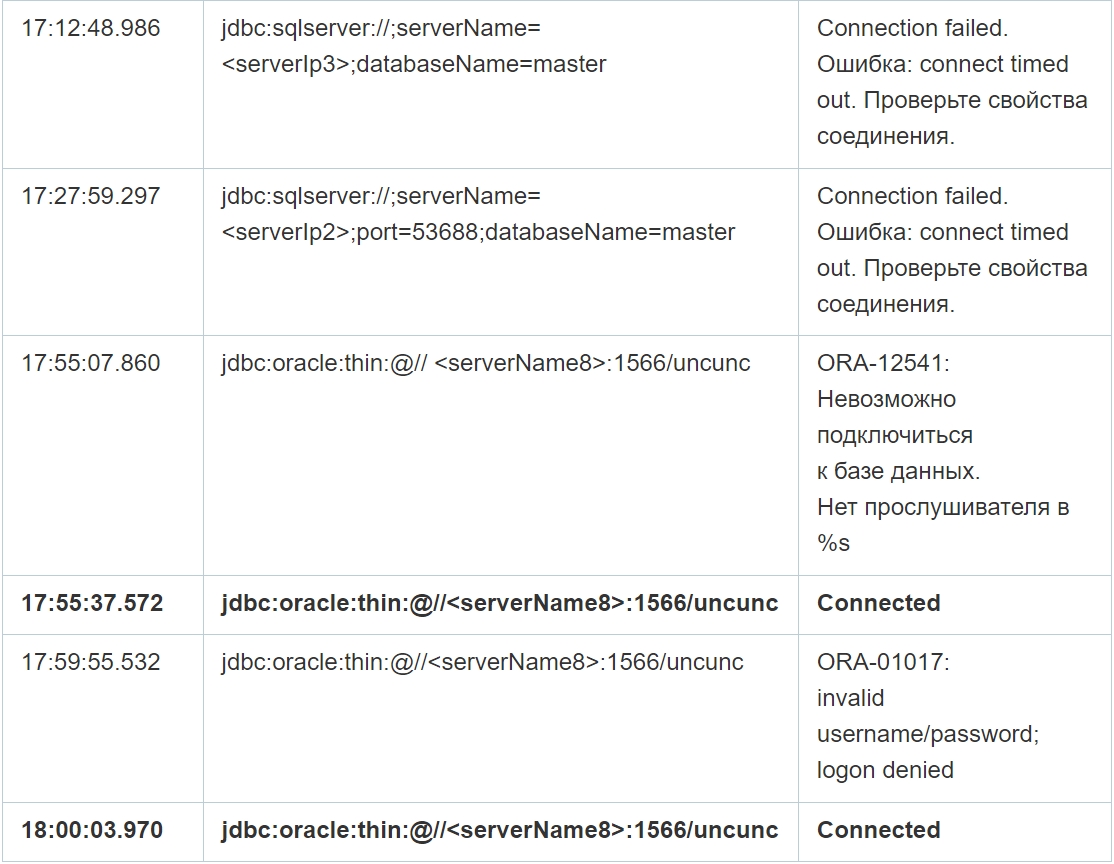
As you can see from the table above, despite multiple failed connection attempts, the connection was successfully established in the selected cases. Moreover, in addition, the application log file contains errors at the database level, that is, when executing queries, which confirms the possibility of data manipulation by attackers on the specified servers. Since there are no logs of completed requests, it is not possible to reliably restore the content of requests.
It is worth noting that in parallel with the events of the same day, at 10: 15: 20, the first files appeared in the file system of the previously compromised host, the names of which are similar to the standard format when uploading the database. However, it is not possible to restore these files due to technical features of the logical space of the virtual disk.

In addition, we recorded a significant increase in outgoing traffic, with a total volume of about 850 MB, which may indicate the first stage of data exfiltration.

During the post-exploitation phase, the attackers used only system tools and legitimate software intended for administration. So, at 18:37:45, the LDAP Admin utility was downloaded, unpacked, and launched (LdapAdminExe-w64-1.8.3.zip) located in the same folder C:\Users\ < victim>\Downloads\, for making LDAP requests to the target server. After analyzing the data obtained, the search for sensitive information continued.
In some cases, we tried connecting to individual servers via WinSCP or via an RDP connection (based on events in the TerminalServices RDPClient\Operational system log).
Additionally, during the attack, the attackers downloaded the qtweb, opera, and PortableGit web browsers. The latter solution is used to work with the Git version control system to view found git repository files.
Based on the log files of the GitLab repository management system, available at https://gitlab. < companyname>. ru/, hackers at 16:31:43 accessed a remote address that belongs to the subnet of the tunnel configured for the contractor. There is no explicit information about the account used for activation. Based on events from domain controllers, authentication on the resource was performed, among other things, using one of the privileged accounts. However, it is impossible to state unequivocally that only this account was used.
A detailed analysis of the requested URIs revealed that the search was performed for individual keywords, including: "bitrix", "password", "mysql", "postgres", "ms-auth", "sftp", "ssh", "oracle", "jdbc", "postgresql", "password prod", "bitrix", "sk2239", "sftp-prod.autoins.ru", "ftp", "password admin", "password basic", "basic auth admin", "aws secret backup", "password username jdbc", "password mysql", " storage.yandexcloud.net", "CLO_STORAGE_YANDEX", "BEGIN RSA PRIVATE KEY", "ssh private rsa"," 10.255.1", several other internal and external addresses, and then search through the branches found.
Later, at 18: 10: 35 and 18: 53: 59 on the same day, the first login was recorded from the same privileged account from the intermediate server to the web interfaces of the Confluence and Jira spaces.

At 20:04:50, in the auth.log log, an ssh connection to another server (already on the GNU/Linux operating system) was recorded using the credentials of a privileged local account that belongs to the sudo group and has the same login password. There were no repeated errors when logging in to the server. Most likely, the authentication material was obtained earlier in clear form from previously studied files.
Because the history of commands entered by the user .bash_history is kept without specifying timestamps, it is not possible to reliably determine the commands entered by intruders on servers, and no obvious signs of malicious activity were found. So, probably, hackers installed the Midnight Commander file manager for more convenient interaction with the file system.:
sudo apt install mc
mc
However, at 22:03:58, the first request to the MySQL database was made from this server on behalf of the service account, probably also obtained in the same way during the study stage.
SELECT * FROM <prodTable> WHERE ID > 12427356;
Presumably, for upload purposes, a tunnel was built using Putty and WinSCP clients to create an SFTP (FTP over SSH) /SCP session. At the same time, the response files received after the first request-user.sql and user2023.sql - were uploaded to the initially compromised server, after which the file was split into RAR archives. It is noteworthy that a number of commands were executed by the attacker directly through WinSCP, namely, checking network access to the server:
nc -zv -w1 10.255.1.6 3306
nc -zv -w1 10.255.1.6 22
ping -c 1 10.255.1.6

Attack. Day three
On the third and final day, at 09: 53: 06 (user session creation - at 08: 49: 37), the second request was made:
SELECT ID,TIMESTAMP_X,LOGIN,’PASSWORD’,NAME,LAST_NAME,EMA IL,LAST_LOGIN,PERSONAL_PHONE,PERSONAL_BIRTHDAY,SEC OND_NAME FROM <prodTable>
When uploading the results of processed requests to the external network, the growth of outgoing traffic is similarly tracked (total for the previous day ≈ 2517 MB, current ≈ 1078 MB). After uploading the results, after deleting some of the traces and files created in the process, the session was completed. In the future, no invalid events were implemented.
Conclusions? Recommendations
Attackers don't always use sophisticated techniques or malicious code. Sometimes they achieve their goal by using only legitimate tools, but they find the necessary information just by carefully studying the available resources.
This behavior of hackers is quite difficult to distinguish from the actions of a regular user or an application administrator. This is exactly what Leak Wolf uses. Perhaps these guys know more about the NLB Telegram channel, where they post the data of some of their victims.
Therefore, we present our practical recommendations to prevent such cyberattacks "on the edge"on distant approaches:
Bonus: Compromise indicators
IP addresses:
We are always in touch, Angara SOC!
Let's note right away that the entry point was the account of an employee who had nothing to do with the IT and information security infrastructure, so this case once again confirms how important cyber literacy is not only for company employees, but also for contractors and even subcontractors.
Attack. First clues
Initially and further, criminals connected directly through Citrix ADC / NetScaler under the domain account of a sales department employee. Citrix is often used to provide remote access to the corporate network, including web-based access to the network. Below are the detected VPN sessions of the initially compromised user.

| Established VPN sessions of the initially compromised user |
149.102.244.66,
146.70.161.198,
146.70.161.171
Attack. Day one
On the first day of the investigation, we got access to the intermediate server and started studying the available local and remote files within the established session. To do this, we used a graphical interface and web resources that were marked in the browser bookmarks of the compromised user.
Below is a part of the history of web page visits in Internet Explorer. As you can see from these screenshots, the attackers were primarily interested in the organization's internal resources, such as Confluence, Jira, and other available applications.


| Part of the web page browsing history of a compromised user's Internet Explorer browser |

| Accessing a Confluence space from a compromised server (10.97.0.83) |
Attack. Second day
After connecting using a VPN the next day at 07: 10, the hackers continued exploring the host to find sensitive information. This is evidenced by the large number of available LNK files that are automatically created by the operating system when opening local or remote files, as well as the history of Internet Explorer, which contains information about access to both web and local resources.
During the entire attack period, the attackers gained access to a variety of files, source codes of individual applications, private keys, configuration files, and files .bash_history containing sensitive information.
After a short time after connecting and viewing individual files, we uploaded one of the first tools – EmEditor-as an archive(emed64_22.3.0_portable.zip). This is a flexible text editor with a wide range of features, including the ability to view very large files and manipulate them through a graphical interface. The archive was unpacked to the directory C:/Users/ < victim>/Downloads, which is actively used by attackers in the future.
As a continuation of our research of network directories, we downloaded three more tools in the same way on the same day:
- HeidiSQL, an open source administration tool for multiple databases at once, such as MariaDB, MySQL, as well as Microsoft SQL Server, PostgreSQL, and SQLite
- WinSCP, an FTP, FTPS, SCP, and SFTP client for Windows
- dbeaver, a database administration tool with the ability to interact with databases via the JDBC driver









As you can see from the table above, despite multiple failed connection attempts, the connection was successfully established in the selected cases. Moreover, in addition, the application log file contains errors at the database level, that is, when executing queries, which confirms the possibility of data manipulation by attackers on the specified servers. Since there are no logs of completed requests, it is not possible to reliably restore the content of requests.
It is worth noting that in parallel with the events of the same day, at 10: 15: 20, the first files appeared in the file system of the previously compromised host, the names of which are similar to the standard format when uploading the database. However, it is not possible to restore these files due to technical features of the logical space of the virtual disk.

| Traces of opening files (Internet Explorer history) |

| Outbound traffic growth |
In some cases, we tried connecting to individual servers via WinSCP or via an RDP connection (based on events in the TerminalServices RDPClient\Operational system log).
Additionally, during the attack, the attackers downloaded the qtweb, opera, and PortableGit web browsers. The latter solution is used to work with the Git version control system to view found git repository files.
Based on the log files of the GitLab repository management system, available at https://gitlab. < companyname>. ru/, hackers at 16:31:43 accessed a remote address that belongs to the subnet of the tunnel configured for the contractor. There is no explicit information about the account used for activation. Based on events from domain controllers, authentication on the resource was performed, among other things, using one of the privileged accounts. However, it is impossible to state unequivocally that only this account was used.
A detailed analysis of the requested URIs revealed that the search was performed for individual keywords, including: "bitrix", "password", "mysql", "postgres", "ms-auth", "sftp", "ssh", "oracle", "jdbc", "postgresql", "password prod", "bitrix", "sk2239", "sftp-prod.autoins.ru", "ftp", "password admin", "password basic", "basic auth admin", "aws secret backup", "password username jdbc", "password mysql", " storage.yandexcloud.net", "CLO_STORAGE_YANDEX", "BEGIN RSA PRIVATE KEY", "ssh private rsa"," 10.255.1", several other internal and external addresses, and then search through the branches found.
Later, at 18: 10: 35 and 18: 53: 59 on the same day, the first login was recorded from the same privileged account from the intermediate server to the web interfaces of the Confluence and Jira spaces.

| Excerpt from the user's browser history |
Because the history of commands entered by the user .bash_history is kept without specifying timestamps, it is not possible to reliably determine the commands entered by intruders on servers, and no obvious signs of malicious activity were found. So, probably, hackers installed the Midnight Commander file manager for more convenient interaction with the file system.:
sudo apt install mc
mc
However, at 22:03:58, the first request to the MySQL database was made from this server on behalf of the service account, probably also obtained in the same way during the study stage.
SELECT * FROM <prodTable> WHERE ID > 12427356;
Presumably, for upload purposes, a tunnel was built using Putty and WinSCP clients to create an SFTP (FTP over SSH) /SCP session. At the same time, the response files received after the first request-user.sql and user2023.sql - were uploaded to the initially compromised server, after which the file was split into RAR archives. It is noteworthy that a number of commands were executed by the attacker directly through WinSCP, namely, checking network access to the server:
nc -zv -w1 10.255.1.6 3306
nc -zv -w1 10.255.1.6 22
ping -c 1 10.255.1.6

| WinSCP.ini configuration file that contains the history of commands entered by the user, as well as information about connections |
On the third and final day, at 09: 53: 06 (user session creation - at 08: 49: 37), the second request was made:
SELECT ID,TIMESTAMP_X,LOGIN,’PASSWORD’,NAME,LAST_NAME,EMA IL,LAST_LOGIN,PERSONAL_PHONE,PERSONAL_BIRTHDAY,SEC OND_NAME FROM <prodTable>
When uploading the results of processed requests to the external network, the growth of outgoing traffic is similarly tracked (total for the previous day ≈ 2517 MB, current ≈ 1078 MB). After uploading the results, after deleting some of the traces and files created in the process, the session was completed. In the future, no invalid events were implemented.
Conclusions? Recommendations
Attackers don't always use sophisticated techniques or malicious code. Sometimes they achieve their goal by using only legitimate tools, but they find the necessary information just by carefully studying the available resources.
This behavior of hackers is quite difficult to distinguish from the actions of a regular user or an application administrator. This is exactly what Leak Wolf uses. Perhaps these guys know more about the NLB Telegram channel, where they post the data of some of their victims.
Therefore, we present our practical recommendations to prevent such cyberattacks "on the edge"on distant approaches:
- Set access control for addresses that belong to VPN providers, proxies, and anonymizers
- Implement multi-factor authentication on all publicly accessible and critical resources to provide an additional level of verification of internal users and increase their security in order to protect them from hacking
- Monitor and conduct a regular inventory of your IT assets, including external ones, to avoid creating a shadow infrastructure
- Strict password policy: at least 14 characters for user accounts, the use of letters of different cases, as well as special characters. Always keep a password log (the number of old passwords that are stored in Active Directory, prohibiting the user from reusing the old password, which is configured similarly through the password policy
- Exclude the possibility of using the same passwords for local privileged accounts for both Windows and Linux systems
- Cybercrime and digital hygiene of employees - your everything
- Make sure that passwords are not stored in easily accessible files in clear text, and when using the terminal, do not enter them explicitly to prevent them from being saved in the command history.
- Use EDR-class solutions to protect your end devices. It is important to ensure maximum network coverage to prevent the appearance of blind spots
- When delineating access, apply the principle of minimum privileges in the system, paying special attention to accounts used for automated processes and remote access.
- Connect the database query log to monitor queries with responses that contain a large number of rows.
Bonus: Compromise indicators
IP addresses:

We are always in touch, Angara SOC!
