Carder
Professional
- Messages
- 2,620
- Reaction score
- 2,043
- Points
- 113
There are many ways to track a person Online. Almost everything leaves traces that allow you to distinguish one user from another: search queries, clicks on links, and system settings. "Banner cutters" help you protect yourself from the simplest surveillance, but gradually more sophisticated ways to cover your tracks are beginning to appear.
Using private mode or clearing your browser history, you only delete local traces. However, logs with all requests remain on the search engine server. They are analyzed in search of statistical correlations and fill the user's shadow profile with fresh data. Everything that can be calculated is taken into account: the frequency of requests, their type, the number of errors, the time spent analyzing search results, clicks on suggested links, reactions to contextual advertising, and much more.
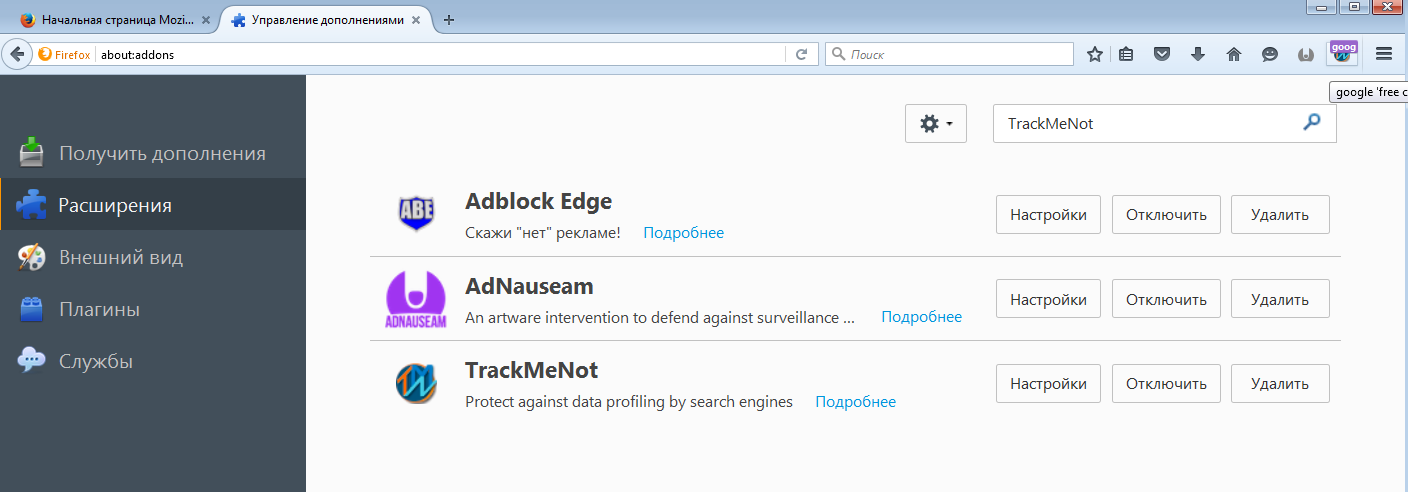
Two plugins in addition to Adblock Edge
Formally, this is done "to improve the quality of service" and the ability to give "personal recommendations". Real — it is often passed on or sold to marketers for use in targeted advertising, and it also often falls into the hands of political strategists and government agencies who are looking for more subtle methods of crowd control and preemptive detection of anyone who poses a potential threat.
Collecting only the information that's available and not even offering to explicitly fill in information about themselves Google, Yandex and other search engines are detailed profiles of all who have ever used their services. By rating queries, it is easy to assess the popularity of operating systems, programs, and plugins, the degree of Internet penetration in different regions, and find out what the majority of users are currently thinking and how they react to news. Based on specific requests and typical behavior, you can identify a person even if they have changed their OS, browser, account, and IP address.
A fundamentally different method is used in TrackMeNot (TMN), a plugin for Firefox and Chrome written in the Department of computer science at new York University using JavaScript, C++, and XUL. It works in the background and generates bogus search queries, dissolving real ones in them and making it difficult to collect information about user preferences. This obfuscation is effective because the plugin operates exclusively on the client side and does not depend on centralized servers.
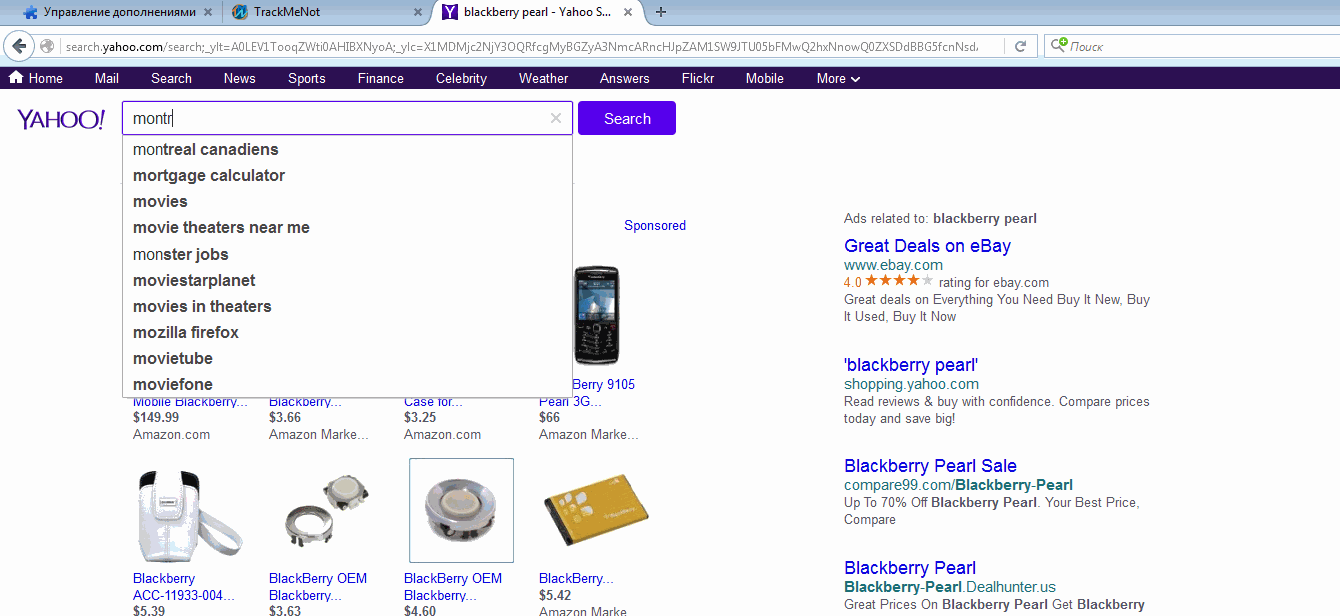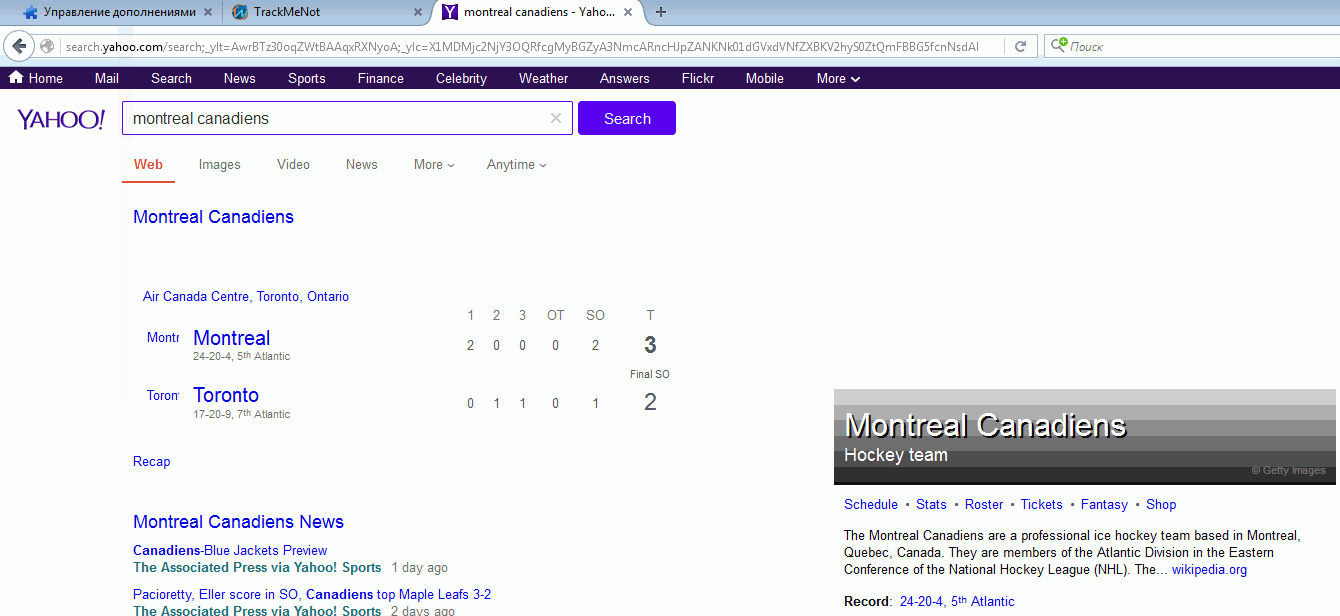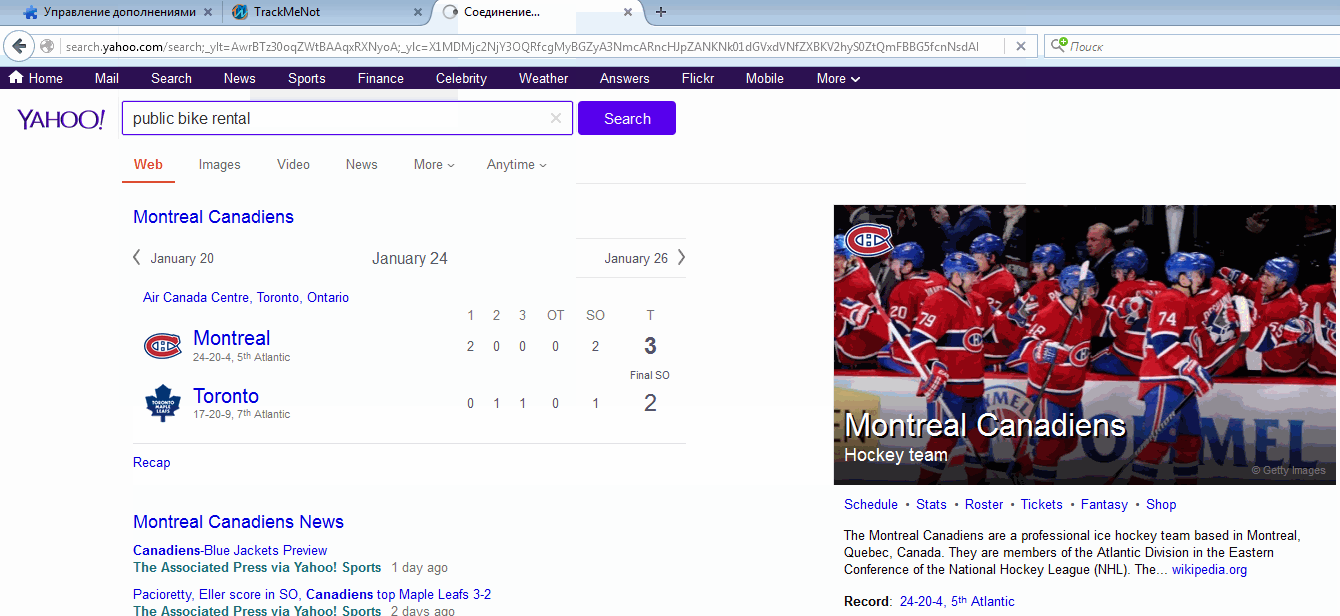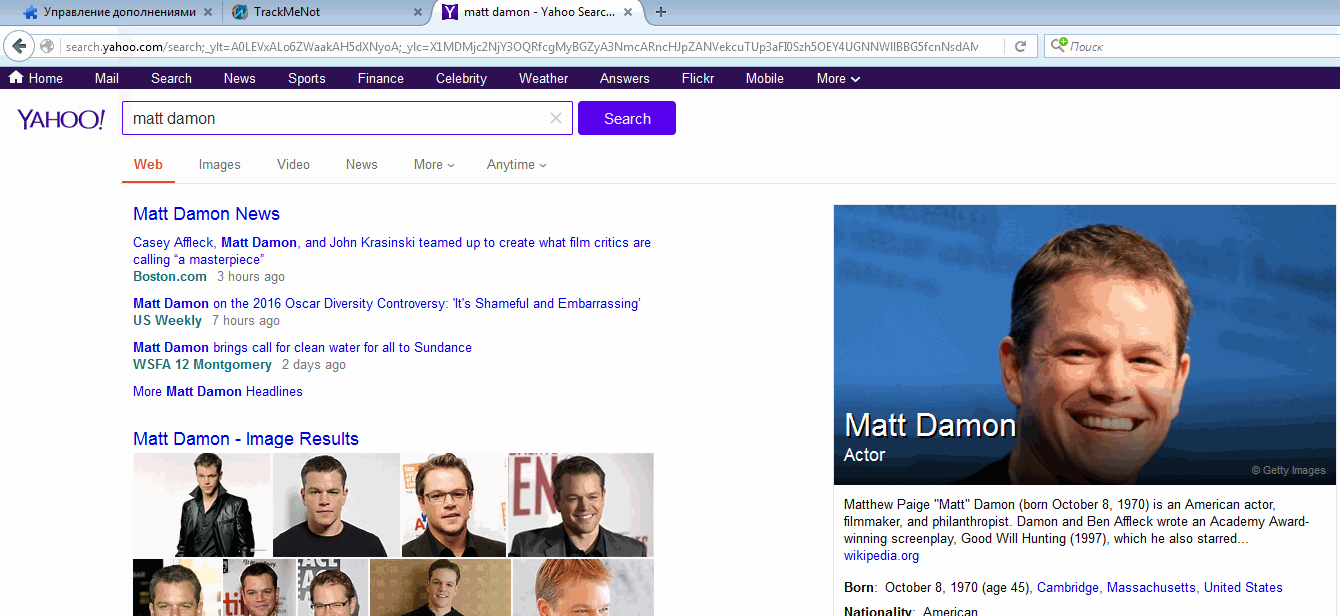
Example of simulating a search in TrackMeNot
For ten years of its existence, the program has acquired interesting mechanisms of mimicry for the actions of a real user. In recent versions, the feature set has been expanded with several original mechanisms: dynamic query lists (with RSS feed-based initialization), a queue of related search phrases, and selective clicks in search results. In addition, TMN can perform queries in the background or in a separate browser tab, simulate scrolling results, and add clarifying words to previously entered phrases.

TMN settings
The burst-mode option better mimics human behavior, since without it, requests are sent at regular intervals. It also helps you avoid being banned by Google (the search engine redirects you to the captcha page if it suspects that a bot is sending requests from your IP address). If the redirect occurs even with burst mode, just change the interval for sending false requests to a longer one (say, ten requests per hour).
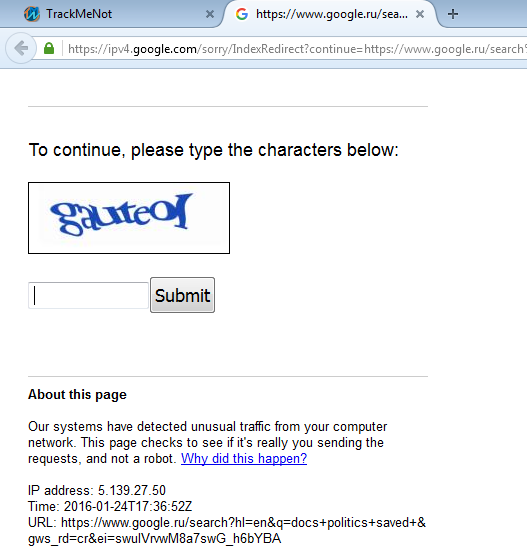
Abuse of TMN leads to IP ban in search engines before entering captcha
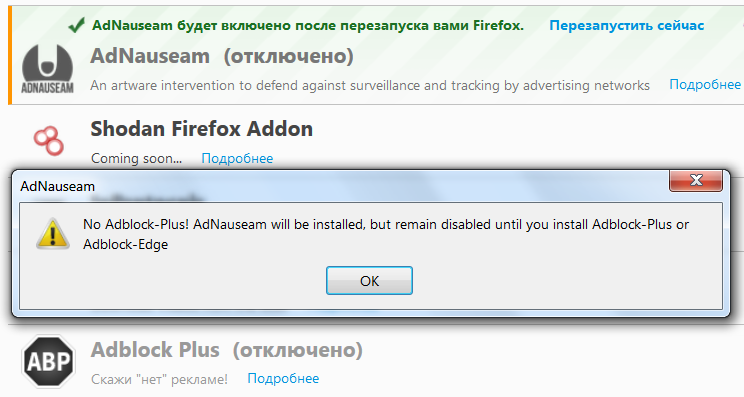
AdNauseam requires Adblock
AdNauseam hides real click-throughs in the automatic click stream. It simply clicks on everything in the background, making it difficult to assign the user to a specific target audience. Working together with Adblock, AdNauseam clogs ad network databases with false statistics. User profiling becomes useless, and they usually don't see the ad itself at all — with a rare and customizable exception. Not all versions of Adblock support the program. After V. 2.6.11 Adblock Plus became incompatible with It, and the formally suitable edge fork was abandoned and in practice also useless. There is only one way out so far: install the old version of Adblock Plus, which can be found on the archive page.
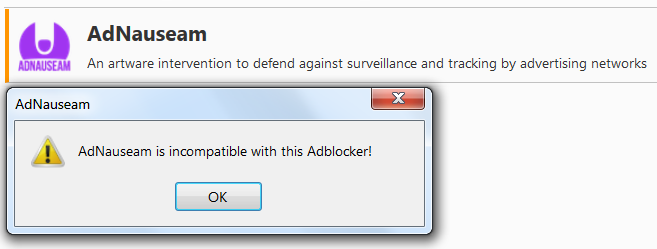
AdNauseam is not compatible with versions of Adblock Plus after 2.6.11
After installing the AdNauseam plugin, you need to run it manually. It works secretly, but allows you to view logs and statistics of your work. Background clicks on advertising links are opened in the "sandbox" - an unreadable browser tab. It is created using the page-worker API in Mozilla Firefox.

Detected ad on the current tab
AdNauseam log in a few minutes of operation
The idea of both Addons lies on the surface and has already proven itself quite well. There is a chance to see similar extensions adapted to use the Cyrillic alphabet and popular advertising networks in Russia.
Public privacy
The search bar for many users has become much more familiar than the address bar.it's not for nothing that most browsers have combined them into one. This is good for search engines: they live by collecting data that we supply to them, without even thinking about it seriously.Using private mode or clearing your browser history, you only delete local traces. However, logs with all requests remain on the search engine server. They are analyzed in search of statistical correlations and fill the user's shadow profile with fresh data. Everything that can be calculated is taken into account: the frequency of requests, their type, the number of errors, the time spent analyzing search results, clicks on suggested links, reactions to contextual advertising, and much more.

Two plugins in addition to Adblock Edge
Formally, this is done "to improve the quality of service" and the ability to give "personal recommendations". Real — it is often passed on or sold to marketers for use in targeted advertising, and it also often falls into the hands of political strategists and government agencies who are looking for more subtle methods of crowd control and preemptive detection of anyone who poses a potential threat.
Collecting only the information that's available and not even offering to explicitly fill in information about themselves Google, Yandex and other search engines are detailed profiles of all who have ever used their services. By rating queries, it is easy to assess the popularity of operating systems, programs, and plugins, the degree of Internet penetration in different regions, and find out what the majority of users are currently thinking and how they react to news. Based on specific requests and typical behavior, you can identify a person even if they have changed their OS, browser, account, and IP address.
Disappear into the crowd
Most of the tools for the protection of privacy using methods of concealing a unique ID and user settings. However, when they try to hide some markers, they add others. Statistics collection technologies are increasingly embedded in browser extensions, and they themselves have unique identifiers — URIs.A fundamentally different method is used in TrackMeNot (TMN), a plugin for Firefox and Chrome written in the Department of computer science at new York University using JavaScript, C++, and XUL. It works in the background and generates bogus search queries, dissolving real ones in them and making it difficult to collect information about user preferences. This obfuscation is effective because the plugin operates exclusively on the client side and does not depend on centralized servers.

Example of simulating a search in TrackMeNot
For ten years of its existence, the program has acquired interesting mechanisms of mimicry for the actions of a real user. In recent versions, the feature set has been expanded with several original mechanisms: dynamic query lists (with RSS feed-based initialization), a queue of related search phrases, and selective clicks in search results. In addition, TMN can perform queries in the background or in a separate browser tab, simulate scrolling results, and add clarifying words to previously entered phrases.

TMN settings
The burst-mode option better mimics human behavior, since without it, requests are sent at regular intervals. It also helps you avoid being banned by Google (the search engine redirects you to the captcha page if it suspects that a bot is sending requests from your IP address). If the redirect occurs even with burst mode, just change the interval for sending false requests to a longer one (say, ten requests per hour).

Abuse of TMN leads to IP ban in search engines before entering captcha
Flood ad networks
Online advertising is becoming more aggressive and is also used for covert profiling of network activity. Blocking it only partially solves the problem and can unmask the user even more. Therefore, the principle of the "white noise" generator was repeated in The adnauseam plugin. "to the point of nausea") - an extension for Firefox that protects the user from tracking banner networks and means of personalization of ad impressions.
AdNauseam requires Adblock
AdNauseam hides real click-throughs in the automatic click stream. It simply clicks on everything in the background, making it difficult to assign the user to a specific target audience. Working together with Adblock, AdNauseam clogs ad network databases with false statistics. User profiling becomes useless, and they usually don't see the ad itself at all — with a rare and customizable exception. Not all versions of Adblock support the program. After V. 2.6.11 Adblock Plus became incompatible with It, and the formally suitable edge fork was abandoned and in practice also useless. There is only one way out so far: install the old version of Adblock Plus, which can be found on the archive page.

AdNauseam is not compatible with versions of Adblock Plus after 2.6.11
After installing the AdNauseam plugin, you need to run it manually. It works secretly, but allows you to view logs and statistics of your work. Background clicks on advertising links are opened in the "sandbox" - an unreadable browser tab. It is created using the page-worker API in Mozilla Firefox.

Detected ad on the current tab

AdNauseam log in a few minutes of operation
From deception to self-deception
The obfuscation methods used by TrackMeNot and AdNauseam have their negative aspects. Obviously, after installing them, network traffic increases. This may be critical if you use the Internet via a mobile network. The very fact of using extensions for obfuscation is easily determined by sites and advertising networks. By default, search queries in TrackMeNot are performed only in English. Theoretically, you can specify Russian-language RSS feeds as the source of keywords in the settings, but in practice this leads to plugin error messages or only English terms are eliminated. Similarly, AdNauseam doesn't recognize ad links from Russian-language resources very well. Despite the "sandbox", background clicking on all links in a row in AdNauseam increases the risk of running into drive-by threats through phishing links. In addition, the authors of the extension will probably be able to profit from the stream of fake clicks if their plugin bypasses the anti-cheating tools.The idea of both Addons lies on the surface and has already proven itself quite well. There is a chance to see similar extensions adapted to use the Cyrillic alphabet and popular advertising networks in Russia.

