Father
Professional
- Messages
- 2,601
- Reaction score
- 836
- Points
- 113
Inaction of administrators leads to loss of confidential data.
Varonis discovered 2 ways to bypass audit logs or create less significant records when downloading files from SharePoint.
The first method uses the Open in App feature of SharePoint, which allows you to open documents in Word instead of a web browser. This action generates an "Access" event in the audit logs instead of "File downloaded", which the administrator can ignore. Especially dangerous is that the URL obtained with this method of accessing the file does not have an expiration date, which allows you to download files without restrictions.
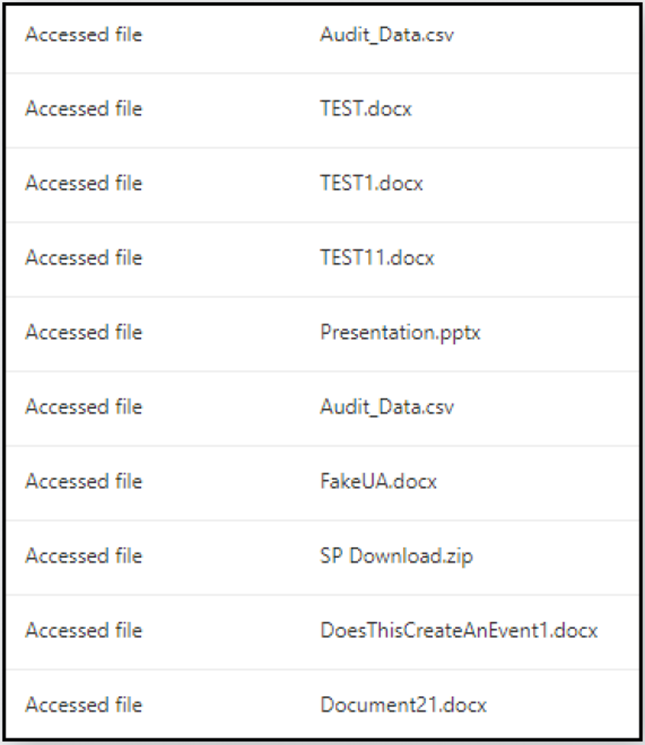
Multiple access events created as a result of a series of file exfiltrations
The second method is to replace the User-Agent string when requesting access to a file, which makes file uploads via the browser or the Microsoft Graph API look like data synchronization events (Microsoft SkyDriveSync), reducing suspicion on the part of security services.
Varonis reported the vulnerabilities to Microsoft in November 2023, and the company added them to the list of issues for future remediation, although they were marked as "not requiring an immediate fix."
Varonis recommends monitoring the high level of access activity in a short period of time and the appearance of new devices from unusual locations, which may indicate unauthorized data extraction. It is also recommended to carefully check synchronization events for anomalies in frequency and data volumes.
Microsoft has confirmed that SharePoint is working properly by reporting file access through the audit log. The company recommends using the FileAccessed, FileDownloaded, FileSyncDownloadedFull, and FileSyncDownloadedPartial events to monitor file access.
Varonis discovered 2 ways to bypass audit logs or create less significant records when downloading files from SharePoint.
The first method uses the Open in App feature of SharePoint, which allows you to open documents in Word instead of a web browser. This action generates an "Access" event in the audit logs instead of "File downloaded", which the administrator can ignore. Especially dangerous is that the URL obtained with this method of accessing the file does not have an expiration date, which allows you to download files without restrictions.

Multiple access events created as a result of a series of file exfiltrations
The second method is to replace the User-Agent string when requesting access to a file, which makes file uploads via the browser or the Microsoft Graph API look like data synchronization events (Microsoft SkyDriveSync), reducing suspicion on the part of security services.
Varonis reported the vulnerabilities to Microsoft in November 2023, and the company added them to the list of issues for future remediation, although they were marked as "not requiring an immediate fix."
Varonis recommends monitoring the high level of access activity in a short period of time and the appearance of new devices from unusual locations, which may indicate unauthorized data extraction. It is also recommended to carefully check synchronization events for anomalies in frequency and data volumes.
Microsoft has confirmed that SharePoint is working properly by reporting file access through the audit log. The company recommends using the FileAccessed, FileDownloaded, FileSyncDownloadedFull, and FileSyncDownloadedPartial events to monitor file access.

