Father
Professional
- Messages
- 2,601
- Reaction score
- 836
- Points
- 113
The malicious image was used for 3 years as a bridge between the hacker and user data.
On one of the product pages of a global retailer specializing in the sale of photographic equipment, a hidden code was found in an image with the inscription "thank you". Initially seemingly harmless, "gratitude" contained a mechanism to bypass security systems, which could lead to the theft of personal data of customers.
A comment with the image was posted by the owner of the Nikon camera, who was looking for recommendations on choosing a 50 mm lens. Despite the fact that the image looked absolutely normal at first glance, it remained on the site without attention for three years.
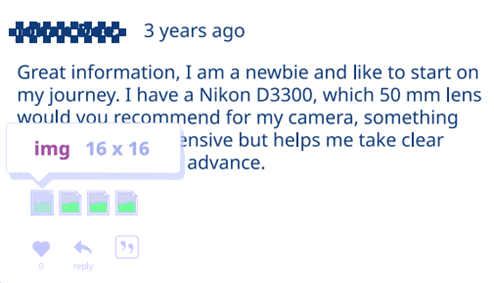
Modified image in a comment on the site
The threat was identified only after the company started using a web security threat management solution. During a routine check, the system found hidden instructions and the address of the compromised domain in the image.
The method used by the attackers is known as steganography — a technique for hiding data inside other information, in this case, inside the image code. The image file embedded in an outdated comment was changed, and JavaScript on the page linking to the image source was linked to the compromised domain. Further investigation revealed that the code was communicating with an external domain.
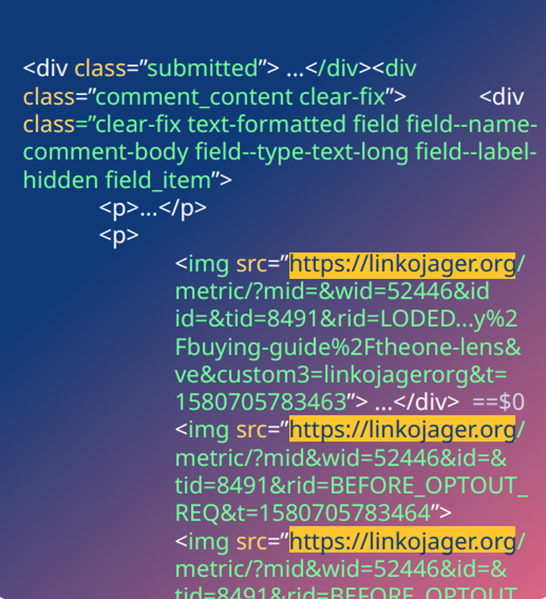
Example of malicious image code
By changing enough pixels, you can create a sequence of values that the computer can interpret as code. In this case, the modified image contained hidden instructions and the address of the compromised domain. It was surprising to find that the JavaScript on the page used this hidden information to link to the domain.
The discovery of such a threat underscores the importance of protecting comments and other user content on e-commerce sites. Cybercriminals are constantly looking for ways to steal personal information and payment data, and laws like the GDPR require companies to comply with strict security measures and impose large fines for data leaks.
The continuous monitoring system used made it possible to identify and prevent potential threats in a timely manner. The platform automatically blocked suspicious activity of web components and protected users confidential information.
On one of the product pages of a global retailer specializing in the sale of photographic equipment, a hidden code was found in an image with the inscription "thank you". Initially seemingly harmless, "gratitude" contained a mechanism to bypass security systems, which could lead to the theft of personal data of customers.
A comment with the image was posted by the owner of the Nikon camera, who was looking for recommendations on choosing a 50 mm lens. Despite the fact that the image looked absolutely normal at first glance, it remained on the site without attention for three years.

Modified image in a comment on the site
The threat was identified only after the company started using a web security threat management solution. During a routine check, the system found hidden instructions and the address of the compromised domain in the image.
The method used by the attackers is known as steganography — a technique for hiding data inside other information, in this case, inside the image code. The image file embedded in an outdated comment was changed, and JavaScript on the page linking to the image source was linked to the compromised domain. Further investigation revealed that the code was communicating with an external domain.

Example of malicious image code
By changing enough pixels, you can create a sequence of values that the computer can interpret as code. In this case, the modified image contained hidden instructions and the address of the compromised domain. It was surprising to find that the JavaScript on the page used this hidden information to link to the domain.
The discovery of such a threat underscores the importance of protecting comments and other user content on e-commerce sites. Cybercriminals are constantly looking for ways to steal personal information and payment data, and laws like the GDPR require companies to comply with strict security measures and impose large fines for data leaks.
The continuous monitoring system used made it possible to identify and prevent potential threats in a timely manner. The platform automatically blocked suspicious activity of web components and protected users confidential information.

