Tomcat
Professional
- Messages
- 2,688
- Reaction score
- 1,037
- Points
- 113
In mid-August, we discovered a malware distribution campaign that was targeting the Czech Republic. It came to our attention because the malware files were distributed through URLs that closely resembled those of the Czech Postal Department. Further analysis of the files showed that we are dealing with banking malware, which is similar in its capabilities to Zeus and SpyEye, but differs from already known families in the technical implementation of its capabilities.
The new Trojan program is called Win32/Spy.Hesperbot and is a powerful tool for stealing online banking data. Hesperbot has the following features:
In our collection, we found several more earlier variants of this Trojan, which we detected as Win32/Agent.UXO .
The attackers' goal is to obtain the credentials that users use to log into their online banking account. In addition, the malicious code convinces the user to install its mobile component on a phone running Symbian, Blackberry or Android.
The Czech campaign to distribute this malware began on August 8, 2013. To do this, the attackers registered the domain ceskaposta.net, which resembles the website of the Czech postal service with the address ceskaposta.cz.
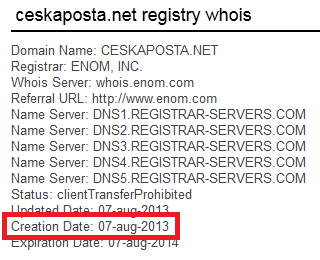
Rice. Domain creation date.
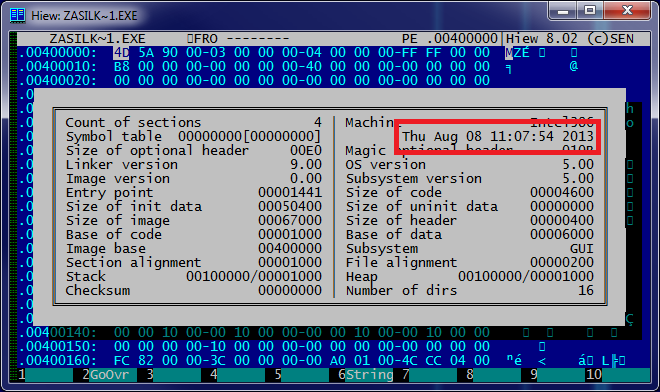
Rice. File compilation date.
The domain was registered on August 7 this year, and the first Hesperbot samples, which were distributed in the Czech Republic, were compiled on the morning of August 8 and later captured by our LiveGrid system.
In addition to the URL, which is very similar to the Czech postal service, the attackers used thematic content of the letters in order to be more convincing. The letter contained information from the postal service about the status of the supposedly sent letter. The names of the files themselves had corresponding names, for example, zasilka.pdf.exe. The word "zasilka" is translated from Czech as "letter". In the message, the attackers used the address ceskaposta.net, disguising it as legitimate ceskaposta.cz.

Rice. Report from the Czech Postal Service about the scam.
Despite the fact that it was the Czech campaign that caught our attention, the country most affected by the activities of this banking Trojan was Turkey. Hesperbot samples related to Turkey were compiled earlier than August 8th. The last peak of botnet activity was detected in Turkey back in July 2013; in addition, older samples date back to April 2013. Some samples of the Trojan program send debugging information to the C&C command server, so the attackers tested intermediate versions of it and checked its functionality.
The campaign, which was carried out by attackers in Turkey, is similar in nature to the Czech attack. The attackers used a similar approach in the emails they sent to potential victims. We later discovered that the same approach was used to target users in Portugal and England.
During our research, we came across an additional component that is used by Win32/Spy.Hesperbot. We are talking about malicious code Win32/Spy.Agent.OEC, which is responsible for collecting email addresses on the infected machine and sending them to a remote server. It is possible that the collected email addresses were then used in malware distribution campaigns.
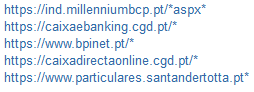
The configuration files used by the malware when intercepting HTTP traffic tell it which online banking sites to intercept. Various botnets specialize in hijacking specific websites. Below are the addresses of online banking systems that are monitored by malicious code.
Czech Republic
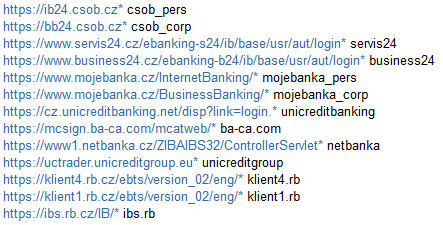
Turkey
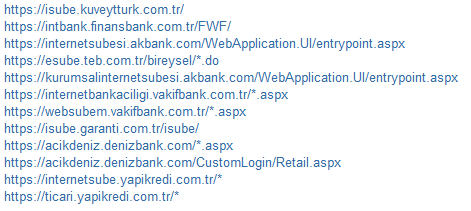
Portugal
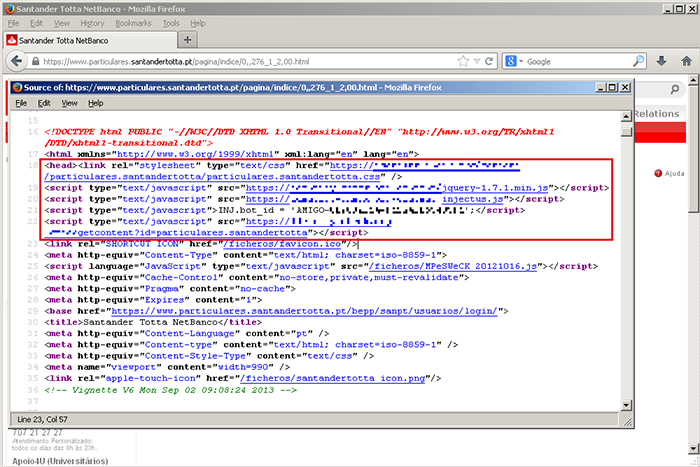
In the case of Turkish and Portuguese botnets, configuration files include information about web injections, i.e. pieces of HTML code that malicious code will insert into web pages. Similar code was not found in the Czech configuration file. This suggests that attackers could use simple keylogger functionality for this purpose.
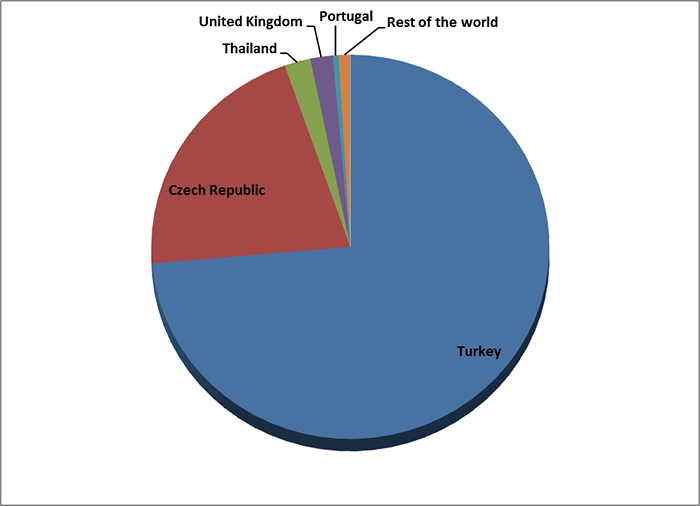
Using the ESET LiveGrid telemetry system, hundreds of cases of compromise of users were recorded in Turkey, the Czech Republic, the UK and Portugal.
(c) https://habr.com/ru/companies/eset/articles/192684/
The new Trojan program is called Win32/Spy.Hesperbot and is a powerful tool for stealing online banking data. Hesperbot has the following features:
- interception of network traffic and HTML injection;
- keylogger;
- taking desktop screenshots;
- video capture;
- creating a remote proxy connection;
- creating a hidden VNC server.
In our collection, we found several more earlier variants of this Trojan, which we detected as Win32/Agent.UXO .
The attackers' goal is to obtain the credentials that users use to log into their online banking account. In addition, the malicious code convinces the user to install its mobile component on a phone running Symbian, Blackberry or Android.
The Czech campaign to distribute this malware began on August 8, 2013. To do this, the attackers registered the domain ceskaposta.net, which resembles the website of the Czech postal service with the address ceskaposta.cz.

Rice. Domain creation date.

Rice. File compilation date.
The domain was registered on August 7 this year, and the first Hesperbot samples, which were distributed in the Czech Republic, were compiled on the morning of August 8 and later captured by our LiveGrid system.
In addition to the URL, which is very similar to the Czech postal service, the attackers used thematic content of the letters in order to be more convincing. The letter contained information from the postal service about the status of the supposedly sent letter. The names of the files themselves had corresponding names, for example, zasilka.pdf.exe. The word "zasilka" is translated from Czech as "letter". In the message, the attackers used the address ceskaposta.net, disguising it as legitimate ceskaposta.cz.

Rice. Report from the Czech Postal Service about the scam.
Despite the fact that it was the Czech campaign that caught our attention, the country most affected by the activities of this banking Trojan was Turkey. Hesperbot samples related to Turkey were compiled earlier than August 8th. The last peak of botnet activity was detected in Turkey back in July 2013; in addition, older samples date back to April 2013. Some samples of the Trojan program send debugging information to the C&C command server, so the attackers tested intermediate versions of it and checked its functionality.
The campaign, which was carried out by attackers in Turkey, is similar in nature to the Czech attack. The attackers used a similar approach in the emails they sent to potential victims. We later discovered that the same approach was used to target users in Portugal and England.
During our research, we came across an additional component that is used by Win32/Spy.Hesperbot. We are talking about malicious code Win32/Spy.Agent.OEC, which is responsible for collecting email addresses on the infected machine and sending them to a remote server. It is possible that the collected email addresses were then used in malware distribution campaigns.
The configuration files used by the malware when intercepting HTTP traffic tell it which online banking sites to intercept. Various botnets specialize in hijacking specific websites. Below are the addresses of online banking systems that are monitored by malicious code.
Czech Republic

Turkey

Portugal

In the case of Turkish and Portuguese botnets, configuration files include information about web injections, i.e. pieces of HTML code that malicious code will insert into web pages. Similar code was not found in the Czech configuration file. This suggests that attackers could use simple keylogger functionality for this purpose.

Using the ESET LiveGrid telemetry system, hundreds of cases of compromise of users were recorded in Turkey, the Czech Republic, the UK and Portugal.

(c) https://habr.com/ru/companies/eset/articles/192684/

