Eyes wide shut
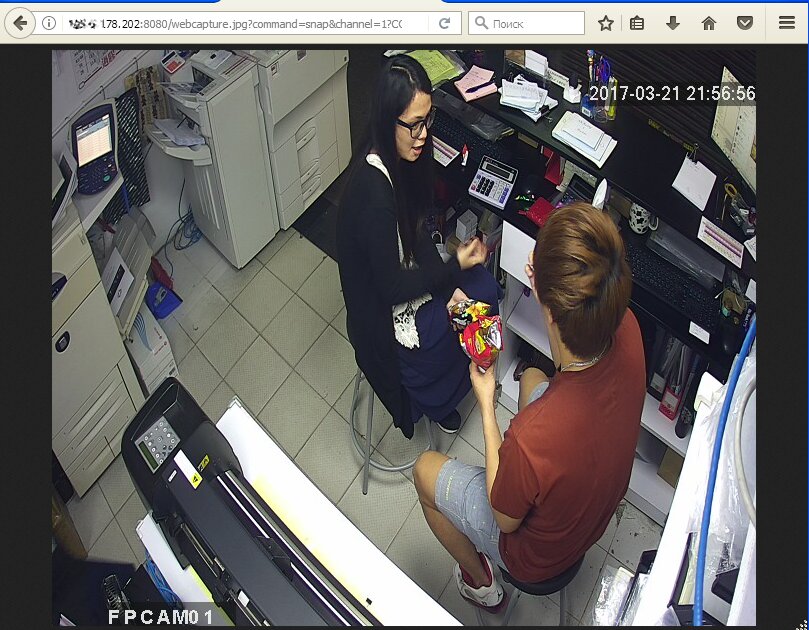
Video surveillance is mainly used for security, so don't expect funny pictures from the first hacked camera. You may be lucky enough to quickly find an HD broadcast from an elite brothel, but more often you will come across boring views of deserted warehouses and parking lots with VGA resolution. If there are people in the frame, they are mostly waiting in the lobby and eating in the cafe. It is much more interesting to watch the operators themselves and the work of all sorts of robots.

Real and formal observation
IP cameras and webcams are often confused, although they are fundamentally different devices. A network camera, or IP camera, is a self-contained surveillance tool. It is controlled via a web interface and transmits the video stream independently over the network. In fact, it is a microcomputer with its own Linux-based OS. The Ethernet (RJ-45) or Wi-Fi network interface allows direct connection to the IP camera. Previously, proprietary client applications were used for this, but most modern cameras are controlled via a browser from any device - even from a computer, even from a smartphone.
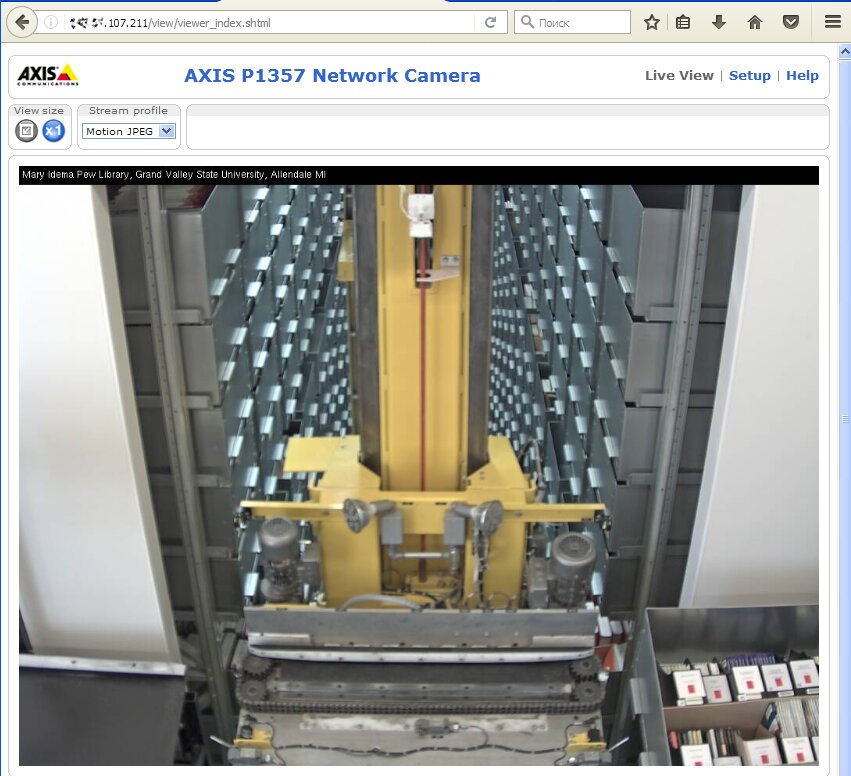
Robot in the library archive
A webcam is a passive device that is controlled locally from a computer (via USB) or laptop (if it is built-in) via the operating system driver. This driver can be of two different types: universal (pre-installed in the OS and suitable for many cameras from different manufacturers) and custom-written for a specific model. The hacker's task here is already different: not to connect to the webcam, but to intercept its video stream, which it broadcasts through the driver. The webcam doesn't have a separate IP address and built-in web server.
N-n-nada glasses?
Hacking surveillance cameras
Hacking IP cameras does not mean that someone is managing the computer from which the owner is watching their video stream. It's just that he doesn't watch it alone anymore. These are separate and fairly easy goals, but there are enough pitfalls on the way to them.

Chinese courtesy
Sometimes there are non-trivial solutions. For example, the Raspberry Pi is turned into a video surveillance server with nginx and video is broadcast over RTMP.

Raspberry Camera
By design, the IP camera is protected from intrusion by two secrets: its IP address and the account password. In practice, IP addresses can hardly be called a secret. They are easily detected at standard addresses, and the cameras respond equally to requests from search robots. For example, the following screenshot shows that the camera owner has disabled anonymous access to it and added CAPTCHA input to prevent automated attacks. However, you can use a direct link/index.htm, you can change them without authorization.
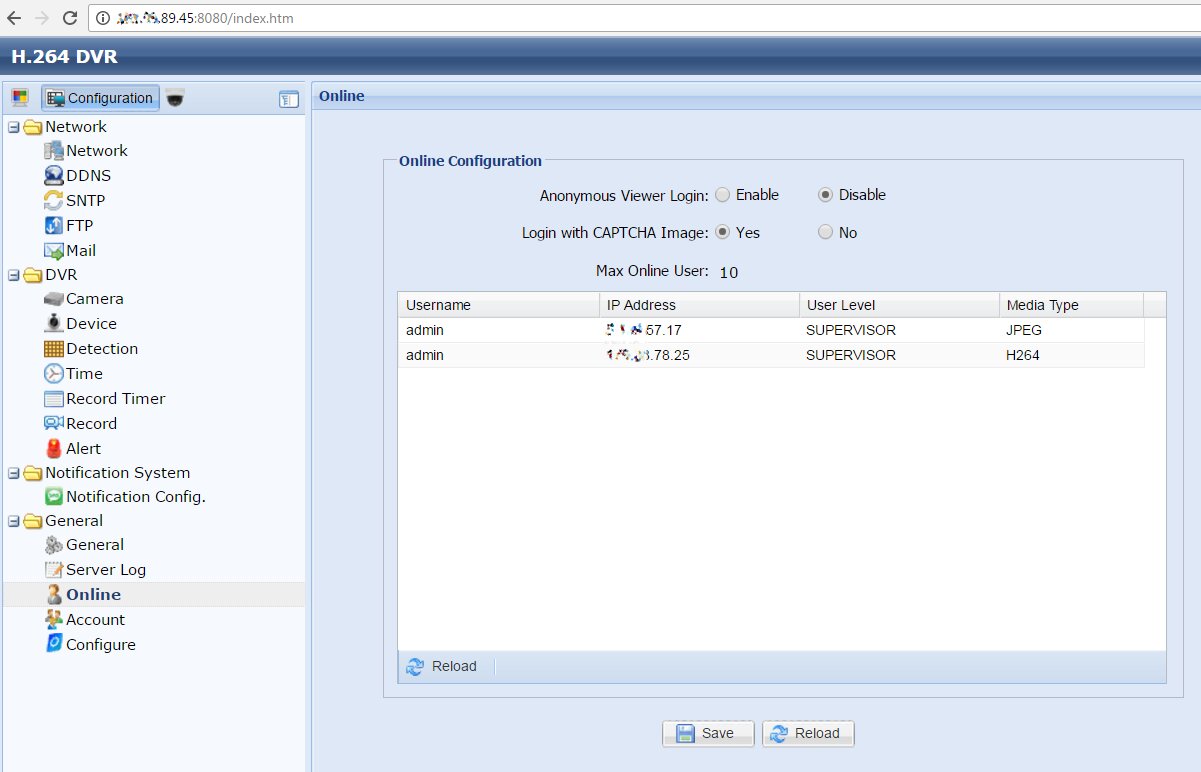
Getting access despite the settings
Vulnerable surveillance cameras can be found through Google or another search engine using advanced queries. For example:
Finding cameras via Google
It is much more convenient to search for them through Shodan. To begin with, you can limit yourself to a simple query netcam, and then go to more advanced ones: netcam city:Moscow, netcam country:RU, webcamxp geo:55.45,37.37, linux upnp avtechand others. Read more about using this search engine in the article "White hat for Shodan".
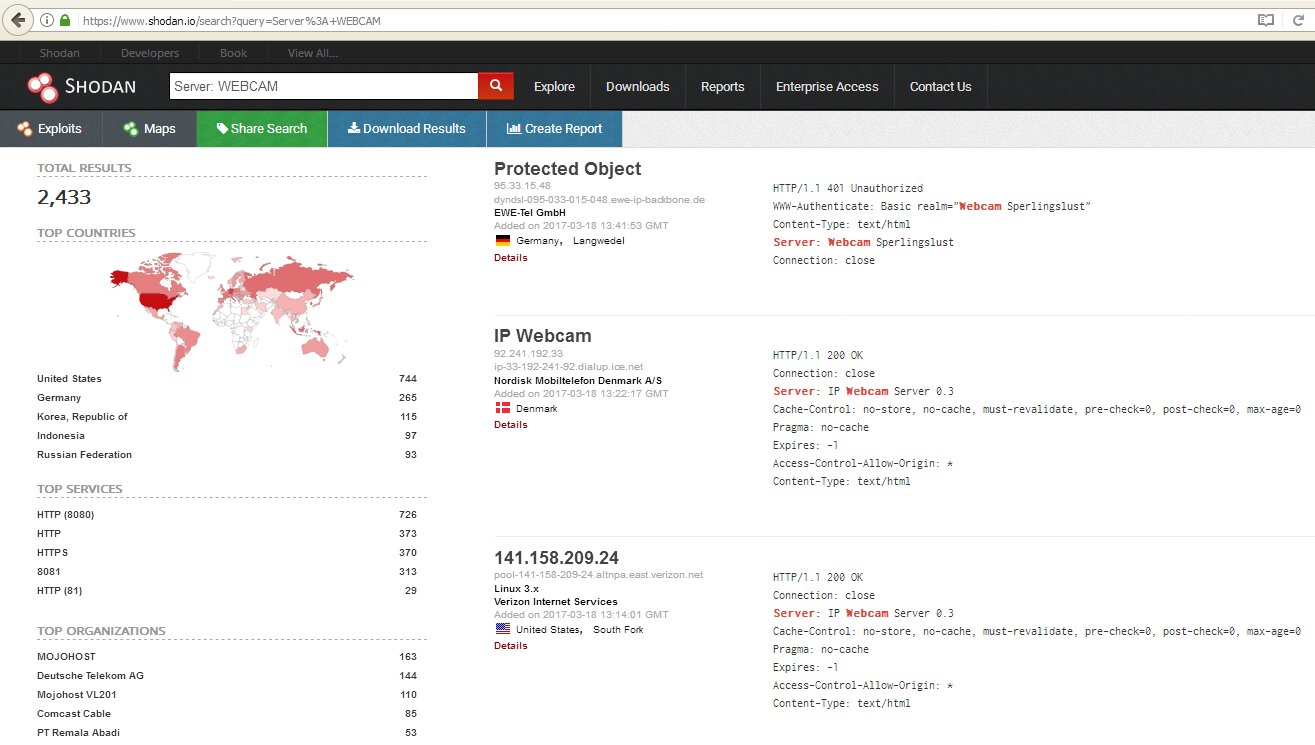
Looking for cameras in Shodan
Perfectly searches for cameras and Censys. The query language is a little more complex, but it's also easy to understand. For example, the query 80.http.get.body: "DVR Web Client" will show the cameras connected to the IP DVR, and metadata.manufacturer: "axis" it will find cameras manufactured by Axis. We also already wrote about how to work with Censys in the article "What can Censys do?".
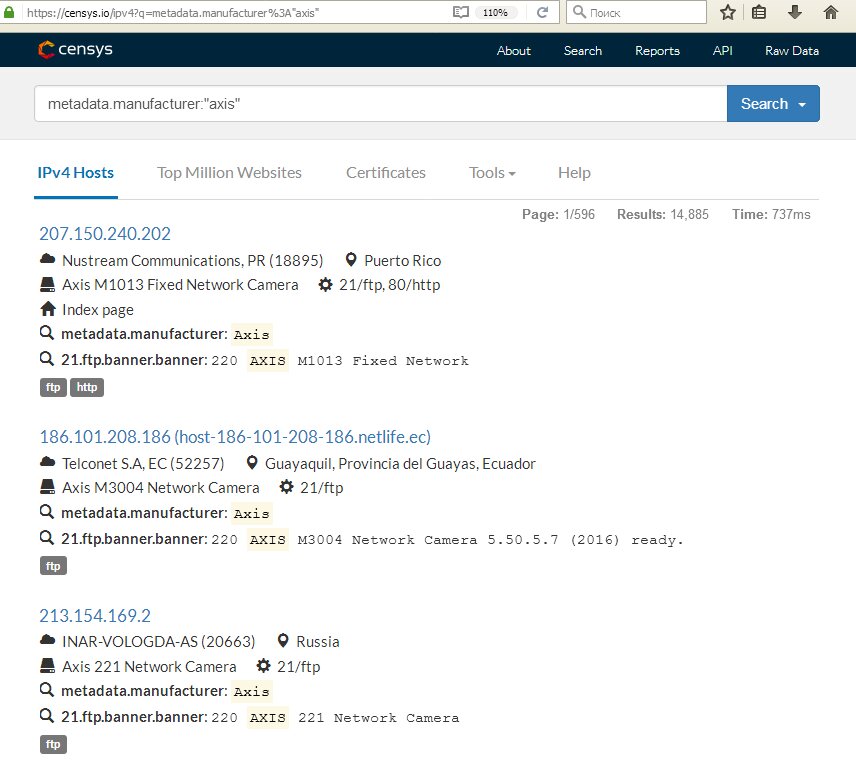
Looking for cameras in Censys
Another great Internet of Things search engine is ZoomEye. Cameras are located in it device:webcam или device:media device.
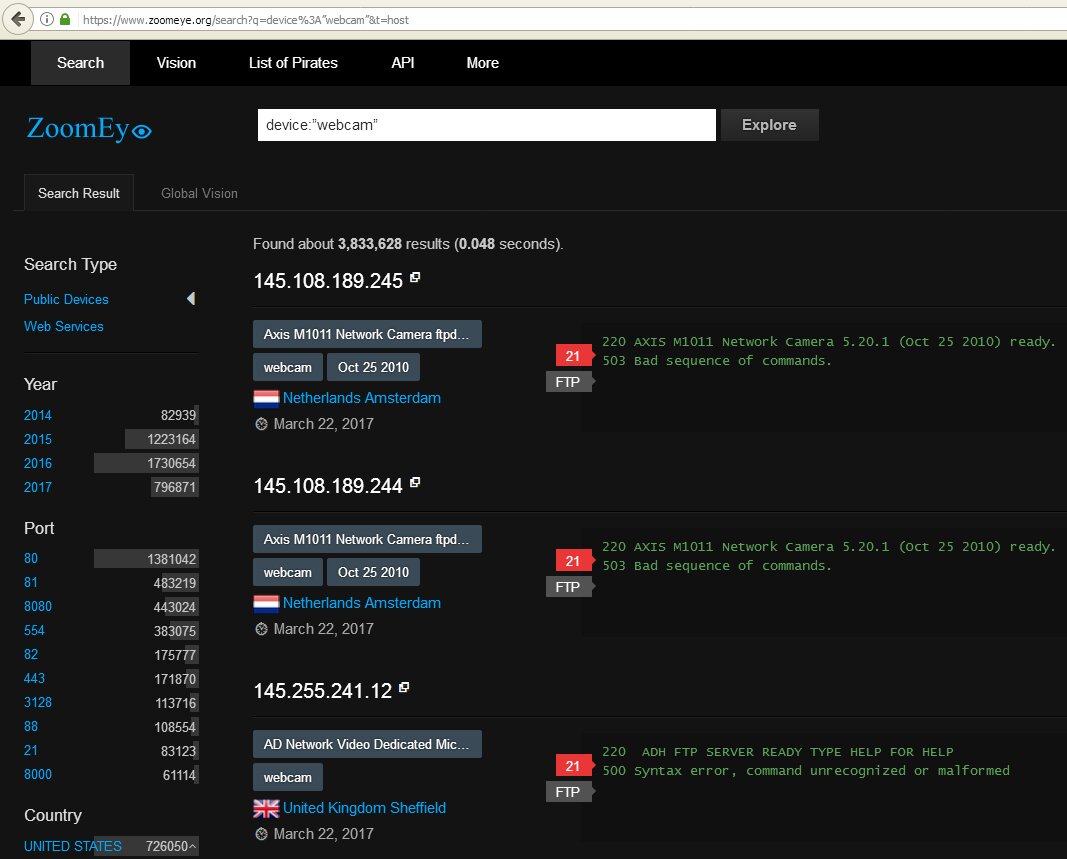
Looking for cameras in ZoomEye
You can also search in the old-fashioned way, simply scanning IP address ranges in search of a characteristic response from the camera. You can get a list of IP users in a particular city on this web service. There's also a port scanner in case you still don't have one of your own.
First of all, we are interested in ports 8000, 8080, and 8888, since they are often set by default. You can find out the default port number for a specific camera in its manual. The phone number is almost never changed. Naturally, other services can also be detected on any port, so the search results will have to be additionally filtered.

RTFM!
It is easy to find out the model of the detected camera: it is usually specified on the title page of the web interface and in its settings.
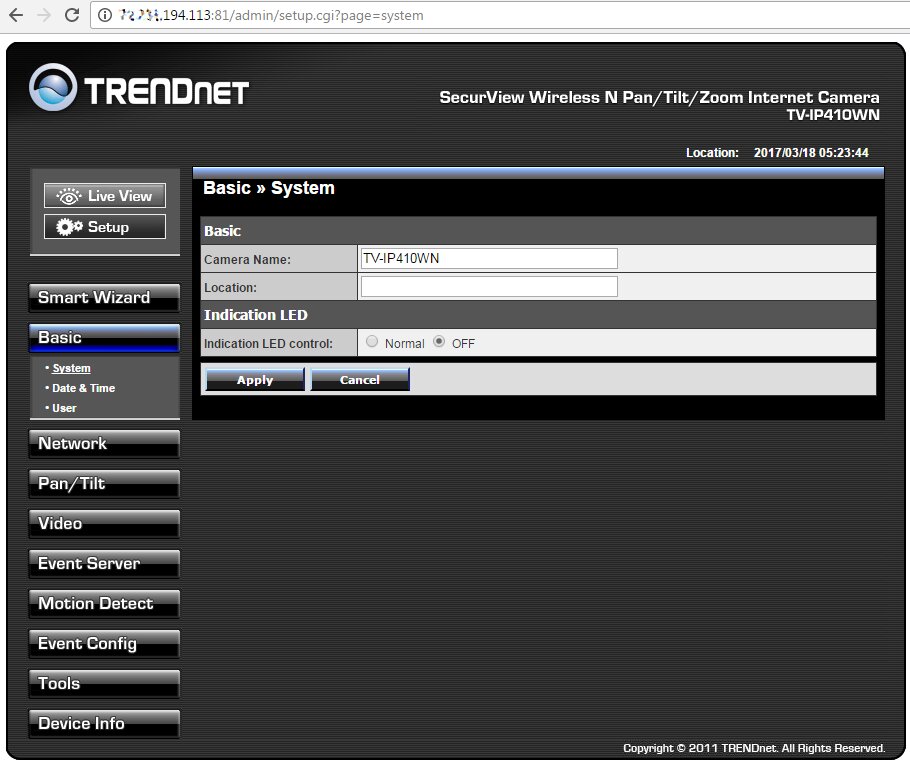
Finding out the camera model and setting it up
When I spoke at the beginning of the article about managing cameras through a "proprietary client application", I was referring to programs like iVMS 4xxx, which comes with Hikvision cameras. On the developer's website, you can read the Russian-language manual for the program and the cameras themselves. If you find such a camera, it is very likely that it will have a factory password, and the program will grant you full access to it.
With passwords to surveillance cameras, things are generally extremely fun. On some cameras, there is simply no password and no authorization at all. Others have a default password, which is easy to find in the camera manual. On the site is a list of the most common usernames and passwords installed on different camera models.

admin/admin, open up!
It often happens that the manufacturer left a service entrance for service centers in the camera firmware. It remains open even after the camera owner has changed the default password. You can no longer read it in the manual, but you can find it on thematic forums.
A huge problem is that many cameras use the same GoAhead web server. It has several known vulnerabilities that camera manufacturers are slow to patch.
GoAhead, in particular, is susceptible to stack overflow, which can be triggered by a simple HTTP GET request. The situation is further complicated by the fact that Chinese manufacturers modify GoAhead in their firmware, adding new holes.

Join in, my dear!
Today, more than a million IP cameras and IP video recorders from different manufacturers allow you to remotely access their settings without any authorization. A Python script that automates attacks on vulnerable devices has already been posted on GitHub. The problem was discovered in early 2017 when reversing DVR firmware manufactured by Dahua Technology. A little later it turned out that it affects more than a thousand models from different manufacturers. They simply replicated each other's mistakes. The author promised to give time for a fix and not disclose all the details yet, but he is ready to share them privately by email with all security specialists. If you have a CEH (Certified Ethical Hacker) certificate or similar - you can try it.
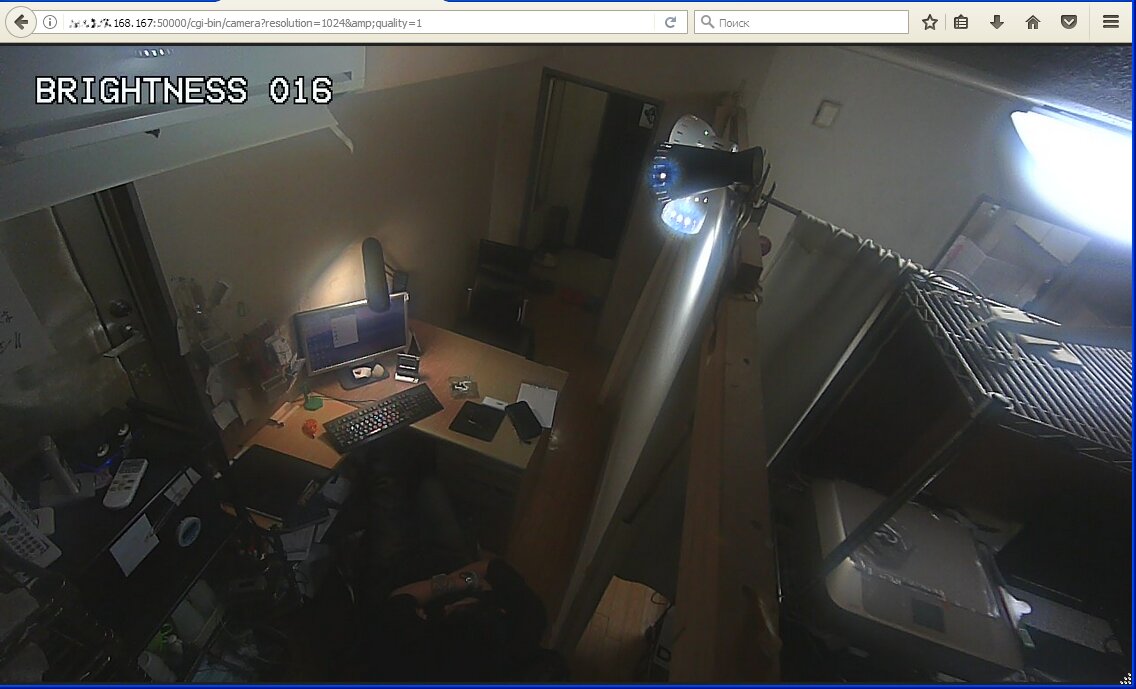
Let's add brightness!
In the code of other firmware versions, there are such blunders as conditional transition curves. Such a camera opens access if you enter the wrong password or simply press the "Cancel" button several times. During our research, I came across more than a dozen such cameras. So, if you are tired of sorting through default passwords, try clicking Cancel - there is a chance to suddenly get access.
Medium and high-end cameras are equipped with rotary mounts. After hacking this one, you can change the angle and fully explore everything around you. It's especially fun to play tug-of-war when someone else is trying to control the camera at the same time. In general, the attacker gets full control of the camera directly from his browser, just by contacting the desired address.
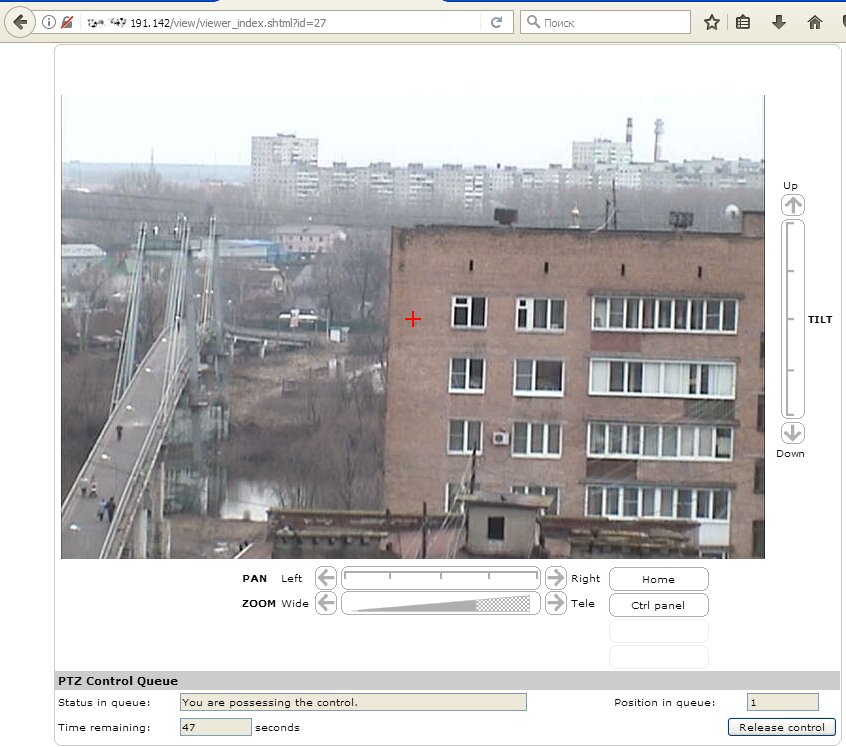
Managing the camera
When we talk about thousands of vulnerable cameras, we want to analyze at least one in more detail. I suggest you start with the popular manufacturer Foscam. Remember what I said about service entrances? So Foscam cameras and many others have them. In addition to the built-in admin account, the password for which is recommended to be set when the camera is turned on for the first time, there is another account - operator. Its default password is empty, and it is rare for anyone to guess to change it.
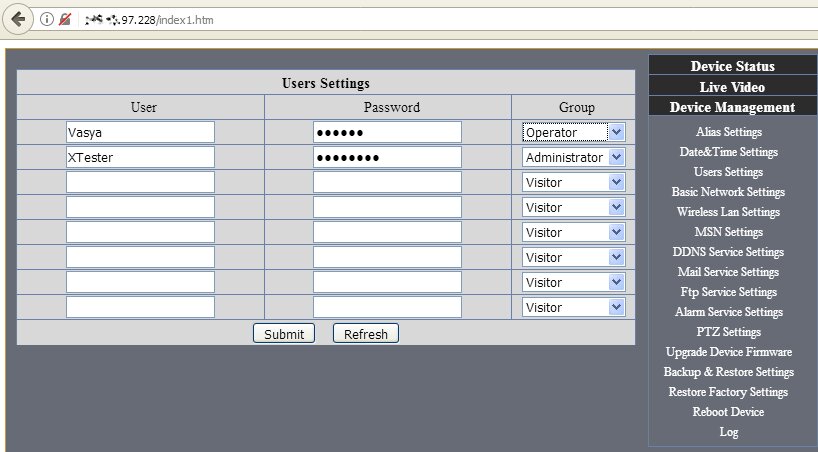
We log in as an operator and add new accounts
In addition, Foscam cameras have very recognizable addresses due to template registration. In general, it looks likexxxxxx.myfoscam.org:88, where the first two xxare Latin letters, and the next four are an ordinal number in decimal format.
If the camera is connected to an IP DVR, you can not only watch remotely in real time, but also view previous recordings.
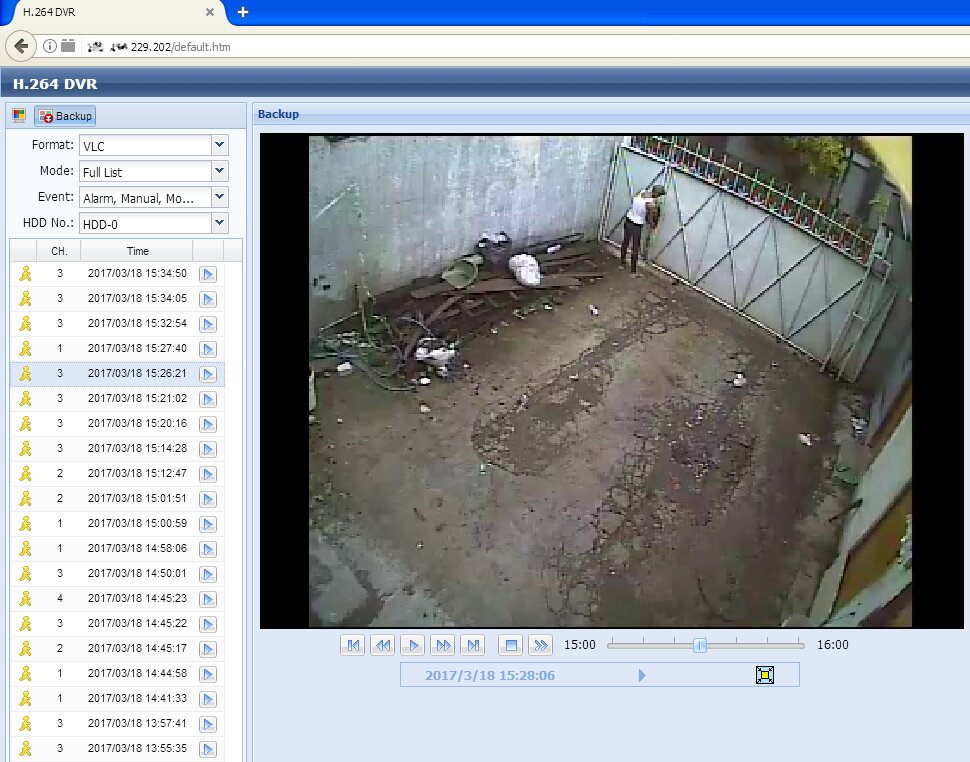
Looking at the record from the backup
How the motion detector works
Professional surveillance cameras are equipped with an additional sensor-a motion detector that works even in complete darkness thanks to an IR receiver. This is more interesting than the constantly on IR illumination, as it does not unmask the camera and allows it to conduct covert surveillance. People always glow in the near-IR range (at least when they're alive). As soon as the sensor detects movement, the controller starts recording. If the photocell indicates low light conditions, the backlight is additionally turned on.
Cheap cameras are simpler. They don't have a separate motion sensor, but instead use frame comparison from the webcam itself. If the picture is different from the previous one, then something has changed in the frame and you need to record it. If no movement is detected, the series of frames is simply deleted. This saves space, traffic, and time for later rewinding the video. Most motion detectors are configurable. You can set a trigger threshold to avoid logging any movement in front of the camera, and set up additional alerts.
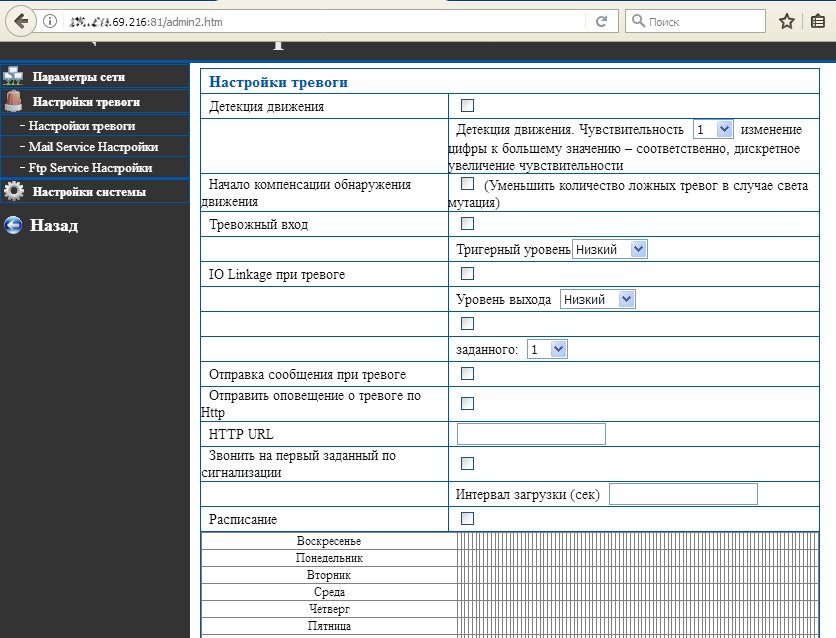
Setting up the camera's motion detector
The software motion detector is much inferior to the hardware one and often causes accidents. In the course of my research, I came across two cameras that continuously sent alerts and recorded gigabytes of "compromising material". All the alarms were false. The first camera was installed outside a warehouse. It was overgrown with cobwebs that shook in the wind and drove the motion detector crazy. The second camera was located in the office opposite the flashing lights of the router. In both cases, the trigger threshold was too low.
Hacking webcams
Web cameras that work through a universal driver are often called UVC-compatible (from USB Video Class - UVC). Hacking a UVC camera is easier because it uses a standard and well-documented protocol. However, in any case, to access the webcam, the attacker will first have to gain control of the computer to which it is connected.
Technically, web cameras on Windows computers of any version and bit depth can be accessed via the camera driver, DirectDraw filters, and VFW codecs. However, a novice hacker does not need to delve into all these details if he is not going to write an advanced backdoor. It is enough to take any "rat" (RAT - Remote Admin Tool) and slightly modify it. There are a lot of remote administration tools available today. In addition to select backdoors with VX Heaven, there are also quite legitimate utilities, such as Ammyy Admin, LiteManager, LuminosityLink, Team Viewer or Radmin.
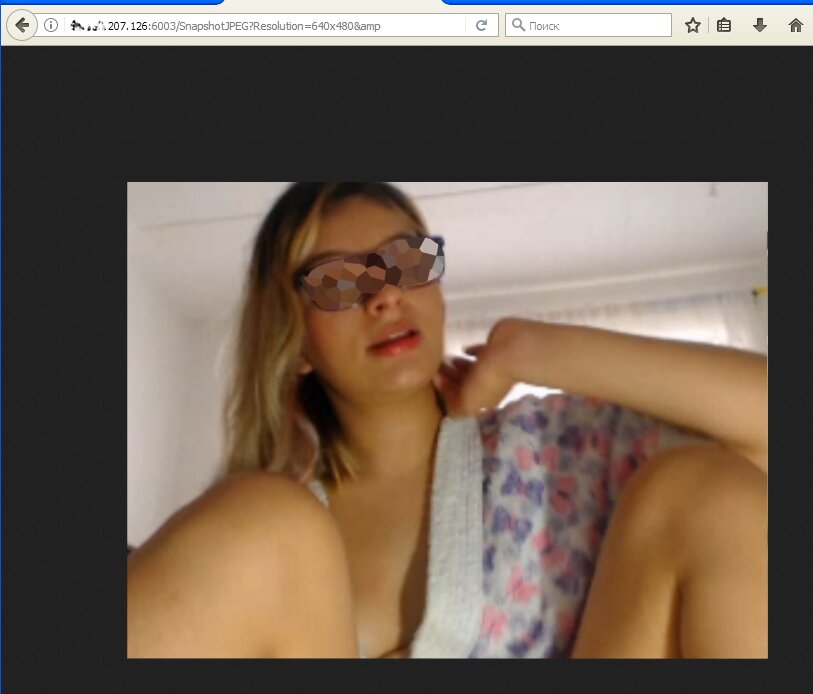
A girl who lives online
The code-modified rat is downloaded by the victim via a phishing link or crawls to her computer itself through the first hole found. For more information on how to automate this process, see the article "Gophish-a framework for phishing". By the way, be careful: most of the links to "camera hacking programs" are phishing themselves and may lead you to download malware.
For the average user, the webcam is inactive most of the time. Usually, the LED warns about its inclusion, but even with this notification, you can perform covert surveillance. As it turned out, the webcam activity indication can be turned off even if the power supply of the LED and CMOS matrix is physically interconnected. This has already been done with the iSight web cameras built into the MacBook. Researchers Broker and Chekoway from Johns Hopkins University wrote iSeeYou, which runs from a simple user and, exploiting the vulnerability of the Cypress controller, replaces its firmware. After the victim starts iSeeYou, the attacker gets the opportunity to turn on the camera without lighting its activity indicator.
Vulnerabilities are regularly found in other microcontrollers. Prevx specialist collected a whole collection of such exploits and showed examples of their use. Almost all the vulnerabilities found were related to 0day, but among them were long-known ones that manufacturers simply did not intend to eliminate.
There are more and more ways to deliver exploits, and it's getting harder to catch them. Antivirus programs often give up on modified PDF files, have pre-installed restrictions on checking large files, and cannot check encrypted malware components. Moreover, polymorphism or constant recompilation of the combat load has become the norm, so signature analysis has long faded into the background. Today it is extremely easy to implement a Trojan that opens remote access to a webcam. This is one of the most popular games among trolls and script kiddies.
Turning a webcam into a surveillance camera
Any webcam can be turned into a kind of IP camera if you install a video surveillance server on the device connected to it. On computers, many people use the old WebcamXP, slightly newer webcam 7, and similar programs.
For smartphones, there is a similar software - for example, Salient Eye. This program can save videos to cloud hosting, freeing up the local memory of your smartphone. However, there are enough holes in such programs and the OS itself, so hacking web cameras controlled by them is often no more difficult than IP cameras with leaky firmware.
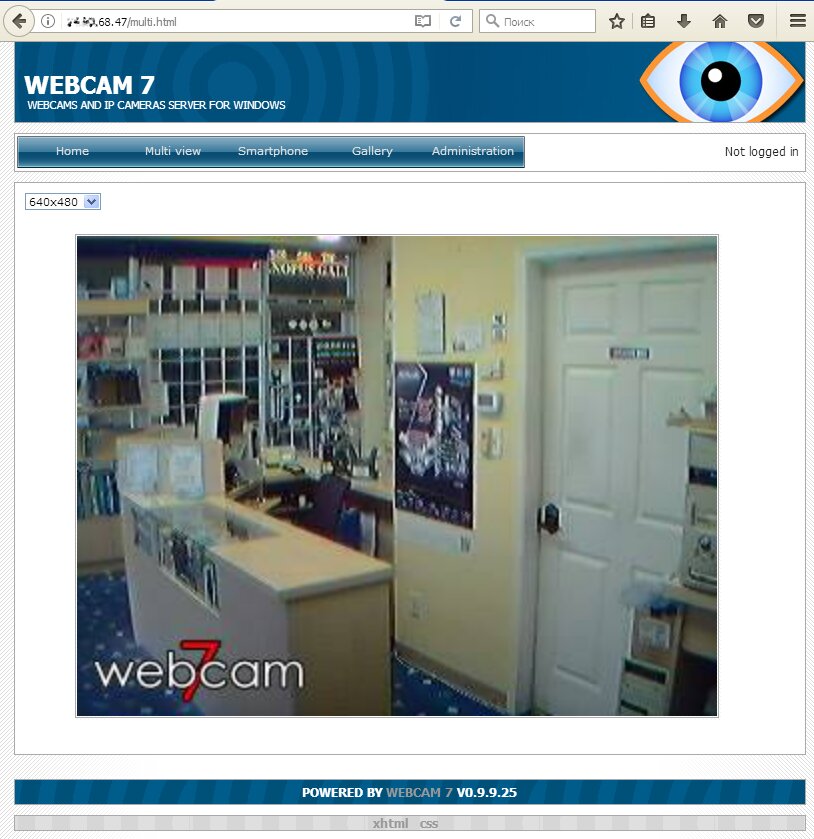
Webcam 7 shows videos without authorization
Smartphone as a means of surveillance
Recently, old smartphones and tablets are often adapted for home video surveillance. Most often, they are installed on Android Webcam Server, a simple application that broadcasts a video stream from the built-in camera to the Internet. It accepts requests on port 8080 and opens the control panel on a page with a telling name /remote.html. Once on it, you can change the camera settings and view the image directly in the browser window (with or without audio).
Usually, such smartphones show rather dull pictures. I don't think you're interested in looking at a sleeping dog or a car parked outside your house. However, you can use Android Webcam Server and similar applications differently. In addition to the rear camera, smartphones also have a front camera. Why don't we turn it on? Then we will see a different side of the smartphone owner's life.
Protection from spying
The first thing that comes to mind for most people after demonstrating easy hacking of cameras is to seal them with electrical tape. Owners of web cameras with a curtain believe that their problem of peeping does not concern them, and in vain. Eavesdropping is also possible, since the cameras have a microphone in addition to the lens.
Developers of antivirus and other software protection systems use confusion in terminology to promote their products. They frighten with statistics of hacking cameras (which is really impressive if you include IP cameras in it), and they themselves offer a solution for controlling access to webcams, and technically limited.
IP camera protection can be improved by simple means: updating the firmware, changing the password, port, and disabling default accounts, as well as enabling IP address filtering. However, this is not enough. Many firmware versions have unresolved errors that allow access without any authorization - for example, at the standard address of a web page from LiveView or the settings panel. When you find another leaky firmware, you just want to update it remotely!
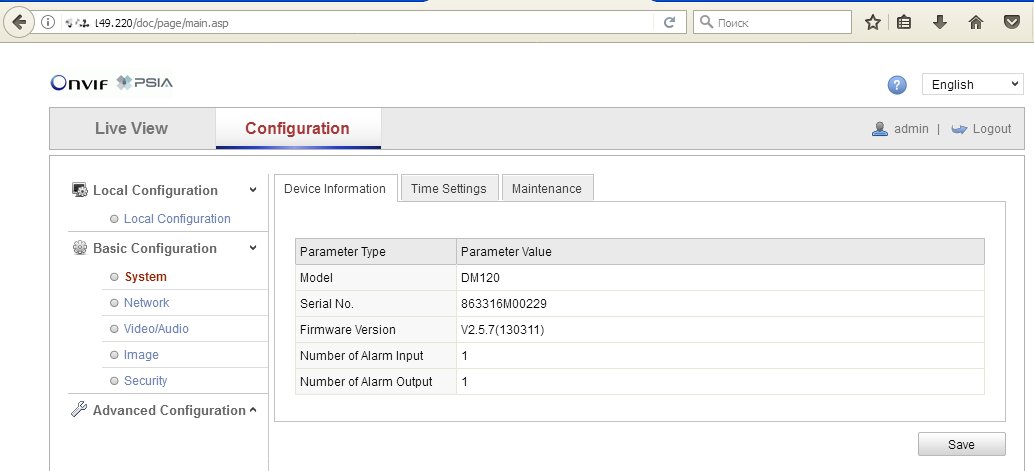
Help me update the vulnerable camera's firmware
Hacking a webcam is another matter entirely. This is always the tip of the iceberg. Usually, by the time an attacker has gained access to it, he has already managed to frolic on local disks, steal the accounts of all accounts, or make the computer part of a botnet.
Kaspersky Internet Security also prevents unauthorized access only to the webcam's video stream. It will not prevent a hacker from changing its settings or enabling the microphone. The list of models it protects is officially limited to Microsoft and Logitech webcams. Therefore, the "webcam protection" function should only be taken as an add-on.
Spying sites
A separate problem is attacks related to the implementation of camera access control in browsers. Many sites offer communication services using the camera, so requests for access to it and its built-in microphone pop up in the browser ten times a day. The special feature here is that the site can use a script that opens pop-under (an additional window in the background). Permissions of the parent window are passed to this child window. When you close the main page, the microphone stays on in the background.
In most browsers, permissions are stored permanently, so the next time you visit the site, you can be seen and heard without warning. You should check the access permissions to the webcam and its microphone for different sites more often. In Google Chrome, you can do this on the settings page chrome://settings/contentExceptions#media-stream. In older versions of Firefox , similar settings were set on the pageabout ermissions. In the new versions , they are set separately for each site when you click on the icon (i)on the left in the address bar. For more information, see the Mozilla documentation.
ermissions. In the new versions , they are set separately for each site when you click on the icon (i)on the left in the address bar. For more information, see the Mozilla documentation.
xakep.ru
Video surveillance is mainly used for security, so don't expect funny pictures from the first hacked camera. You may be lucky enough to quickly find an HD broadcast from an elite brothel, but more often you will come across boring views of deserted warehouses and parking lots with VGA resolution. If there are people in the frame, they are mostly waiting in the lobby and eating in the cafe. It is much more interesting to watch the operators themselves and the work of all sorts of robots.

Real and formal observation
IP cameras and webcams are often confused, although they are fundamentally different devices. A network camera, or IP camera, is a self-contained surveillance tool. It is controlled via a web interface and transmits the video stream independently over the network. In fact, it is a microcomputer with its own Linux-based OS. The Ethernet (RJ-45) or Wi-Fi network interface allows direct connection to the IP camera. Previously, proprietary client applications were used for this, but most modern cameras are controlled via a browser from any device - even from a computer, even from a smartphone.

Robot in the library archive
A webcam is a passive device that is controlled locally from a computer (via USB) or laptop (if it is built-in) via the operating system driver. This driver can be of two different types: universal (pre-installed in the OS and suitable for many cameras from different manufacturers) and custom-written for a specific model. The hacker's task here is already different: not to connect to the webcam, but to intercept its video stream, which it broadcasts through the driver. The webcam doesn't have a separate IP address and built-in web server.

N-n-nada glasses?
Hacking surveillance cameras
Hacking IP cameras does not mean that someone is managing the computer from which the owner is watching their video stream. It's just that he doesn't watch it alone anymore. These are separate and fairly easy goals, but there are enough pitfalls on the way to them.
First, remote access to the selected camera can only be supported through a specific browser. Give some people a fresh Chrome or Firefox, while others work only with the old IE. Secondly, the video stream is broadcast to the Internet in different formats. Somewhere you will need to install the VLC plugin to view it , other cameras will require Flash Player, and still others will not show anything without old Java version или собственного плагина.Spying through cameras can lead to administrative and criminal penalties. Usually a fine is imposed, but not everyone manages to get off easily. Matthew Anderson served a year and a half for hacking webcams using a Trojan. Repeated his feat was awarded four years.
Chinese courtesy
Sometimes there are non-trivial solutions. For example, the Raspberry Pi is turned into a video surveillance server with nginx and video is broadcast over RTMP.

Raspberry Camera
By design, the IP camera is protected from intrusion by two secrets: its IP address and the account password. In practice, IP addresses can hardly be called a secret. They are easily detected at standard addresses, and the cameras respond equally to requests from search robots. For example, the following screenshot shows that the camera owner has disabled anonymous access to it and added CAPTCHA input to prevent automated attacks. However, you can use a direct link/index.htm, you can change them without authorization.

Getting access despite the settings
Vulnerable surveillance cameras can be found through Google or another search engine using advanced queries. For example:
Code:
inurl:«wvhttp-01»
inurl:«viewerframe?mode=»
inurl:«videostream.cgi»
inurl:«webcapture»
inurl:«snap.jpg»
inurl:«snapshot.jpg»
inurl:«video.mjpg»
Finding cameras via Google
It is much more convenient to search for them through Shodan. To begin with, you can limit yourself to a simple query netcam, and then go to more advanced ones: netcam city:Moscow, netcam country:RU, webcamxp geo:55.45,37.37, linux upnp avtechand others. Read more about using this search engine in the article "White hat for Shodan".

Looking for cameras in Shodan
Perfectly searches for cameras and Censys. The query language is a little more complex, but it's also easy to understand. For example, the query 80.http.get.body: "DVR Web Client" will show the cameras connected to the IP DVR, and metadata.manufacturer: "axis" it will find cameras manufactured by Axis. We also already wrote about how to work with Censys in the article "What can Censys do?".

Looking for cameras in Censys
Another great Internet of Things search engine is ZoomEye. Cameras are located in it device:webcam или device:media device.

Looking for cameras in ZoomEye
You can also search in the old-fashioned way, simply scanning IP address ranges in search of a characteristic response from the camera. You can get a list of IP users in a particular city on this web service. There's also a port scanner in case you still don't have one of your own.
First of all, we are interested in ports 8000, 8080, and 8888, since they are often set by default. You can find out the default port number for a specific camera in its manual. The phone number is almost never changed. Naturally, other services can also be detected on any port, so the search results will have to be additionally filtered.

RTFM!
It is easy to find out the model of the detected camera: it is usually specified on the title page of the web interface and in its settings.

Finding out the camera model and setting it up
When I spoke at the beginning of the article about managing cameras through a "proprietary client application", I was referring to programs like iVMS 4xxx, which comes with Hikvision cameras. On the developer's website, you can read the Russian-language manual for the program and the cameras themselves. If you find such a camera, it is very likely that it will have a factory password, and the program will grant you full access to it.
With passwords to surveillance cameras, things are generally extremely fun. On some cameras, there is simply no password and no authorization at all. Others have a default password, which is easy to find in the camera manual. On the site is a list of the most common usernames and passwords installed on different camera models.
admin/admin, open up!
It often happens that the manufacturer left a service entrance for service centers in the camera firmware. It remains open even after the camera owner has changed the default password. You can no longer read it in the manual, but you can find it on thematic forums.
A huge problem is that many cameras use the same GoAhead web server. It has several known vulnerabilities that camera manufacturers are slow to patch.
GoAhead, in particular, is susceptible to stack overflow, which can be triggered by a simple HTTP GET request. The situation is further complicated by the fact that Chinese manufacturers modify GoAhead in their firmware, adding new holes.
Join in, my dear!
Today, more than a million IP cameras and IP video recorders from different manufacturers allow you to remotely access their settings without any authorization. A Python script that automates attacks on vulnerable devices has already been posted on GitHub. The problem was discovered in early 2017 when reversing DVR firmware manufactured by Dahua Technology. A little later it turned out that it affects more than a thousand models from different manufacturers. They simply replicated each other's mistakes. The author promised to give time for a fix and not disclose all the details yet, but he is ready to share them privately by email with all security specialists. If you have a CEH (Certified Ethical Hacker) certificate or similar - you can try it.

Let's add brightness!
In the code of other firmware versions, there are such blunders as conditional transition curves. Such a camera opens access if you enter the wrong password or simply press the "Cancel" button several times. During our research, I came across more than a dozen such cameras. So, if you are tired of sorting through default passwords, try clicking Cancel - there is a chance to suddenly get access.
Medium and high-end cameras are equipped with rotary mounts. After hacking this one, you can change the angle and fully explore everything around you. It's especially fun to play tug-of-war when someone else is trying to control the camera at the same time. In general, the attacker gets full control of the camera directly from his browser, just by contacting the desired address.

Managing the camera
When we talk about thousands of vulnerable cameras, we want to analyze at least one in more detail. I suggest you start with the popular manufacturer Foscam. Remember what I said about service entrances? So Foscam cameras and many others have them. In addition to the built-in admin account, the password for which is recommended to be set when the camera is turned on for the first time, there is another account - operator. Its default password is empty, and it is rare for anyone to guess to change it.

We log in as an operator and add new accounts
In addition, Foscam cameras have very recognizable addresses due to template registration. In general, it looks likexxxxxx.myfoscam.org:88, where the first two xxare Latin letters, and the next four are an ordinal number in decimal format.
If the camera is connected to an IP DVR, you can not only watch remotely in real time, but also view previous recordings.

Looking at the record from the backup
How the motion detector works
Professional surveillance cameras are equipped with an additional sensor-a motion detector that works even in complete darkness thanks to an IR receiver. This is more interesting than the constantly on IR illumination, as it does not unmask the camera and allows it to conduct covert surveillance. People always glow in the near-IR range (at least when they're alive). As soon as the sensor detects movement, the controller starts recording. If the photocell indicates low light conditions, the backlight is additionally turned on.
Cheap cameras are simpler. They don't have a separate motion sensor, but instead use frame comparison from the webcam itself. If the picture is different from the previous one, then something has changed in the frame and you need to record it. If no movement is detected, the series of frames is simply deleted. This saves space, traffic, and time for later rewinding the video. Most motion detectors are configurable. You can set a trigger threshold to avoid logging any movement in front of the camera, and set up additional alerts.

Setting up the camera's motion detector
The software motion detector is much inferior to the hardware one and often causes accidents. In the course of my research, I came across two cameras that continuously sent alerts and recorded gigabytes of "compromising material". All the alarms were false. The first camera was installed outside a warehouse. It was overgrown with cobwebs that shook in the wind and drove the motion detector crazy. The second camera was located in the office opposite the flashing lights of the router. In both cases, the trigger threshold was too low.
Hacking webcams
Web cameras that work through a universal driver are often called UVC-compatible (from USB Video Class - UVC). Hacking a UVC camera is easier because it uses a standard and well-documented protocol. However, in any case, to access the webcam, the attacker will first have to gain control of the computer to which it is connected.
Technically, web cameras on Windows computers of any version and bit depth can be accessed via the camera driver, DirectDraw filters, and VFW codecs. However, a novice hacker does not need to delve into all these details if he is not going to write an advanced backdoor. It is enough to take any "rat" (RAT - Remote Admin Tool) and slightly modify it. There are a lot of remote administration tools available today. In addition to select backdoors with VX Heaven, there are also quite legitimate utilities, such as Ammyy Admin, LiteManager, LuminosityLink, Team Viewer or Radmin.

A girl who lives online
The code-modified rat is downloaded by the victim via a phishing link or crawls to her computer itself through the first hole found. For more information on how to automate this process, see the article "Gophish-a framework for phishing". By the way, be careful: most of the links to "camera hacking programs" are phishing themselves and may lead you to download malware.
For the average user, the webcam is inactive most of the time. Usually, the LED warns about its inclusion, but even with this notification, you can perform covert surveillance. As it turned out, the webcam activity indication can be turned off even if the power supply of the LED and CMOS matrix is physically interconnected. This has already been done with the iSight web cameras built into the MacBook. Researchers Broker and Chekoway from Johns Hopkins University wrote iSeeYou, which runs from a simple user and, exploiting the vulnerability of the Cypress controller, replaces its firmware. After the victim starts iSeeYou, the attacker gets the opportunity to turn on the camera without lighting its activity indicator.
Vulnerabilities are regularly found in other microcontrollers. Prevx specialist collected a whole collection of such exploits and showed examples of their use. Almost all the vulnerabilities found were related to 0day, but among them were long-known ones that manufacturers simply did not intend to eliminate.
There are more and more ways to deliver exploits, and it's getting harder to catch them. Antivirus programs often give up on modified PDF files, have pre-installed restrictions on checking large files, and cannot check encrypted malware components. Moreover, polymorphism or constant recompilation of the combat load has become the norm, so signature analysis has long faded into the background. Today it is extremely easy to implement a Trojan that opens remote access to a webcam. This is one of the most popular games among trolls and script kiddies.
Turning a webcam into a surveillance camera
Any webcam can be turned into a kind of IP camera if you install a video surveillance server on the device connected to it. On computers, many people use the old WebcamXP, slightly newer webcam 7, and similar programs.
For smartphones, there is a similar software - for example, Salient Eye. This program can save videos to cloud hosting, freeing up the local memory of your smartphone. However, there are enough holes in such programs and the OS itself, so hacking web cameras controlled by them is often no more difficult than IP cameras with leaky firmware.

Webcam 7 shows videos without authorization
Smartphone as a means of surveillance
Recently, old smartphones and tablets are often adapted for home video surveillance. Most often, they are installed on Android Webcam Server, a simple application that broadcasts a video stream from the built-in camera to the Internet. It accepts requests on port 8080 and opens the control panel on a page with a telling name /remote.html. Once on it, you can change the camera settings and view the image directly in the browser window (with or without audio).
Usually, such smartphones show rather dull pictures. I don't think you're interested in looking at a sleeping dog or a car parked outside your house. However, you can use Android Webcam Server and similar applications differently. In addition to the rear camera, smartphones also have a front camera. Why don't we turn it on? Then we will see a different side of the smartphone owner's life.

Protection from spying
The first thing that comes to mind for most people after demonstrating easy hacking of cameras is to seal them with electrical tape. Owners of web cameras with a curtain believe that their problem of peeping does not concern them, and in vain. Eavesdropping is also possible, since the cameras have a microphone in addition to the lens.
Developers of antivirus and other software protection systems use confusion in terminology to promote their products. They frighten with statistics of hacking cameras (which is really impressive if you include IP cameras in it), and they themselves offer a solution for controlling access to webcams, and technically limited.
IP camera protection can be improved by simple means: updating the firmware, changing the password, port, and disabling default accounts, as well as enabling IP address filtering. However, this is not enough. Many firmware versions have unresolved errors that allow access without any authorization - for example, at the standard address of a web page from LiveView or the settings panel. When you find another leaky firmware, you just want to update it remotely!

Help me update the vulnerable camera's firmware
Hacking a webcam is another matter entirely. This is always the tip of the iceberg. Usually, by the time an attacker has gained access to it, he has already managed to frolic on local disks, steal the accounts of all accounts, or make the computer part of a botnet.
Kaspersky Internet Security also prevents unauthorized access only to the webcam's video stream. It will not prevent a hacker from changing its settings or enabling the microphone. The list of models it protects is officially limited to Microsoft and Logitech webcams. Therefore, the "webcam protection" function should only be taken as an add-on.
Spying sites
A separate problem is attacks related to the implementation of camera access control in browsers. Many sites offer communication services using the camera, so requests for access to it and its built-in microphone pop up in the browser ten times a day. The special feature here is that the site can use a script that opens pop-under (an additional window in the background). Permissions of the parent window are passed to this child window. When you close the main page, the microphone stays on in the background.
In most browsers, permissions are stored permanently, so the next time you visit the site, you can be seen and heard without warning. You should check the access permissions to the webcam and its microphone for different sites more often. In Google Chrome, you can do this on the settings page chrome://settings/contentExceptions#media-stream. In older versions of Firefox , similar settings were set on the pageabout
xakep.ru
