Mutt
Professional
- Messages
- 1,458
- Reaction score
- 1,262
- Points
- 113
Approximately 90% of all mobile phones in the world can be opened by hackers, according to a study by the Russian company Positive Technologies, which deals with the security of cellular operators' systems. Listening to conversations, intercepting SMS messages, gaining access to mobile banking and even instant messengers allows a little-known vulnerability in the global telephone infrastructure - the system of SS7 signaling protocols, through which service commands of cellular networks are transmitted. In 2013, former CIA and US National Security Agency employee Edward Snowden provided a document from the National Security Agency archives about a special program based on SS7, which makes it possible to spy on any subscriber. In April 2016, the "hole" in SS7 was successfully used for "experimental wiretapping" of the American congressman. Probably, an information security specialist at one of the Russian cyber defense companies said that intelligence services can conduct surveillance through SORM (wiretapping equipment that FSB operatives use by court order) or spyware on the phone. But it is possible, he said, that the wiretapping was carried out through a vulnerability in mobile communications, which almost no one knows about - with the help of a "hole" in the SS7 protocol system used by telephone companies to transmit service commands. Thanks to this vulnerability, after a simple hack, you can intercept and listen to calls, track the location of the subscriber, read and even rewrite SMS.
Almost any owner of a telephone can be under attack - a politician, human rights activist, journalist, businessman, wife of a jealous husband, husband of a jealous wife; the other seven and a half billion mobile subscribers. Hackers can attack any phones - old push-button phones, smartphones, and devices based on iOS or Android.
About 90% of the world's mobile operators are not protected from attacks via SS7; SMS messages of 89% of subscribers can be intercepted; 58% of subscribers can be tracked; conversations of half of the subscribers can be listened to. This is stated in the report of the Russian company Positive Technologies, which investigated the security systems of the world's largest mobile operators.
What is SS7
SS7 vulnerability has been ignored for over 30 years.
SS7 development began in the 1970s. At that time, radio amateurs were fond of designing home-made devices, with the help of which it was possible to simulate the transmission of signals between telephone exchanges ("inter-office signaling") and send the necessary commands to them. Such devices, known as "blue boxes", allowed calls to be made almost free of charge to any destination, paying for the calls as local. For example, Apple creators Steve Jobs and Steven Wozniak also assembled blue boxes in the garage.
To combat fraudsters, telephone companies have separated subscriber (voice) and service (technical commands) traffic. This is how SS7 appeared, a system of signaling protocols for exchanging information and routing calls (which number calls, whom, from where, and so on). It can be compared to the subway system: SS7 are service tunnels for workers, not the ones used by trains.
SS7 began operating in the early 1980s and brought together telephone operators around the world. In Russia, the USA, Asia, Europe, the protocols are called differently, they differ slightly, but they are compatible with each other; in general, the system resembles the Internet in its structure. In Russia SS7 is called OKS-7 (common signaling channel No. 7), in the USA - CCS7, in Germany - N7, in the UK - CCIS7; common name - SS7.
In the early 2000s, an add-on to SS7 was developed - the Sigtran software, which made it possible to transmit messages and commands over IP networks: SS7 network components became available on public networks, some of them can be connected via the Internet. New and innovative software continued to run on the old system, which was not protected in any way; moreover, it has now turned out to be even easier to "insert" into this system.
Public discussion of the "hole" in SS7 began in 2008. At the Chaos Computer Club hacker conference, German information security researcher Tobias Engel showed the audience how to spy on mobile subscribers based on penetrating SS7. The governments and intelligence agencies apparently knew about the vulnerability even earlier. In a 2007 book by telecom experts Thomas Porter and Michael Goof, "How to Bypass VoIP Security", it was indicated that the US presidential administration was seriously concerned about the high threat level of SS7-based attacks. The possibility of attacks through the vulnerability in SS7 has been discussed in other American documents since 1998. Mobile operators could not be unaware of the vulnerability.
In 2013, a former CIA and US National Security Agency employee, Edward Snowden, handed over archives to The Guardian and The Washington Post, confirming that the US and UK intelligence agencies themselves can spy on anyone on the planet (and use this opportunity). He explained his actions by saying that "he does not want to live in a world where everything that I do and say is recorded."
In the same year, The Washington Post reported that the NSA used attacks on SS7 as one of its methods of surveillance. And in 2014, the journalists of the publication reported about special programs for surveillance based on SS7 - and that using SS7 hackers can "determine the location of a subscriber anywhere in the world, listen to conversations in real time or record encrypted calls and text messages for further decryption".
It was only after publications in The Washington Post that ordinary citizens learned about the vulnerability.
Nevertheless, almost three years after the publication of the first materials based on the Snowden archives, nothing seems to have changed in the security system of mobile networks. Mobile operators around the world generally refuse to acknowledge the problem. Many "white hackers" (they hack companies by order of the companies themselves) are sure that SS7 was created and continues to exist in its former form, including due to the fact that it is convenient to use it for surveillance and wiretapping. “For years, intelligence agencies have known and kept silent about vulnerabilities in communication networks that make citizens vulnerable to hackers. Why? They also use them, ”the Daily Beast claimed.
At the end of April 2020, Wired magazine called the SS7 vulnerability "critical."

Information Security Specialist Tobias Engel
How attacks happen
When the small meeting on information security comes to an end, Dmitry Kurbatov from Positive Technologies instructs the audience: “SMS is only for congratulations, secret conversations are in the field. The constitution guarantees the right to privacy of correspondence, but one should not rely on it. "
At work, Kurbatov daily, with the permission of Russian mobile operators, tries to hack them.
“Listening to [citizens] through SS7 is a very dusty way, you leave no traces, you can act from anywhere,” says Kurbatov. "You can sit in South America and listen to a person in Germany."
Access to hacking and wiretapping is opened after connecting to the SS7 system - this is the most difficult part of the whole hacking process.
In the early years, select commercial and government telephone companies had access to SS7. In 2020, it is impossible to count the number of legal connections to SS7: these are mobile operators, virtual mobile operators, and entertainment content providers. These companies employ hundreds of thousands of people; among them may be disloyal employees with the necessary skills.
In 2014, Kurbatov and his colleague Sergei Puzankov tested how easy it is to find an operator willing to connect strangers to SS7. Talking to mobile operators in South America and Central Asia, they pretended to be up-and-coming value-added content providers who need to connect to SS7 to "send subscribers the best weather forecasts." Many operators agreed to give them access officially, while others offered a connection for four thousand dollars. According to Kurbatov, having acquaintances in any of the telecom operators, it is very easy to get access to SS7.
Wiretapping and surveillance seem to be the specialization of security officials, extremely expensive and difficult. However, due to the insecurity of SS7, privacy information can be obtained by any average hacker. No sophisticated equipment is required to attack subscribers. “You don't need to be a genius or an intelligence service to do all this,” Kurbatov says. - We ourselves wrote the software package, supplementing the downloaded from the Internet. The entry threshold is low. "
Having done the main thing, that is, having hooked up to SS7, the cracker starts working “according to the targets” - that is, according to the subscribers he is going to monitor. First, using the appropriate software, he learns the IMSI number - a special identifier that is assigned to each mobile subscriber (contains the country code, operator code and internal unique SIM card number). At the same time, it receives the MSC / VLR parameters (call and location switch), thanks to which the subscriber is in the network.
The hacker will need all this in order to deceive the subscriber's "home" network and transfer it to his own - a fake one. For a "home" network, it will look as if the subscriber ("target") has roamed; the subscriber himself will never know about it. The fake network will send a command to the operator that now it serves the subscriber itself (that is, the operator will receive a signal that his subscriber is in the service area of another mobile operator). After that - with the help of special software - the hacker will be able to intercept SMS, listen to calls, track the location of the "target".
Kurbatov says this access is less used for surveillance; more often - to steal money from mobile wallets and SMS-banking: this is usually little money, but criminal groups take over. They operate in a distributed manner: those who invented the scheme are in one country, programmers in another; most often come across those who work "on the ground" and are engaged in transfers and cashing stolen money.
In the "deep internet", which can be accessed through Tor, it is easy to find offers of surveillance: “You want to follow your girlfriend? Kidalov is gone, the first day of surveillance is free ”; “Making a breakthrough, determining the location. And other useful services. " They also sell programs that allow you to attack SS7. But even on the regular open Internet there are dozens of sites offering to order a printout of SMS and calls. One of them says: “Do you want to be confident in a person? Would you like to make a mistake? Our service was created for you! " However, judging by the reviews, these sites are fraudulent; they stop responding to "customers" when they receive the first installment. One information security expert questioned whether surveillance sites could openly operate on the Internet.
In addition to intercepting calls and messages using SS7 attacks, a hacker can disable the phone: the device shows that it is receiving a signal, but it cannot be reached. Such attacks can harm businessmen during negotiations; journalists contacting sources; they can also be used during armed conflicts.
Hacks
In April 2020, German researcher of mobile networks Carsten Nohl, as part of an experiment on the CBS television channel, hacked and listened to the conversations of the American Congressman Ted Lew. The cracker only knew the politician's mobile phone number. The hacker used a vulnerability in SS7 to attack. In addition to wiretapping and recording all conversations, he was able to track the movements of the congressman - despite the fact that the GPS was turned off in the smartphone.
The congressman was shocked. After the experiment, he admitted to reporters that in 2015, US President Barack Obama called him on his personal phone. “We discussed a number of issues with him,” he said. - If the hackers listened to us, they would know the content of this conversation. All of this is causing great concern. "He demanded that Congress investigate and secure mobile phone users." People who knew about this gap should be fired, "he said. - You cannot expose 300 million Americans, the entire nation, to the risk of interception of telephone conversations just because this vulnerability is known and can be useful to the special services. This is unacceptable ".
Through SS7, apparently, politicians were seriously tapped more than once.
In February 2014, an audio recording of a telephone conversation was posted on YouTube, in which US Deputy Secretary of State Victoria Nuland and US Ambassador to Kiev Jeffrey Payet allegedly participated. "Diplomats" discussed Ukrainian politicians, "Nuland" during the conversation said, in particular, that it does not consider it a "good idea" to include Vitali Klitschko in the local government - and proposed its candidates. Dmitry Rogozin's assistant Dmitry Loskutov was one of the first to post the recording of the conversation on Twitter; he later claimed to have stumbled upon the link by accident. In the same year, an audio recording of an alleged conversation between Ukrainian politicians Yulia Tymoshenko and Nestor Shufrich appeared on YouTube.
At the end of May 2020, the National Commission for State Regulation in the Sphere of Communications and Informatization of Ukraine (NCCIR) published the results of the verification of information that calls from some subscribers of the Ukrainian MTS pass through Russian switches. The report indicated that the hackers, using the vulnerability, switched subscribers of MTS-Ukraine to a server presumably belonging to the Russian subsidiary of Tele2 - Rostov Cellular Communications. A Tele2 spokesman denied this.
In Russia, to wiretap calls and intercept correspondence, special services can use SORM - a system of technical means to ensure operational search activities. It has been around since the late 1980s and has been updated several times. According to Russian law, the special services have the right to activate the system only by a court decision. At the same time, in 2012, the Supreme Court of Russia recognized the right of the special services to wiretap opposition members only on the grounds that they were engaged in protest activities. In the investigation of the Russian Forbes, it was indicated that the FSB officer is not obliged to show the decision to wiretap to anyone - telecom operators have no right to know whose negotiations or mail are being intercepted by the special services.
However, with the help of SORM, special services can only listen to subscribers of Russian operators - citizens of the Russian Federation who have left for other countries, it will not be possible to track them with the help of SORM. But this allows you to make the SS7 vulnerability.
Experiment
An SS7 burglar, Sergei Puzankov, is experienced sitting at a table in the corner. There are two monitors in front of him. One has Wireshark open, in which it monitors SS7 traffic. The second is a proprietary program for testing mobile operators, that is, for legal hacking.
Dmitry Kurbatov is standing nearby. “We finished this software to create attacks, attackers can do the same,” he says and promises to show how easy it is to intercept calls and SMS. They refuse to conduct an experiment with wiretapping of Russian politicians, similar to that organized by the American television channel CBS.
At the request of Sergei Puzankov, I call his "experimental" number, registered in the network of one of the Russian mobile operators. The melody of a mobile phone lying on the table is heard; we talk with Puzankov for a few seconds. He nods, opens the program, writes a few lines, a phone number, IMSI into the hacking software - and thus transfers the "hacked phone" to a fake network. Sergey asks to call again. The "tracked" phone is silent, but another one, lying on the table nearby, rings. “This is how we redirected the call,” he says. “And they could just redirect the call so as to record it, while A and B would normally talk and would not notice anything,” adds Kurbatov.
Puzankov offers to track the location of the subscriber by number. "Come on, can we try my wife?" - offers Kurbatov. An employee of the company, standing nearby, offers to check on her husband. “Let's give my husband's number, find out if he works? I'll come home today with a frying pan, ”she says. The voice of another employee is heard from behind the monitor: “May my mother-in-law! She does not care. "
Puzankov eventually dials an experimental number that I have already called. In the same hacking software, he enters several lines - and overlays the results on the OpenCellId map. The location of the phone is shown there - not far from Preobrazhenskaya Square.
I am asking to intercept my SMS. I am sending a message with the word "interception" to Puzankov's number. The message does not reach the subscriber, it ends up in a "fake network" - in the intercepted traffic in Wireshark, you can see my number and the content of the SMS. Puzankov adds that the SMS in the "fake network" can be rewritten and sent to the target's phone in an edited form.
Hacking messengers
In the same way, a hacker who has gained access to SS7 can intercept authorization codes from Telegram, WhatsApp and two-factor authorization passwords for Gmail, Facebook, VKontakte.
After transferring the target number to the "fake network", the hacker initiates a connection to Telegram. The captured phone will receive an SMS with a password. After entering the password, the hacker will have full access to the messenger - he will be able to write messages on behalf of the subscriber and read all his correspondence, which Telegram automatically uploads to the new phone. Encrypted chats will remain closed for reading. The hacker will be able to create a new secret chat and correspond on behalf of the captured subscriber.
Old messages cannot be read in WhatsApp - they are not stored on the server; since April 2016, WhatsApp has enabled full encryption for all users.
Using the phone in roaming, the hacker can also intercept the password from two-factor authentication from Gmail, which comes as an SMS. "Anything that depends on SMS can be hacked - and it has already been hacked since SS7 went live," said German hacker Carsten Nol. "The mobile network is probably the weakest link in our digital security."
Victims seldom know they've been hacked. According to a study by the American company FireEye, which develops programs against cyberattacks, the average time a hacker spends in a compromised network or account before being discovered is about 205 days.
On the night of April 29, 2016, oppositionist Oleg Kozlovsky and an employee of the Anti-Corruption Foundation Georgy Alburov, both MTS subscribers, reported about the hacking of their Telegram accounts. Unknown persons intercepted SMS with authorization codes from their accounts. This was enough to enter the system - the oppositionists did not have two-factor authentication with a password enabled. Kozlovsky and Alburov did not receive an SMS with authorization.
Kozlovsky said that at the time of the hack, MTS turned off the SMS delivery service. The support service allegedly told him: "The service of short messages has been disabled by our technical security department." Later, activists posted receipts for services for April 2016: both Kozlovsky and Alburov indicated that short message services were disabled. MTS denied this, MTS spokesman Dmitry Solodovnikov said: “No targeted actions were taken to shut down services. I do not exclude the possibility of a virus attack or access to your account through the web interface. "
If the opposition was attacked via SS7, the hackers could well have prevented the hacked subscribers from receiving SMS. According to Positive Technologies experts, this story can be viewed from a different angle: perhaps the security department of MTS disabled SMS in order to prevent the development of the attack. “We don't know when and at what level they were broken and how many subscribers were attacked,” they wrote. "It is possible that they discovered suspicious transactions and, just in case, blocked a number of services (but it was already too late)."
After the hack, the creator of Telegram Pavel Durov said: “Apparently, the special services of the Russian Federation decided to start putting pressure on telecom operators to intercept the authorization SMS code. Usually this occurs only within the framework of cannibalistic regimes that do not care about their reputation - Central Asia, sometimes the Middle East."
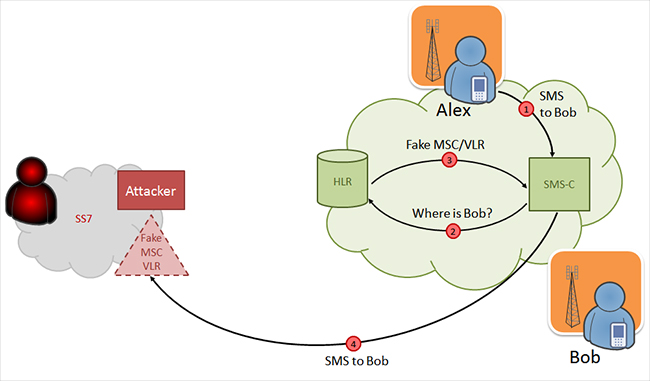
How Cell Phones Attack with SS7 Vulnerability
Russian mobile operators
Megafon representative Yulia Dorokhina agreed that "the use of these protocols for malicious purposes by unscrupulous organizations connected to SS7 is a risk for the industry." She added that SS7 "is not fully available to regular subscribers," and accused Positive Technologies of "inflating the problem." “They want to increase their sales; the equipment they have developed is not in demand, ”said Dorokhina.
The mobile operator has repeatedly recorded suspicious requests to SS7 from foreign operators, but they were blocked by special equipment; Megafon's technical specialists, according to a company representative, “closed the vulnerabilities,” and it will not be possible to listen to subscribers (as CBS did during the experiment with the congressman).
Anna Aibasheva, a representative of VimpelCom (Beeline), sent a short comment: “The security of our clients' personal data is our top priority. VimpelCom implements a whole range of measures to maximize the protection of its network. As a result, we see the absence of massive attacks on our SS7 network. Unfortunately, we cannot disclose the details of the protection of our network, since this is information of limited access."
MTS declined to comment. “Alas, we will refrain,” said Dmitry Solodovnikov from MTS. Tele2 employees were unable to provide an answer within a week, citing lack of time.
Representatives of Russian mobile operators are extremely reluctant to discuss cases of wiretapping or interception of messages through SS7. At one of the meetings, an employee of one of the operators turned the monitor away from Kurbatov and said: "I can't let you see who was the target of the attacks."
6 tips for the paranoid
1. Do not publish your phone number - let only acquaintances know it.
2. Do not register mail and instant messengers to the "highlighted" phone number. It is better to ask a friend whom you trust and who is not associated with you in the first place, to become your key keeper - two-factor authorization passwords will be sent to his phone.
3. Use only secret chats in messengers.
4. In secret chats, use a code word (which the interlocutor knows) - this way you can insure yourself against a conversation with an intruder who has taken possession of someone else's secret chat.
5. Use two-factor authentication - protect your account with a password; bind the account itself to the SIM card of "adequate jurisdiction" (advice from Pavel Durov).
6. Truly secret conversations in the field. In an open field.
Almost any owner of a telephone can be under attack - a politician, human rights activist, journalist, businessman, wife of a jealous husband, husband of a jealous wife; the other seven and a half billion mobile subscribers. Hackers can attack any phones - old push-button phones, smartphones, and devices based on iOS or Android.
About 90% of the world's mobile operators are not protected from attacks via SS7; SMS messages of 89% of subscribers can be intercepted; 58% of subscribers can be tracked; conversations of half of the subscribers can be listened to. This is stated in the report of the Russian company Positive Technologies, which investigated the security systems of the world's largest mobile operators.
What is SS7
SS7 vulnerability has been ignored for over 30 years.
SS7 development began in the 1970s. At that time, radio amateurs were fond of designing home-made devices, with the help of which it was possible to simulate the transmission of signals between telephone exchanges ("inter-office signaling") and send the necessary commands to them. Such devices, known as "blue boxes", allowed calls to be made almost free of charge to any destination, paying for the calls as local. For example, Apple creators Steve Jobs and Steven Wozniak also assembled blue boxes in the garage.
To combat fraudsters, telephone companies have separated subscriber (voice) and service (technical commands) traffic. This is how SS7 appeared, a system of signaling protocols for exchanging information and routing calls (which number calls, whom, from where, and so on). It can be compared to the subway system: SS7 are service tunnels for workers, not the ones used by trains.
SS7 began operating in the early 1980s and brought together telephone operators around the world. In Russia, the USA, Asia, Europe, the protocols are called differently, they differ slightly, but they are compatible with each other; in general, the system resembles the Internet in its structure. In Russia SS7 is called OKS-7 (common signaling channel No. 7), in the USA - CCS7, in Germany - N7, in the UK - CCIS7; common name - SS7.
In the early 2000s, an add-on to SS7 was developed - the Sigtran software, which made it possible to transmit messages and commands over IP networks: SS7 network components became available on public networks, some of them can be connected via the Internet. New and innovative software continued to run on the old system, which was not protected in any way; moreover, it has now turned out to be even easier to "insert" into this system.
Public discussion of the "hole" in SS7 began in 2008. At the Chaos Computer Club hacker conference, German information security researcher Tobias Engel showed the audience how to spy on mobile subscribers based on penetrating SS7. The governments and intelligence agencies apparently knew about the vulnerability even earlier. In a 2007 book by telecom experts Thomas Porter and Michael Goof, "How to Bypass VoIP Security", it was indicated that the US presidential administration was seriously concerned about the high threat level of SS7-based attacks. The possibility of attacks through the vulnerability in SS7 has been discussed in other American documents since 1998. Mobile operators could not be unaware of the vulnerability.
In 2013, a former CIA and US National Security Agency employee, Edward Snowden, handed over archives to The Guardian and The Washington Post, confirming that the US and UK intelligence agencies themselves can spy on anyone on the planet (and use this opportunity). He explained his actions by saying that "he does not want to live in a world where everything that I do and say is recorded."
In the same year, The Washington Post reported that the NSA used attacks on SS7 as one of its methods of surveillance. And in 2014, the journalists of the publication reported about special programs for surveillance based on SS7 - and that using SS7 hackers can "determine the location of a subscriber anywhere in the world, listen to conversations in real time or record encrypted calls and text messages for further decryption".
It was only after publications in The Washington Post that ordinary citizens learned about the vulnerability.
Nevertheless, almost three years after the publication of the first materials based on the Snowden archives, nothing seems to have changed in the security system of mobile networks. Mobile operators around the world generally refuse to acknowledge the problem. Many "white hackers" (they hack companies by order of the companies themselves) are sure that SS7 was created and continues to exist in its former form, including due to the fact that it is convenient to use it for surveillance and wiretapping. “For years, intelligence agencies have known and kept silent about vulnerabilities in communication networks that make citizens vulnerable to hackers. Why? They also use them, ”the Daily Beast claimed.
At the end of April 2020, Wired magazine called the SS7 vulnerability "critical."

Information Security Specialist Tobias Engel
How attacks happen
When the small meeting on information security comes to an end, Dmitry Kurbatov from Positive Technologies instructs the audience: “SMS is only for congratulations, secret conversations are in the field. The constitution guarantees the right to privacy of correspondence, but one should not rely on it. "
At work, Kurbatov daily, with the permission of Russian mobile operators, tries to hack them.
“Listening to [citizens] through SS7 is a very dusty way, you leave no traces, you can act from anywhere,” says Kurbatov. "You can sit in South America and listen to a person in Germany."
Access to hacking and wiretapping is opened after connecting to the SS7 system - this is the most difficult part of the whole hacking process.
In the early years, select commercial and government telephone companies had access to SS7. In 2020, it is impossible to count the number of legal connections to SS7: these are mobile operators, virtual mobile operators, and entertainment content providers. These companies employ hundreds of thousands of people; among them may be disloyal employees with the necessary skills.
In 2014, Kurbatov and his colleague Sergei Puzankov tested how easy it is to find an operator willing to connect strangers to SS7. Talking to mobile operators in South America and Central Asia, they pretended to be up-and-coming value-added content providers who need to connect to SS7 to "send subscribers the best weather forecasts." Many operators agreed to give them access officially, while others offered a connection for four thousand dollars. According to Kurbatov, having acquaintances in any of the telecom operators, it is very easy to get access to SS7.
Wiretapping and surveillance seem to be the specialization of security officials, extremely expensive and difficult. However, due to the insecurity of SS7, privacy information can be obtained by any average hacker. No sophisticated equipment is required to attack subscribers. “You don't need to be a genius or an intelligence service to do all this,” Kurbatov says. - We ourselves wrote the software package, supplementing the downloaded from the Internet. The entry threshold is low. "
Having done the main thing, that is, having hooked up to SS7, the cracker starts working “according to the targets” - that is, according to the subscribers he is going to monitor. First, using the appropriate software, he learns the IMSI number - a special identifier that is assigned to each mobile subscriber (contains the country code, operator code and internal unique SIM card number). At the same time, it receives the MSC / VLR parameters (call and location switch), thanks to which the subscriber is in the network.
The hacker will need all this in order to deceive the subscriber's "home" network and transfer it to his own - a fake one. For a "home" network, it will look as if the subscriber ("target") has roamed; the subscriber himself will never know about it. The fake network will send a command to the operator that now it serves the subscriber itself (that is, the operator will receive a signal that his subscriber is in the service area of another mobile operator). After that - with the help of special software - the hacker will be able to intercept SMS, listen to calls, track the location of the "target".
Kurbatov says this access is less used for surveillance; more often - to steal money from mobile wallets and SMS-banking: this is usually little money, but criminal groups take over. They operate in a distributed manner: those who invented the scheme are in one country, programmers in another; most often come across those who work "on the ground" and are engaged in transfers and cashing stolen money.
In the "deep internet", which can be accessed through Tor, it is easy to find offers of surveillance: “You want to follow your girlfriend? Kidalov is gone, the first day of surveillance is free ”; “Making a breakthrough, determining the location. And other useful services. " They also sell programs that allow you to attack SS7. But even on the regular open Internet there are dozens of sites offering to order a printout of SMS and calls. One of them says: “Do you want to be confident in a person? Would you like to make a mistake? Our service was created for you! " However, judging by the reviews, these sites are fraudulent; they stop responding to "customers" when they receive the first installment. One information security expert questioned whether surveillance sites could openly operate on the Internet.
In addition to intercepting calls and messages using SS7 attacks, a hacker can disable the phone: the device shows that it is receiving a signal, but it cannot be reached. Such attacks can harm businessmen during negotiations; journalists contacting sources; they can also be used during armed conflicts.
Hacks
In April 2020, German researcher of mobile networks Carsten Nohl, as part of an experiment on the CBS television channel, hacked and listened to the conversations of the American Congressman Ted Lew. The cracker only knew the politician's mobile phone number. The hacker used a vulnerability in SS7 to attack. In addition to wiretapping and recording all conversations, he was able to track the movements of the congressman - despite the fact that the GPS was turned off in the smartphone.
The congressman was shocked. After the experiment, he admitted to reporters that in 2015, US President Barack Obama called him on his personal phone. “We discussed a number of issues with him,” he said. - If the hackers listened to us, they would know the content of this conversation. All of this is causing great concern. "He demanded that Congress investigate and secure mobile phone users." People who knew about this gap should be fired, "he said. - You cannot expose 300 million Americans, the entire nation, to the risk of interception of telephone conversations just because this vulnerability is known and can be useful to the special services. This is unacceptable ".
Through SS7, apparently, politicians were seriously tapped more than once.
In February 2014, an audio recording of a telephone conversation was posted on YouTube, in which US Deputy Secretary of State Victoria Nuland and US Ambassador to Kiev Jeffrey Payet allegedly participated. "Diplomats" discussed Ukrainian politicians, "Nuland" during the conversation said, in particular, that it does not consider it a "good idea" to include Vitali Klitschko in the local government - and proposed its candidates. Dmitry Rogozin's assistant Dmitry Loskutov was one of the first to post the recording of the conversation on Twitter; he later claimed to have stumbled upon the link by accident. In the same year, an audio recording of an alleged conversation between Ukrainian politicians Yulia Tymoshenko and Nestor Shufrich appeared on YouTube.
At the end of May 2020, the National Commission for State Regulation in the Sphere of Communications and Informatization of Ukraine (NCCIR) published the results of the verification of information that calls from some subscribers of the Ukrainian MTS pass through Russian switches. The report indicated that the hackers, using the vulnerability, switched subscribers of MTS-Ukraine to a server presumably belonging to the Russian subsidiary of Tele2 - Rostov Cellular Communications. A Tele2 spokesman denied this.
In Russia, to wiretap calls and intercept correspondence, special services can use SORM - a system of technical means to ensure operational search activities. It has been around since the late 1980s and has been updated several times. According to Russian law, the special services have the right to activate the system only by a court decision. At the same time, in 2012, the Supreme Court of Russia recognized the right of the special services to wiretap opposition members only on the grounds that they were engaged in protest activities. In the investigation of the Russian Forbes, it was indicated that the FSB officer is not obliged to show the decision to wiretap to anyone - telecom operators have no right to know whose negotiations or mail are being intercepted by the special services.
However, with the help of SORM, special services can only listen to subscribers of Russian operators - citizens of the Russian Federation who have left for other countries, it will not be possible to track them with the help of SORM. But this allows you to make the SS7 vulnerability.
Experiment
An SS7 burglar, Sergei Puzankov, is experienced sitting at a table in the corner. There are two monitors in front of him. One has Wireshark open, in which it monitors SS7 traffic. The second is a proprietary program for testing mobile operators, that is, for legal hacking.
Dmitry Kurbatov is standing nearby. “We finished this software to create attacks, attackers can do the same,” he says and promises to show how easy it is to intercept calls and SMS. They refuse to conduct an experiment with wiretapping of Russian politicians, similar to that organized by the American television channel CBS.
At the request of Sergei Puzankov, I call his "experimental" number, registered in the network of one of the Russian mobile operators. The melody of a mobile phone lying on the table is heard; we talk with Puzankov for a few seconds. He nods, opens the program, writes a few lines, a phone number, IMSI into the hacking software - and thus transfers the "hacked phone" to a fake network. Sergey asks to call again. The "tracked" phone is silent, but another one, lying on the table nearby, rings. “This is how we redirected the call,” he says. “And they could just redirect the call so as to record it, while A and B would normally talk and would not notice anything,” adds Kurbatov.
Puzankov offers to track the location of the subscriber by number. "Come on, can we try my wife?" - offers Kurbatov. An employee of the company, standing nearby, offers to check on her husband. “Let's give my husband's number, find out if he works? I'll come home today with a frying pan, ”she says. The voice of another employee is heard from behind the monitor: “May my mother-in-law! She does not care. "
Puzankov eventually dials an experimental number that I have already called. In the same hacking software, he enters several lines - and overlays the results on the OpenCellId map. The location of the phone is shown there - not far from Preobrazhenskaya Square.
I am asking to intercept my SMS. I am sending a message with the word "interception" to Puzankov's number. The message does not reach the subscriber, it ends up in a "fake network" - in the intercepted traffic in Wireshark, you can see my number and the content of the SMS. Puzankov adds that the SMS in the "fake network" can be rewritten and sent to the target's phone in an edited form.
Hacking messengers
In the same way, a hacker who has gained access to SS7 can intercept authorization codes from Telegram, WhatsApp and two-factor authorization passwords for Gmail, Facebook, VKontakte.
After transferring the target number to the "fake network", the hacker initiates a connection to Telegram. The captured phone will receive an SMS with a password. After entering the password, the hacker will have full access to the messenger - he will be able to write messages on behalf of the subscriber and read all his correspondence, which Telegram automatically uploads to the new phone. Encrypted chats will remain closed for reading. The hacker will be able to create a new secret chat and correspond on behalf of the captured subscriber.
Old messages cannot be read in WhatsApp - they are not stored on the server; since April 2016, WhatsApp has enabled full encryption for all users.
Using the phone in roaming, the hacker can also intercept the password from two-factor authentication from Gmail, which comes as an SMS. "Anything that depends on SMS can be hacked - and it has already been hacked since SS7 went live," said German hacker Carsten Nol. "The mobile network is probably the weakest link in our digital security."
Victims seldom know they've been hacked. According to a study by the American company FireEye, which develops programs against cyberattacks, the average time a hacker spends in a compromised network or account before being discovered is about 205 days.
On the night of April 29, 2016, oppositionist Oleg Kozlovsky and an employee of the Anti-Corruption Foundation Georgy Alburov, both MTS subscribers, reported about the hacking of their Telegram accounts. Unknown persons intercepted SMS with authorization codes from their accounts. This was enough to enter the system - the oppositionists did not have two-factor authentication with a password enabled. Kozlovsky and Alburov did not receive an SMS with authorization.
Kozlovsky said that at the time of the hack, MTS turned off the SMS delivery service. The support service allegedly told him: "The service of short messages has been disabled by our technical security department." Later, activists posted receipts for services for April 2016: both Kozlovsky and Alburov indicated that short message services were disabled. MTS denied this, MTS spokesman Dmitry Solodovnikov said: “No targeted actions were taken to shut down services. I do not exclude the possibility of a virus attack or access to your account through the web interface. "
If the opposition was attacked via SS7, the hackers could well have prevented the hacked subscribers from receiving SMS. According to Positive Technologies experts, this story can be viewed from a different angle: perhaps the security department of MTS disabled SMS in order to prevent the development of the attack. “We don't know when and at what level they were broken and how many subscribers were attacked,” they wrote. "It is possible that they discovered suspicious transactions and, just in case, blocked a number of services (but it was already too late)."
After the hack, the creator of Telegram Pavel Durov said: “Apparently, the special services of the Russian Federation decided to start putting pressure on telecom operators to intercept the authorization SMS code. Usually this occurs only within the framework of cannibalistic regimes that do not care about their reputation - Central Asia, sometimes the Middle East."

How Cell Phones Attack with SS7 Vulnerability
Russian mobile operators
Megafon representative Yulia Dorokhina agreed that "the use of these protocols for malicious purposes by unscrupulous organizations connected to SS7 is a risk for the industry." She added that SS7 "is not fully available to regular subscribers," and accused Positive Technologies of "inflating the problem." “They want to increase their sales; the equipment they have developed is not in demand, ”said Dorokhina.
The mobile operator has repeatedly recorded suspicious requests to SS7 from foreign operators, but they were blocked by special equipment; Megafon's technical specialists, according to a company representative, “closed the vulnerabilities,” and it will not be possible to listen to subscribers (as CBS did during the experiment with the congressman).
Anna Aibasheva, a representative of VimpelCom (Beeline), sent a short comment: “The security of our clients' personal data is our top priority. VimpelCom implements a whole range of measures to maximize the protection of its network. As a result, we see the absence of massive attacks on our SS7 network. Unfortunately, we cannot disclose the details of the protection of our network, since this is information of limited access."
MTS declined to comment. “Alas, we will refrain,” said Dmitry Solodovnikov from MTS. Tele2 employees were unable to provide an answer within a week, citing lack of time.
Representatives of Russian mobile operators are extremely reluctant to discuss cases of wiretapping or interception of messages through SS7. At one of the meetings, an employee of one of the operators turned the monitor away from Kurbatov and said: "I can't let you see who was the target of the attacks."
6 tips for the paranoid
1. Do not publish your phone number - let only acquaintances know it.
2. Do not register mail and instant messengers to the "highlighted" phone number. It is better to ask a friend whom you trust and who is not associated with you in the first place, to become your key keeper - two-factor authorization passwords will be sent to his phone.
3. Use only secret chats in messengers.
4. In secret chats, use a code word (which the interlocutor knows) - this way you can insure yourself against a conversation with an intruder who has taken possession of someone else's secret chat.
5. Use two-factor authentication - protect your account with a password; bind the account itself to the SIM card of "adequate jurisdiction" (advice from Pavel Durov).
6. Truly secret conversations in the field. In an open field.
