Father
Professional
- Messages
- 2,602
- Reaction score
- 830
- Points
- 113
HelloKitty changes its name and gives players a Witcher 3 build.
The operator of the ransomware program HelloKitty announced a change of name to HelloGookie and released passwords for previously leaked CD Projekt RED source codes, information about Cisco networks, and keys for decrypting data from previous attacks.
The name change is accompanied by the launch of a new portal on the darknet. In honor of the launch, the attacker, known as Gookee / kapuchin0 and claiming to have created HelloKitty, released 4 private keys to decrypt the files of previous attacks, as well as internal information stolen from Cisco in 2022 and passwords to the leaked source code of Gwent, Witcher 3 and Red Engine, stolen from CD Projekt in 2021 year.
According to VX-Underground, the source code for The Witcher 3 has already been compiled, and screenshots and videos of the game's builds being developed have appeared on the Internet.
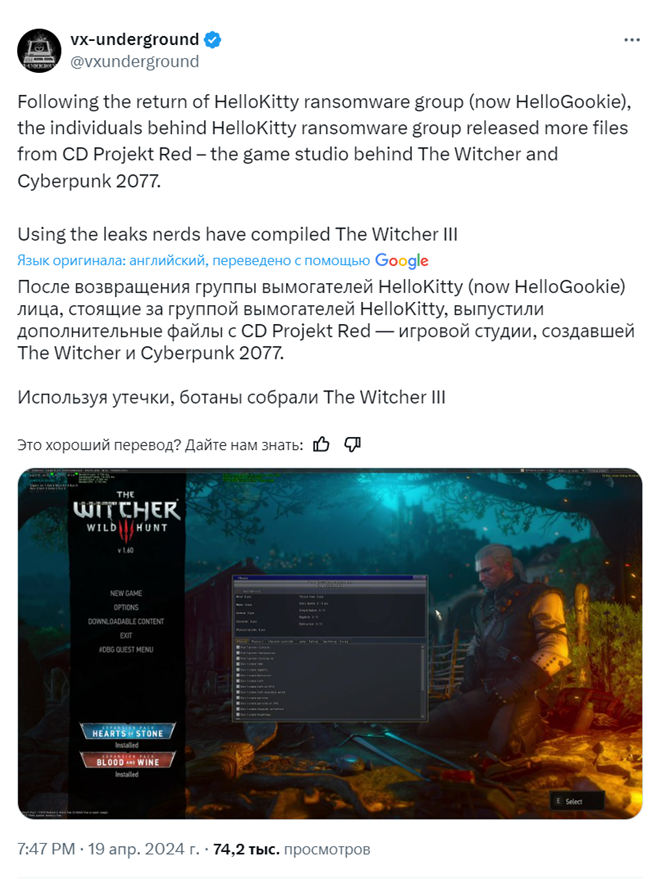
VX-Underground Tweet about the Witcher 3 Build
One of the representatives of the Witcher 3 team, known as "sventek", said that the leaked CD Projekt data occupies 450 GB in uncompressed form and contains the source codes of the Witcher 3, Gwent, Cyberpunk games, as well as SDKs for various consoles (PS4/PS5 XBOX NINTENDO) and some build logs. Sventek also noted that he had previously managed to compile Cyberpunk 2077 from leaked data and that he was behind the previous GTA V source code leak.
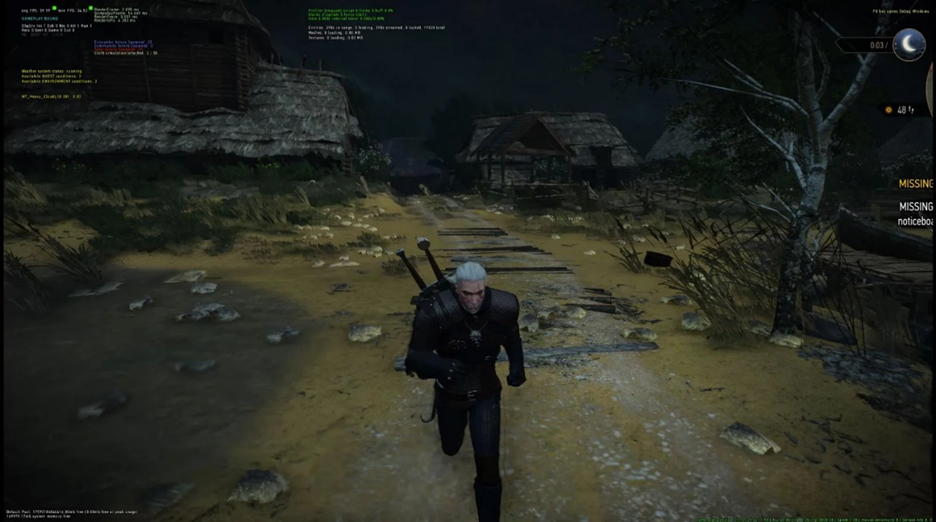
Screenshot of the alleged Witcher 3 build compiled from leaked source code
Gookee / kapuchin0 also shared that in October 2023, information about the HelloKitty builder and source code was leaked on one of the hacker forums, which marked the end of HelloKitty operations.
Under the new name HelloGookie, data from old attacks on CD Projekt Red and Cisco were published. The leak site also published 4 private keys for the old version of the HelloKity cryptographer, which may allow some victims to recover their files for free.
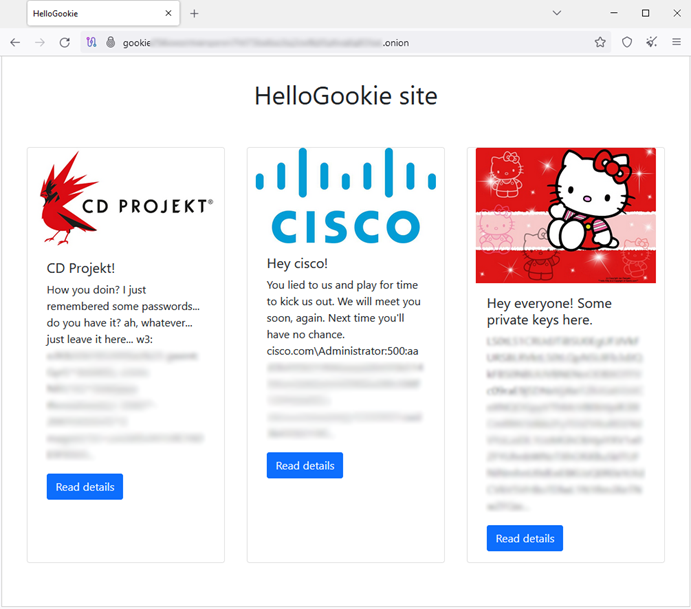
New HelloGookie website
Cisco confirmed that it is familiar with the published information about the leak and recalled that a detailed description of the incident was published in 2022 on the Cisco Talos blog.
It remains to be seen whether HelloGookie will be able to achieve the same level of operational success, attack volumes, and visibility as HelloKitty.
The operator of the ransomware program HelloKitty announced a change of name to HelloGookie and released passwords for previously leaked CD Projekt RED source codes, information about Cisco networks, and keys for decrypting data from previous attacks.
The name change is accompanied by the launch of a new portal on the darknet. In honor of the launch, the attacker, known as Gookee / kapuchin0 and claiming to have created HelloKitty, released 4 private keys to decrypt the files of previous attacks, as well as internal information stolen from Cisco in 2022 and passwords to the leaked source code of Gwent, Witcher 3 and Red Engine, stolen from CD Projekt in 2021 year.
According to VX-Underground, the source code for The Witcher 3 has already been compiled, and screenshots and videos of the game's builds being developed have appeared on the Internet.

VX-Underground Tweet about the Witcher 3 Build
One of the representatives of the Witcher 3 team, known as "sventek", said that the leaked CD Projekt data occupies 450 GB in uncompressed form and contains the source codes of the Witcher 3, Gwent, Cyberpunk games, as well as SDKs for various consoles (PS4/PS5 XBOX NINTENDO) and some build logs. Sventek also noted that he had previously managed to compile Cyberpunk 2077 from leaked data and that he was behind the previous GTA V source code leak.

Screenshot of the alleged Witcher 3 build compiled from leaked source code
Gookee / kapuchin0 also shared that in October 2023, information about the HelloKitty builder and source code was leaked on one of the hacker forums, which marked the end of HelloKitty operations.
Under the new name HelloGookie, data from old attacks on CD Projekt Red and Cisco were published. The leak site also published 4 private keys for the old version of the HelloKity cryptographer, which may allow some victims to recover their files for free.

New HelloGookie website
Cisco confirmed that it is familiar with the published information about the leak and recalled that a detailed description of the incident was published in 2022 on the Cisco Talos blog.
It remains to be seen whether HelloGookie will be able to achieve the same level of operational success, attack volumes, and visibility as HelloKitty.
