BadB
Professional
- Messages
- 2,459
- Reaction score
- 2,449
- Points
- 113
We will hack the cellular network and intercept any data from any number.
Salute to everyone, dear friends!
As you already understood, today we will talk about attacks on the SS7 protocol.
Let's, so that most of you understand what is at stake, we will immediately explain:
What is SS7?
SS7, also known as Signaling System # 7, refers to a data network and a set of technical protocols or rules that govern the exchange of data over it. It was developed in the 1970s to track and connect calls across different carrier networks, but is now commonly used to calculate cellular billing and send text messages in addition to routing mobile and landline calls between carriers and regional switching centers.
What will the SS7 hack give?
Wiretapping and interception of SMS from any person on the planet, anywhere in the world. All we need to know is a phone number
Impressive, isn't it?
How do I get access?
Please note that the instructions are not intended for beginners, as well as any method of hacking SS7.
OS requirement:
Used tools:
tsscale opensource ss7 stack (CLICK TO DOWNLOAD)
This tool is in Java format - .jar
Recent JDK 7u6 releases include the JavaFX SDK (version 2.2 or later). You need to install the JavaFX SDK and runtime and integrate them into the standard JDK directory structure.
Now about installing 64-bit JRE on Linux platforms:
THIS PROCEDURE INSTALLS JAVA RUNTIME ENRIVONMENT (JRE) FOR 64-BIT LINUX, USING A DUAL ARCHIVE FILE (.TAR.GZ). THESE INSTRUCTIONS USE THE FOLLOWING FILE:
jre-8uversion-linux-x64.tar.gz
Before starting the client on any Ss7 network:
Make sure you change the client_config file:
// Client
SERVER_IP = "STP IP address you are connecting to"
CLIENT_IP = "IP address provided to you by STP"
SERVERPORT = "STP port" CLIENTPORT = "Client supplied port" IS_SSERVER = FALSE "must always be false" LocalC = "Point code assigned to you"
Remote_SPCSPC = “STP Point Code” Local = “Local SSN” Remote_SSN = SSN = “Remote SSN” ”Routingt =“ Routing Context assigned to you by STP ”NETWORK_INDICATOR =“ Network Indicator ”
Local_GT = "Local global title assigned to you"
Remote_GT = "remote global header that you are testing" "" Network indicator "Local_GT =" Local global header assigned to you "
Remote_GT = "the remote global header you are testing" ""
Commands for Simulating SS7 Network
SafeSeven Launch Commands
How to intercept SMS using MapSMS.jar:
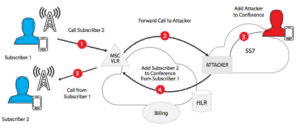
Step 1
1. We send a SendRoutingInfoForSM request by addressing the MAP message (part of the mobile application) by MSISDN (target phone number)
2. The HLR (Home Resource Locator) responds with its own address serving the MSC address, IMSI (International Mobile Subscriber Identity (IMSI) is an international standardized unique number for identifying a mobile subscriber. IMSI is defined in ITU-T Rec. E 0.212 .
IMSI consists of Mobile Country Code (MCC), Mobile Network Code (MNC) and Mobile Station Identification Number (MSIN)
Step 2
1. Register the victim's phone number on a fake MSC
2. HLR sets a new location for our target number
3. HLR asks the real MSC to free memory
Step 3
1. Someone sends an SMS to the victim's number
2. MSC translates SMS to SMS-C
3. SMS-C asks HLR to locate the target number
4. HLR replies with a bogus MSC address
5. SMS-C transfers SMS to fake MSC
Your Wireshark intercepts SMS and that's all.
As you understand, dear friends, in order to carry out this attack, you must have a good skill. And where to pump this skill?
Hacker Place Academy, of course!
It doesn't matter what knowledge you have at the time of entering the Academy. We will train any person without extra chromosomes.
Salute to everyone, dear friends!
As you already understood, today we will talk about attacks on the SS7 protocol.
Let's, so that most of you understand what is at stake, we will immediately explain:
What is SS7?
SS7, also known as Signaling System # 7, refers to a data network and a set of technical protocols or rules that govern the exchange of data over it. It was developed in the 1970s to track and connect calls across different carrier networks, but is now commonly used to calculate cellular billing and send text messages in addition to routing mobile and landline calls between carriers and regional switching centers.
What will the SS7 hack give?
Wiretapping and interception of SMS from any person on the planet, anywhere in the world. All we need to know is a phone number
Impressive, isn't it?
How do I get access?
Please note that the instructions are not intended for beginners, as well as any method of hacking SS7.
OS requirement:
- Linux OS with SCTP support
- JRE 1.7 (Java SE Runtime Environment) or higher [/URL]CLICK TO DOWNLOAD)
Used tools:
tsscale opensource ss7 stack (CLICK TO DOWNLOAD)
This tool is in Java format - .jar
Recent JDK 7u6 releases include the JavaFX SDK (version 2.2 or later). You need to install the JavaFX SDK and runtime and integrate them into the standard JDK directory structure.
Now about installing 64-bit JRE on Linux platforms:
THIS PROCEDURE INSTALLS JAVA RUNTIME ENRIVONMENT (JRE) FOR 64-BIT LINUX, USING A DUAL ARCHIVE FILE (.TAR.GZ). THESE INSTRUCTIONS USE THE FOLLOWING FILE:
jre-8uversion-linux-x64.tar.gz
- Change the current directory to the directory where you want to install the JDK, and then move the .tar.gz binary archive file there
- Unpack the archive and install the JRE:
- The Java Development Kit files are installed in a directory named jdk1.8.0_version in the directory of your choice.
- Now let's unpack the safeseven files into your home directory.
- Now let's open WireShark. (Wireshark comes preinstalled on Kali Linux)
- Let 's select "SCTP" and start capturing data packets.
- Then we'll open a terminal.
Before starting the client on any Ss7 network:
Make sure you change the client_config file:
// Client
SERVER_IP = "STP IP address you are connecting to"
CLIENT_IP = "IP address provided to you by STP"
SERVERPORT = "STP port" CLIENTPORT = "Client supplied port" IS_SSERVER = FALSE "must always be false" LocalC = "Point code assigned to you"
Remote_SPCSPC = “STP Point Code” Local = “Local SSN” Remote_SSN = SSN = “Remote SSN” ”Routingt =“ Routing Context assigned to you by STP ”NETWORK_INDICATOR =“ Network Indicator ”
Local_GT = "Local global title assigned to you"
Remote_GT = "remote global header that you are testing" "" Network indicator "Local_GT =" Local global header assigned to you "
Remote_GT = "the remote global header you are testing" ""
Commands for Simulating SS7 Network
- Simulated HLR :java -jar server.jar hlr_config
- Simulated MSC / VLR :java -jar server.jar vlr_config
- Start STP : java -jar STP.jar stp_config
SafeSeven Launch Commands
- MS related operations: java -jar SMS.jar client_config
- Operations related to USSD: java -jar ussd.jar client_config
- Call-related operations: java -jar Call_Handling.jar client_config
- Operations related to mobility: java -jar Mobility.jar client_config
- Operations related to mobility: java -jar Mobility.jar client_config
How to intercept SMS using MapSMS.jar:

Step 1
1. We send a SendRoutingInfoForSM request by addressing the MAP message (part of the mobile application) by MSISDN (target phone number)
2. The HLR (Home Resource Locator) responds with its own address serving the MSC address, IMSI (International Mobile Subscriber Identity (IMSI) is an international standardized unique number for identifying a mobile subscriber. IMSI is defined in ITU-T Rec. E 0.212 .
IMSI consists of Mobile Country Code (MCC), Mobile Network Code (MNC) and Mobile Station Identification Number (MSIN)
Step 2
1. Register the victim's phone number on a fake MSC
2. HLR sets a new location for our target number
3. HLR asks the real MSC to free memory
Step 3
1. Someone sends an SMS to the victim's number
2. MSC translates SMS to SMS-C
3. SMS-C asks HLR to locate the target number
4. HLR replies with a bogus MSC address
5. SMS-C transfers SMS to fake MSC
Your Wireshark intercepts SMS and that's all.
As you understand, dear friends, in order to carry out this attack, you must have a good skill. And where to pump this skill?
Hacker Place Academy, of course!
It doesn't matter what knowledge you have at the time of entering the Academy. We will train any person without extra chromosomes.
Last edited by a moderator:

