Friend
Professional
- Messages
- 2,669
- Reaction score
- 944
- Points
- 113
Cybercriminals have found a new way to deceive even the most cautious users.
Menlo Security discovered a new phishing campaign that uses Google + to bypass security systems and deceive users, forcing victims to click on fake links created to steal confidential information.
The attack is a prime example of Living off Trusted Sites (LoTS), when attackers use known and trusted sites for malicious purposes. The attackers chose some of the most popular services in the IT sphere, Google and WhatsApp, to host the attack tools, and also created a fake Amazon page to collect victims data.
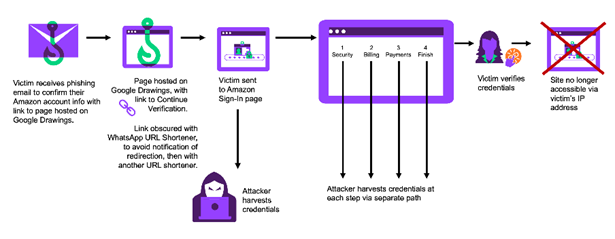
Attack Chain
The attack begins with a phishing email that directs recipients to an image purporting to represent an Amazon account verification link. The image is hosted on Google Drawings, which helps avoid detection.
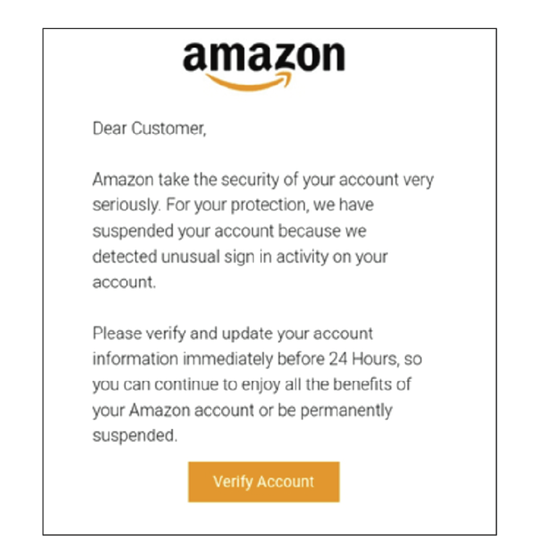
Image that mimics the link for checking your Amazon account
Using legitimate services provides attackers with obvious advantages: not only do they save on cost, but they can also communicate within networks without being detected by security tools and firewalls. The Google Images service is attractive at the initial stage of the attack because it allows you to include links in graphic images. The user may not even notice the link, especially if they feel the urgency of a threat to their Amazon account.
Users who click on the link to verify their account are taken to a fake Amazon login page. The page address is created sequentially using two shortened URLs-via WhatsApp ("l.wl[.]co"), and then qrco[.]de – for additional obfuscation and deception of URL crawlers.
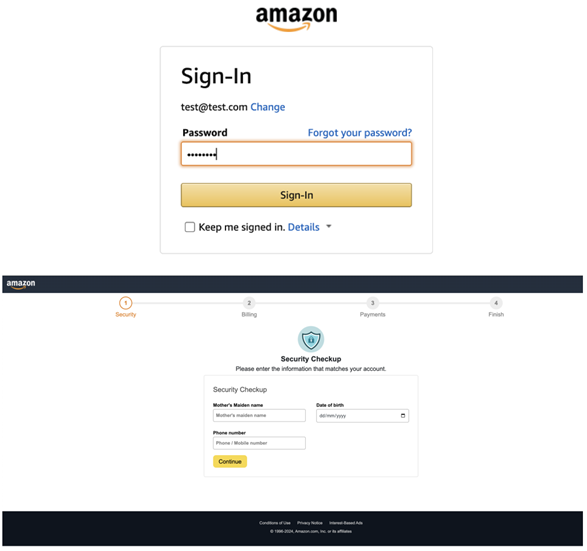
Fake login page and account "verification" process
When the victim enters their credentials on the fake login page, four different pages are then displayed to collect further information step-by-step. The victim's data is collected as each of the four steps is completed and sent to the attacker. It is noteworthy that even if the victim changes his mind or stops in the process of filling in the data, the cybercriminal will still receive information from each step that has already been completed.
The fake page is designed to collect credentials, personal information, and credit card details. After data theft, victims are redirected to the real Amazon login page. As an additional precaution, the page becomes inaccessible from the same IP address after the credentials have been verified.
Source
Menlo Security discovered a new phishing campaign that uses Google + to bypass security systems and deceive users, forcing victims to click on fake links created to steal confidential information.
The attack is a prime example of Living off Trusted Sites (LoTS), when attackers use known and trusted sites for malicious purposes. The attackers chose some of the most popular services in the IT sphere, Google and WhatsApp, to host the attack tools, and also created a fake Amazon page to collect victims data.

Attack Chain
The attack begins with a phishing email that directs recipients to an image purporting to represent an Amazon account verification link. The image is hosted on Google Drawings, which helps avoid detection.

Image that mimics the link for checking your Amazon account
Using legitimate services provides attackers with obvious advantages: not only do they save on cost, but they can also communicate within networks without being detected by security tools and firewalls. The Google Images service is attractive at the initial stage of the attack because it allows you to include links in graphic images. The user may not even notice the link, especially if they feel the urgency of a threat to their Amazon account.
Users who click on the link to verify their account are taken to a fake Amazon login page. The page address is created sequentially using two shortened URLs-via WhatsApp ("l.wl[.]co"), and then qrco[.]de – for additional obfuscation and deception of URL crawlers.

Fake login page and account "verification" process
When the victim enters their credentials on the fake login page, four different pages are then displayed to collect further information step-by-step. The victim's data is collected as each of the four steps is completed and sent to the attacker. It is noteworthy that even if the victim changes his mind or stops in the process of filling in the data, the cybercriminal will still receive information from each step that has already been completed.
The fake page is designed to collect credentials, personal information, and credit card details. After data theft, victims are redirected to the real Amazon login page. As an additional precaution, the page becomes inaccessible from the same IP address after the credentials have been verified.
Source
