Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,036
- Points
- 113
How scammers make money from the popularity of antivirus programs.
Cybercriminals use fake sites that mimic the sites of Avast, Bitdefender, and Malwarebytes to distribute infostilers for Android and Windows. Trellix specialists told about the new campaign in their report.
Trellix has identified a list of fraudulent sites:
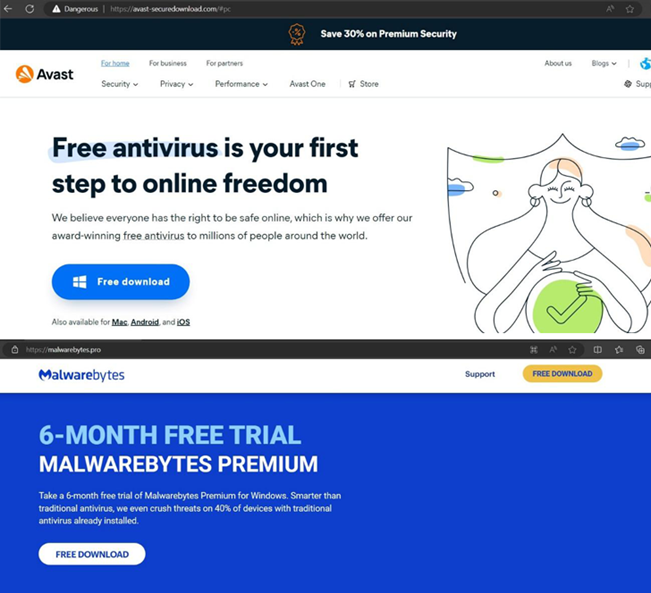
Fake sites
In addition, Trellix detected a fake executable file AMCoreDat.exe, which serves as a distribution channel for malware that can collect information about the victim, including browser data, and transmit it to a remote server.
At the moment, it is not clear how fake sites are distributed, but such campaigns usually use methods such as malicious advertising (Malvertising) and SEO poisoning (SEO poisoning) in order to increase the visibility of fake sites in search results.
Cybercriminals use fake sites that mimic the sites of Avast, Bitdefender, and Malwarebytes to distribute infostilers for Android and Windows. Trellix specialists told about the new campaign in their report.
Trellix has identified a list of fraudulent sites:
- avast-securedownload[.]com - distributes the Spnote Trojan as an Android package (Avast. apk). Once installed, the app asks for intrusive permissions to read SMS messages and call logs, install and uninstall apps, create screenshots, track your location, and even mine cryptocurrency.
- bitdefender-app[.]com - distributes a ZIP archive (setup-win-x86-x64.exe.zip) containing a Lumma Stealer designed to steal information.
- malwarebytes[.]pro - distributes the RAR archive (MBSetup.rar), which installs the StealC malware to steal data.

Fake sites
In addition, Trellix detected a fake executable file AMCoreDat.exe, which serves as a distribution channel for malware that can collect information about the victim, including browser data, and transmit it to a remote server.
At the moment, it is not clear how fake sites are distributed, but such campaigns usually use methods such as malicious advertising (Malvertising) and SEO poisoning (SEO poisoning) in order to increase the visibility of fake sites in search results.

