Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,318
- Points
- 113
An anonymous hacker challenges the protection of the leading Bug Bounty platform.
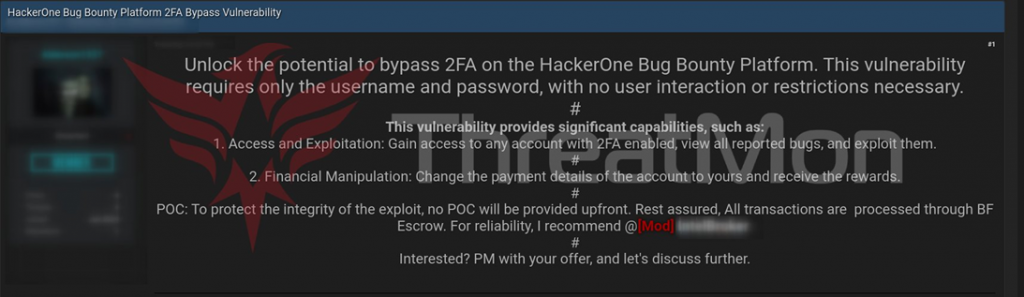
An anonymous hacker from a cybercrime forum recently reported a vulnerability that could bypass two-factor authentication (2FA) on the HackerOne platform, known for its bug bounty programs. A message about this appeared in the official account of ThreatMon, a company specializing in information security.
HackerOne is a leading information security platform that connects companies with cybersecurity experts to identify and eliminate vulnerabilities. Among the largest clients of the platform, for example, you can specify the company Netflix.
Judging by the attacker's statement, he has a valid PoC exploit that can be used to bypass HackerOne's two-factor authentication, which significantly simplifies the potential compromise of company accounts or the white hackers themselves.
The platform is known for its robust security measures, so the claim of a vulnerability is particularly worrisome. Experts suggest that the confirmation of this breach can have serious consequences for users of the platform and the community of cyber specialists in general.
So far, HackerOne representatives have not released an official confirmation or denial about the existence of a vulnerability in 2FA, which shrouds the situation in an additional veil of intrigue.
The information security community reacted to this news with a combination of skepticism and concern. Some are waiting for an official statement and details from HackerOne, while others are already discussing the potential consequences of such a vulnerability.
If the 2FA bypass turns out to be real, attackers can get unauthorized access to confidential information, as well as to cybersecurity reports that include data on undisclosed vulnerabilities of a particular software, which will undoubtedly undermine the overall level of security in cyberspace.
Source
An anonymous hacker from a cybercrime forum recently reported a vulnerability that could bypass two-factor authentication (2FA) on the HackerOne platform, known for its bug bounty programs. A message about this appeared in the official account of ThreatMon, a company specializing in information security.

HackerOne is a leading information security platform that connects companies with cybersecurity experts to identify and eliminate vulnerabilities. Among the largest clients of the platform, for example, you can specify the company Netflix.
Judging by the attacker's statement, he has a valid PoC exploit that can be used to bypass HackerOne's two-factor authentication, which significantly simplifies the potential compromise of company accounts or the white hackers themselves.
The platform is known for its robust security measures, so the claim of a vulnerability is particularly worrisome. Experts suggest that the confirmation of this breach can have serious consequences for users of the platform and the community of cyber specialists in general.
So far, HackerOne representatives have not released an official confirmation or denial about the existence of a vulnerability in 2FA, which shrouds the situation in an additional veil of intrigue.
The information security community reacted to this news with a combination of skepticism and concern. Some are waiting for an official statement and details from HackerOne, while others are already discussing the potential consequences of such a vulnerability.
If the 2FA bypass turns out to be real, attackers can get unauthorized access to confidential information, as well as to cybersecurity reports that include data on undisclosed vulnerabilities of a particular software, which will undoubtedly undermine the overall level of security in cyberspace.
Source

