CarderPlanet
Professional
- Messages
- 2,549
- Reaction score
- 724
- Points
- 113
Weak site protection or deliberate action by hackers?
The hacker group Snatch Ransomware faced a data leak that revealed internal operations and the true location of cybercriminals on the Internet. The Snatch leak site not only provides user data, but also demonstrates network infrastructure vulnerabilities. This was written by the publication KrebsOnSecurity, referring to the analysis.
The Snatch group, first discovered in 2018, publishes the stolen data of organizations that refused to pay ransom on a site on the open Internet, as well as on a site in the Tor network. However, the "server status" page in the darknet version of Snatch reveals the real IP addresses of users.
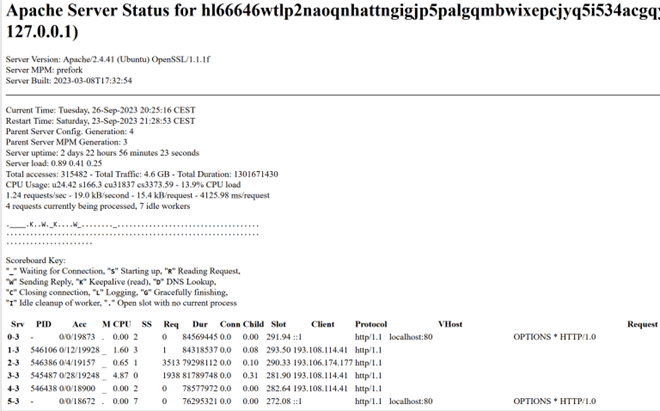
The Snatch website operates on Central European Summer Time (CET,UTC+1) and on OpenSSL / 1.1.1 f, which is no longer supported by security updates
It is noted that some IP addresses that frequently visit the Snatch website are linked to servers in Yekaterinburg and Moscow. The detected servers contain not only Snatch domains, but also numerous phishing domains that mimic well-known brands and software.
Additional analysis confirmed that the Snatch group uses Google Ads to distribute malware, disguising it as popular free programs such as Microsoft Teams, Adobe Reader, and others. Interestingly, all the phishing domains associated with the Snatch group are registered in one name, which has more than 1,300 domain names, half of which are associated with phishing sites, and the other half with escort service sites.
In August 2023, researchers from Trustwave Spiderlabs discovered the domains used to distribute the Rilide information theft Trojan . KrebsOnSecurity also said that cybercriminals sell "fraudulent advertising as a service" (Malvertising-as-a-Service) on the darknet, which is probably the reason for the surge in malicious activity. This trend raises serious security concerns, as users can encounter malware even by simply searching for popular programs on the Internet.
The hacker group Snatch Ransomware faced a data leak that revealed internal operations and the true location of cybercriminals on the Internet. The Snatch leak site not only provides user data, but also demonstrates network infrastructure vulnerabilities. This was written by the publication KrebsOnSecurity, referring to the analysis.
The Snatch group, first discovered in 2018, publishes the stolen data of organizations that refused to pay ransom on a site on the open Internet, as well as on a site in the Tor network. However, the "server status" page in the darknet version of Snatch reveals the real IP addresses of users.

The Snatch website operates on Central European Summer Time (CET,UTC+1) and on OpenSSL / 1.1.1 f, which is no longer supported by security updates
It is noted that some IP addresses that frequently visit the Snatch website are linked to servers in Yekaterinburg and Moscow. The detected servers contain not only Snatch domains, but also numerous phishing domains that mimic well-known brands and software.
Additional analysis confirmed that the Snatch group uses Google Ads to distribute malware, disguising it as popular free programs such as Microsoft Teams, Adobe Reader, and others. Interestingly, all the phishing domains associated with the Snatch group are registered in one name, which has more than 1,300 domain names, half of which are associated with phishing sites, and the other half with escort service sites.
In August 2023, researchers from Trustwave Spiderlabs discovered the domains used to distribute the Rilide information theft Trojan . KrebsOnSecurity also said that cybercriminals sell "fraudulent advertising as a service" (Malvertising-as-a-Service) on the darknet, which is probably the reason for the surge in malicious activity. This trend raises serious security concerns, as users can encounter malware even by simply searching for popular programs on the Internet.

