Man
Professional
- Messages
- 3,223
- Reaction score
- 915
- Points
- 113

This guy opened all the turnstiles at the station. Do you still think all hackers are bad?
Let me start with a simple question: How many of you use public transportation? And who likes paying for it? If there are any of those, you can safely stop reading this article. For the rest, I have a story about how four high school students from Massachusetts hacked the local transit system.
For Bostonians, this article will help you get free rides, and for everyone else, this material will be a good lesson in reverse engineering. Or, at the very least, you will learn an interesting story.
Various authors have written on Habr about hacking transport cards many times. In 2016, Troika got it, then Podorozhnik, Citycard and Metromoney. The first articles in this series soon mysteriously disappeared from the site's pages, but fixing the problem of leaky transport systems in reality turned out to be somewhat more difficult. Otherwise, why is it still relevant today, 7 years later, in major cities around the world?
This time, the topic was explored by ordinary high school students Matty Harris, Zachary Bertocchi, Noah Gibson, and Scott Campbell. As a result, they presented a report at DEF CON 31. Let's figure out how and what they achieved.
Brief background

So, the T (aka MBTA) — the Massachusetts Bay Transportation Authority — was hacked. It's an American government agency that coordinates the local subway, commuter trains, ferries, and most buses in Boston. It's also the oldest transportation system in the United States, and it already had problems with hackers in 2008.
Then a group of MIT students figured out how to hack Charlie magnetic stripe cards and charge them up to $600. They wanted to give a presentation at DEF CON, but the MBTA didn't like the idea. The agency filed an injunction, and the presentation never took place.
The irony is that when they were sued, under US law the presentation and all the research materials went into the public domain. These recordings inspired a new generation of hackers to try again.
An awl for soap

The last time transit cards were hacked, it was because people bought a magnetic stripe reader. That's why the MBTA has abandoned that technology and is now using contactless passes.

Zachary Bertocchi did his own research and found out that the “modern” Boston transit cards use MIFARE technology. There are many varieties: MIFARE Plus, Ultralight, DESfire, but the most infamous is MIFARE Classic. Of course, this is what is used in Charlie cards. Zachary looked for a suitable NFC reader and, after trying several options, settled on the PN532. It is a small red card that costs about $9, is sold on Aliexpress and works in tandem with a Raspberry Pi.

MIFARE Classic uses a proprietary 48-bit NXP encryption algorithm called Crypto1, which is based on the principle of security through obscurity. When you dive into cryptography superficially, it may seem that this is not bad. In fact, such encryption can be cracked in about an hour, which has been repeatedly demonstrated in practice. Unlike conventional encryption, which has one or two keys, MIFARE Classic has a total of 32 Sector keys. To obtain them, you can use two types of attacks: nested and dark side. It is easy to find a number of tools for their implementation on the Internet and all the necessary reference information.
Zachary found standard MIFARE keys online, loaded them into a utility called MFOC, which implements a nested attack, and obtained all sixteen A and B key pairs.

It is clear that when introducing contactless passes, the MBTA simply did not bother to change the standard keys. This gives free rein to anyone who wants to manipulate the data stored on the cards.

Screenshot from a hex editor with binary data from a Charlie transport card.
First, Zachary dumped the binary data from Charlie's bus pass to perform an attack similar to the one the MIT students had done. He wrote the dump to a blank dummy — a Chinese card with a backdoor that allowed the UID to be changed. And it worked.

The terminal withdrew money from the blank, but the original card still had the same amount. Therefore, in this transport system there is no source of truth in the form of some database. All balance information is stored directly on the card.
Not everything is so simple
This cloning resembles a cheat code for infinite money, but it has a number of problems. To exploit such a vulnerability, you first need to buy and top up the original card. Moreover, pairs of identical travel cards are blocked quite quickly - their repeated use triggers the protection systems. Counterfeiting cards is a completely different matter. But for this, I had to carefully study the hexadecimal dump.It turned out that when the first four bytes (UID) were converted to decimal form, they corresponded to the number printed on the travel card – the serial number.

Then Zachary remembered that Charlie's old tickets had a checksum, and found something similar in the fresh dump.

The data bytes highlighted in yellow are most likely a checksum, since they are present even in the lines filled with zeros.
Unfortunately, none of the dozens of popular hashing algorithms worked with these strings.
Decrypting the hash
Somewhere around this point, Scott Campbell and Matty Harris joined the project. Together, the researchers began comparing dumps of different cards.

Examples of checksum from two different cards.
In the example above, identical strings from two dumps from different travel cards have different checksums. This means that cryptographic salt has been added to them. Understanding this could be the next step in deciphering the hash. But the researchers spent about three weeks testing standard checksum calculators with salt and still got nowhere.

Checksum calculators.
The breakthrough came from finding mathematical patterns between the checksums. It turned out that if you take a pair of lines with the same data from different travel cards and apply the XOR function to them, you get the same value.

0x98С3 — checksum modifier.
How can this be used? The first step is to find two identical lines. The easiest ones are those that contain only zeros. Then comes the calculation of the checksum modifier. This is what the researchers called the value that is obtained by XORing two checksums. This value can be used to transfer lines from one card to another.
To do this, you need to copy any line from the card dump, then apply XOR to the old checksum, and get a new one. After that, it remains to write it to the appropriate slot, and the line is copied.
Opportunities for reverse engineering
At first glance, this approach differs little from simple cloning, but it allows not only to transfer dumps from card to card, but also to edit data. In addition, the possibilities for reverse engineering are significantly expanded.
For a long time, Harris, Bertocchi, Gibson and Campbell operated by trial and error, changing random data on cards and immediately applying them to readers at subway stations. To save time and rewrite cards "without leaving the cash register", they assembled a portable NFC reader from a PN532, Raspberry Pi and a power bank.
Let's say you topped up your travel card with $50 and cloned it. If the travel card is blocked, these funds will disappear. But you can copy the line with money from the old card to the new one and continue using it. To do this, you need to determine which line of the dump contains information about the funds stored on the card. Naturally, this value should change after payment, so you only need to find the necessary variables.

The current amount on the card is shown in green, the previous amount is shown in pink.
It might not seem like a dollar amount, but here's where the math magic begins. If you convert the values from hexadecimal to decimal, you get the following numbers.

It still doesn't look anything like bucks, but if you divide these values by two, they start to look familiar. After repeating these operations with several more cards, the researchers realized that this variable is where the money is stored. Only for some reason it is expressed in halves - 0.5 cents. It also turned out that each card has two transaction registers in its memory: one for the current and previous values.

How to change the contents of a card and "wind up" money
The first step is to isolate the variables. As you can see, the only data that is different between these two rows is highlighted in red.
On the left is money, on the right is the checksum.
The researchers then tried to XOR the two values in different versions. This makes sense, since this operation was the key to copying data between cards. This yielded the green value, which they called the data modifier. They then XORed the two checksums, yielding the red value, the checksum modifier.
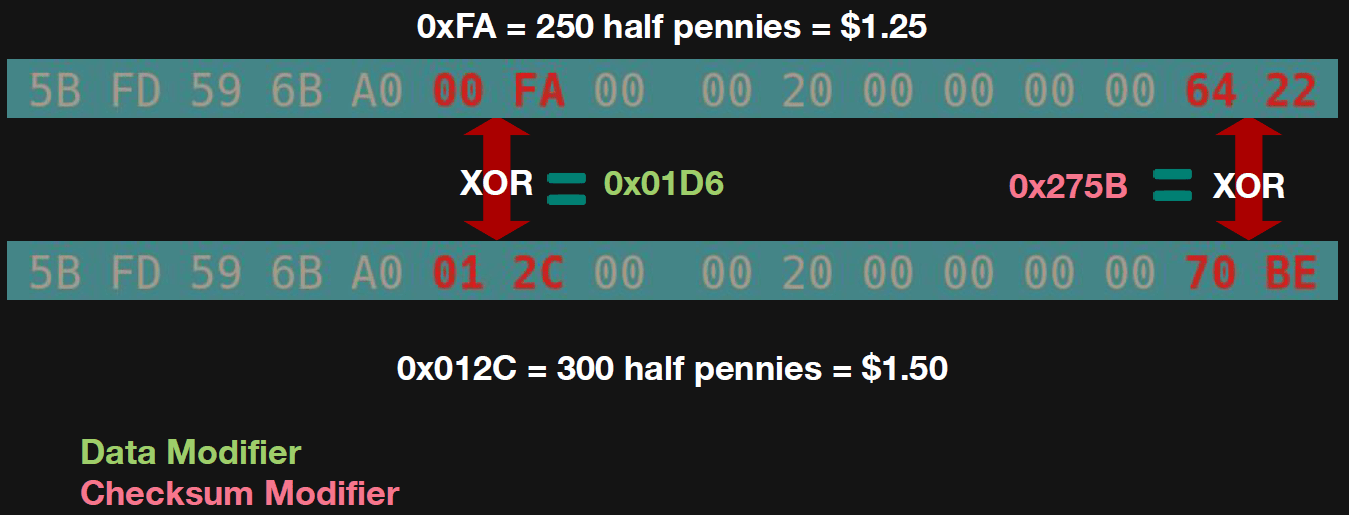
Next, the researchers took a card containing zero dollars and zero cents and XORed it with a data modifier. At the same time, they XORed the checksum with a checksum modifier.

It worked: a new line was created, which was written to the card. And the reader accepted it.
However, these changes were not enough for even one trip. To significantly increase the amount, an additional 25 cents had to be put on the card first.

The extra quarter is needed because this method uses XOR of two values. As you can see from the example above, it is not possible to XOR the value 15 any further. You need to add an external value to get another bit before continuing the "twisting".
Having a card with two dollars and sixty cents in hand, you can repeat the described operations over and over again:
- perform XOR to get the data modifier and the checksum modifier;
- take a card with zero, XOR the money with the data modifier and the checksum with the checksum modifier;
- get a new line with $4.95;
And so on in a circle.
The data and checksum modifiers are doubled until they reach the limit of $327.67. This is despite the fact that the Charlie card cannot normally be loaded with more than $100.

Later, the researchers improved the process so that they didn't have to add 25 cents each time: they collected all the modifiers into a large table and automated the modification of the dump.

Dictionary and brief description of transformations of different types of data in the memory of the travel card.
Thus:
- You need to choose what to change, for example: 0x32 ($0.25) to 0xC8 ($1) in column 7.
- Find the data modifier: XOR 0x32 with 0xC8 to get 0xFA.
- Find the checksum modifier: substitute 0xFA and column 7 into the lookup table.
- XOR the modified checksum (0xDE81) with the old checksum to obtain the target checksum.
With automation, the hack into Boston's transit system ultimately came down to two steps:
- Buy a card for 25 cents;
- Change data to $327.
Post-mortem

Anatomy of a Charlie Card.
The most interesting thing in the dump is the variables that are responsible for money and the card type. The former allow you to make a Charlie for $300, and the latter - to make travel cards for people with visual impairments, pensioners, students and subway employees.
To demonstrate their achievement, Harris, Bertocchi, Gibson, and Campbell built a transit card machine and approached the MBTA.

CharlieKiosk v2: Raspberry Pi 4, PN532, Raspberry Pi, Adafruit speaker kit, 3D printed PLA enclosure. UI based on Tauri framework (source.
Although hacking transit cards is illegal, the transit agency did not sue this time. In fact, it even allowed our heroes to present their project at DEF CON.

Photo Bostonglobe.
The researchers were invited to a meeting at the agency's headquarters and their recommendations were heard. Essentially, they boil down to the following:
- When implementing a travel payment system, you should not store money on the card;
- It is worth using ready-made secure systems like Apple and Google Pay;
- It is advisable to store data about cards, transactions and users in a separate database;
- Such systems need to be maintained and regularly upgraded after deployment.
Has the Massachusetts Bay Transportation Authority learned anything from this whole story? It seems so. Bostonglobe reports that the MBTA has worked with researchers to develop automated scripts that can detect counterfeit cards and remotely deactivate them every 24 hours. However, a permanent solution to the problem will clearly require replacing the current CharlieCard system. The upgrade is scheduled to be completed by March 2025.
Source
